第一种方法,分部出口有nat设备,且总部用模版,总部外线为固定地址,分部出口可以无固定地址。

主要配置:
所有默认策略全部放行,具体怎么开策略可以等通后用命令dis firewall session table ver看
security-policy
default active permit
i.配置接口IP地址。
system-view
[sysname] sysname FW_A
[FW_A] interface GigabitEthernet 1/0/1
[FW_A-GigabitEthernet1/0/1] ip address 10.1.1.1 24
[FW_A-GigabitEthernet1/0/1] quit
[FW_A] interface GigabitEthernet 1/0/2
[FW_A-GigabitEthernet1/0/2] ip address 1.1.2.1 24
[FW_A-GigabitEthernet1/0/2] quit
ii.将接口加入相应的安全区域。
[FW_A] firewall zone trust
[FW_A-zone-trust] add interface GigabitEthernet 1/0/1
[FW_A-zone-trust] quit
[FW_A] firewall zone untrust
[FW_A-zone-untrust] add interface GigabitEthernet 1/0/2
[FW_A-zone-untrust] quit
c.配置默认路由下一跳地址为1.1.2.2为公网地址
[FW_A] ip route-static 0.0.0.0 0 1.1.2.2
2.在FW_A上配置IPSec。
a.定义被保护的数据流。
[FW_A] acl 3000
[FW_A-acl-adv-3000] rule 5 permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
b.配置IPSec安全提议tran1。采用默认参数。
[FW_A] ipsec proposal tran1
[FW_A-ipsec-proposal-tran1] esp authentication-algorithm sha2-256 //默认就有
[FW_A-ipsec-proposal-tran1] esp encryption-algorithm aes-256 //默认就有
[FW_A-ipsec-proposal-tran1] quit
c.配置IKE安全提议。采用默认参数。
[FW_A] ike proposal 10
[FW_A-ike-proposal-10] authentication-method pre-share //默认就有
[FW_A-ike-proposal-10] prf hmac-sha2-256 //默认就有
[FW_A-ike-proposal-10] encryption-algorithm aes-256 //默认就有
[FW_A-ike-proposal-10] dh group14 //默认就有
[FW_A-ike-proposal-10] integrity-algorithm hmac-sha2-256 //默认就有
[FW_A-ike-proposal-10] quit
d.配置IKE Peer。
[FW_A] ike peer c
[FW_A-ike-peer-c] ike-proposal 10
[FW_A-ike-peer-c] pre-shared-key admin123
[FW_A-ike-peer-c] quit
e.配置IPSec策略模板temp。
[FW_A] ipsec policy-template temp 1
[FW_A-ipsec-policy-templet-temp-1] security acl 3000
[FW_A-ipsec-policy-templet-temp-1] proposal tran1
[FW_A-ipsec-policy-templet-temp-1] ike-peer c
[FW_A-ipsec-policy-templet-temp-1] quit
f.创建IPSec策略并引用IPSec策略模板temp。
[FW_A] ipsec policy map1 10 isakmp template temp
g.在接口GigabitEthernet 1/0/2上应用IPSec策略组map1。
[FW_A] interface GigabitEthernet 1/0/2
[FW_A-GigabitEthernet1/0/2] ipsec policy map1
[FW_A-GigabitEthernet1/0/2] quit
3.配置FW_C的基础配置。 a.配置接口IP地址,并将接口加入域。
请根据图1的数据配置接口IP地址。
将接口GigabitEthernet 1/0/1加入Trust区域
接口GigabitEthernet 1/0/2加入Untrust区域
详细步骤可参见FW_A的配置。
c.配置静态路由,下一跳地址为10.1.5.1出口路由地址
ip route-static 0.0.0.0 0.0.0.0 10.1.5.1
4.在FW_C上配置IPSec策略。 a.定义被保护的数据流。
[FW_C] acl 3000
[FW_C-acl-adv-3000] rule 5 permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
b.配置IPSec安全提议tran1。采用默认参数。
[FW_C] ipsec proposal tran1
[FW_C-ipsec-proposal-tran1] esp authentication-algorithm sha2-256 //默认就有
[FW_C-ipsec-proposal-tran1] esp encryption-algorithm aes-256 //默认就有
[FW_C-ipsec-proposal-tran1] quit
c.配置IKE安全提议。采用默认参数。
[FW_C] ike proposal 10
