每年的misc都是最无聊坐牢的
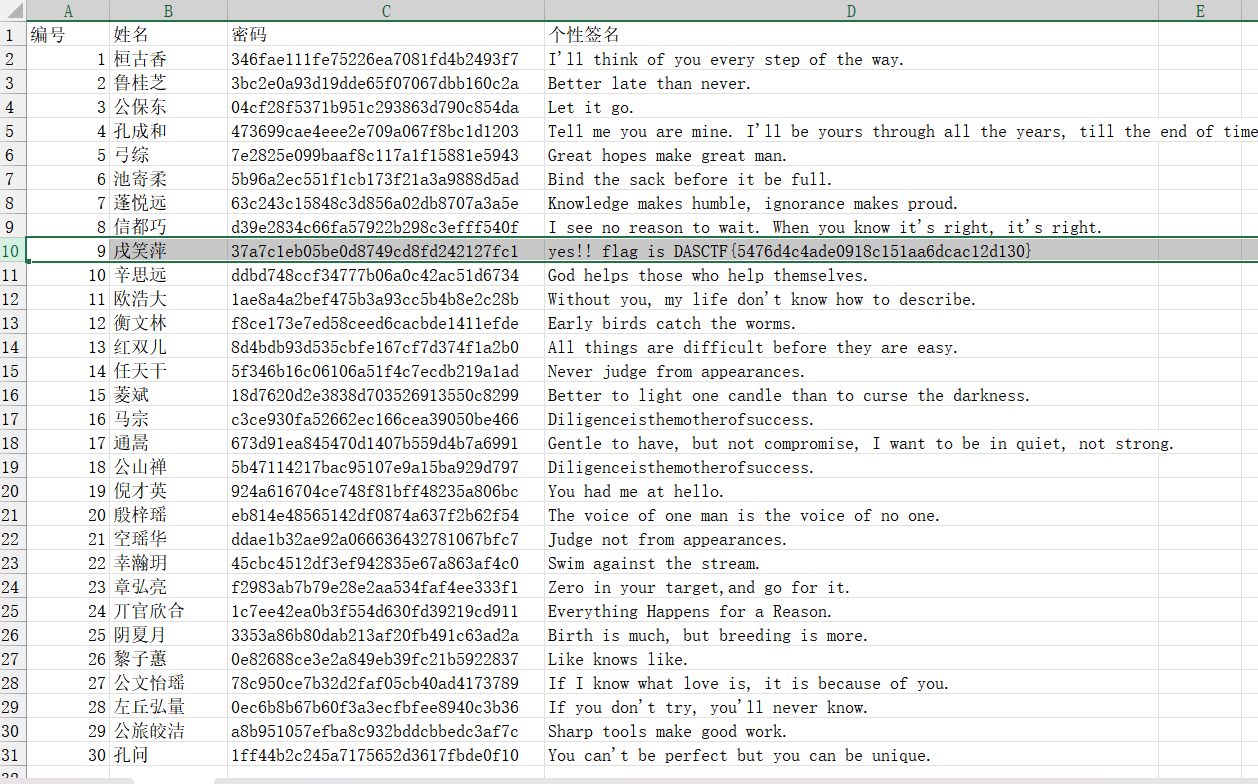
数据安全-easy_tables
import pandas as pd
import hashlib
from datetime import datetime
users_df = pd.read_csv('users.csv')
permissions_df = pd.read_csv('permissions.csv')
tables_df = pd.read_csv('tables.csv')
actionlog_df = pd.read_csv('actionlog.csv')
#判断操作是否在允许的操作中
def is_action_allowed(allowed_actions, action):
return action in allowed_actions
#判断表是否在允许的表中
def is_table_allowed(allowed_tables, table_name):
return str(table_name) in allowed_tables
#检查时间
def is_time_in_range(time_str, time_range_str):
time = datetime.strptime(time_str, "%H:%M:%S").time()
for period in time_range_str.split(','):
