目录
💥1 概述
📚2 运行结果
🎉3 参考文献
👨💻4 Matlab代码
💥1 概述
信息通信技术的发展和智能设备的引入使电力系统逐渐演变为电力信息物理系统,而信息层与物理层之间的深度耦合也加剧了电力系统遭受网络攻击的风险。虚假数据注入攻击(false data injection attack,FDIA)作为一种兼具隐蔽性、灵活性和攻击导向性的网络攻击方式,对电力数据采集与监控系统的安全稳定构成很大威胁。
📚2 运行结果
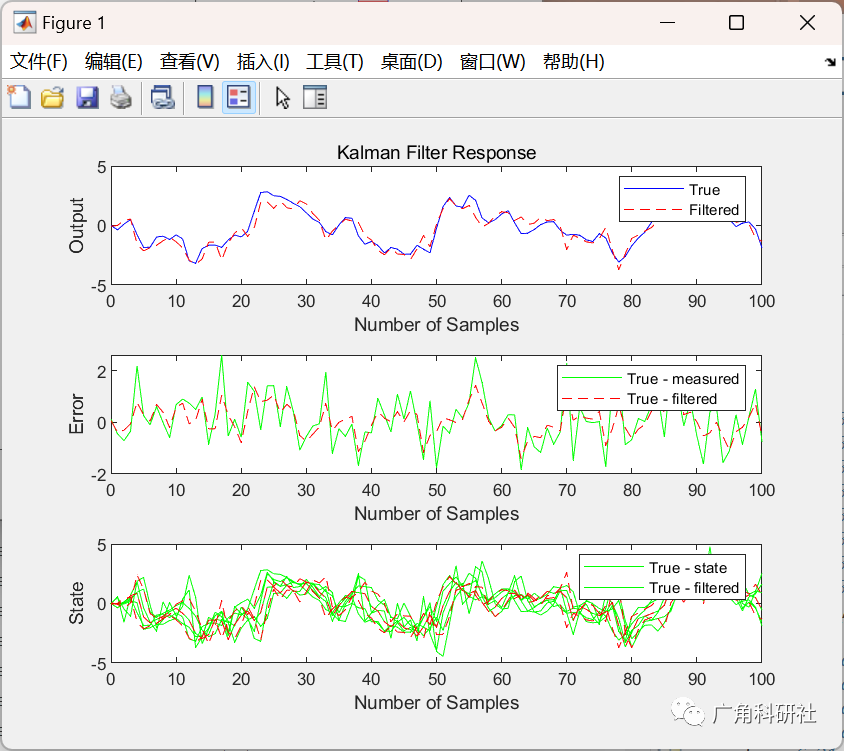
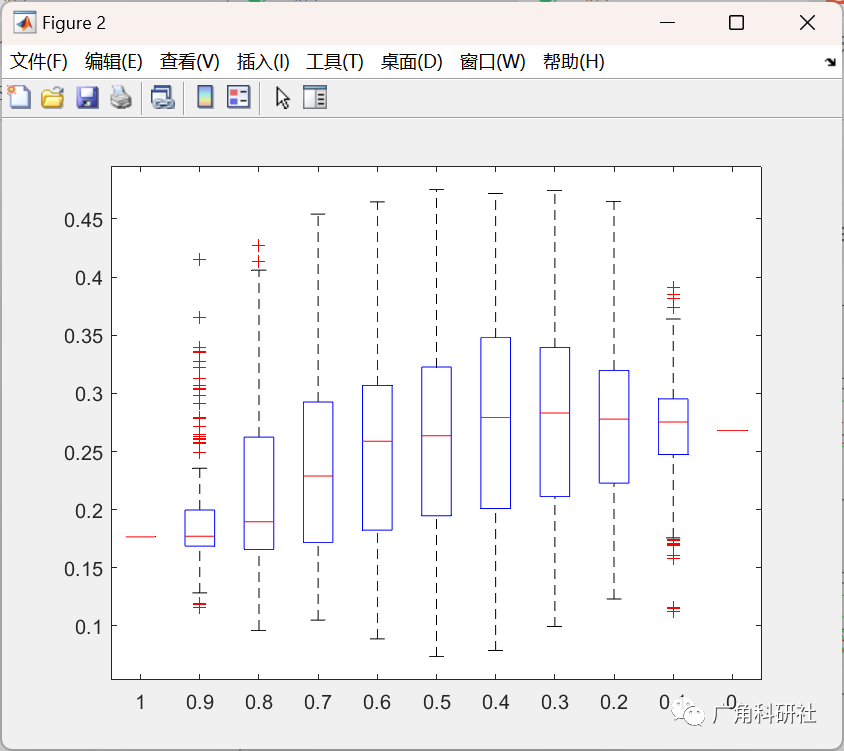

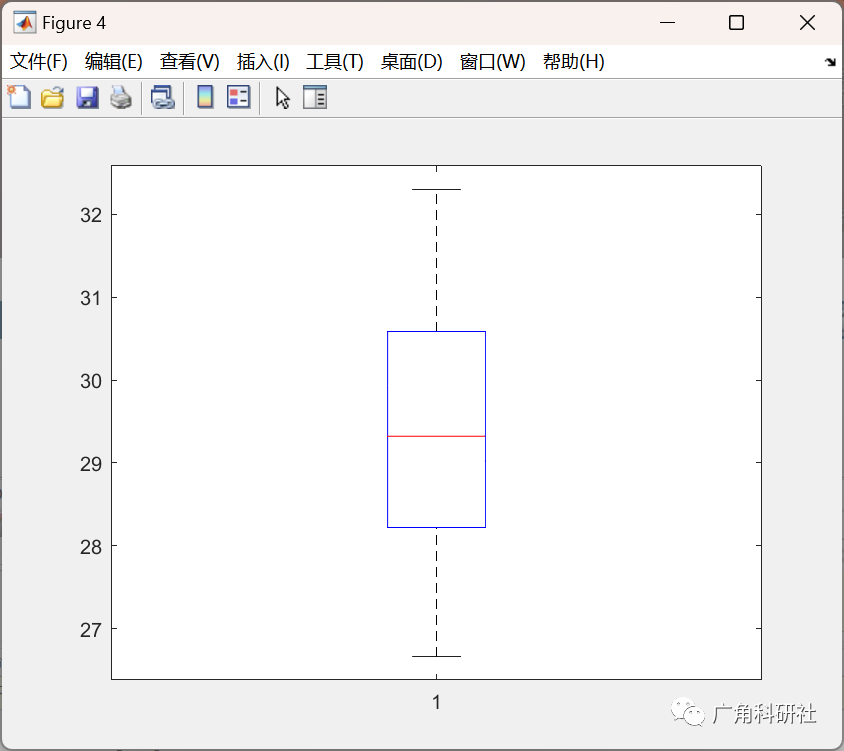
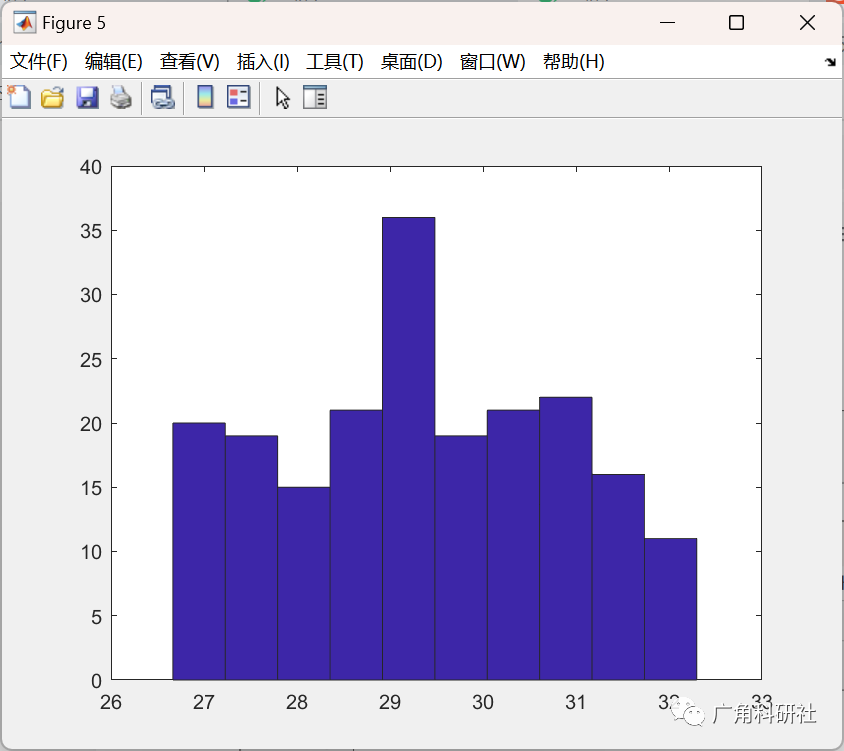
主函数部分代码:
%traditional ACSE: wls method
%close all
clear
addpath(genpath('matpower7.0/')) %add all subfolders
casename = 'case30.m';
%% simulate reality/environment
if ~(exist('measure')==1)
disp("simulate grid enviroment and meters by power flow")
mpc = loadcase(casename);
%simulate truth by power flow, and SCADA meters with noise
noise_level = 0.01; %std of gaussian noise to be added on meters
pf_results = runpf(mpc);
ref = find(mpc.bus(:,2)==3);
[measure,idx,sigma,GT,V_GT] = simulate_SCADA_meters(pf_results, noise_level);
%% add bad data (traditional)
if_bad = 0;
if if_bad==1
%add one bad data
measure.Pinj(3) = sign(measure.Pinj(3))*(1+abs(measure.Pinj(3)));
end
end
%% attacker side:
%create imperfect grid model: topology error/inaccurate network parameter
%grid model [baseMVA, bus_as, gen_as, branch_as]
baseMVA = mpc.baseMVA;
bus_as = mpc.bus;
gen_as = mpc.gen;
branch_as0 = mpc.branch;
%create some imperfectness in network parameters
branch_as1 = mpc.branch;
branch_as1(2,11)=0;
branch_as2 = mpc.branch;
branch_as2(:,4) = branch_as0(:,4)+0.02*randn(size(branch_as0,1),1);
