目录
- 1.下载及安装blackbox_exporter
- 2.修改配置文件设置监控内容
- 2.1.使用http方式作为探测
- 3.与prometheus集成
- 4.导入blackbox仪表盘进行观测
1.下载及安装blackbox_exporter
- 下载安装包
wget https://github.com/prometheus/blackbox_exporter/releases/download/v0.23.0/blackbox_exporter-0.23.0.linux-amd64.tar.gz
- 将压缩包解压至
/data目录下
mkdir /data
tar xf blackbox_exporter-0.23.0.linux-amd64.tar.gz -C /data/
cd /data
ln -s blackbox_exporter-0.23.0.linux-amd64/ blackbox_exporter
-
为blackbox_exporter创建启动文件
vi /usr/lib/systemd/system/blackbox_exporter.service
[Unit]
Description=blackbox_exporter
After=network.target
[Service]
Type=simple
User=root
Group=root
ExecStart=/data/blackbox_exporter/blackbox_exporter \
--config.file=/data/blackbox_exporter/blackbox.yml \
--web.listen-address=:9115
Restart=on-failure
[Install]
WantedBy=multi-user.target
systemctl daemon-reload
systemctl start blackbox_exporter.service
systemctl enable blackbox_exporter.service
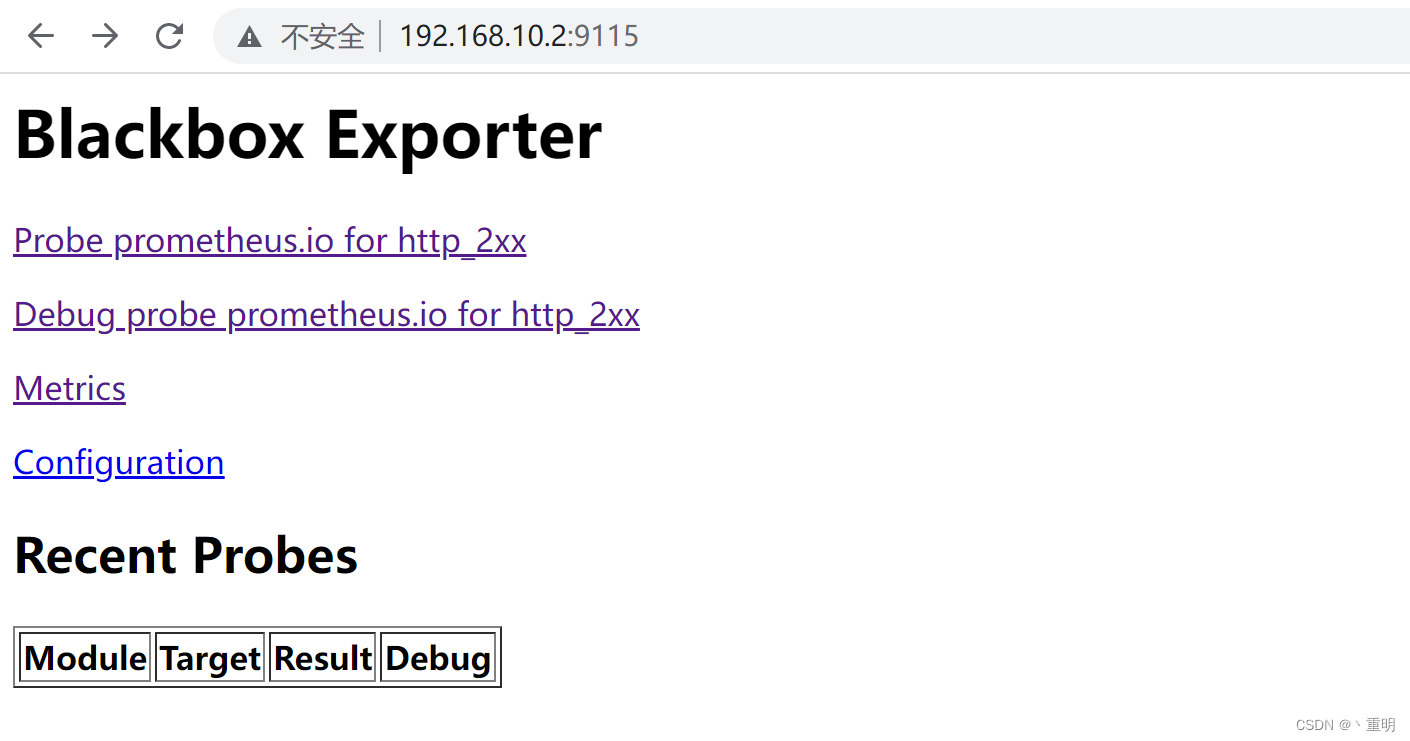
