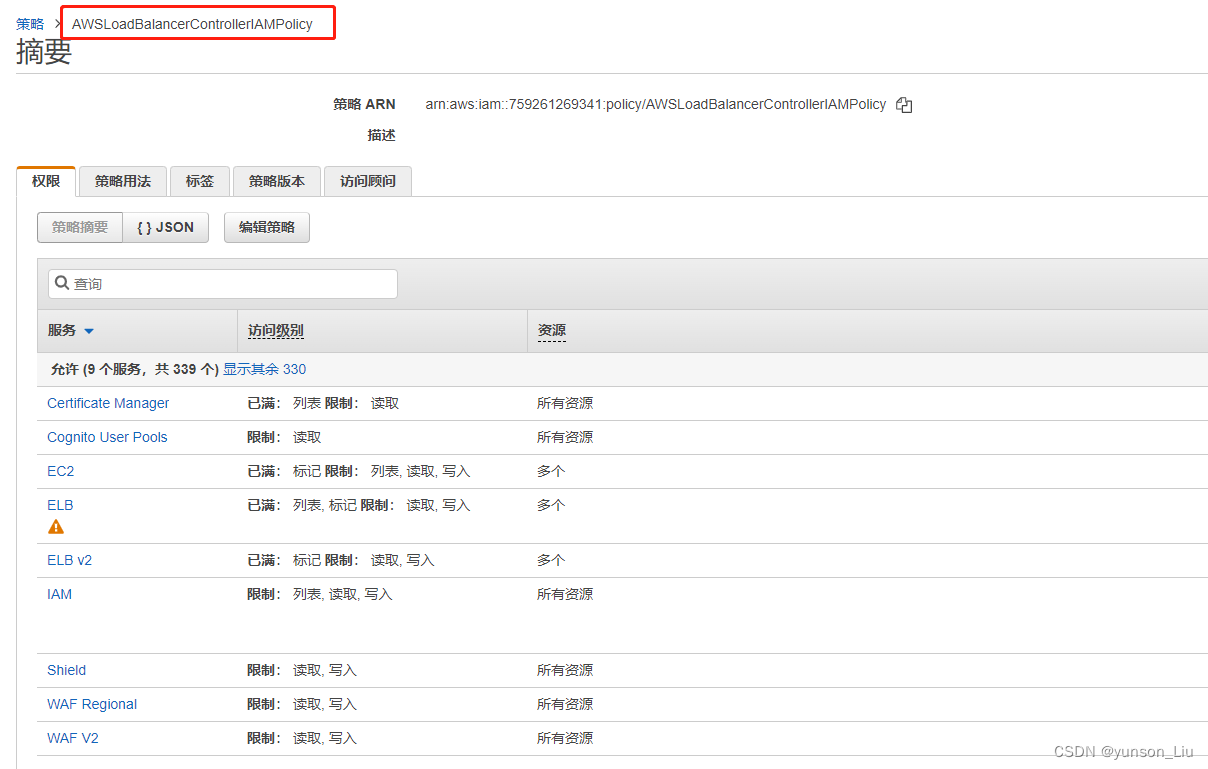
1、创建AWS Load Balancer Controller 的 IAM 策略
亚马逊相关文档
下载地址
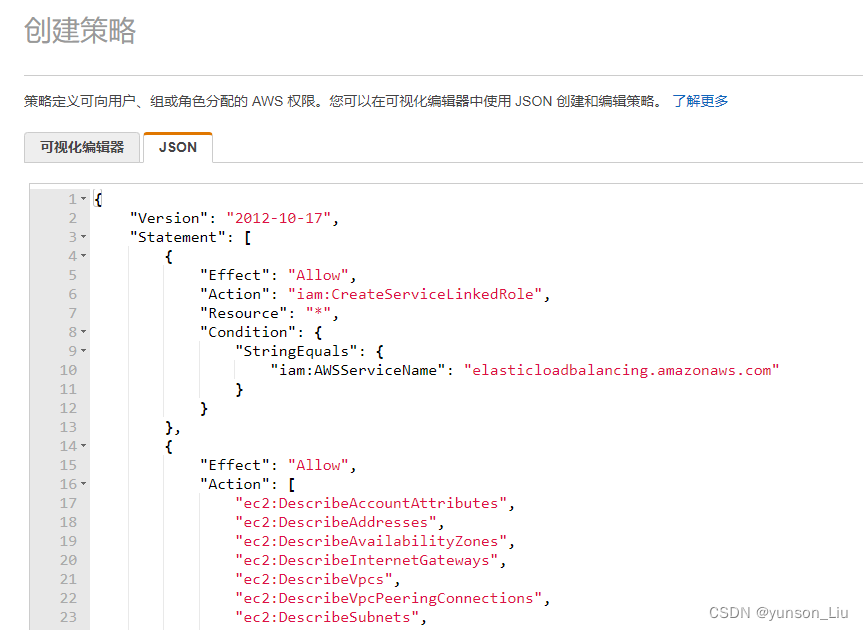
打开 策略 点击 创建策略 打开 IAM_Policy.json 复制内容粘贴到 json
点击下一步:标签
然后一直下一步 在下图中名称填写 AWSLoadBalancerControllerIAMPolicy 你也可以自定义名称。然后创建策略。
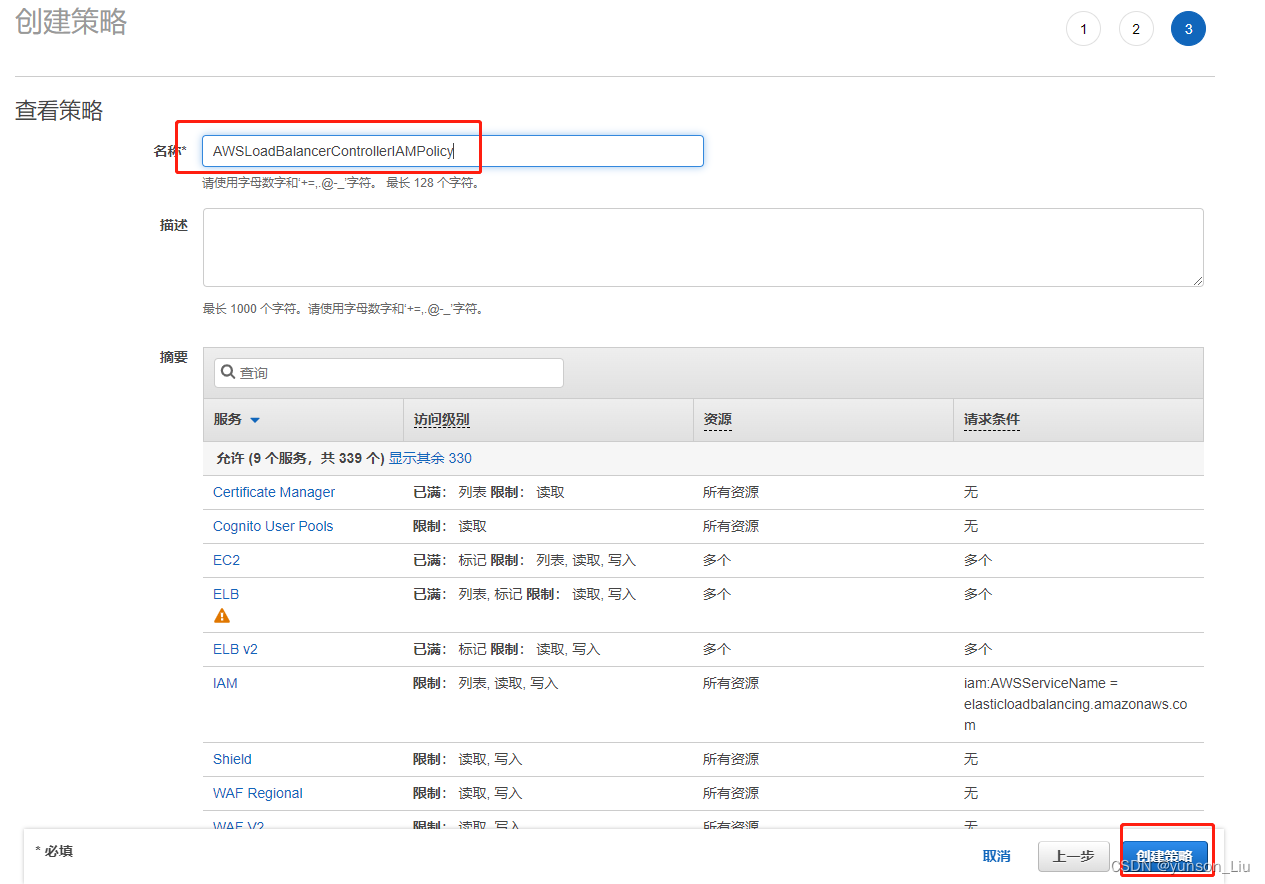
至此,策略创建成功
json文本内容如下
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"iam:CreateServiceLinkedRole",
"ec2:DescribeAccountAttributes",
"ec2:DescribeAddresses",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeInternetGateways",
"ec2:DescribeVpcs",
"ec2:DescribeSubnets",
"ec2:DescribeSecurityGroups",
"ec2:DescribeInstances",
"ec2:DescribeNetworkInterfaces",
"ec2:DescribeTags",
"ec2:GetCoipPoolUsage",
"ec2:DescribeCoipPools",
"elasticloadbalancing:DescribeLoadBalancers",
"elasticloadbalancing:DescribeLoadBalancerAttributes",
"elasticloadbalancing:DescribeListeners",
"elasticloadbalancing:DescribeListenerCertificates",
"elasticloadbalancing:DescribeSSLPolicies",
"elasticloadbalancing:DescribeRules",
"elasticloadbalancing:DescribeTargetGroups",
"elasticloadbalancing:DescribeTargetGroupAttributes",
"elasticloadbalancing:DescribeTargetHealth",
"elasticloadbalancing:DescribeTags"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"cognito-idp:DescribeUserPoolClient",
"acm:ListCertificates",
"acm:DescribeCertificate",
"iam:ListServerCertificates",
"iam:GetServerCertificate",
"waf-regional:GetWebACL",
"waf-regional:GetWebACLForResource",
"waf-regional:AssociateWebACL",
"waf-regional:DisassociateWebACL",
"wafv2:GetWebACL",
"wafv2:GetWebACLForResource",
"wafv2:AssociateWebACL",
"wafv2:DisassociateWebACL",
"shield:GetSubscriptionState",
"shield:DescribeProtection",
"shield:CreateProtection",
"shield:DeleteProtection"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"ec2:AuthorizeSecurityGroupIngress",
"ec2:RevokeSecurityGroupIngress"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"ec2:CreateSecurityGroup"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"ec2:CreateTags"
],
"Resource": "arn:aws-cn:ec2:*:*:security-group/*",
"Condition": {
"StringEquals": {
"ec2:CreateAction": "CreateSecurityGroup"
},
"Null": {
"aws:RequestTag/elbv2.k8s.aws/cluster": "false"
}
}
},
{
"Effect": "Allow",
"Action": [
"ec2:CreateTags",
"ec2:DeleteTags"
],
"Resource": "arn:aws-cn:ec2:*:*:security-group/*",
"Condition": {
"Null": {
"aws:RequestTag/elbv2.k8s.aws/cluster": "true",
"aws:ResourceTag/elbv2.k8s.aws/cluster": "false"
}
}
},
{
"Effect": "Allow",
"Action": [
"ec2:AuthorizeSecurityGroupIngress",
"ec2:RevokeSecurityGroupIngress",
"ec2:DeleteSecurityGroup"
],
"Resource": "*",
"Condition": {
"Null": {
"aws:ResourceTag/elbv2.k8s.aws/cluster": "false"
}
}
},
{
"Effect": "Allow",
"Action": [
"elasticloadbalancing:CreateLoadBalancer",
"elasticloadbalancing:CreateTargetGroup"
],
"Resource": "*",
"Condition": {
"Null": {
"aws:RequestTag/elbv2.k8s.aws/cluster": "false"
}
}
},
{
"Effect": "Allow",
"Action": [
"elasticloadbalancing:CreateListener",
"elasticloadbalancing:DeleteListener",
"elasticloadbalancing:CreateRule",
"elasticloadbalancing:DeleteRule"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"elasticloadbalancing:AddTags",