branch_as3 = branch_as2;
branch_as3(2,11)=0;
branch_as3(6,11)=0;
%prepare infomation: state x,
%generate: manipulated measurement measure_a (z_a) z_a = z + ha(Xa)-ha(X)
% functin runpf returns angle in degree
Vest_as0 = V_GT; %X, estimation of the state x on attacker's server
%Vest_as = abs(V_GT); %imperfect state x
Vest_as1 = Vest_as0 + randn(length(Vest_as0),1)*0.01;
Vest_as1(1) = 1+0i; %attackers know reference bus
%target bad case
tgtcase_as = mpc;
tgtcase_as.bus(:,3:4) = mpc.bus(:,3:4)*0.9; %reduce load by 10%
%tgtcase_as.bus(6:10,3:4) = tgtcase_as.bus(6:10,3:4)-1;
pf_astgt = runpf(tgtcase_as);
dA_as = 3*randn(length(bus_as),1); %for FDIA DC
%dA_as = 3.*pf_results.bus(:,9);
dA_as(11:end)=0;
Instances_modes = {'perfect','perfect','DC','DC'};
Instances_cons = {'No','combined','No','combined'};
%Instances_modes = {'perfect','perfect','perfect','perfect','perfect',...
% 'DC','DC','DC','DC','DC'};
%Instances_cons = {'No','topology','ntwpara','state','combined',...
% 'No','topology','ntwpara','state','combined'};
for i = 1:length(Instances_modes)
MODE_FDIA = Instances_modes{i}; %'DC','target AC','perfect'
constraint = Instances_cons{i};
Vest_as = Vest_as0;
branch_as = branch_as0;
if strcmp(constraint,'topology')==1
branch_as = branch_as1;
elseif strcmp(constraint,'ntwpara')==1
branch_as = branch_as2;
elseif strcmp(constraint,'state')==1
Vest_as = Vest_as1;
elseif strcmp(constraint,'combined')==1
