一、手工方式建立
手工方式建立IPsec的场景,全部参数需要手工配置,工作量大,适用于小型静态网络。
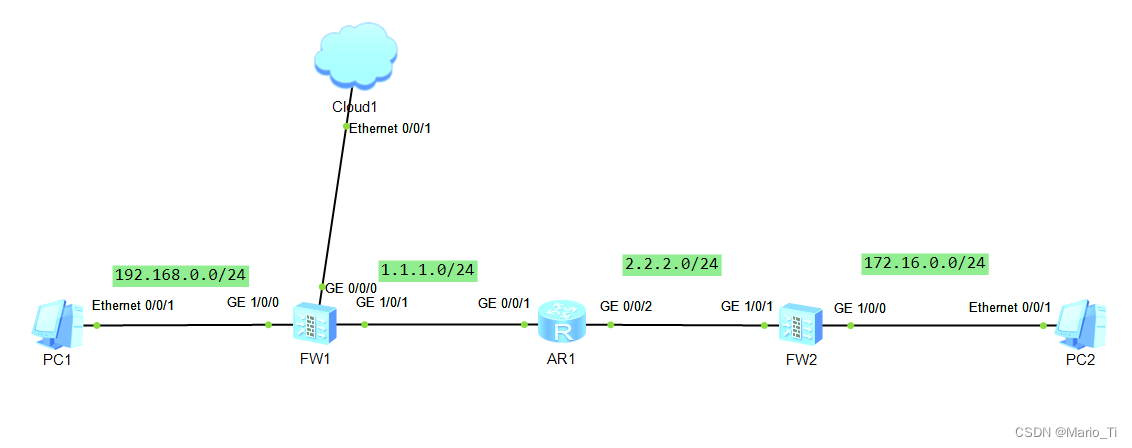
当企业总部与分支通过FW1和FW2之间建立的IPsec隧道进行安全通信。

手工配置步骤主要有四个:
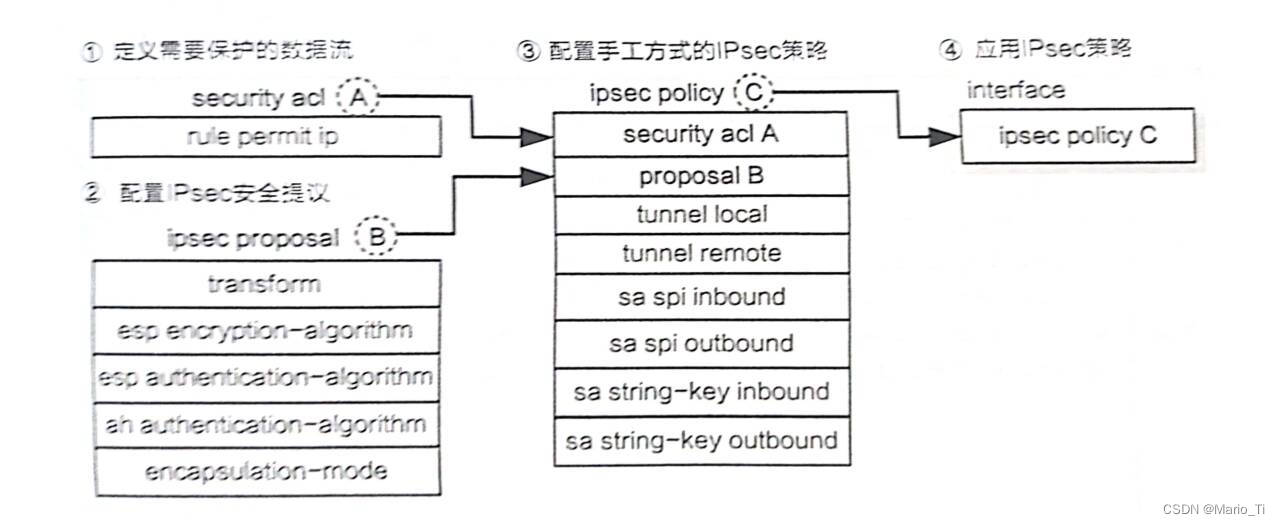
①定义需要保护的数据流;
②配置IPsec安全提议,两端通过对方的提议决定是否成为盟友,封装模式、安全协议、加密算法、验证算法均在此处配置;
③配置手工方式的IPsec策略,指定总部和分支防火墙的公网地址、安全联盟标识符SPI,以及加密密钥和验证密钥;、
④应用IPsec策略。
[Fw1]acl number 3000
[Fw1-acl-adv-3000]rule 5 permit ip source 192.168.0.0 0.0.0.255 destination 172.
16.0.0 0.0.0.255
[Fw1-acl-adv-3000]quit
[Fw1]ipsec proposal pro1
[Fw1-ipsec-proposal-pro1]transform esp
[Fw1-ipsec-proposal-pro1]encapsulation-mode tunnel
[Fw1-ipsec-proposal-pro1]esp authentication-algorithm sha2-256
[Fw1-ipsec-proposal-pro1]esp encryption-algorithm aes-256
[Fw1-ipsec-proposal-pro1]quit
[Fw1]ipsec policy policy1 1 manual
[Fw1-ipsec-policy-manual-policy1-1]security acl 3000
[Fw1-ipsec-policy-manual-policy1-1]proposal pro1
[Fw1-ipsec-policy-manual-policy1-1]tunnel local 1.1.1.1
[Fw1-ipsec-policy-manual-policy1-1]tunnel remote 2.2.2.1
[Fw1-ipsec-policy-manual-policy1-1]sa spi inbound esp 54321
[Fw1-ipsec-policy-manual-policy1-1]sa spi outbound esp 12345
[Fw1-ipsec-policy-manual-policy1-1]sa string-key inbound esp huawei@123
[Fw1-ipsec-policy-manual-policy1-1]sa string-key outbound esp huawei@456
[Fw1]interface g1/0/1
[Fw1-GigabitEthernet1/0/1]ipsec policy policy1
[Fw1]ip route-static 172.16.0.0 24 1.1.1.2[FW2]acl number 3000
[FW2-acl-adv-3000]rule 5 permit ip source 172.16.0.0 0.0.0.255 destination 192.1