"elasticloadbalancing:RemoveTags"
],
"Resource": [
"arn:aws-cn:elasticloadbalancing:*:*:targetgroup/*/*",
"arn:aws-cn:elasticloadbalancing:*:*:loadbalancer/net/*/*",
"arn:aws-cn:elasticloadbalancing:*:*:loadbalancer/app/*/*"
],
"Condition": {
"Null": {
"aws:RequestTag/elbv2.k8s.aws/cluster": "true",
"aws:ResourceTag/elbv2.k8s.aws/cluster": "false"
}
}
},
{
"Effect": "Allow",
"Action": [
"elasticloadbalancing:AddTags",
"elasticloadbalancing:RemoveTags"
],
"Resource": [
"arn:aws-cn:elasticloadbalancing:*:*:listener/net/*/*/*",
"arn:aws-cn:elasticloadbalancing:*:*:listener/app/*/*/*",
"arn:aws-cn:elasticloadbalancing:*:*:listener-rule/net/*/*/*",
"arn:aws-cn:elasticloadbalancing:*:*:listener-rule/app/*/*/*"
]
},
{
"Effect": "Allow",
"Action": [
"elasticloadbalancing:ModifyLoadBalancerAttributes",
"elasticloadbalancing:SetIpAddressType",
"elasticloadbalancing:SetSecurityGroups",
"elasticloadbalancing:SetSubnets",
"elasticloadbalancing:DeleteLoadBalancer",
"elasticloadbalancing:ModifyTargetGroup",
"elasticloadbalancing:ModifyTargetGroupAttributes",
"elasticloadbalancing:DeleteTargetGroup"
],
"Resource": "*",
"Condition": {
"Null": {
"aws:ResourceTag/elbv2.k8s.aws/cluster": "false"
}
}
},
{
"Effect": "Allow",
"Action": [
"elasticloadbalancing:RegisterTargets",
"elasticloadbalancing:DeregisterTargets"
],
"Resource": "arn:aws-cn:elasticloadbalancing:*:*:targetgroup/*/*"
},
{
"Effect": "Allow",
"Action": [
"elasticloadbalancing:SetWebAcl",
"elasticloadbalancing:ModifyListener",
"elasticloadbalancing:AddListenerCertificates",
"elasticloadbalancing:RemoveListenerCertificates",
"elasticloadbalancing:ModifyRule"
],
"Resource": "*"
}
]
}
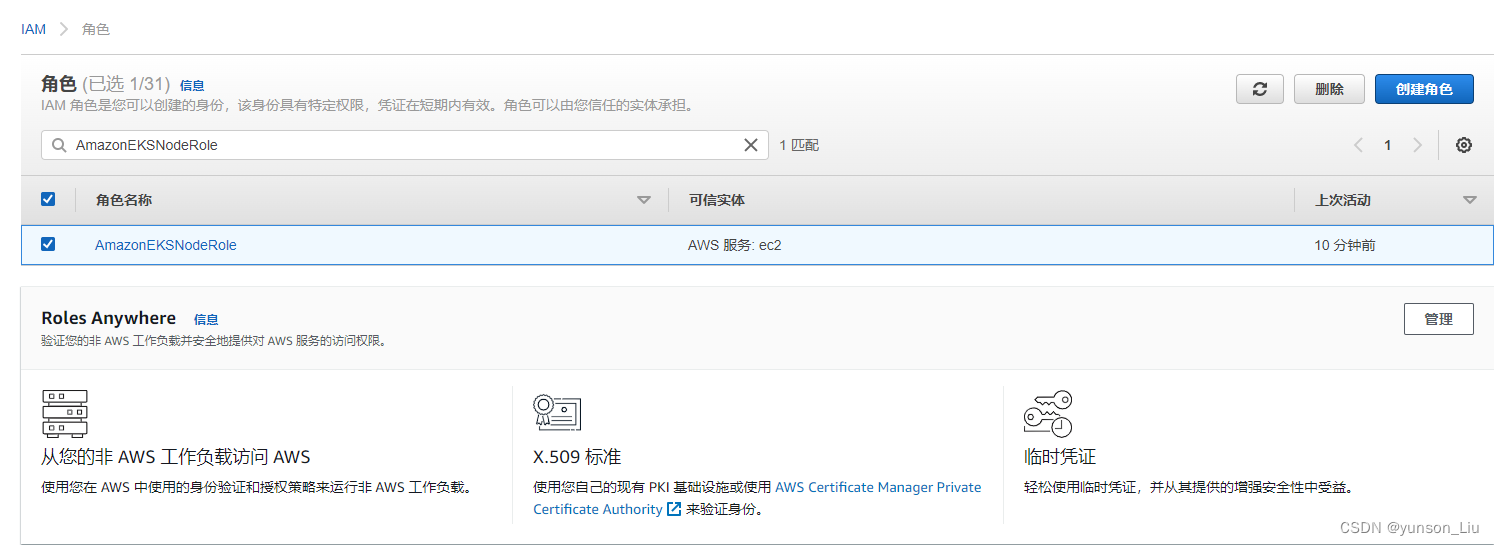
2、赋予 EKS node 权限
在 角色 中搜索 AmazonEKSNodeRole 找到你对应的 EKS 集群 如下图
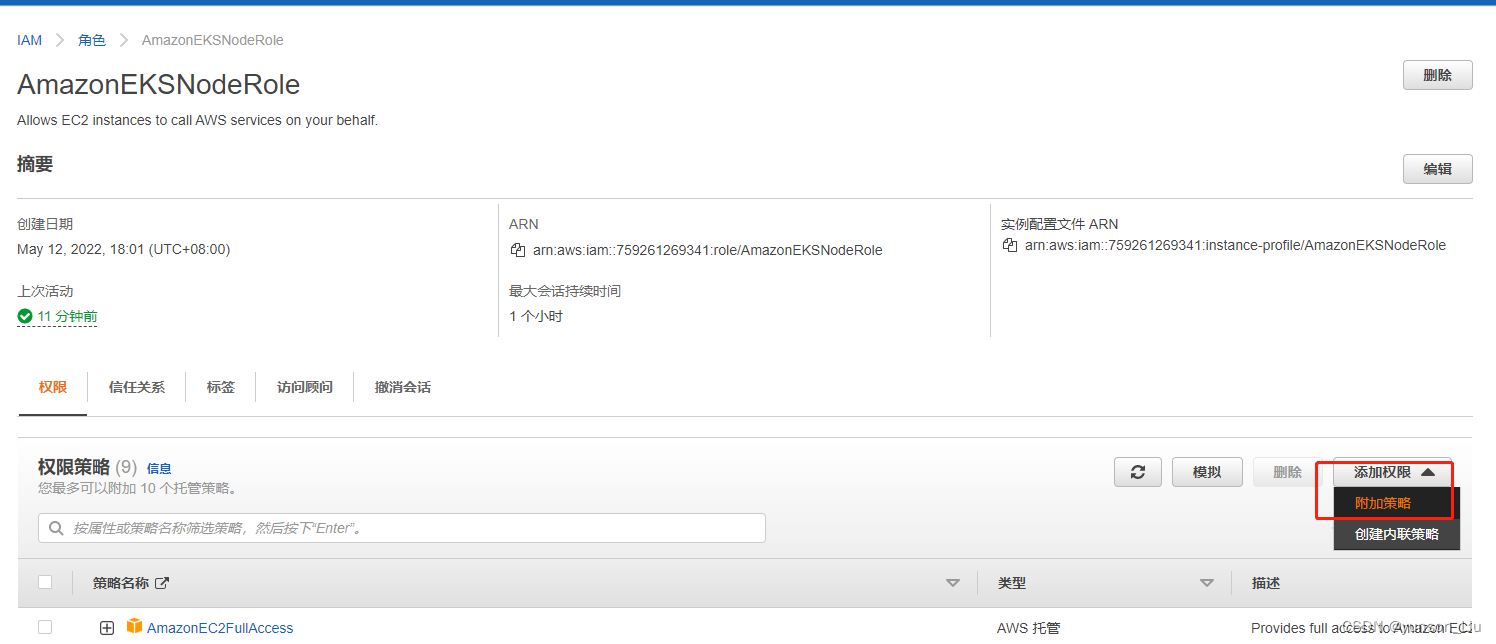
然后点击该角色-- 点击附加策略
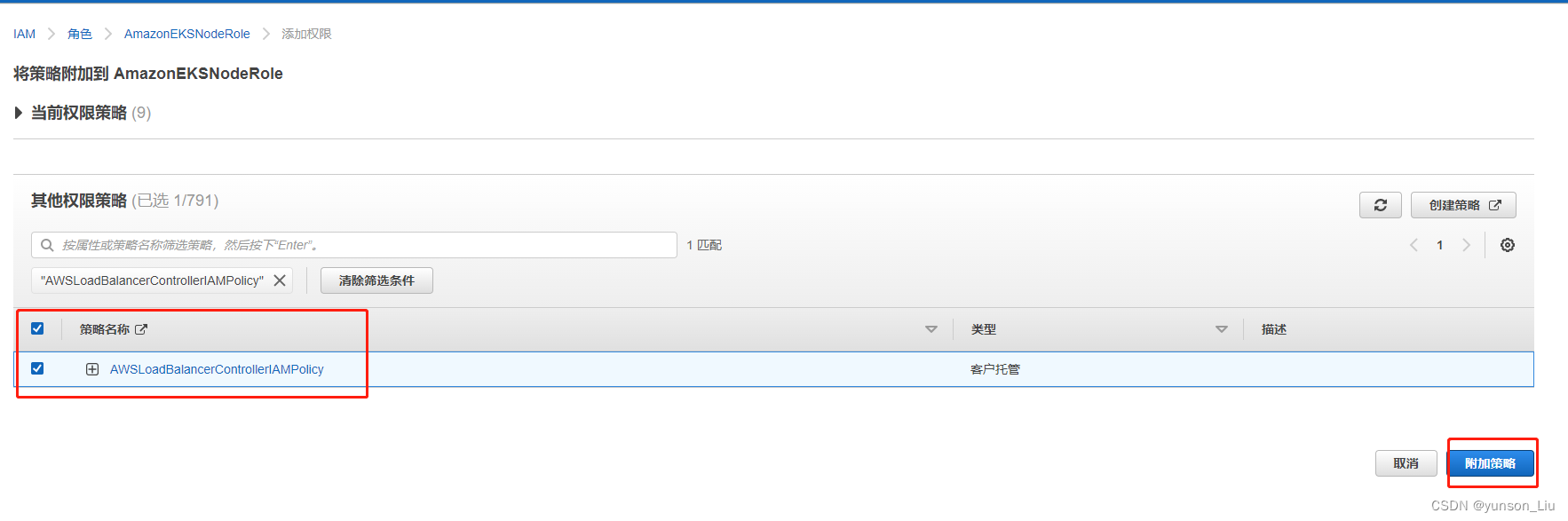
在搜索框内 输入刚才创建的策略名称 然后选中,点击最下边的附加策略。
我的策略名称为:AWSLoadBalancerControllerIAMPolicy
3、在 EKS 中安装 AWS Load Balancer Controller
安装证书管理器
[root@ip-172-93-6-200 ~]# kubectl apply --validate=false -f https://github.com/jetstack/cert-manager/releases/download/v1.5.3/cert-manager.yaml
customresourcedefinition.apiextensions.k8s.io/certificaterequests.cert-manager.io created
customresourcedefinition.apiextensions.k8s.io/certificates.cert-manager.io created
customresourcedefinition.apiextensions.k8s.io/challenges.acme.cert-manager.io created
customresourcedefinition.apiextensions.k8s.io/clusterissuers.cert-manager.io created
customresourcedefinition.apiextensions.k8s.io/issuers.cert-manager.io created
customresourcedefinition.apiextensions.k8s.io/orders.acme.cert-manager.io created
namespace/cert-manager created
serviceaccount/cert-manager-cainjector created
serviceaccount/cert-manager created
serviceaccount/cert-manager-webhook created
clusterrole.rbac.authorization.k8s.io/cert-manager-cainjector created
clusterrole.rbac.authorization.k8s.io/cert-manager-controller-issuers created
clusterrole.rbac.authorization.k8s.io/cert-manager-controller-clusterissuers created
clusterrole.rbac.authorization.k8s.io/cert-manager-controller-certificates created