start, end = period.split('~')
start_time = datetime.strptime(start, "%H:%M:%S").time()
end_time = datetime.strptime(end, "%H:%M:%S").time()
if start_time <= time <= end_time:
return True
return False
def calculate_md5(s):
return hashlib.md5(s.encode()).hexdigest()
user_permission_group = {row['账号']: row['所属权限组编号'] for index, row in users_df.iterrows()}
group_permissions = {row['编号']: row['可操作权限'].split(',') for index, row in permissions_df.iterrows()}
group_tables = {row['编号']: row['可操作表编号'].split(',') for index, row in permissions_df.iterrows()}
table_times = {row['编号']: row['可操作时间段(时:分:秒)'] for index, row in tables_df.iterrows()}
bad = []
for index, log in actionlog_df.iterrows():
user = log['账号']
operation = log['执行操作'].split()[0] # 操作类型 (insert, delete,......),并且不同的类型出现的表位置不同
if(operation == 'update'):
table_name = log['执行操作'].split()[1]
elif(operation == 'select'):
table_name = log['执行操作'].split()[3]
else:
table_name = log['执行操作'].split()[2]
operation_time = log['操作时间'].split()[1]
# print(user,operation,table_name,operation_time)
# 检查账号是否存在
if user not in user_permission_group:
bad.append(f"0_0_0_{log['编号']}")
continue
permission_group_id = user_permission_group[user]
allowed_actions = group_permissions.get(permission_group_id, [])
allowed_tables = group_tables.get(permission_group_id, [])