68.0.0 0.0.0.255
[FW2-acl-adv-3000]quit
[FW2]ipsec proposal pro1
[FW2-ipsec-proposal-pro1]transform esp
[FW2-ipsec-proposal-pro1]encapsulation-mode tunnel
[FW2-ipsec-proposal-pro1]esp authentication-algorithm sha2-256
[FW2-ipsec-proposal-pro1]esp encryption-algorithm aes-256
[FW2-ipsec-proposal-pro1]quit
[FW2]ipsec policy policy1 1 manual
[FW2-ipsec-policy-manual-policy1-1]security acl 3000
[FW2-ipsec-policy-manual-policy1-1]proposal pro1
[FW2-ipsec-policy-manual-policy1-1]tunnel local 2.2.2.1
[FW2-ipsec-policy-manual-policy1-1]tunnel remote 1.1.1.1
[FW2-ipsec-policy-manual-policy1-1]sa spi inbound esp 12345
[FW2-ipsec-policy-manual-policy1-1]sa spi outbound esp 54321
[FW2-ipsec-policy-manual-policy1-1]sa string-key inbound esp huawei@456
[FW2-ipsec-policy-manual-policy1-1]sa string-key outbound esp huawei@123
[FW2]interface g1/0/1
[FW2-GigabitEthernet1/0/1]ipsec policy policy1
[FW2]ip route-static 192.168.0.0 24 2.2.2.2
[Fw1]firewall zone trust
[Fw1-zone-trust]add interface g1/0/0
[Fw1-zone-trust]firewall zone untrust
[Fw1-zone-untrust]add interface g1/0/1
[Fw1-policy-security]display this
2024-03-08 11:53:20.430
#
security-policy
rule name tr_to_untr
source-zone trust
destination-zone untrust
source-address 192.168.0.0 mask 255.255.255.0
destination-address 172.16.0.0 mask 255.255.255.0
action permit
rule name local_to_untr
source-zone local
destination-zone untrust