clusterrole.rbac.authorization.k8s.io/cert-manager-controller-orders created
clusterrole.rbac.authorization.k8s.io/cert-manager-controller-challenges created
clusterrole.rbac.authorization.k8s.io/cert-manager-controller-ingress-shim created
clusterrole.rbac.authorization.k8s.io/cert-manager-view created
clusterrole.rbac.authorization.k8s.io/cert-manager-edit created
clusterrole.rbac.authorization.k8s.io/cert-manager-controller-approve:cert-manager-io created
clusterrole.rbac.authorization.k8s.io/cert-manager-controller-certificatesigningrequests created
clusterrole.rbac.authorization.k8s.io/cert-manager-webhook:subjectaccessreviews created
clusterrolebinding.rbac.authorization.k8s.io/cert-manager-cainjector created
clusterrolebinding.rbac.authorization.k8s.io/cert-manager-controller-issuers created
clusterrolebinding.rbac.authorization.k8s.io/cert-manager-controller-clusterissuers created
clusterrolebinding.rbac.authorization.k8s.io/cert-manager-controller-certificates created
clusterrolebinding.rbac.authorization.k8s.io/cert-manager-controller-orders created
clusterrolebinding.rbac.authorization.k8s.io/cert-manager-controller-challenges created
clusterrolebinding.rbac.authorization.k8s.io/cert-manager-controller-ingress-shim created
clusterrolebinding.rbac.authorization.k8s.io/cert-manager-controller-approve:cert-manager-io created
clusterrolebinding.rbac.authorization.k8s.io/cert-manager-controller-certificatesigningrequests created
clusterrolebinding.rbac.authorization.k8s.io/cert-manager-webhook:subjectaccessreviews created
role.rbac.authorization.k8s.io/cert-manager-cainjector:leaderelection created
role.rbac.authorization.k8s.io/cert-manager:leaderelection created
role.rbac.authorization.k8s.io/cert-manager-webhook:dynamic-serving created
rolebinding.rbac.authorization.k8s.io/cert-manager-cainjector:leaderelection created
rolebinding.rbac.authorization.k8s.io/cert-manager:leaderelection created
rolebinding.rbac.authorization.k8s.io/cert-manager-webhook:dynamic-serving created
service/cert-manager created
service/cert-manager-webhook created
deployment.apps/cert-manager-cainjector created
deployment.apps/cert-manager created
deployment.apps/cert-manager-webhook created
mutatingwebhookconfiguration.admissionregistration.k8s.io/cert-manager-webhook created
validatingwebhookconfiguration.admissionregistration.k8s.io/cert-manager-webhook created
4、部署 YAML
下载负载平衡器控制器的规范。
[root@ip-172-93-6-200 ~]# cd /etc/gamefi/
[root@ip-172-93-6-200 gamefi]# ls
business-client.yaml system.yaml
[root@ip-172-93-6-200 gamefi]# wget https://github.com/kubernetes-sigs/aws-load-balancer-controller/releases/download/v2.3.1/v2_3_1_full.yaml
--2022-11-14 10:24:00-- https://github.com/kubernetes-sigs/aws-load-balancer-controller/releases/download/v2.3.1/v2_3_1_full.yaml
Resolving github.com (github.com)... 20.205.243.166
Connecting to github.com (github.com)|20.205.243.166|:443... connected.
HTTP request sent, awaiting response... 302 Found
