1 ULPI PHY passive sniffing mode
概念: non driving, no pull-up, no pull-down
Function Control.opMode = 1; // non-Driving
OTG Control.DpPulldown = 0; // no pull-down
OTG Control.DmPulldown = 0; // no pull-down
USB IO.ChargerPullupEnDP = 0; // no pull-up
USB IO.ChargerPullupEnDM = 0; // no pull-up
2 Beagle USB Analyzer
2.1 Beagle USB 12 Analyzer
在USB Host和Device之间的DP/DM上连接一个Fairchild USB1T11A,Fairchild USB1T11A连接到隔离器件ADUM1400后,隔离器件再连接到FPGA;FPGA通过CY7C68013A连接到PC。
Figure 2-1 Beagle USB 12 Analyzer

2.2 Beagle USB 480 Analyzer
USB 2.0的协议分析仪有2个PHY,支持LS/FS的Fairchild USB1T11A,支持HS的USB3300(passive sniffing mode)。
Figure 2-2 Beagle USB 480 Analyzer

2.3 Beagle USB 5000 v2 analyzer
有2块PCB,下层是模拟PCB,上层是数字PCB,数字PCB上包括FPGA和CYUSB3014 BZX,其中CYUSB3014 BZX负责上传数据到PC,该芯片在数字PCB上的位置靠近Target Host Port口。
It uses British standard plug.
2.4 URLs
Review: Total Phase Beagle USB 12 Analyzer
https://eleccelerator.com/review-total-phase-beagle-usb-12-analyzer/
Beagle USB 480
https://www.bunniestudios.com/blog/?p=4106
3 OpenVizsla
3.1 FPGA-based USB analyzer
在USB Host和Device之间的DP/DM上连接一个USB3343(passive sniffing mode),USB3343连接到FPGA;FPGA通过FIFO模式连接到FT2232H,FT2232H连接到PC。
Figure 3-1 OpenVizsla board
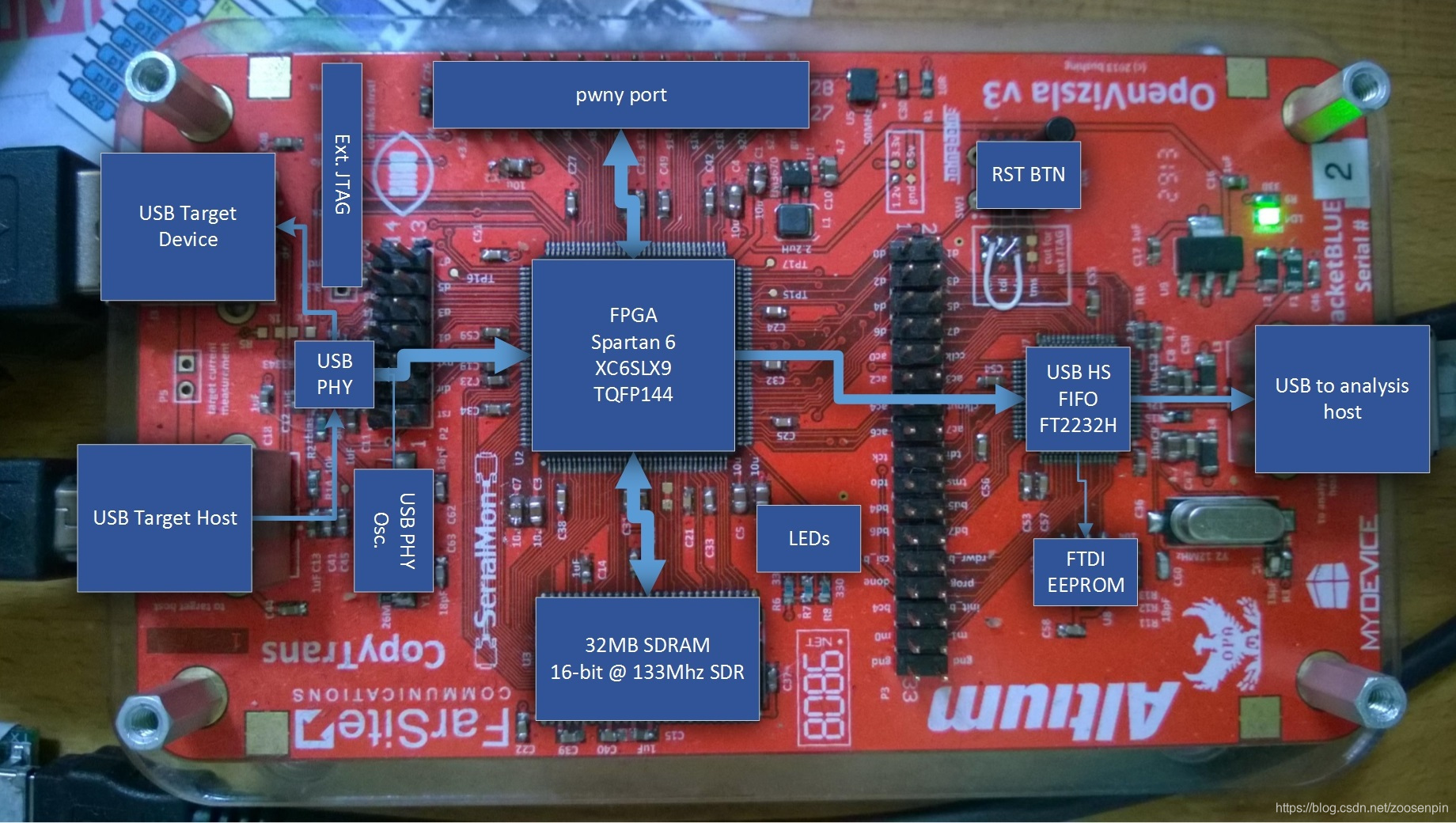
3.2 URLs
Open Hardware FPGA-based USB analyzer
http://openvizsla.org/
https://github.com/openvizsla
USB 2.0 Bus/Protocol Analyzer Hardware/Software Comparison