source-address 1.1.1.1 mask 255.255.255.255
destination-address 2.2.2.1 mask 255.255.255.255
action permit
rule name untr_to_local
source-zone untrust
destination-zone local
source-address 2.2.2.1 mask 255.255.255.255
destination-address 1.1.1.1 mask 255.255.255.255
action permit
rule name untr_to_tr
source-zone untrust
destination-zone trust
source-address 172.16.0.0 mask 255.255.255.0
action permit
#
return
[FW2]firewall zone trust
[FW2-zone-trust]add interface g1/0/0
[FW2-zone-trust]firewall zone untrust
[FW2-zone-untrust]add interface g1/0/1
[FW2-policy-security]display this
2024-03-08 11:56:43.140
#
security-policy
rule name tr_to_untr
source-zone trust
destination-zone untrust
source-address 172.16.0.0 mask 255.255.255.0
destination-address 192.168.0.0 mask 255.255.255.0
action permit
rule name local_to_untr
source-zone local
destination-zone untrust
source-address 2.2.2.1 mask 255.255.255.255
destination-address 1.1.1.1 mask 255.255.255.255
action permit
rule name untr_to_local
source-zone untrust
destination-zone local
source-address 1.1.1.1 mask 255.255.255.255
destination-address 2.2.2.1 mask 255.255.255.255
action permit
rule name untr_to_tr
source-zone untrust
destination-zone trust
source-address 192.168.0.0 mask 255.255.255.0
destination-address 172.16.0.0 mask 255.255.255.0
action permit
#
return注意:配置Trust域与Untrust域之间的域间安全策略、配置Untrust域与Local域之间的域间安全策略。
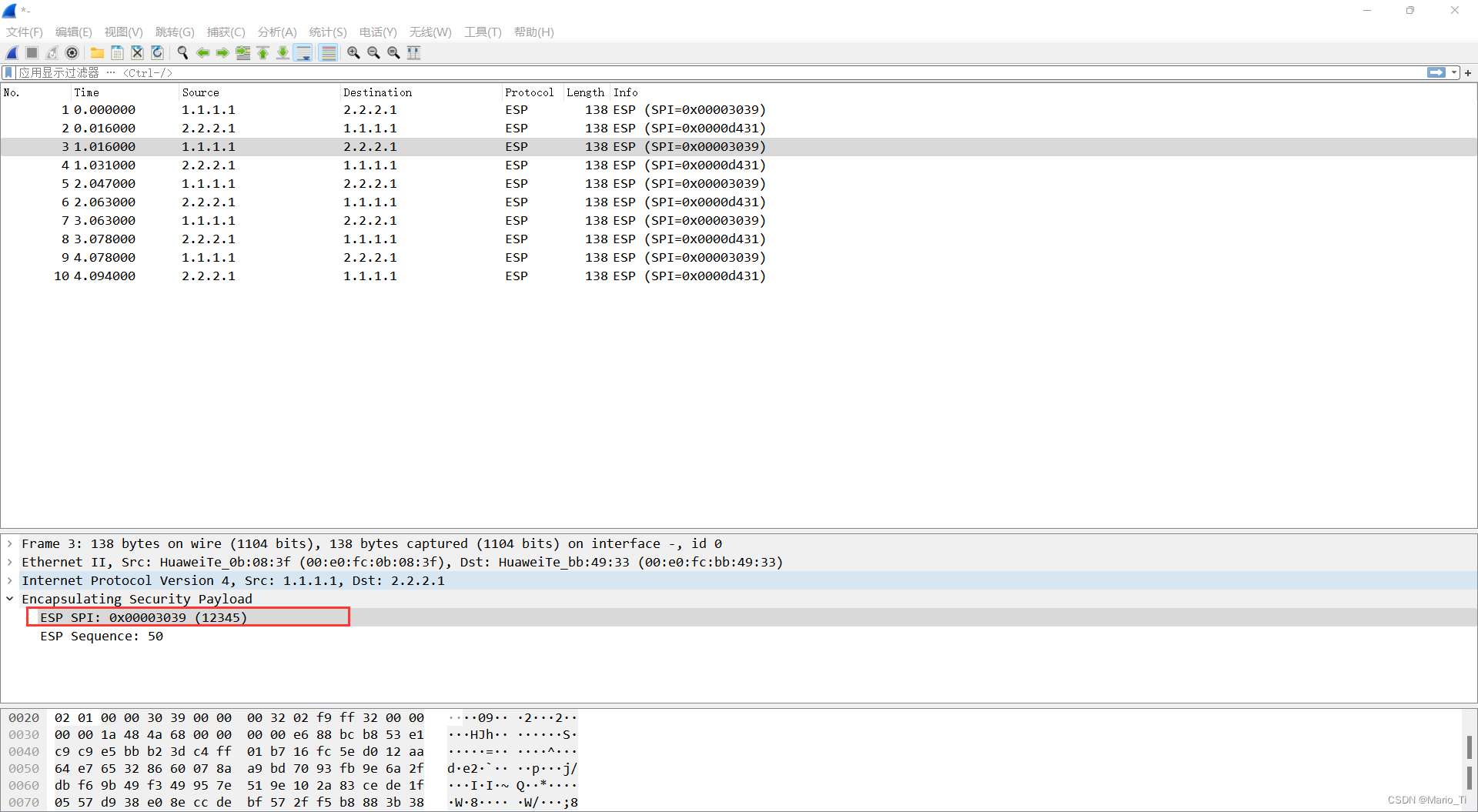