Location: https://objects.githubusercontent.com/github-production-release-asset-2e65be/84610043/e1412997-05df-48e5-83e4-4a0e9edcc0c7?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20221114%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20221114T022400Z&X-Amz-Expires=300&X-Amz-Signature=ba9ac04cf9cc0aba453ddf304598535308986187c8cf05b0a153462545efa857&X-Amz-SignedHeaders=host&actor_id=0&key_id=0&repo_id=84610043&response-content-disposition=attachment%3B%20filename%3Dv2_3_1_full.yaml&response-content-type=application%2Foctet-stream [following]
--2022-11-14 10:24:00-- https://objects.githubusercontent.com/github-production-release-asset-2e65be/84610043/e1412997-05df-48e5-83e4-4a0e9edcc0c7?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20221114%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20221114T022400Z&X-Amz-Expires=300&X-Amz-Signature=ba9ac04cf9cc0aba453ddf304598535308986187c8cf05b0a153462545efa857&X-Amz-SignedHeaders=host&actor_id=0&key_id=0&repo_id=84610043&response-content-disposition=attachment%3B%20filename%3Dv2_3_1_full.yaml&response-content-type=application%2Foctet-stream
Resolving objects.githubusercontent.com (objects.githubusercontent.com)... 185.199.109.133, 185.199.110.133, 185.199.111.133, ...
Connecting to objects.githubusercontent.com (objects.githubusercontent.com)|185.199.109.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 31767 (31K) [application/octet-stream]
Saving to: ‘v2_3_1_full.yaml’
100%[==============================================================================================================================================================================================================>] 31,767 --.-K/s in 0s
2022-11-14 10:24:01 (97.5 MB/s) - ‘v2_3_1_full.yaml’ saved [31767/31767]
5、编辑保存的 yaml 文件,转到部署规范,并将控制器 --cluster-name arg 值设置为您的 EKS 集群名称
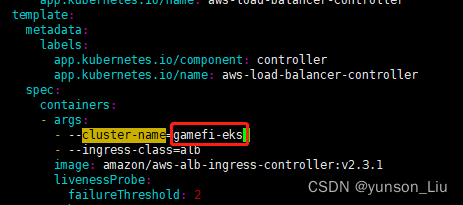
如果您为服务账户使用 IAM 角色,我们建议您从 yaml 规范中删除 ServiceAccount。如果您从 yaml 规范中删除安装部分,这将保留 eksctl 创建的 iamserviceaccount。
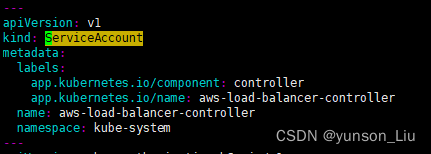
[root@ip-172-93-6-200 gamefi]# vim v2_3_1_full.yaml
---
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/name: aws-load-balancer-controller
name: aws-load-balancer-controller
namespace: kube-system
应用 yaml 文件
[root@ip-172-93-6-200 gamefi]# kubectl apply -f v2_3_1_full.yaml
customresourcedefinition.apiextensions.k8s.io/ingressclassparams.elbv2.k8s.aws created
customresourcedefinition.apiextensions.k8s.io/targetgroupbindings.elbv2.k8s.aws created
role.rbac.authorization.k8s.io/aws-load-balancer-controller-leader-election-role created
clusterrole.rbac.authorization.k8s.io/aws-load-balancer-controller-role created
rolebinding.rbac.authorization.k8s.io/aws-load-balancer-controller-leader-election-rolebinding created
clusterrolebinding.rbac.authorization.k8s.io/aws-load-balancer-controller-rolebinding created
service/aws-load-balancer-webhook-service created
deployment.apps/aws-load-balancer-controller created
certificate.cert-manager.io/aws-load-balancer-serving-cert created
issuer.cert-manager.io/aws-load-balancer-selfsigned-issuer created
mutatingwebhookconfiguration.admissionregistration.k8s.io/aws-load-balancer-webhook created
validatingwebhookconfiguration.admissionregistration.k8s.io/aws-load-balancer-webhook created
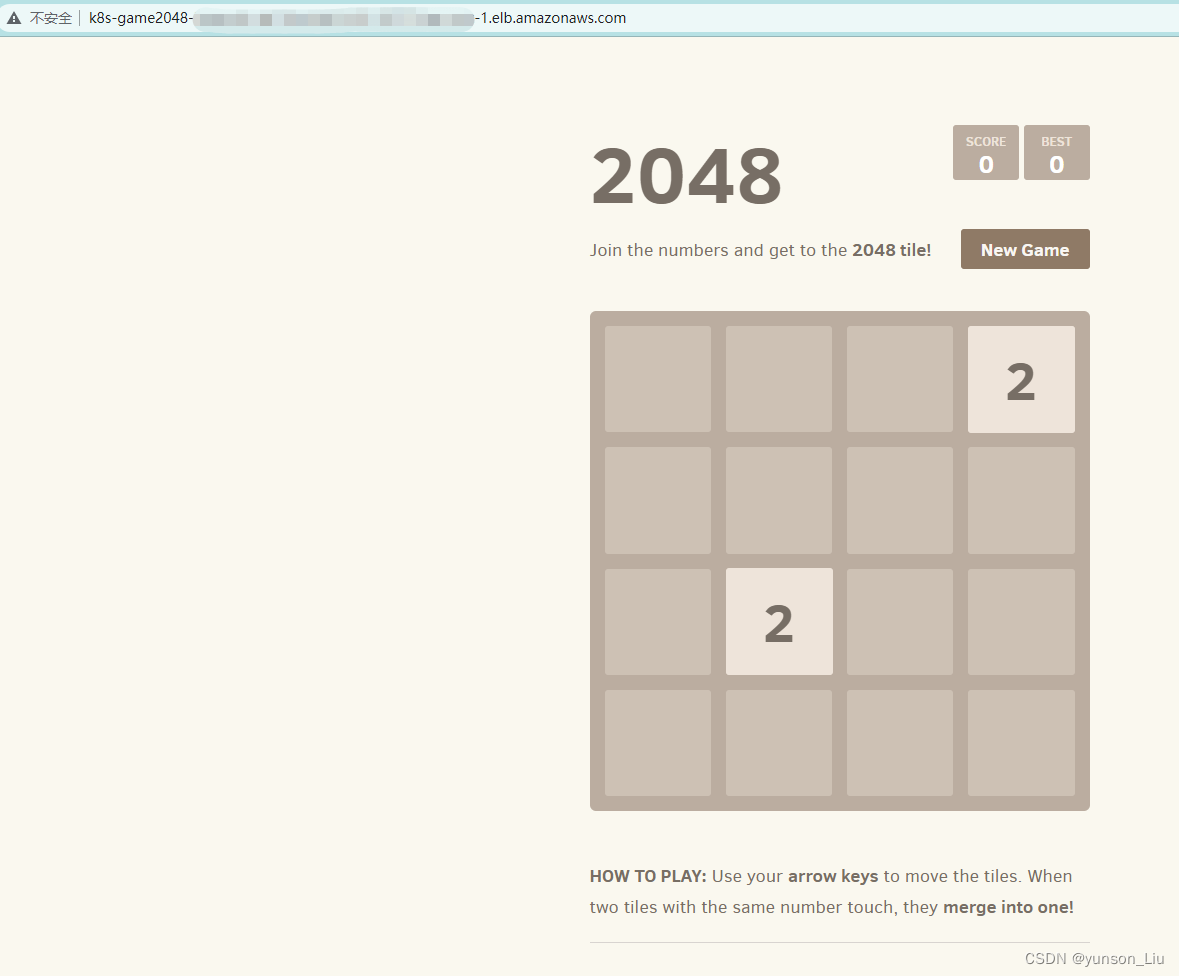
6、部署示例应用程序