# print(allowed_tables,allowed_actions)
# 检查表是否存在及是否允许操作此表
table_id = tables_df[tables_df['表名'] == table_name]['编号'].values
if len(table_id) == 0 or not is_table_allowed(allowed_tables, table_id[0]):
print('can')
bad.append(f"{users_df[users_df['账号'] == user]['编号'].values[0]}_{permission_group_id}_{table_id[0]}_{log['编号']}")
continue
else:
table_id = table_id[0]
# 检查操作权限
if not is_action_allowed(allowed_actions, operation):
print('allow')
bad.append(f"{users_df[users_df['账号'] == user]['编号'].values[0]}_{permission_group_id}_{table_id}_{log['编号']}")
continue
# 检查操作时间
allowed_time_ranges = table_times.get(table_id, "")
if not is_time_in_range(operation_time, allowed_time_ranges):
print('time')
bad.append(f"{users_df[users_df['账号'] == user]['编号'].values[0]}_{permission_group_id}_{table_id}_{log['编号']}")
print(bad)
bad_sort = ','.join(sorted(bad, key=lambda x: [int(i) for i in x.split('_')]))
flag_md5 = hashlib.md5(bad_sort.encode()).hexdigest()
flag_auto = f"DASCTF{{{flag_md5}}}"
print(bad_sort)
print(flag_auto)
allow
can
allow
time
can
time
time
['30_87_36_235', '7_64_69_3448', '9_18_61_5681', '6_14_91_6786', '0_0_0_6810', '49_37_30_8295', '0_0_0_8377', '75_15_43_8461', '79_3_15_9011', '31_76_85_9617']
0_0_0_6810,0_0_0_8377,6_14_91_6786,7_64_69_3448,9_18_61_5681,30_87_36_235,31_76_85_9617,49_37_30_8295,75_15_43_8461,79_3_15_9011