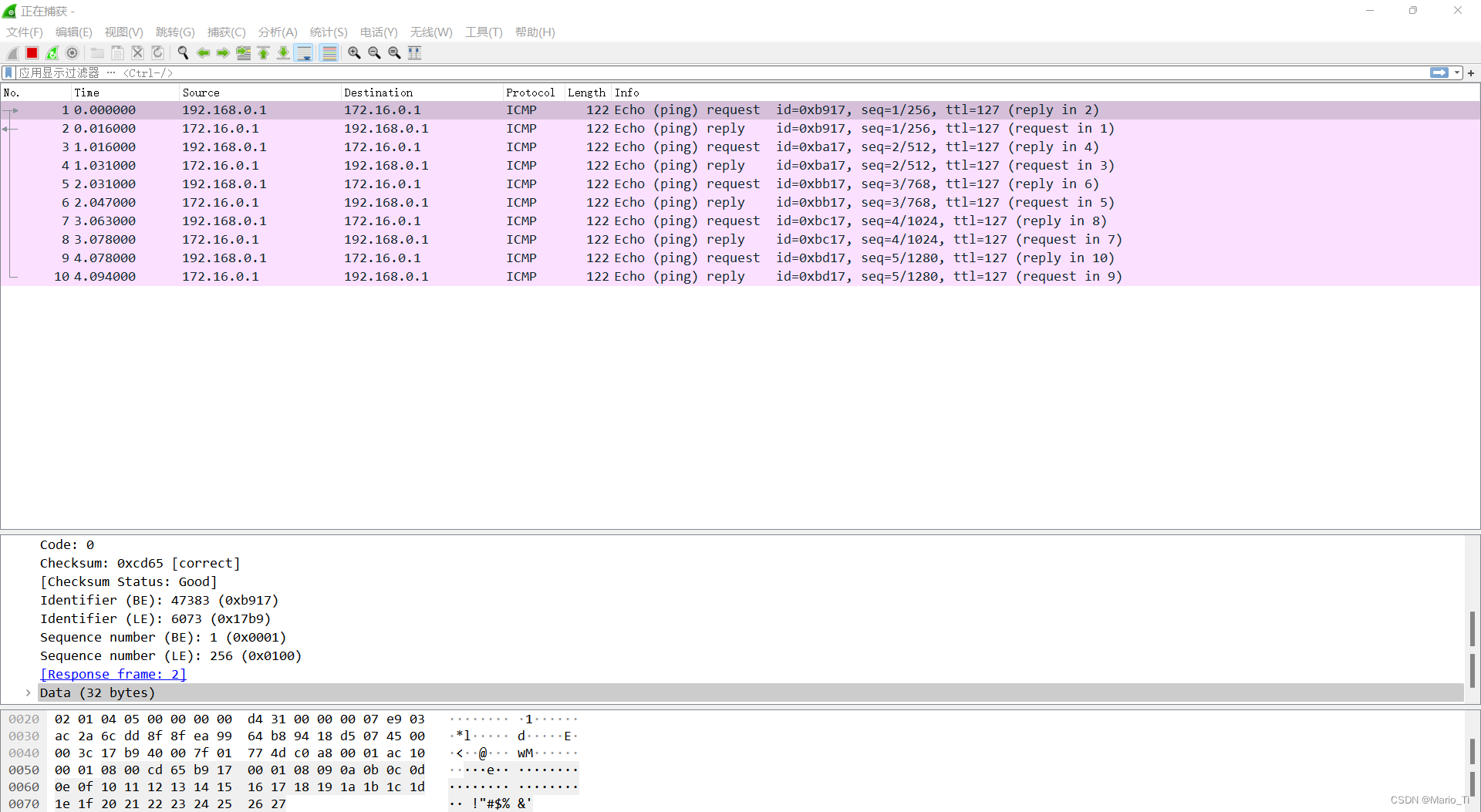
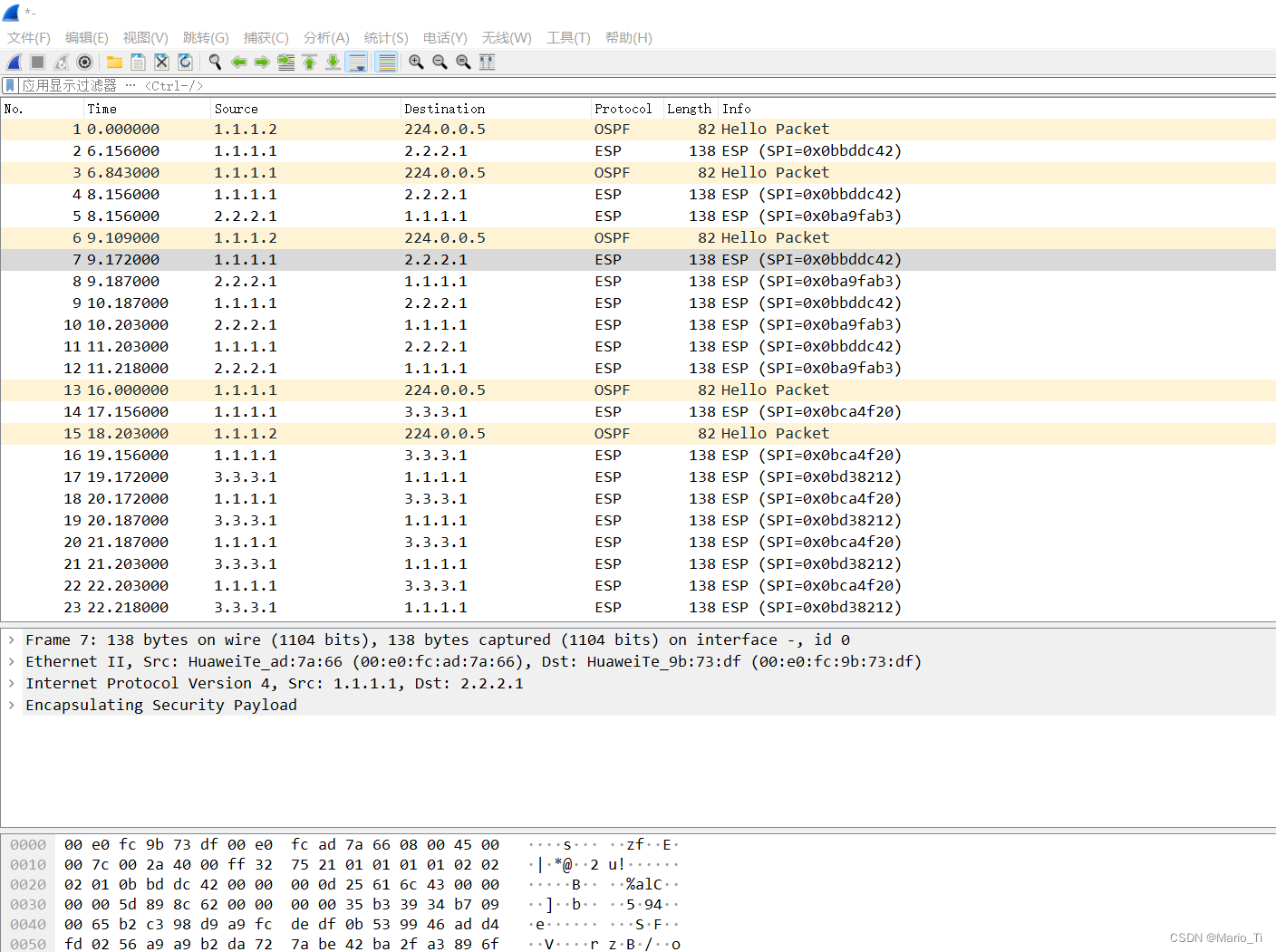
当PC1 ping PC2时,通过抓包可以发现,去程包的SPI为0x00003039,即12345,回程为0x0000等31 ,即54321。
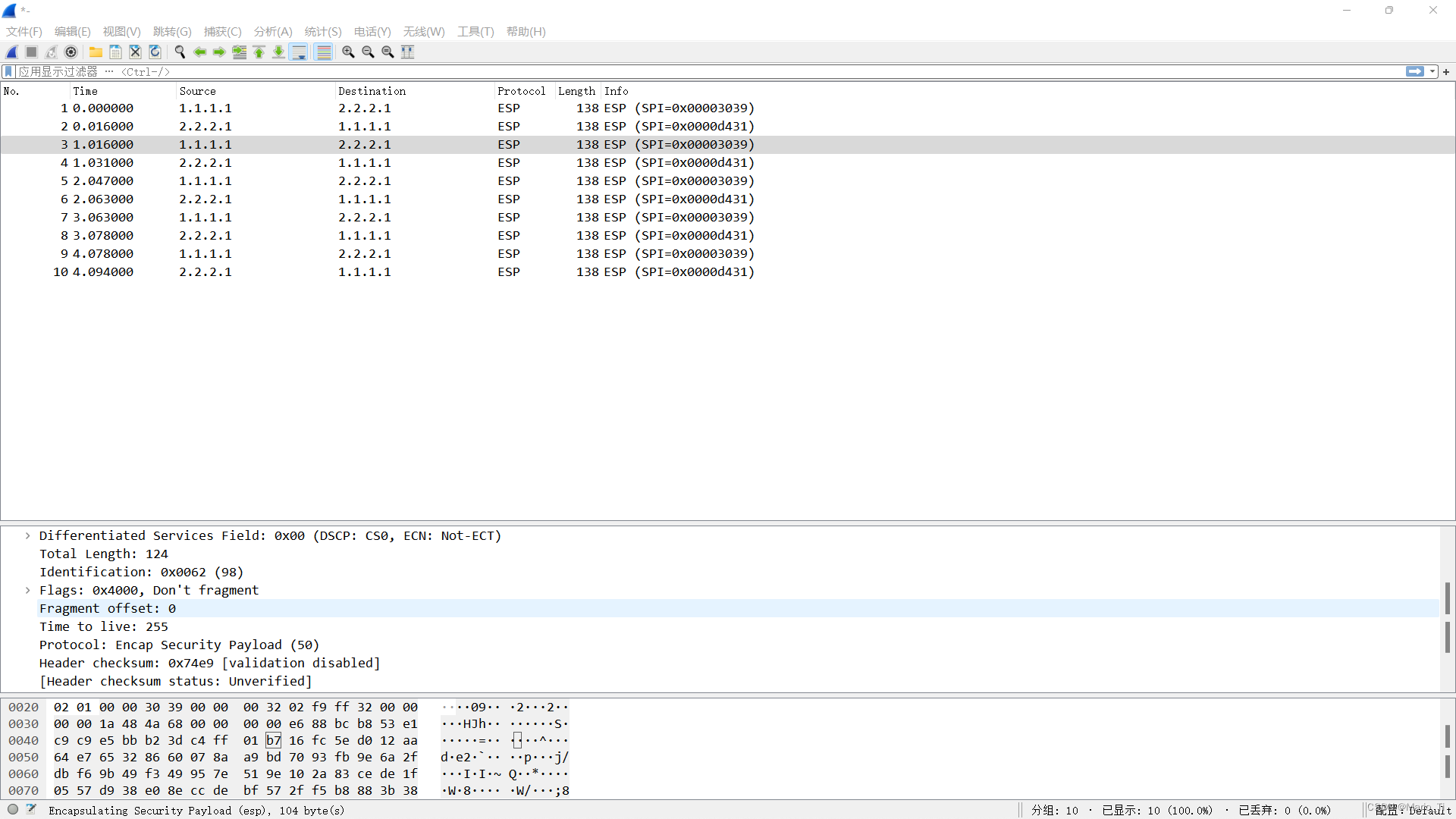
分析报文内容,ESP报文头部内消息被加密。
若采用AH,抓包分析,可见AH没有加密功能,只有验证功能。
二、IKE方式建立
1、ISAKMP方式的IPsec策略
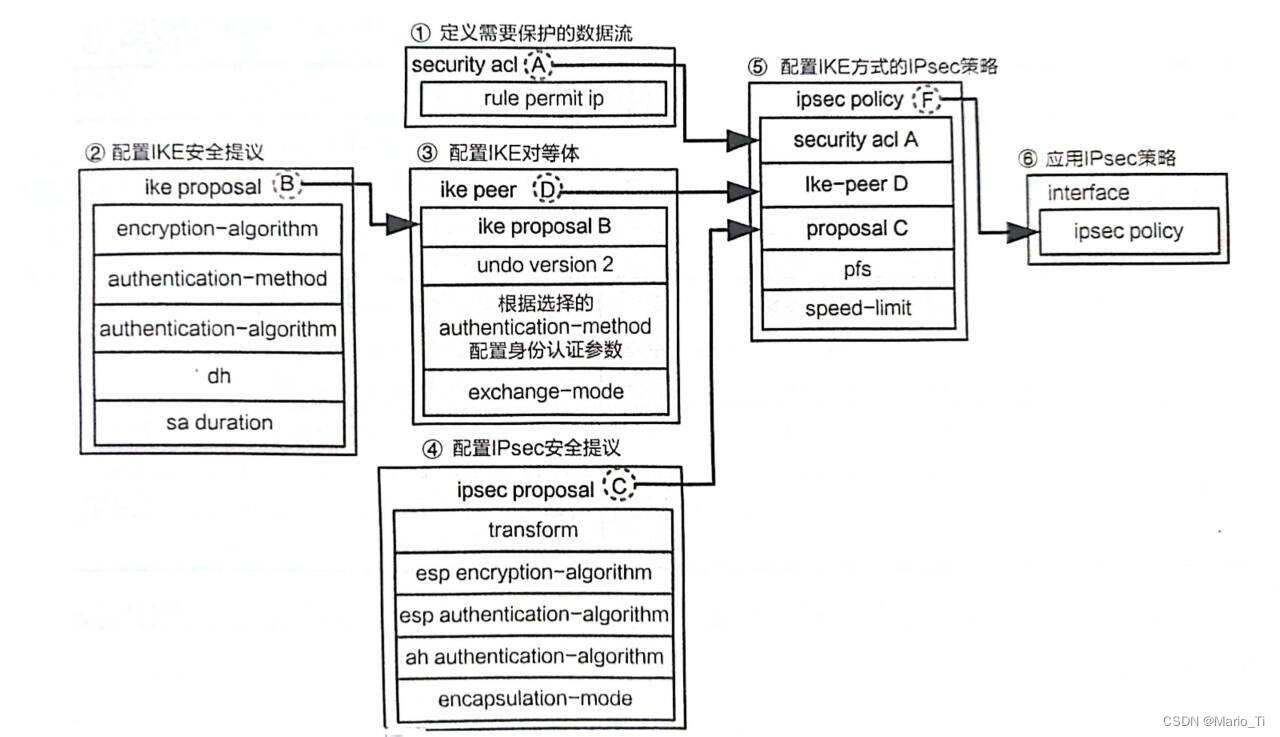
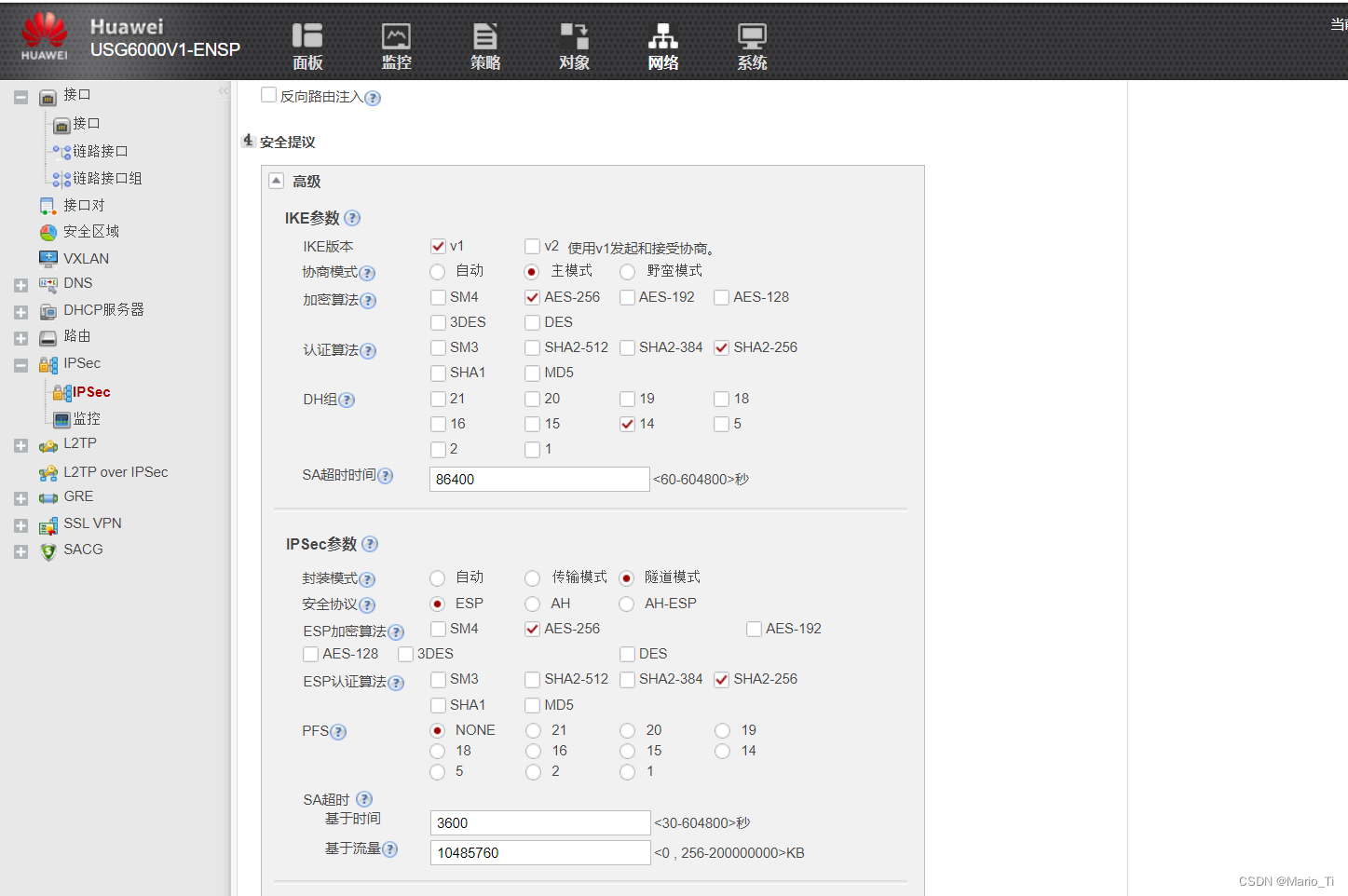
相比手工配置的方式,采用ISAKMP方式的IPsec策略配置步骤只多了两步,配置IKE安全提议和IKE对等体,以IKEv1为例。
ISAKMP方式的IPsec策略配置示意图可参考下图:
[Fw1]ike proposal 10
[Fw1-ike-proposal-10]display this
2024-03-09 07:28:31.710
#
ike proposal 10
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
return
[Fw1]ike peer b
[Fw1-ike-peer-b]ike-proposal 10
[Fw1-ike-peer-b]undo version 2
[Fw1-ike-peer-b]exchange-mode main
[Fw1-ike-peer-b]remote-address 2.2.2.1
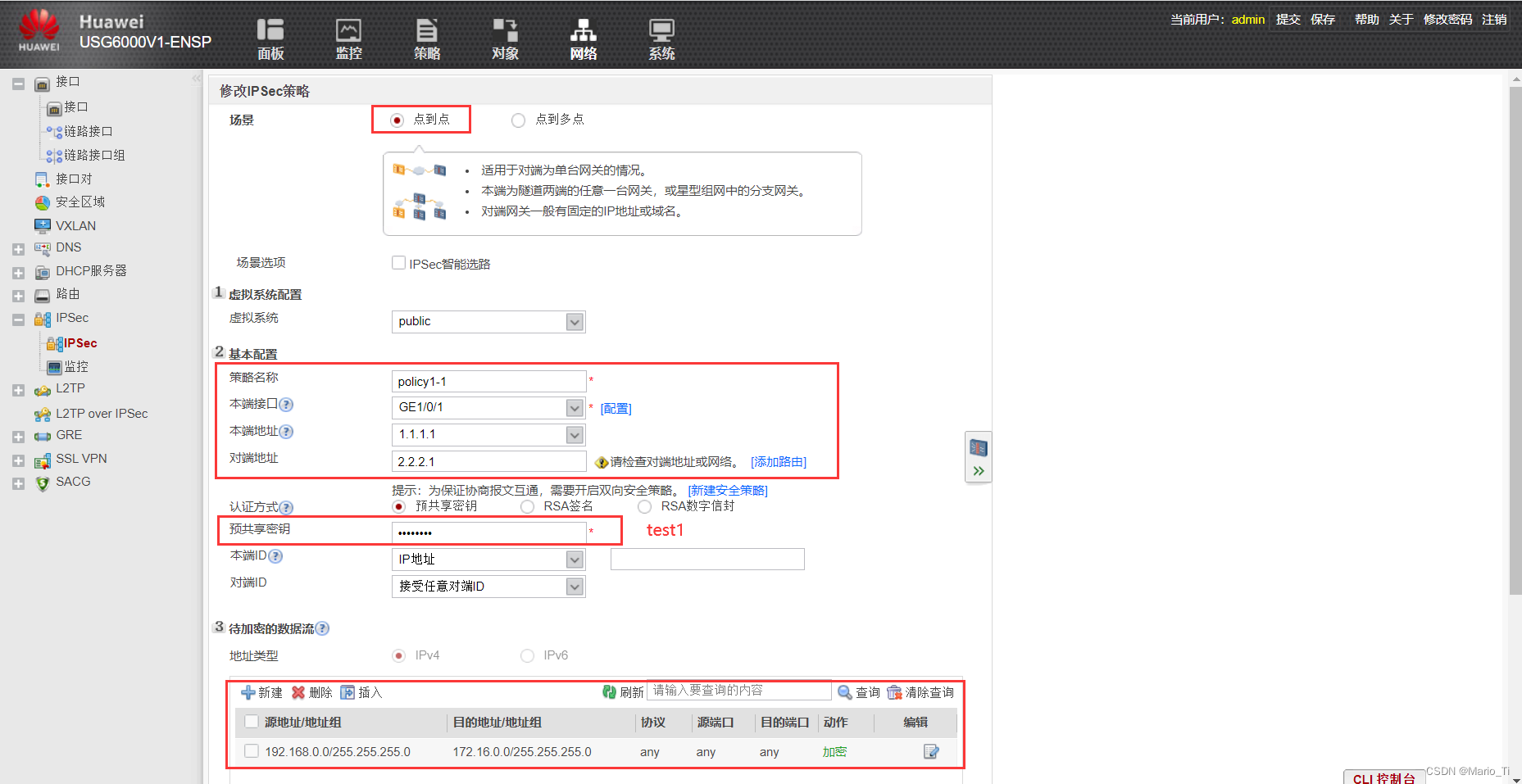
[Fw1-ike-peer-b]pre-shared-key test1
[Fw1]acl number 3000
[Fw1-acl-adv-3000]display this
2024-03-09 07:30:58.010
#
acl number 3000
rule 5 permit ip source 192.168.0.0 0.0.0.255 destination 172.16.0.0 0.0.0.255
#
return
[Fw1]ipsec proposal a
[Fw1-ipsec-proposal-a]transform esp
[Fw1-ipsec-proposal-a]encapsulation-mode tunnel
[Fw1-ipsec-proposal-a]esp authentication-algorithm sha2-256
[Fw1-ipsec-proposal-a]esp encryption-algorithm aes-256
[Fw1]ipsec policy policy1 1 isakmp
Info: The ISAKMP policy sequence number should be smaller than the template poli
cy sequence number in the policy group. Otherwise, the ISAKMP policy does not ta
ke effect.