将游戏 2048 部署为示例应用程序,以确认作为入口对象的结果,Amazon负载均衡器控制器是否会创建 Amazon ALB。
出现报错
错误一:
[root@ip-172-93-6-200 gamefi]# kubectl logs --tail 100 aws-load-balancer-controller-957d4466-kj26d -n kube-system
{"level":"info","ts":1668394482.8632996,"msg":"version","GitVersion":"v2.3.1","GitCommit":"1d492cb8648b2053086761140d9db9236f867237","BuildDate":"2021-12-08T18:13:11+0000"}
{"level":"info","ts":1668394482.9612875,"logger":"controller-runtime.metrics","msg":"metrics server is starting to listen","addr":":8080"}
{"level":"error","ts":1668394482.964263,"logger":"setup","msg":"unable to create controller","controller":"Ingress","error":"the server could not find the requested resource"}
解决办法
换成更高的版本2.4.5
[root@ip-172-93-6-200 gamefi]# kubectl replace --force -f v2_4_5_full.yaml
customresourcedefinition.apiextensions.k8s.io "ingressclassparams.elbv2.k8s.aws" deleted
customresourcedefinition.apiextensions.k8s.io "targetgroupbindings.elbv2.k8s.aws" deleted
serviceaccount "aws-load-balancer-controller" deleted
role.rbac.authorization.k8s.io "aws-load-balancer-controller-leader-election-role" deleted
clusterrole.rbac.authorization.k8s.io "aws-load-balancer-controller-role" deleted
rolebinding.rbac.authorization.k8s.io "aws-load-balancer-controller-leader-election-rolebinding" deleted
clusterrolebinding.rbac.authorization.k8s.io "aws-load-balancer-controller-rolebinding" deleted
service "aws-load-balancer-webhook-service" deleted
deployment.apps "aws-load-balancer-controller" deleted
certificate.cert-manager.io "aws-load-balancer-serving-cert" deleted
issuer.cert-manager.io "aws-load-balancer-selfsigned-issuer" deleted
mutatingwebhookconfiguration.admissionregistration.k8s.io "aws-load-balancer-webhook" deleted
validatingwebhookconfiguration.admissionregistration.k8s.io "aws-load-balancer-webhook" deleted
ingressclass.networking.k8s.io "alb" deleted
customresourcedefinition.apiextensions.k8s.io/ingressclassparams.elbv2.k8s.aws replaced
customresourcedefinition.apiextensions.k8s.io/targetgroupbindings.elbv2.k8s.aws replaced
serviceaccount/aws-load-balancer-controller replaced
role.rbac.authorization.k8s.io/aws-load-balancer-controller-leader-election-role replaced
clusterrole.rbac.authorization.k8s.io/aws-load-balancer-controller-role replaced
rolebinding.rbac.authorization.k8s.io/aws-load-balancer-controller-leader-election-rolebinding replaced
clusterrolebinding.rbac.authorization.k8s.io/aws-load-balancer-controller-rolebinding replaced
service/aws-load-balancer-webhook-service replaced
deployment.apps/aws-load-balancer-controller replaced
certificate.cert-manager.io/aws-load-balancer-serving-cert replaced
issuer.cert-manager.io/aws-load-balancer-selfsigned-issuer replaced
mutatingwebhookconfiguration.admissionregistration.k8s.io/aws-load-balancer-webhook replaced
validatingwebhookconfiguration.admissionregistration.k8s.io/aws-load-balancer-webhook replaced
ingressclass.networking.k8s.io/alb replaced
错误二:
{"level":"info","ts":1668397162.7676105,"logger":"controller.service","msg":"Starting workers","worker count":3}
{"level":"info","ts":1668397162.7676473,"logger":"controller.targetGroupBinding","msg":"Starting workers","reconciler group":"elbv2.k8s.aws","reconciler kind":"TargetGroupBinding","worker count":3}