- 看到这个页面说明启动成功:通过IP:端口访问
2.修改配置文件设置监控内容
- 安装完成后会有默认配置文件模板,分别有http探测、tcp探测、grpc探测、ssh探测、irc探测和icmp探测等内容。
- 使用时可根据具体情况选择合适探测方式
modules:
http_2xx:
prober: http
http_post_2xx:
prober: http
http:
method: POST
tcp_connect:
prober: tcp
pop3s_banner:
prober: tcp
tcp:
query_response:
- expect: "^+OK"
tls: true
tls_config:
insecure_skip_verify: false
grpc:
prober: grpc
grpc:
tls: true
preferred_ip_protocol: "ip4"
grpc_plain:
prober: grpc
grpc:
tls: false
service: "service1"
ssh_banner:
prober: tcp
tcp:
query_response:
- expect: "^SSH-2.0-"
- send: "SSH-2.0-blackbox-ssh-check"
irc_banner:
prober: tcp
tcp:
query_response:
- send: "NICK prober"
- send: "USER prober prober prober :prober"
- expect: "PING :([^ ]+)"
send: "PONG ${1}"
- expect: "^:[^ ]+ 001"
icmp:
prober: icmp
icmp_ttl5:
prober: icmp
timeout: 5s
icmp:
ttl: 5
2.1.使用http方式作为探测
vim blackbox.yml
- 以下配置含义为:定义了一个名为http的http检测模块,超时时间为10s,探针验证的HTTP响应状态代码的为空数组,默认是200-299 。该探针使用的HTTP方法为GET,insecure_skip_verify: false 表示该探针不允许跳过TLS证书验证