http://www.summitsoftconsulting.com/UsbAnalyzers.htm
4 Teledyne LeCroy NRZI Waveform
Choose Packet - Right Click - Show Raw Bits
5 Windows软件抓包工具
5.1 Bus Hound
5.2 USBPcap
USBPcap - USB Packet capture for Windows
https://desowin.org/usbpcap/
6 Linux usbmon抓包
6.1 sniff原理
binary格式路径:/dev/usbmonX
text格式路径:/sys/kernel/debug/usb/usbmon
获得usbmon的主设备号:cat /proc/devices
创建binary节点:
mknod /dev/usbmon0 c $major 0
mknod /dev/usbmon1 c $major 1
mknod /dev/usbmon2 c $major 2
6.2 usbmon tcpdump
1)mount -t debugfs none_debugs /sys/kernel/debug
2)cat /sys/kernel/debug/usb/devices - 确定usb的总线号
3)tcpdump -D
4)tcpdump -i usbmon1 -s 128 -w /data/usb_sniff.pcap &
5)killall tcpdump
6)wireshark工具打开usb_sniff.pcap
Intel APL (Gen9, A39X0) 8-port MPH xHCI
usbmon1 - xHCI LS/FS/HS
usbmon2 - xHCI SS
6.3 Wireshark过滤规则
1)usb.src == "1.6.1" and usb.dst == "host" - 改到对应的USB bus_no.addr.ep_no
2)usb.src == host and ublox
6.4 USB协议URB解析Wireshark插件
usb_table = DissectorTable.get("usb.bulk")
usb_table:add(0xff, my_proto)
usb_table:add(0xffff, my_proto)
6.5 usbmon sysfs接口
cat /sys/kernel/debug/usb/usbmon/1u > /sdcard/1u_usbmon.txt
命令中1u表示Bus=01,通过命令获得cat /sys/kernel/debug/usb/devices
cd /sys/kernel/debug/usb/usbmon
反向查找,查找不包含"1:003:2"(总线号:设备地址:端点号)字符串的其它内容
cat 1u |grep -v "1:003:2"
排除多个字符串:cat 1u |grep -vE "1:003:2|1:004:1"
6.6 usbfs
echo 1 > /sys/module/usbcore/parameters/usbfs_snoop
7 Abbreviations
DSLogic:Dream Source Lab