{"level":"info","ts":1668397162.7689776,"logger":"controller.ingress","msg":"Starting workers","worker count":3}
{"level":"error","ts":1668397163.0093007,"logger":"controller.ingress","msg":"Reconciler error","name":"ingress-2048","namespace":"default","error":"couldn't auto-discover subnets: unable to discover at least one subnet"}
{"level":"error","ts":1668397163.0816932,"logger":"controller.ingress","msg":"Reconciler error","name":"ingress-2048","namespace":"default","error":"couldn't auto-discover subnets: unable to discover at least one subnet"}
{"level":"error","ts":1668397163.1536942,"logger":"controller.ingress","msg":"Reconciler error","name":"ingress-2048","namespace":"default","error":"couldn't auto-discover subnets: unable to discover at least one subnet"}
{"level":"error","ts":1668397163.239786,"logger":"controller.ingress","msg":"Reconciler error","name":"ingress-2048","namespace":"default","error":"couldn't auto-discover subnets: unable to discover at least one subnet"}
{"level":"error","ts":1668397163.3413012,"logger":"controller.ingress","msg":"Reconciler error","name":"ingress-2048","namespace":"default","error":"couldn't auto-discover subnets: unable to discover at least one subnet"}
{"level":"error","ts":1668397163.4856465,"logger":"controller.ingress","msg":"Reconciler error","name":"ingress-2048","namespace":"default","error":"couldn't auto-discover subnets: unable to discover at least one subnet"}
{"level":"error","ts":1668397163.7127712,"logger":"controller.ingress","msg":"Reconciler error","name":"ingress-2048","namespace":"default","error":"couldn't auto-discover subnets: unable to discover at least one subnet"}
{"level":"error","ts":1668397164.094966,"logger":"controller.ingress","msg":"Reconciler error","name":"ingress-2048","namespace":"default","error":"couldn't auto-discover subnets: unable to discover at least one subnet"}
{"level":"error","ts":1668397164.8004348,"logger":"controller.ingress","msg":"Reconciler error","name":"ingress-2048","namespace":"default","error":"couldn't auto-discover subnets: unable to discover at least one subnet"}
解决办法:
原因:
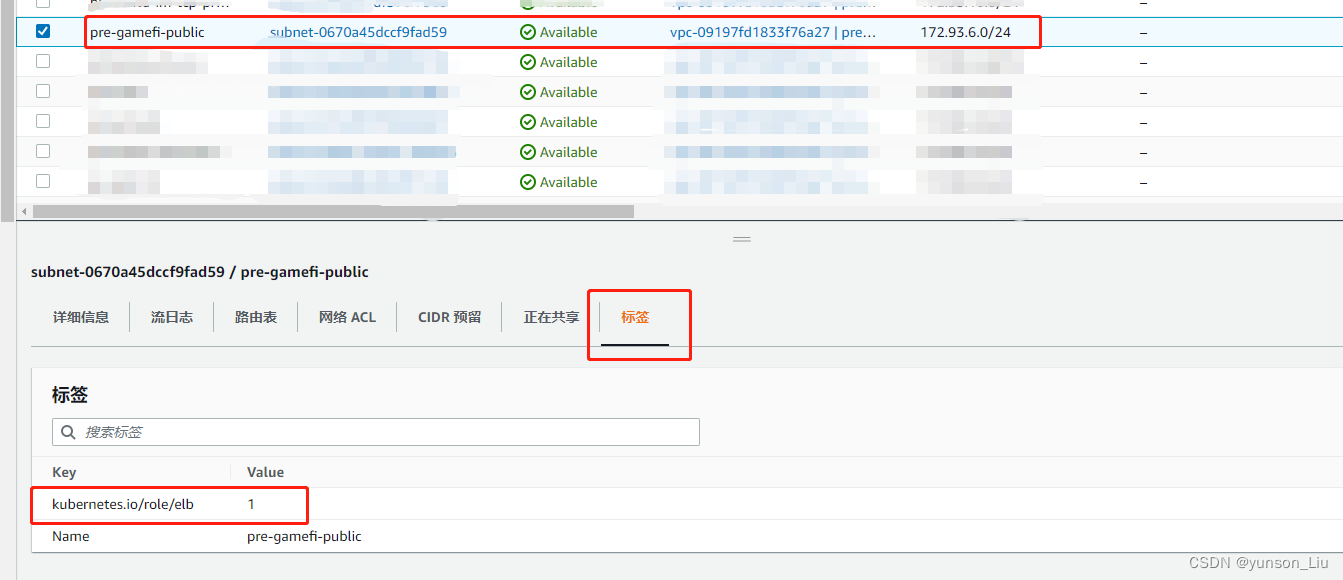
如果是通过eksctl创建的subnet,那么自动已经打好标签了,我是因为使用现有的subnet,所以这些标签没有加上,需要手动添加。打标签的时候,如果是直接从网页复制粘贴,可能无意会粘贴上换行符,导致失败
解决相关文档
官网文档有解析
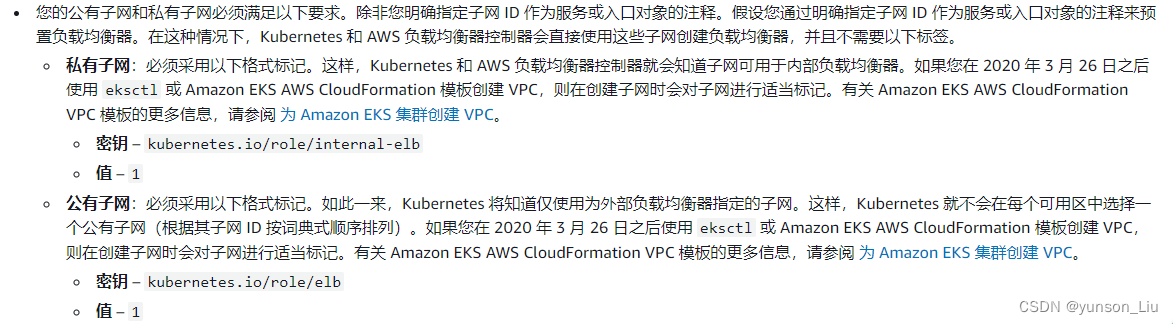
添加标签,我这边有两个子网,都是这样添加
重启pod
[root@ip-172-93-6-200 gamefi]# kubectl replace --force -f v2_4_5_full.yaml
customresourcedefinition.apiextensions.k8s.io "ingressclassparams.elbv2.k8s.aws" deleted
customresourcedefinition.apiextensions.k8s.io "targetgroupbindings.elbv2.k8s.aws" deleted
serviceaccount "aws-load-balancer-controller" deleted
role.rbac.authorization.k8s.io "aws-load-balancer-controller-leader-election-role" deleted
clusterrole.rbac.authorization.k8s.io "aws-load-balancer-controller-role" deleted
rolebinding.rbac.authorization.k8s.io "aws-load-balancer-controller-leader-election-rolebinding" deleted
clusterrolebinding.rbac.authorization.k8s.io "aws-load-balancer-controller-rolebinding" deleted
service "aws-load-balancer-webhook-service" deleted