branch_as = branch_as3;
Vest_as = Vest_as1;
end
if strcmp(MODE_FDIA,'target AC')
%AC FDIA designed by certain target wrong solution Vtarget_as
Vtarget_as = Vest_as; %target manipulate on estimate x
Vtarget_abs = abs(Vest_as); %magnitude of wrong solution
Vtarget_as=Vtarget_abs.*exp(1i*angle(Vest_as)*2); %Xa, the bad state that attackers want to mislead operators toward
%Vtarget_as(2) = 0.95;
Vtarget_as(ref)=1+0i; %attackers know reference bus
[measure_a, idx] = ...
fdia_ac_gen(Vest_as,Vtarget_as, measure, idx,...
baseMVA, bus_as, gen_as, branch_as);
elseif strcmp(MODE_FDIA, 'perfect')||strcmp(MODE_FDIA, 'DC')
%well crafted fdia ac
%Vest_as ready
if strcmp(MODE_FDIA, 'perfect')
[measure_a, idx, Vtarget_as] = ...
fdia_perfac_gen(Vest_as,pf_astgt, ...
measure,idx,...
baseMVA, bus_as, gen_as, branch_as);
elseif strcmp(MODE_FDIA, 'DC')
%DC FDiA:
%dA_as = randn(length(bus_as),1); %delta angle (radias), create some random disturb of angle
%dA_as = angle(Vest_as)-pf_astgt.bus(:,9)./180.*pi;
%dA_as(ref)=0;
[measure_a, idx] = fdia_dc_gen(dA_as,measure,idx, baseMVA, bus_as, gen_as, branch_as);
Vtarget_as=abs(V_GT).*exp(1i*(angle(V_GT)+dA_as)); %Xa, the bad state that attackers want to mislead operators toward
end
end
🎉3 参考文献
[1]黄冬梅,丁仲辉,胡安铎等.低成本对抗性隐蔽虚假数据注入攻击及其检测方法[J].电网技术,2023,47(04):1531-1540.
部分理论引用网络文献,若有侵权联系博主删除。


![[STM32F103C8T6]基于stm32的循迹,跟随,避障智能小车](https://img-blog.csdnimg.cn/45c3ffdf5d3b490cab04da518cadbc29.png)