DASCTF{271b1ffebf7a76080c7a6e134ae4c929}
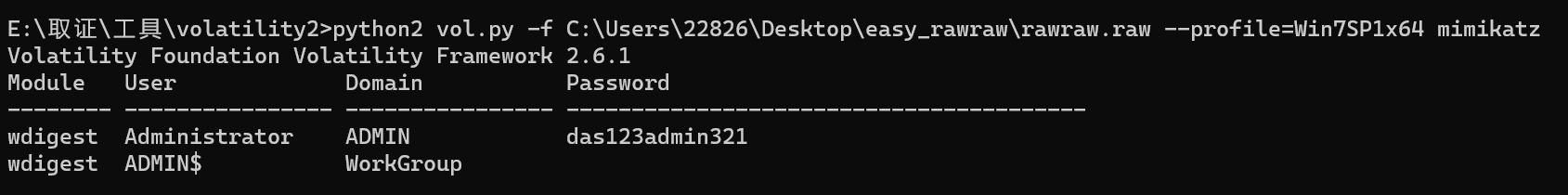
easy_rawraw
管理员密码 mimikatz第一个密码das123admin321
剪贴板 clipboard第二个密码DasrIa456sAdmIn987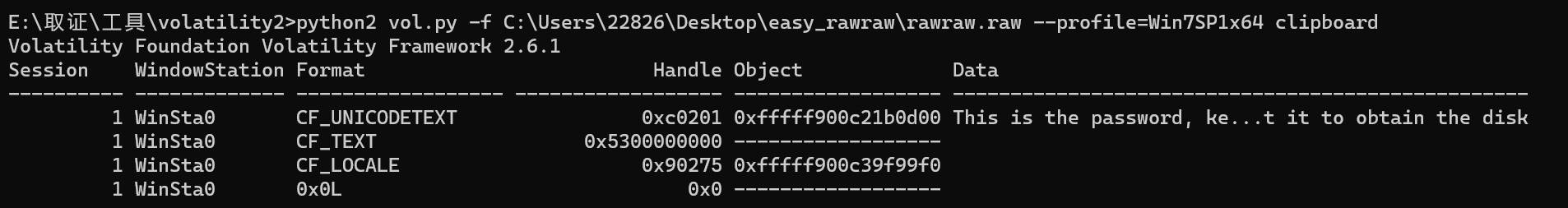
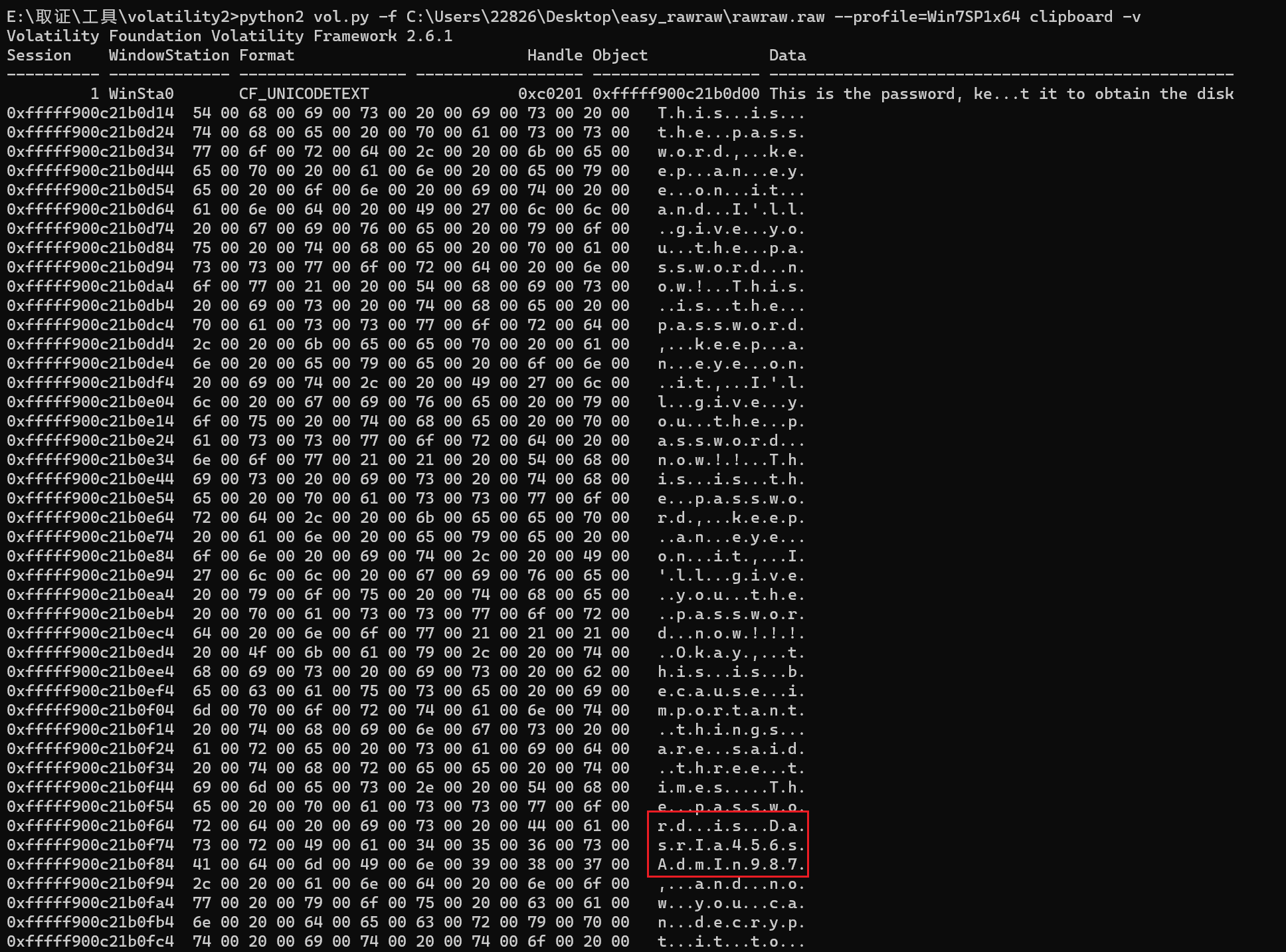
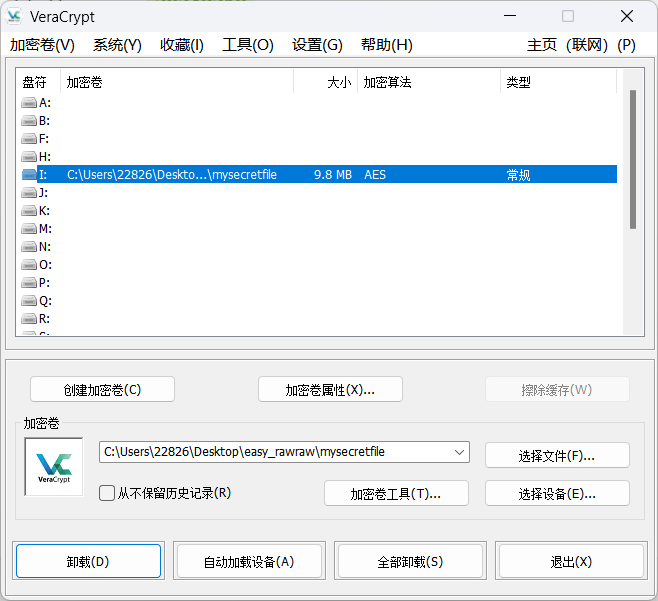
对应rar密码,解开根据大小、乱码和前面剪贴板内容的描述显然是vc容器
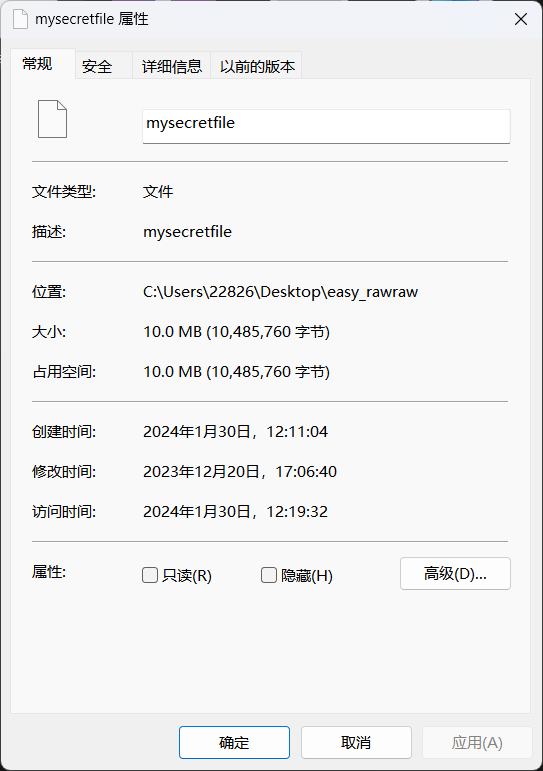
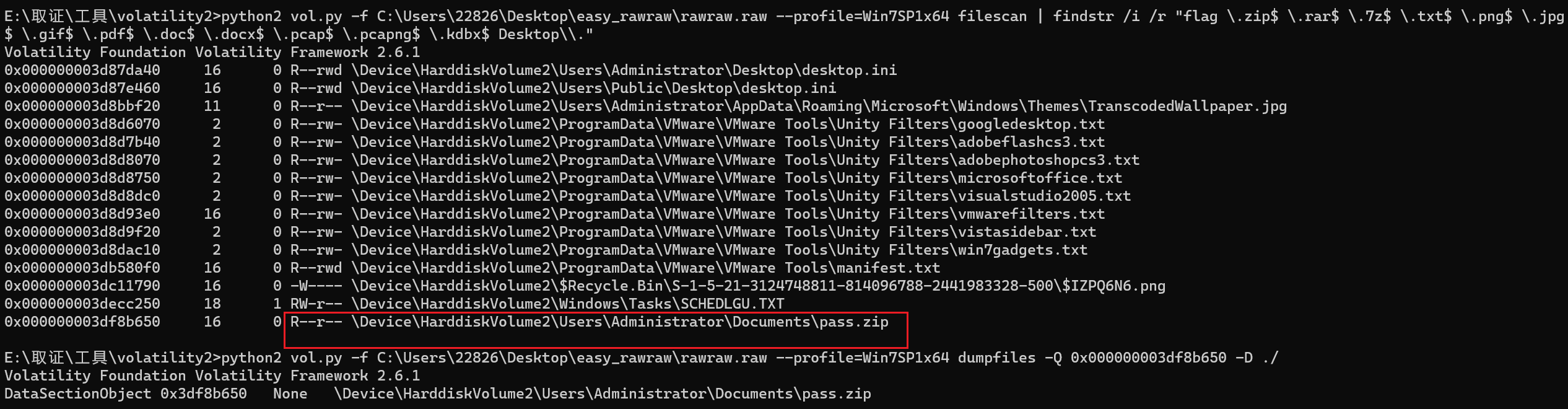
第三个密码文件,在documents下
解开png文件尾有zip

8位数字爆破,对上zip的注释Have a good New Year!!!,应该刚好是正月初一
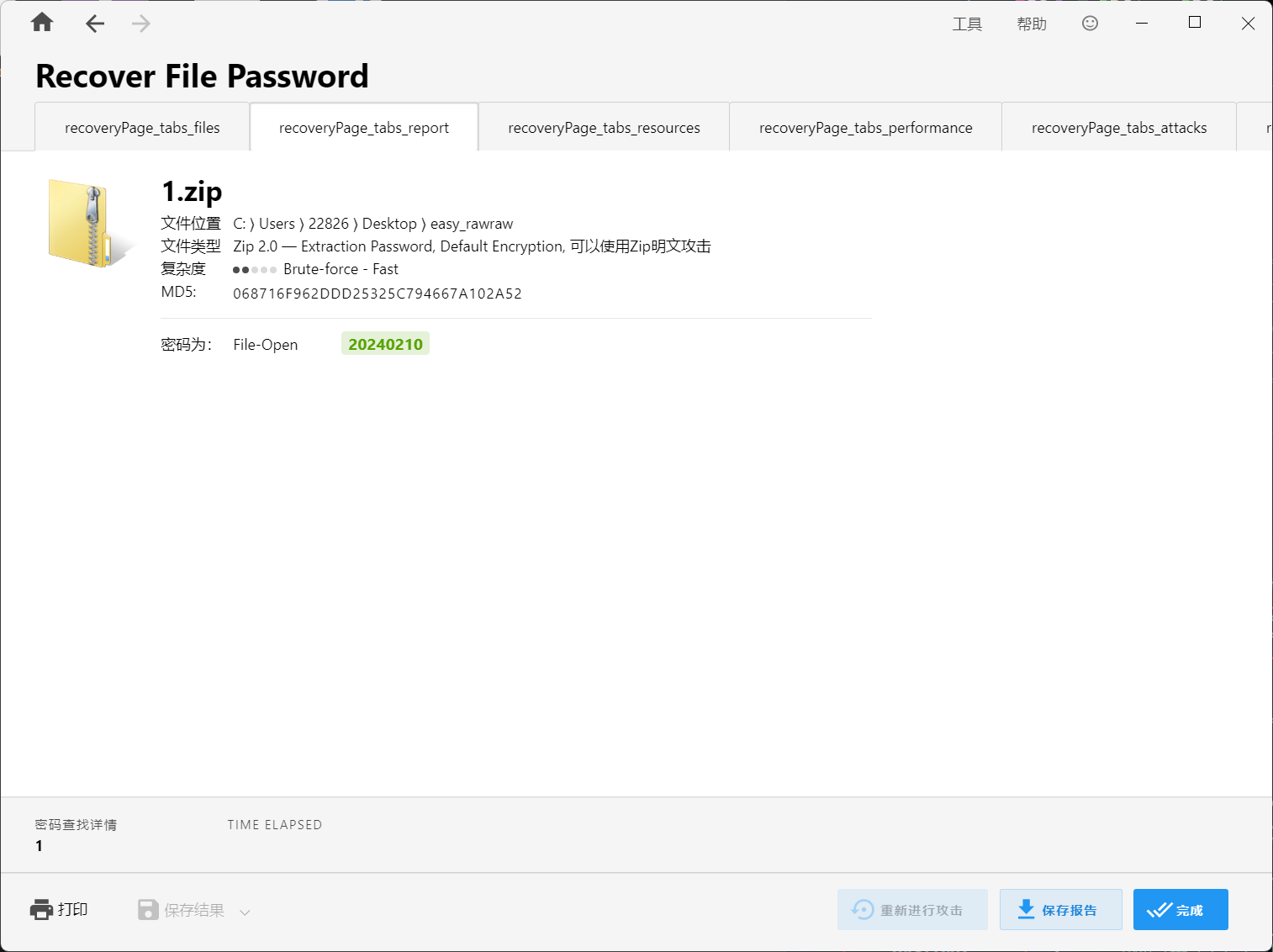
得到一个密码本,爆破vc容器密码无果,fuzz后将其当作密钥文件解开vc
一个隐藏excel
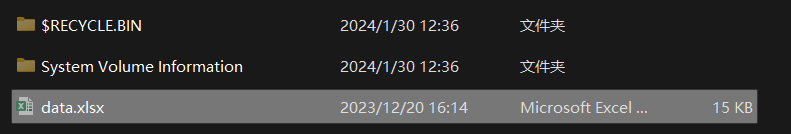
excel密码是前面admin的密码
中间隐藏了一行,重新拉开是flag