deployment.apps "aws-load-balancer-controller" deleted
certificate.cert-manager.io "aws-load-balancer-serving-cert" deleted
issuer.cert-manager.io "aws-load-balancer-selfsigned-issuer" deleted
mutatingwebhookconfiguration.admissionregistration.k8s.io "aws-load-balancer-webhook" deleted
validatingwebhookconfiguration.admissionregistration.k8s.io "aws-load-balancer-webhook" deleted
ingressclass.networking.k8s.io "alb" deleted
customresourcedefinition.apiextensions.k8s.io/ingressclassparams.elbv2.k8s.aws replaced
customresourcedefinition.apiextensions.k8s.io/targetgroupbindings.elbv2.k8s.aws replaced
serviceaccount/aws-load-balancer-controller replaced
role.rbac.authorization.k8s.io/aws-load-balancer-controller-leader-election-role replaced
clusterrole.rbac.authorization.k8s.io/aws-load-balancer-controller-role replaced
rolebinding.rbac.authorization.k8s.io/aws-load-balancer-controller-leader-election-rolebinding replaced
clusterrolebinding.rbac.authorization.k8s.io/aws-load-balancer-controller-rolebinding replaced
service/aws-load-balancer-webhook-service replaced
deployment.apps/aws-load-balancer-controller replaced
certificate.cert-manager.io/aws-load-balancer-serving-cert replaced
issuer.cert-manager.io/aws-load-balancer-selfsigned-issuer replaced
mutatingwebhookconfiguration.admissionregistration.k8s.io/aws-load-balancer-webhook replaced
validatingwebhookconfiguration.admissionregistration.k8s.io/aws-load-balancer-webhook replaced
ingressclass.networking.k8s.io/alb replaced
查询日志如下
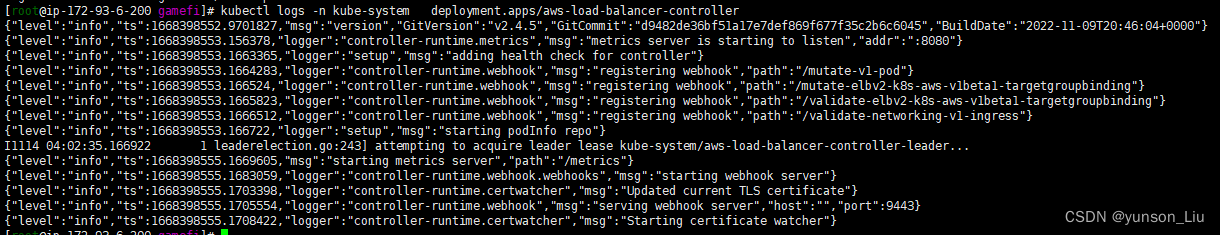
[root@ip-172-93-6-200 gamefi]# aws ec2 describe-subnets --subnet-ids subnet-0670a45dccf9fad59 --region ap-east-1
{
"Subnets": [
{
"MapPublicIpOnLaunch": true,
"AvailabilityZoneId": "ape1-az2",
"Tags": [
{
"Value": "1",
"Key": "kubernetes.io/role/elb"
},
{
"Value": "pre-gamefi-public",
"Key": "Name"
}
],
"AvailableIpAddressCount": 231,
"DefaultForAz": false,
"SubnetArn": "arn:aws:ec2:ap-east-1:759261269341:subnet/subnet-0670a45dccf9fad59",
"Ipv6CidrBlockAssociationSet": [],
"VpcId": "vpc-09197fd1833f76a27",
"MapCustomerOwnedIpOnLaunch": false,
"AvailabilityZone": "ap-east-1b",
"SubnetId": "subnet-0670a45dccf9fad59",
"OwnerId": "759261269341",
"CidrBlock": "172.93.6.0/24",
"State": "available",
"AssignIpv6AddressOnCreation": false
}
]
}
启动2048游戏时报错
错误三:
[root@ip-172-93-6-200 gamefi]# kubectl replace --force -f https://raw.githubusercontent.com/kubernetes-sigs/aws-load-balancer-controller/v2.2.0/docs/examples/2048/2048_full.yaml
unable to recognize "https://raw.githubusercontent.com/kubernetes-sigs/aws-load-balancer-controller/v2.2.0/docs/examples/2048/2048_full.yaml": no matches for kind "Ingress" in version "networking.k8s.io/v1beta1"
查询负载均衡对应的pod
[root@ip-172-93-6-200 gamefi]# kubectl get pods --all-namespaces -o wide |grep aws-load-balancer-controller-5d589484dc-442cc
kube-system aws-load-balancer-controller-5d589484dc-442cc 1/1 Running 0 3m35s 172.93.5.236 ip-172-93-5-25.ap-east-1.compute.internal <none> <none>
原因:
在部署Ingress-nginx过程中(我使用的是1.23版本的k8s),遇到问题 “no matches for kind “Ingress” in version “networking.k8s.io/v1beta1””,查阅资料确定是因为k8s版本过新且已不支持对应的api,所有需要对其进行更改。