[Fw1-ipsec-policy-isakmp-policy1-1]security acl 3000
[Fw1-ipsec-policy-isakmp-policy1-1]proposal a
[Fw1-ipsec-policy-isakmp-policy1-1]ike-peer b
[Fw1]interface g1/0/1
[Fw1-GigabitEthernet1/0/1]ipsec policy policy1
[Fw1]ip route-static 172.16.0.0 24 1.1.1.2
[FW2]ike proposal 10
[FW2-ike-proposal-10]quit
[FW2]ike peer a
[FW2-ike-peer-a]ike-proposal 10
[FW2-ike-peer-a]undo version 2
[FW2-ike-peer-a]exchange-mode main
[FW2-ike-peer-a]remote-address 1.1.1.1
[FW2-ike-peer-a]pre-shared-key test1
[FW2]acl number 3000
[FW2-acl-adv-3000]display this
2024-03-09 07:36:12.140
#
acl number 3000
rule 5 permit ip source 172.16.0.0 0.0.0.255 destination 192.168.0.0 0.0.0.255
#
return
[FW2]ipsec proposal b
[FW2-ipsec-proposal-b]transform esp
[FW2-ipsec-proposal-b]encapsulation-mode tunnel
[FW2-ipsec-proposal-b]esp authentication-algorithm sha2-256
[FW2-ipsec-proposal-b]esp encryption-algorithm aes-256
[FW2]ipsec policy policy1 1 isakmp
Info: The ISAKMP policy sequence number should be smaller than the template poli
cy sequence number in the policy group. Otherwise, the ISAKMP policy does not ta
ke effect.
[FW2-ipsec-policy-isakmp-policy1-1]security acl 3000
[FW2-ipsec-policy-isakmp-policy1-1]proposal b
[FW2-ipsec-policy-isakmp-policy1-1]ike-peer a
[FW2]interface g1/0/1
[FW2-GigabitEthernet1/0/1]ipsec policy policy1
[FW2]ip route-static 192.168.0.0 24 2.2.2.2
FW2的web配置方式与FW1类似,此处不再赘述。
安全策略的配置仍与手工配置一致即可。
[Fw1]firewall zone trust
[Fw1-zone-trust]add interface g1/0/0
[Fw1-zone-trust]firewall zone untrust
[Fw1-zone-untrust]add interface g1/0/1
[Fw1-policy-security]display this
2024-03-08 11:53:20.430
#
security-policy
rule name tr_to_untr
source-zone trust
destination-zone untrust
source-address 192.168.0.0 mask 255.255.255.0
destination-address 172.16.0.0 mask 255.255.255.0
action permit
rule name local_to_untr
source-zone local
destination-zone untrust
source-address 1.1.1.1 mask 255.255.255.255
destination-address 2.2.2.1 mask 255.255.255.255
action permit
rule name untr_to_local
source-zone untrust
destination-zone local
source-address 2.2.2.1 mask 255.255.255.255
destination-address 1.1.1.1 mask 255.255.255.255
action permit
rule name untr_to_tr
source-zone untrust
destination-zone trust
source-address 172.16.0.0 mask 255.255.255.0
action permit
#
return
[FW2]firewall zone trust
[FW2-zone-trust]add interface g1/0/0
[FW2-zone-trust]firewall zone untrust
[FW2-zone-untrust]add interface g1/0/1
[FW2-policy-security]display this
2024-03-08 11:56:43.140
#
security-policy
rule name tr_to_untr
source-zone trust
destination-zone untrust
source-address 172.16.0.0 mask 255.255.255.0
destination-address 192.168.0.0 mask 255.255.255.0
action permit
rule name local_to_untr
source-zone local
destination-zone untrust
source-address 2.2.2.1 mask 255.255.255.255
destination-address 1.1.1.1 mask 255.255.255.255
action permit
rule name untr_to_local
source-zone untrust
destination-zone local
source-address 1.1.1.1 mask 255.255.255.255
destination-address 2.2.2.1 mask 255.255.255.255
action permit
rule name untr_to_tr
source-zone untrust
destination-zone trust
source-address 192.168.0.0 mask 255.255.255.0
destination-address 172.16.0.0 mask 255.255.255.0
action permit
#
return抓包分析可见,SPI是随机生成的,以及用了ESP,具有加密功能。
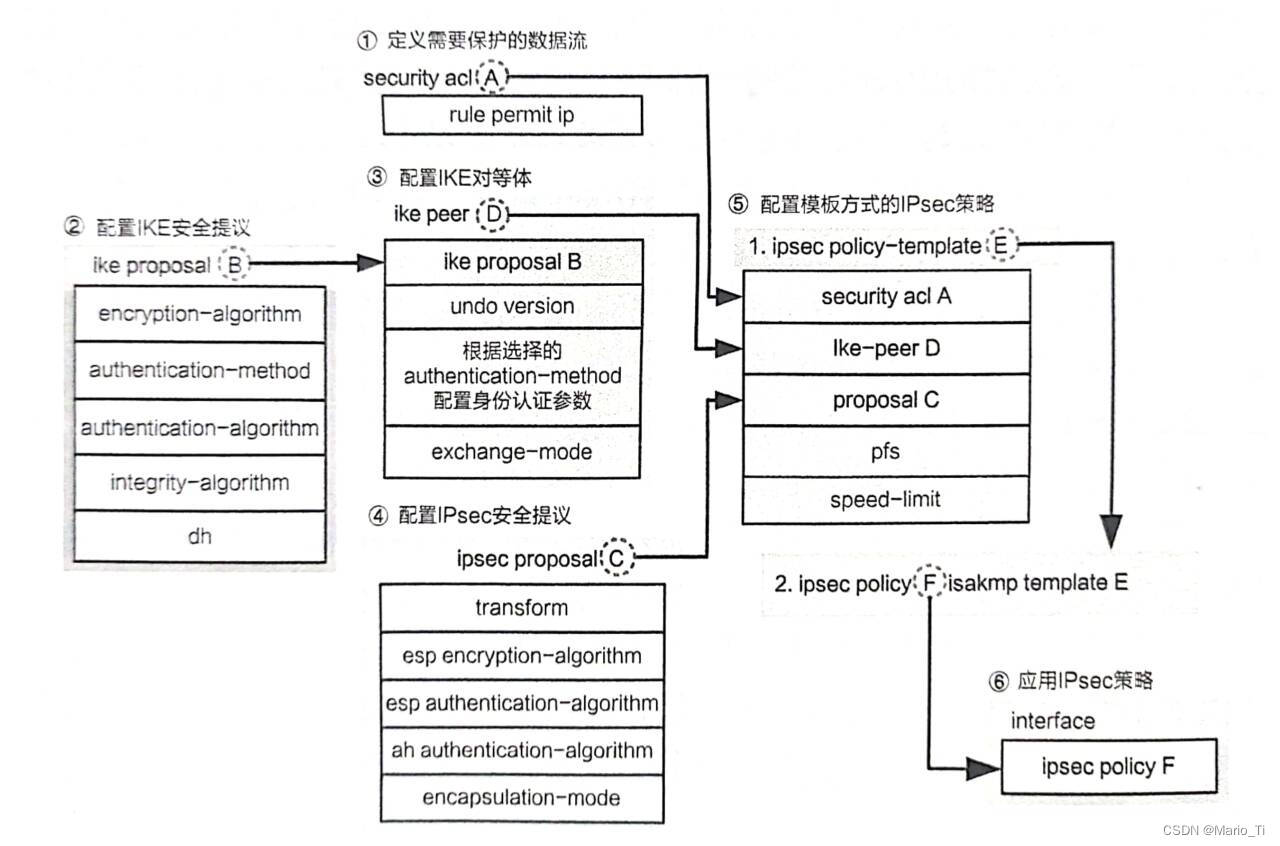
2、模板方式的IPsec策略