modules:
http:
prober: http
timeout: 10s
http:
valid_status_codes: []
method: GET
tls_config:
insecure_skip_verify: false
systemctl restart blackbox_exporter
3.与prometheus集成
-
修改prometheus配置文件
vim prometheus.yml
- job_name: "blackbox"
metrics_path: /probe
params:
# 模块名需要与prober: http一致
module: [http]
static_configs:
# 需要探测的域名
- targets:
- www.baidu.com
relabel_configs:
- source_labels: [__address__]
target_label: __param_target
- source_labels: [__param_target]
target_label: instance
- target_label: __address__
replacement: 192.168.10.3:9115
systemctl restart prometheus
relabel_configs内容为:
1.将所有含有 address 标签的项目重新标记为 __param_target
2.将所有含有 __param_target 标签的项目重新标记为 instance
3.将所有 address 标签替换为 blackbox_exporter IP:9115
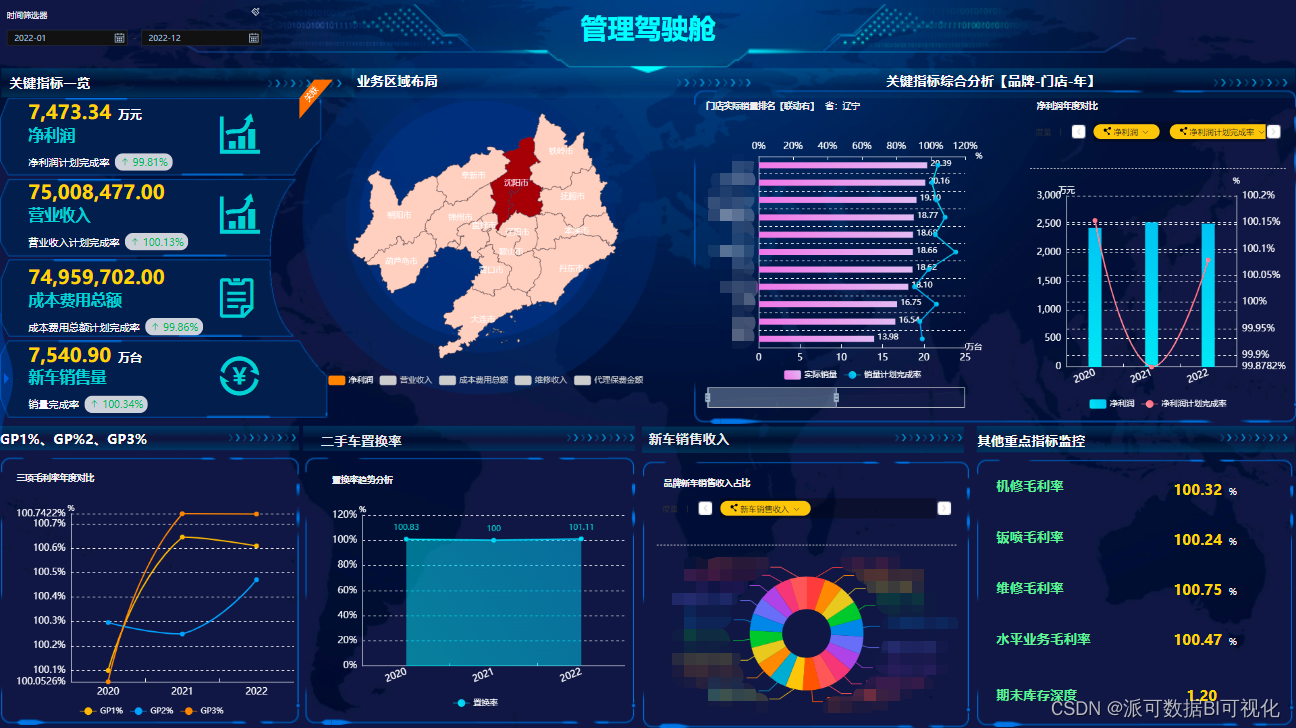
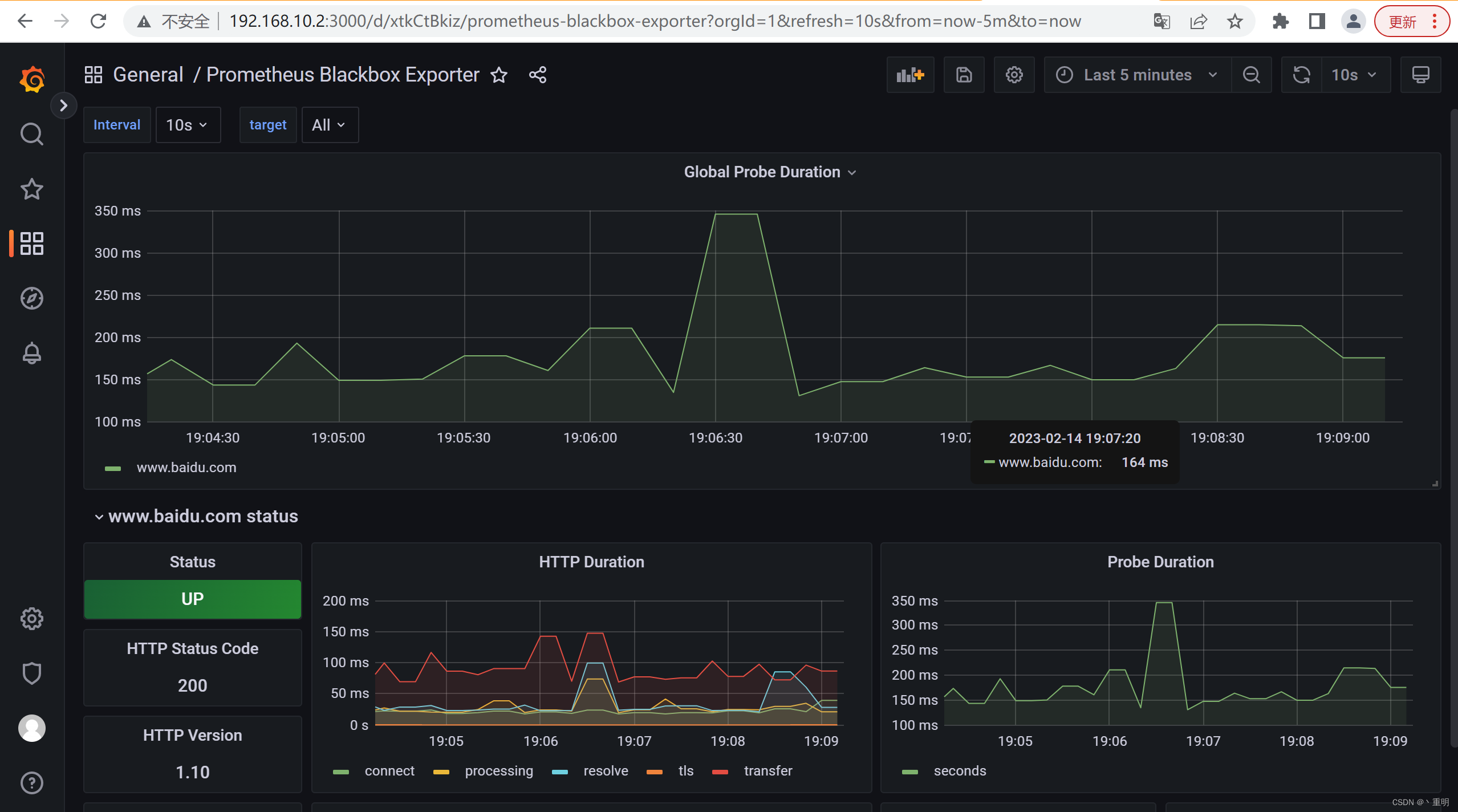
4.导入blackbox仪表盘进行观测
- 怎么导入就不说了,请看我其他prometheus系列文章
- 导入的仪表盘ID为7587
- 仪表盘内容:
更多内容请参考官方示例