资料1
资料2
解决办法:
将最后ingess部分如下
#---
#apiVersion: networking.k8s.io/v1beta1
#kind: Ingress
#metadata:
# namespace: game-2048
# name: ingress-2048
# annotations:
# kubernetes.io/ingress.class: alb
# alb.ingress.kubernetes.io/scheme: internet-facing
# alb.ingress.kubernetes.io/target-type: ip
#spec:
# rules:
# - http:
# paths:
# - path: /*
# backend:
# serviceName: service-2048
# servicePort: 80
更改成下面的
[root@ip-172-93-6-200 gamefi]# https://raw.githubusercontent.com/kubernetes-sigs/aws-load-balancer-controller/v2.2.0/docs/examples/2048/2048_full.yaml
[root@ip-172-93-6-200 gamefi]# vim 2048_full.yaml
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
namespace: game-2048
name: ingress-2048
annotations:
kubernetes.io/ingress.class: alb
alb.ingress.kubernetes.io/scheme: internet-facing
alb.ingress.kubernetes.io/target-type: ip
spec:
rules:
- host: "foo.bar.com"
http:
paths:
- pathType: Prefix
path: "/*"
backend:
service:
name: service-2048
port:
number: 80
# - host: "*.foo.com"
# http:
# paths:
# - pathType: Prefix
# path: "/foo"
# backend:
# service:
# name: service2
# port:
# number: 80
最后重新启动pod 2048
[root@ip-172-93-6-200 gamefi]# kubectl replace --force -f 2048_full.yaml
namespace "game-2048" deleted
deployment.apps "deployment-2048" deleted
service "service-2048" deleted
ingress.networking.k8s.io "ingress-2048" deleted
namespace/game-2048 replaced
deployment.apps/deployment-2048 replaced
service/service-2048 replaced
ingress.networking.k8s.io/ingress-2048 replaced
还是没有解决问题,最后通过下载2.4.5版本的2048
2048-2.4.5版本
文本内容如下
---
apiVersion: v1
kind: Namespace
metadata:
name: game-2048
---
apiVersion: apps/v1
kind: Deployment
metadata:
namespace: game-2048
name: deployment-2048
spec:
selector:
matchLabels:
app.kubernetes.io/name: app-2048
replicas: 5
template:
metadata:
labels:
app.kubernetes.io/name: app-2048
spec:
containers:
- image: public.ecr.aws/l6m2t8p7/docker-2048:latest
imagePullPolicy: Always
name: app-2048
ports:
- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:
namespace: game-2048
name: service-2048
spec:
ports:
- port: 80
targetPort: 80
protocol: TCP
type: NodePort
selector:
app.kubernetes.io/name: app-2048
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
namespace: game-2048
name: ingress-2048
annotations:
alb.ingress.kubernetes.io/scheme: internet-facing
alb.ingress.kubernetes.io/target-type: ip
spec:
ingressClassName: alb
rules:
- http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: service-2048
port:
number: 80
[root@ip-172-93-6-200 gamefi]# kubectl apply -f 2048_full.yaml
namespace/game-2048 created
deployment.apps/deployment-2048 created
service/service-2048 created
ingress.networking.k8s.io/ingress-2048 created
几分钟后,验证是否已使用以下命令创建入口资源。
[root@ip-172-93-6-200 gamefi]# kubectl get ingress/ingress-2048 -n game-2048
NAME CLASS HOSTS ADDRESS PORTS AGE
ingress-2048 alb * k8s-game2048-ingress2-ASAAAAAAAAAAAAAAA.ap-east-1.elb.amazonaws.com 80 3m6s
查询现有的ALB
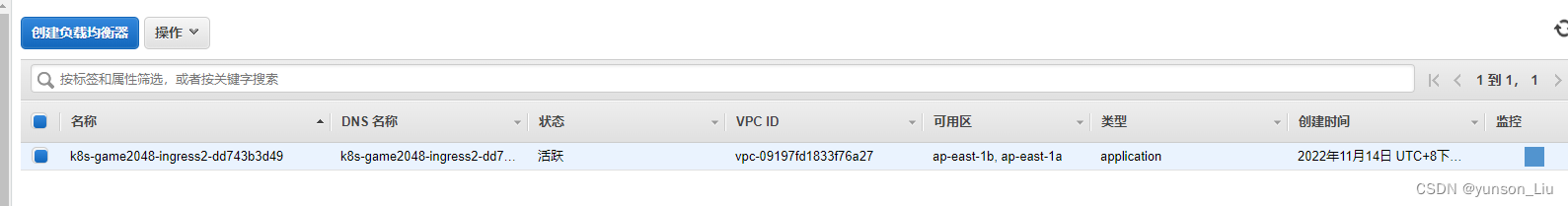
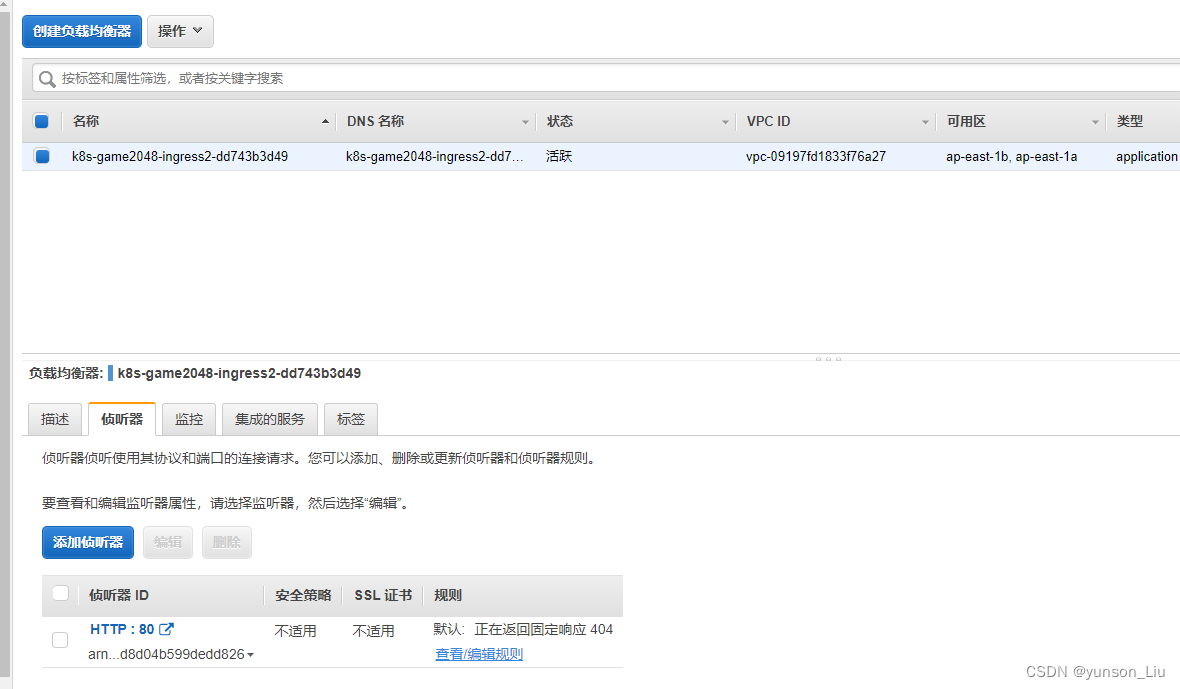
默认监听80端口
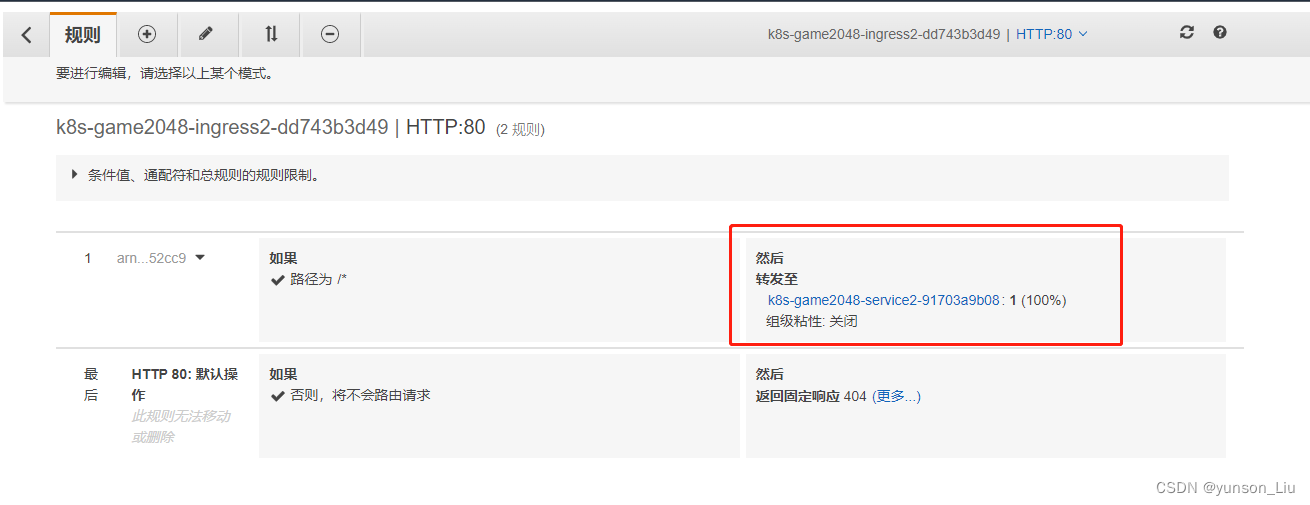
最后目标群组指向我们的5个pod
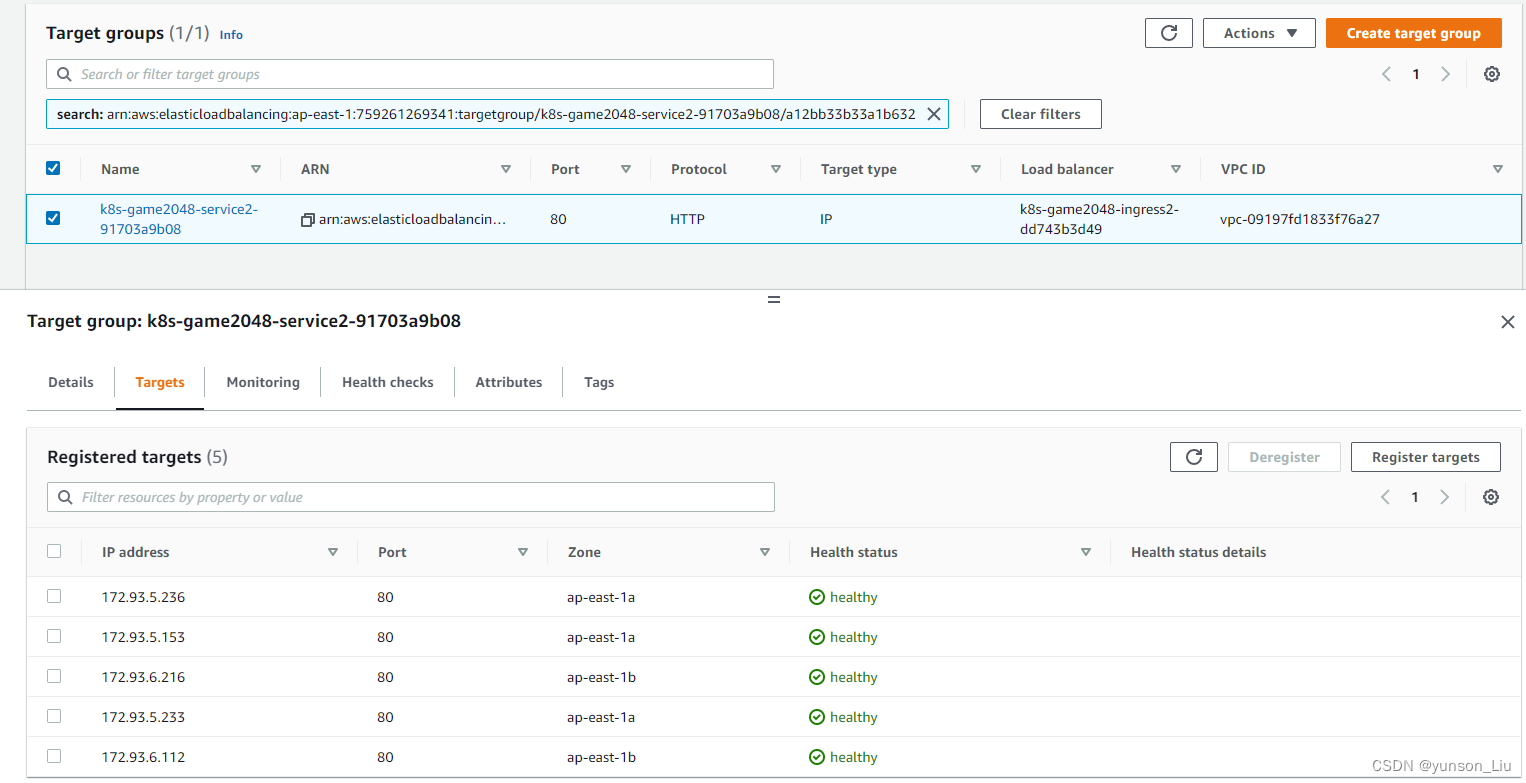
验证,输入上文中查询到的地址就可以访问了