采用模板可以简化多条IPsec隧道建立的配置工作,但是采用模板方式时,采用模板的一端不能主动发起协商,只能作为协商响应的一方接受对端的协商请求,隧道两端不可以同时采用模板配置的方式。
模板方式的IPsec策略示意图如下所示:
此处以点到多点为例,更能体现模板方式的魅力之处,总部与分部1、2如图所示。
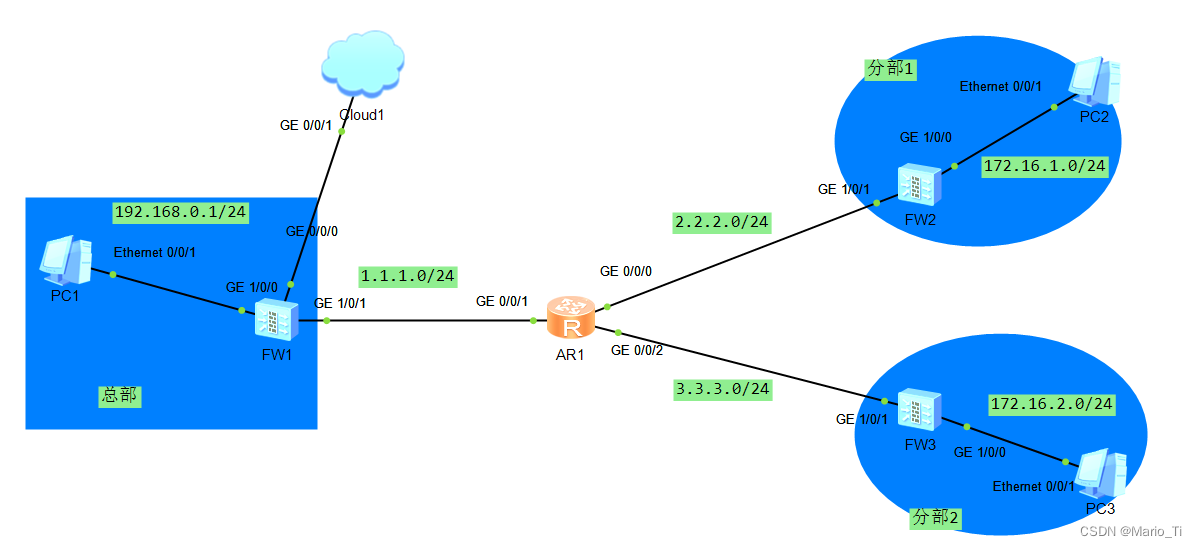
AR1基础配置:
[AR1]interface g0/0/1
[AR1-GigabitEthernet0/0/1]ip add 1.1.1.2 24
[AR1-GigabitEthernet0/0/1]quit
[AR1]interface g0/0/0
[AR1-GigabitEthernet0/0/0]ip add 2.2.2.2 24
[AR1-GigabitEthernet0/0/0]quit
[AR1]interface g0/0/2
[AR1-GigabitEthernet0/0/2]ip add 3.3.3.2 24
[AR1]ip route-static 192.168.0.0 24 1.1.1.1
[AR1]ip route-static 172.16.1.0 24 2.2.2.1
[AR1]ip route-static 172.16.2.0 24 3.3.3.1FW1基础配置:
[FW1]interface g1/0/0
[FW1-GigabitEthernet1/0/0]ip add 192.168.0.254 24
[FW1-GigabitEthernet1/0/0]quit
[FW1]interface g1/0/1
[FW1-GigabitEthernet1/0/1]ip add 1.1.1.1 24
[FW1-GigabitEthernet1/0/1]quit
[FW1]firewall zone untrust
[FW1-zone-untrust]add interface g1/0/1
[FW1-zone-untrust]quit
[FW1]firewall zone trust
[FW1-zone-trust]add interface g1/0/0
[FW1]ip route-static 172.16.1.0 24 1.1.1.2
[FW1]ip route-static 172.16.2.0 24 1.1.1.2FW2基础配置:
[FW2]interface g1/0/0
[FW2-GigabitEthernet1/0/0]ip add 172.16.1.254 24
[FW2-GigabitEthernet1/0/0]quit
[FW2]interface g1/0/1
[FW2-GigabitEthernet1/0/1]ip add 2.2.2.1 24
[FW2-GigabitEthernet1/0/1]quit
[FW2]firewall zone trust
[FW2-zone-trust]add interface g1/0/0
[FW2-zone-trust]quit
[FW2]firewall zone untrust
[FW2-zone-untrust]add interface g1/0/1
[FW2-zone-untrust]quit
[FW2]ip route-static 192.168.0.0 24 2.2.2.2FW3基础配置:
[FW3]interface g1/0/0
[FW3-GigabitEthernet1/0/0]ip add 172.16.2.254 24
[FW3-GigabitEthernet1/0/0]quit
[FW3]interface g1/0/1
[FW3-GigabitEthernet1/0/1]ip add 3.3.3.1 24
[FW3-GigabitEthernet1/0/1]quit
[FW3]firewall zone trust
[FW3-zone-trust]add interface g1/0/0
[FW3-zone-trust]quit
[FW3]firewall zone untrust
[FW3-zone-untrust]add interface g1/0/1
[FW3-zone-untrust]quit
[FW3]ip route-static 192.168.0.0 24 3.3.3.2总部采用模板方式进行配置,分部采用ISAKMP方式配置IPsec策略,若总部配置remote-address指定隧道对端IP地址端,那么总部会检查分部设备的ID(IP地址)是否包含在IP地址段中,包含则接纳请求,若没有配置remote-address,总部职能接收分部的主动访问,不验证分部,也不主动访问分支。
可见模板方式可以应付对端没有固定IP地址、没有公网IP地址的局面,当然这都是总部放弃主动访问分部为代价所获得的。
[FW1]ike proposal 10
[FW1-ike-proposal-10]quit
[FW1]ike peer a
[FW1-ike-peer-a]ike-proposal 10
[FW1-ike-peer-a]pre-shared-key test1
Info: The password you entered does not meet the minimum complexity requirement.
The password is suggested to contain at least three types of characters from the
following four groups: Uppercase letters <A-Z>; Lowercase letters <a-z>; Numera
ls <0-9>; Symbols (all characters not defined as letters or numerals), such as !
,$,#, and %.
[FW1-ike-peer-a]quit
[FW1]acl number 3000
[FW1-acl-adv-3000]rule 5 permit ip source 192.168.0.0 0.0.0.255 destination 172.16.1.0 0.0.0.255
[FW1-acl-adv-3000]rule 10 permit ip source 192.168.0.0 0.0.0.255 destination 172.16.2.0 0.0.0.255
[FW1-acl-adv-3000]quit
[FW1]ipsec proposal a
[FW1-ipsec-proposal-a]display this
2024-03-09 08:27:29.610
#
ipsec proposal a
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
return
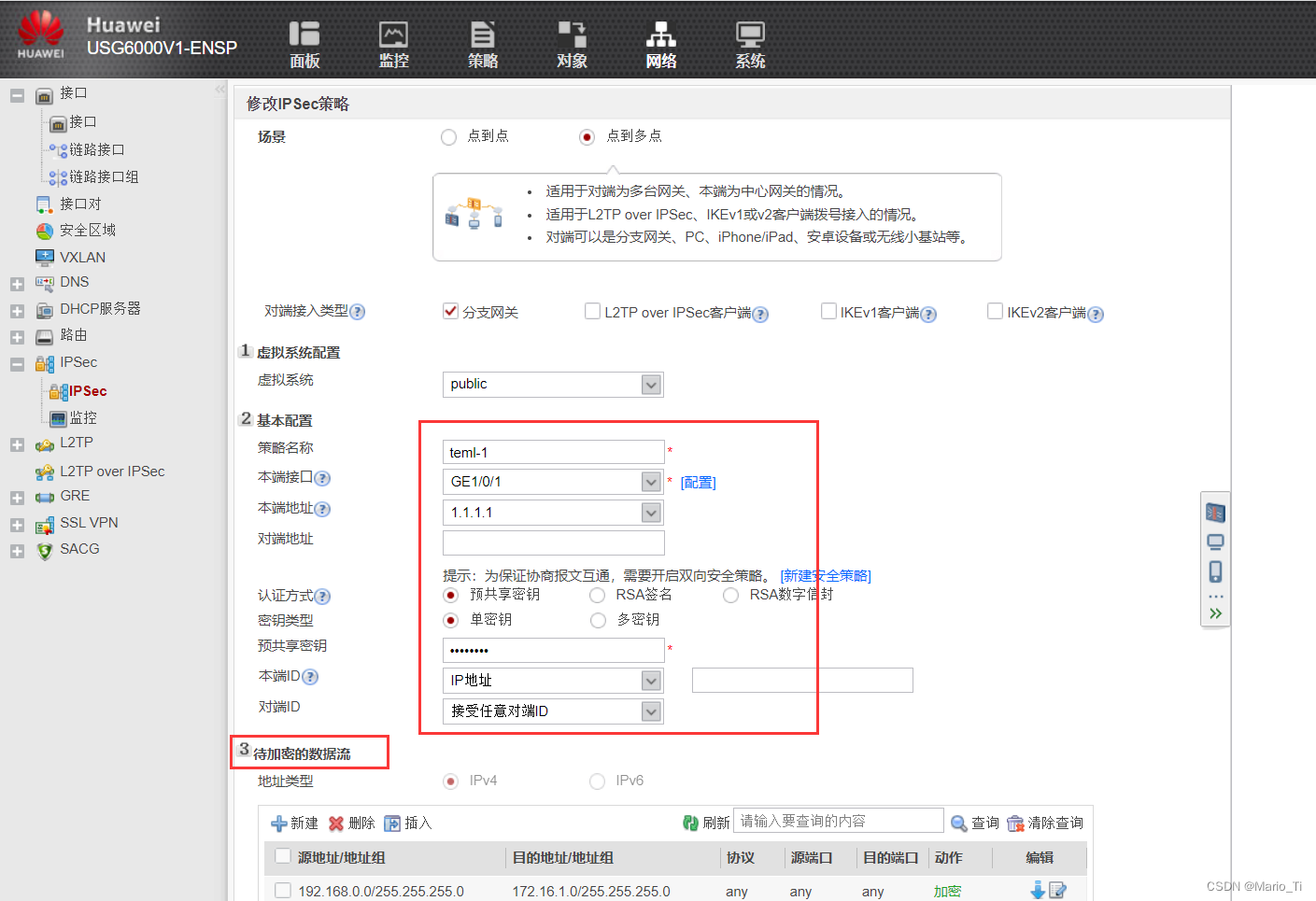
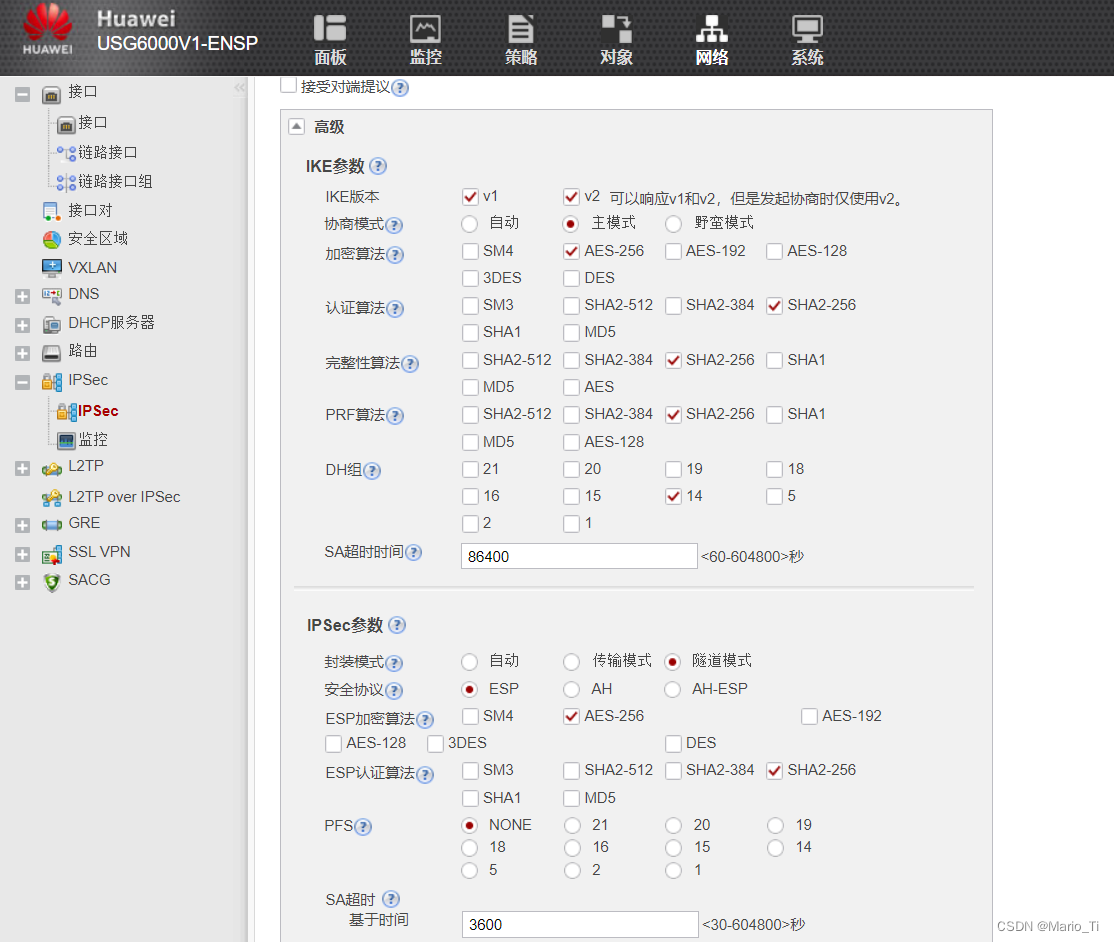
[FW1]ipsec policy-template teml 1
[FW1-ipsec-policy-templet-teml-1]display this
2024-03-09 08:42:17.640
#
ipsec policy-template teml 1
security acl 3000
ike-peer a
proposal a
#
return
[FW1]ipsec policy policy1 12 isakmp template teml
Info: The ISAKMP policy sequence number should be smaller than the template poli
cy sequence number in the policy group. Otherwise, the ISAKMP policy does not ta
ke effect.
[FW1]interface g1/0/1
[FW1-GigabitEthernet1/0/1]ipsec policy policy1
[FW2]ike proposal 10
[FW2-ike-proposal-10]quit
[FW2]ike peer a
[FW2-ike-peer-a]ike-proposal 10
[FW2-ike-peer-a]remote-address 1.1.1.1
[FW2-ike-peer-a]pre-shared-key test1
Info: The password you entered does not meet the minimum complexity requirement.
The password is suggested to contain at least three types of characters from the
following four groups: Uppercase letters <A-Z>; Lowercase letters <a-z>; Numera
ls <0-9>; Symbols (all characters not defined as letters or numerals), such as !
,$,#, and %.
[FW2-ike-peer-a]quit
[FW2]acl number 3000
[FW2-acl-adv-3000]rule 5 permit ip source 172.16.1.0 0.0.0.255 destination 192.168.0.0 0.0.0.255
[FW2-acl-adv-3000]quit
[FW2]ipsec proposal a
[FW2-ipsec-proposal-a]display this
2024-03-09 08:34:23.380
#
ipsec proposal a
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
return
[FW2-ipsec-proposal-a]quit
[FW2]ipsec policy policy1 1 isakmp
Info: The ISAKMP policy sequence number should be smaller than the template poli
cy sequence number in the policy group. Otherwise, the ISAKMP policy does not ta
ke effect.
[FW2-ipsec-policy-isakmp-policy1-1]security acl 3000
[FW2-ipsec-policy-isakmp-policy1-1]proposal a
[FW2-ipsec-policy-isakmp-policy1-1]ike-peer a
[FW2-ipsec-policy-isakmp-policy1-1]quit
[FW2]interface g1/0/1
[FW2-GigabitEthernet1/0/1]ipsec policy policy1
安全策略配置
[FW1-policy-security]display this
2024-03-09 08:47:30.710
#
security-policy
rule name tr_to_untr
source-zone trust
destination-zone untrust
source-address 192.168.0.0 mask 255.255.255.0
destination-address 172.16.1.0 mask 255.255.255.0
destination-address 172.16.2.0 mask 255.255.255.0
action permit
rule name local_to_untr
source-zone local
destination-zone untrust
source-address 1.1.1.1 mask 255.255.255.255
destination-address 2.2.2.1 mask 255.255.255.255
destination-address 3.3.3.1 mask 255.255.255.255
action permit
rule name untr_to_local
source-zone untrust
destination-zone local
source-address 2.2.2.1 mask 255.255.255.255
source-address 3.3.3.1 mask 255.255.255.255
destination-address 1.1.1.1 mask 255.255.255.255
action permit
rule name untr_to_tr
source-zone untrust
destination-zone trust
source-address 172.16.1.0 mask 255.255.255.0
source-address 172.16.2.0 mask 255.255.255.0
action permit
#
return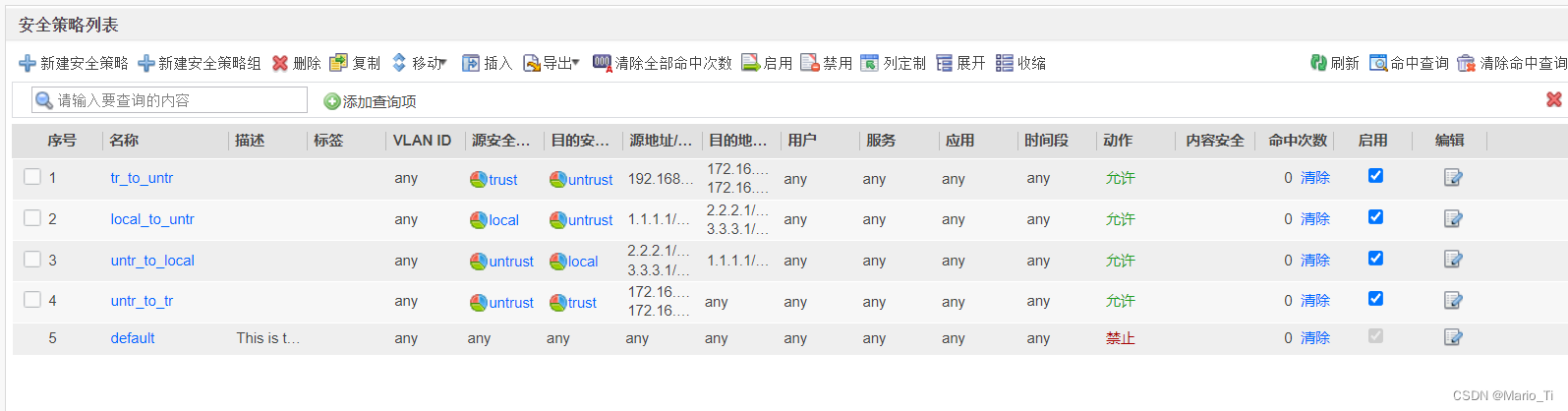
[FW2-policy-security]display this
2024-03-09 08:51:27.580
#
security-policy
rule name tr_to_untr
source-zone trust
destination-zone untrust
source-address 172.16.1.0 mask 255.255.255.0
destination-address 192.168.0.0 mask 255.255.255.0
action permit
rule name local_to_untr
source-zone local
destination-zone untrust
source-address 2.2.2.1 mask 255.255.255.255
destination-address 1.1.1.1 mask 255.255.255.255
action permit
rule name untr_to_local
source-zone untrust
destination-zone local
source-address 1.1.1.1 mask 255.255.255.255
destination-address 2.2.2.1 mask 255.255.255.255
action permit
rule name untr_to_tr
source-zone untrust
destination-zone trust
source-address 192.168.0.0 mask 255.255.255.0
destination-address 172.16.1.0 mask 255.255.255.0
action permit
#
returnFW3配置!!!可以自己动手!!!
[FW3]ike proposal 10
[FW3-ike-proposal-10]quit
[FW3]ike peer a
[FW3-ike-peer-a]ike-proposal 10
[FW3-ike-peer-a]remote-address 1.1.1.1
[FW3-ike-peer-a]pre-shared-key test1
Info: The password you entered does not meet the minimum complexity requirement.
The password is suggested to contain at least three types of characters from the
following four groups: Uppercase letters <A-Z>; Lowercase letters <a-z>; Numera
ls <0-9>; Symbols (all characters not defined as letters or numerals), such as !
,$,#, and %.
[FW3-ike-peer-a]quit
[FW3]acl number 3000
[FW3-acl-adv-3000]rule 5 permit ip source 172.16.2.0 0.0.0.255 destination 192.1
68.0.0 0.0.0.255
[FW3-acl-adv-3000]quit
[FW3]ipsec proposal a
[FW3-ipsec-proposal-a]quit
[FW3]ipsec policy policy1 1 isakmp
Info: The ISAKMP policy sequence number should be smaller than the template poli
cy sequence number in the policy group. Otherwise, the ISAKMP policy does not ta
ke effect.
[FW3-ipsec-policy-isakmp-policy1-1]security acl 3000
[FW3-ipsec-policy-isakmp-policy1-1]proposal a
[FW3-ipsec-policy-isakmp-policy1-1]ike-peer a
[FW3-ipsec-policy-isakmp-policy1-1]quit
[FW3]interface g1/0/1
[FW3-GigabitEthernet1/0/1]ipsec policy policy1
[FW3-policy-security]display this
2024-03-09 08:56:25.110
#
security-policy
rule name tr_to_untr
source-zone trust
destination-zone untrust
source-address 172.16.2.0 mask 255.255.255.0
destination-address 192.168.0.0 mask 255.255.255.0
action permit
rule name local_to_untr
source-zone local
destination-zone untrust
source-address 3.3.3.1 mask 255.255.255.255
destination-address 1.1.1.1 mask 255.255.255.255
action permit
rule name untr_to_local
source-zone untrust
destination-zone local
source-address 1.1.1.1 mask 255.255.255.255
destination-address 3.3.3.1 mask 255.255.255.255
action permit
rule name untr_to_tr
source-zone untrust
destination-zone trust
source-address 192.168.0.0 mask 255.255.255.0
destination-address 172.16.2.0 mask 255.255.255.0
action permit
#
return经过测试可知,分部网络均可以访问总部,但是总部不可以主动访问分部,这就是模板方式,采用模板的一端不能主动发起协商,只能作为协商响应的一方接受对端的协商请求,隧道两端不可以同时采用模板配置的方式。
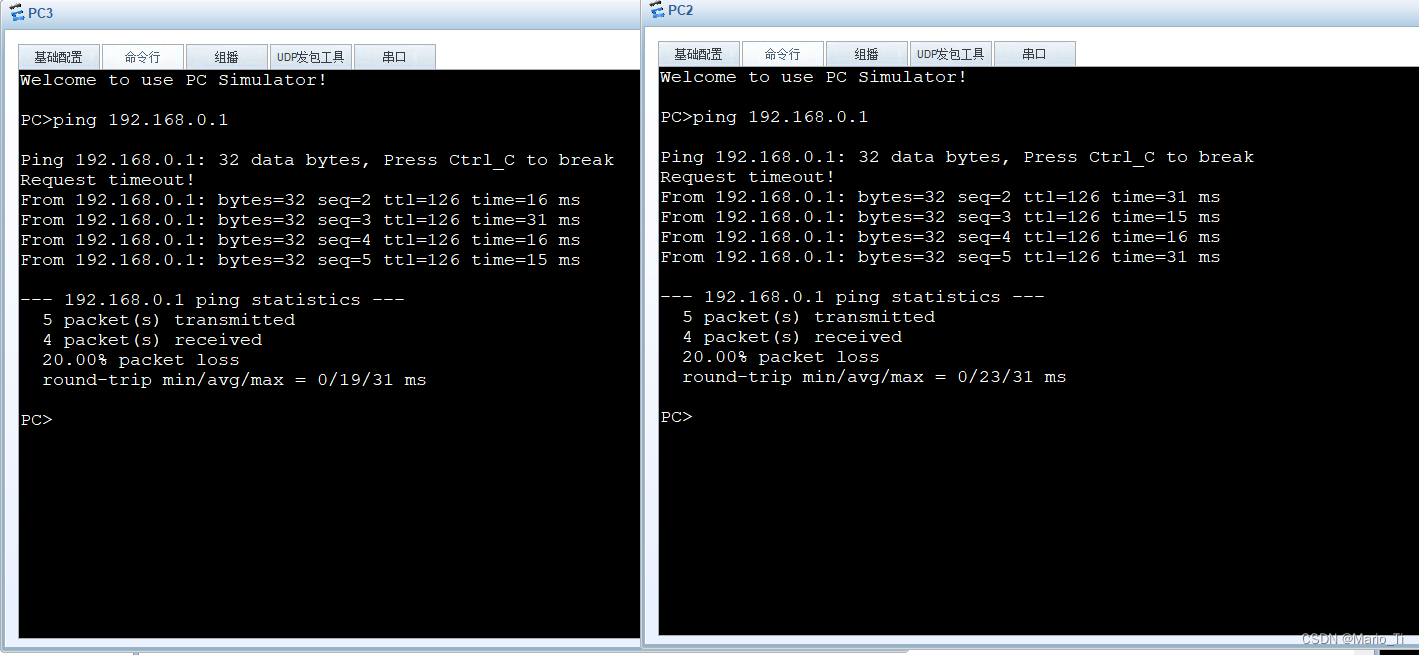
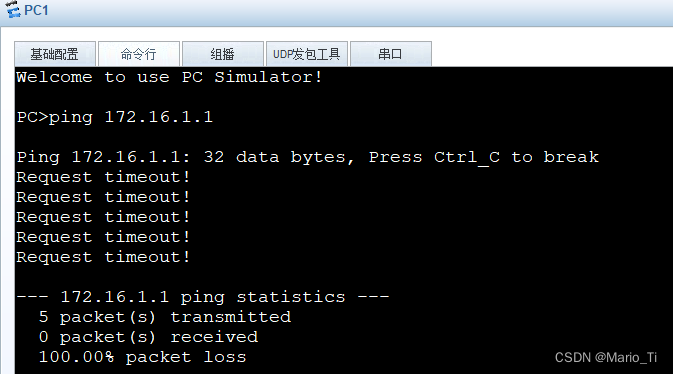
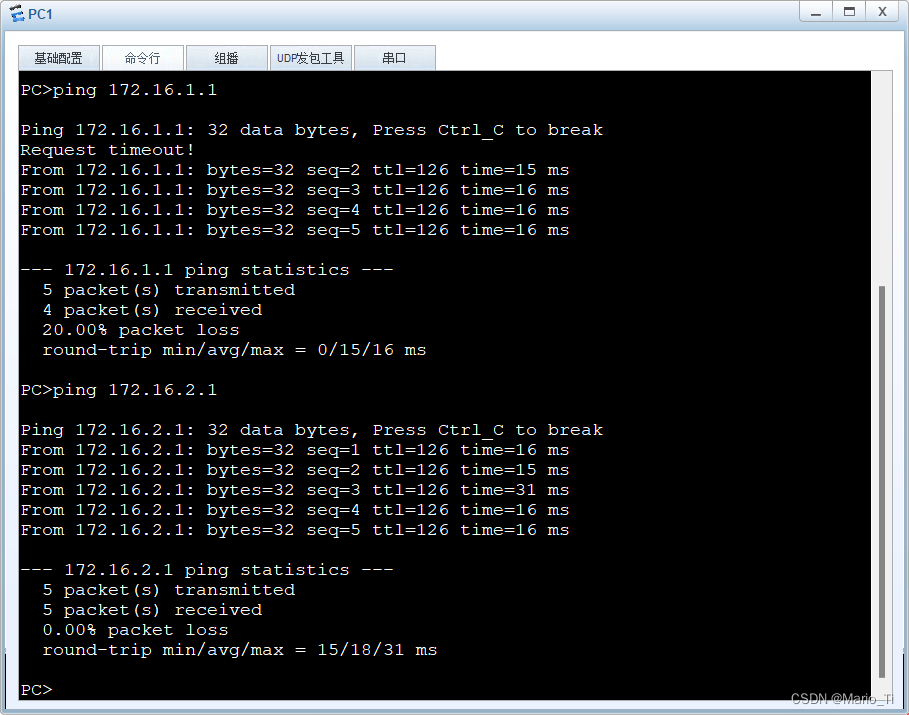
当分部访问总部,此时的总部可知。
抓包分析,可知数据均加密。
参考资料:防火墙和VPN技术与实践——李学昭