[FW_C-ike-proposal-10] authentication-method pre-share //默认就有
[FW_C-ike-proposal-10] prf hmac-sha2-256 //默认就有
[FW_C-ike-proposal-10] encryption-algorithm aes-256 //默认就有
[FW_C-ike-proposal-10] dh group14 //默认就有
[FW_C-ike-proposal-10] integrity-algorithm hmac-sha2-256 //默认就有
[FW_C-ike-proposal-10] quit
d.配置IKE Peer。
[FW_C] ike peer a
[FW_C-ike-peer-a] ike-proposal 10
[FW_C-ike-peer-a] remote-address 1.1.2.1
[FW_C-ike-peer-a] pre-shared-key admin123
[FW_C-ike-peer-a] quit
e.配置IPSec策略map1。
[FW_C] ipsec policy map1 10 isakmp
[FW_C-ipsec-policy-isakmp-map1-10] security acl 3000
[FW_C-ipsec-policy-isakmp-map1-10] proposal tran1
[FW_C-ipsec-policy-isakmp-map1-10] ike-peer a
[FW_C-ipsec-policy-isakmp-map1-10] quit
f.在接口GigabitEthernet 1/0/2上应用IPSec策略组map1。
[FW_C] interface GigabitEthernet 1/0/2
[FW_C-GigabitEthernet1/0/2] ipsec policy map1
[FW_C-GigabitEthernet1/0/2] quit
c.出路路由器配置。
acl number 2000
rule 5 permit source 10.1.2.0 0.0.0.255
interface GigabitEthernet0/0/0
ip address 10.1.5.1 255.255.255.0
interface GigabitEthernet0/0/1
ip address 1.1.5.1 255.255.255.0
nat outbound 2000
ip route-static 0.0.0.0 0.0.0.0 1.1.5.2
ip route-static 10.1.2.0 255.255.255.0 10.1.5.2
结果验证
1.配置完成后,PC2发起访问,之后PC1与PC2之间可以相互访问。PC2同时可以访问到公网。
2.PC2可以Ping通FW_A的1.1.2.1,同时在FW_B上可以查看NAT转换session表项。
<FW_B> display firewall session table
Current Total Sessions : 2
udp VPN:public --> public 10.1.5.2:500[1.1.5.1:2048]–>1.1.2.1:500
udp VPN:public --> public 10.1.5.2:4500[1.1.5.1:2048]–>1.1.2.1:4500
3.总部防火墙FW_A上可以查看到对应的IKE SA。
<FW_A> display ike sa
IKE SA information :
Conn-ID Peer VPN Flag(s) Phase RemoteType RemoteID
83887864 1.1.5.1:500 RD|A v2:2 IP 1.1.5.1
83887652 1.1.5.1:500 RD|A v2:1 IP 1.1.5.1
Number of IKE SA : 2
Flag Description:
RD–READY ST–STAYALIVE RL–REPLACED FD–FADING TO–TIMEOUT
HRT–HEARTBEAT LKG–LAST KNOWN GOOD SEQ NO. BCK–BACKED UP
M–ACTIVE S–STANDBY A–ALONE NEG–NEGOTIATING
4.分支上FW_C可以查看到对端为总部的IKE SA,FW_C是发起方,标志位为ST。
<FW_C> display ike sa
IKE SA information :
Conn-ID Peer VPN Flag(s) Phase RemoteType RemoteID
62887864 1.1.2.1:500 RD|ST|A v2:2 IP 1.1.2.1
62887652 1.1.2.1:500 RD|ST|A v2:1 IP 1.1.2.1
Number of IKE SA : 2
Flag Description:
RD–READY ST–STAYALIVE RL–REPLACED FD–FADING TO–TIMEOUT
HRT–HEARTBEAT LKG–LAST KNOWN GOOD SEQ NO. BCK–BACKED UP
M–ACTIVE S–STANDBY A–ALONE NEG–NEGOTIATING
5.总部防火墙FW_A上可以查看到一对双向的IPSec SA,对应分支FW_C。
<FW_A> display ipsec sa brief
Current ipsec sa num:2
Spu board slot 1, cpu 1 ipsec sa information:
Number of SAs:2
Src address Dst address SPI VPN Protocol Algorithm
1.1.2.1 1.1.5.1 3923280450 ESP E:AES-256 A:SHA2_256_128
1.1.5.1 1.1.2.1 2676437093 ESP E:AES-256 A:SHA2_256_128
6.分支节点FW_C上可以查看到一对双向IPSec SA。<FW_C> display ipsec sa brief
Current ipsec sa num:2
Spu board slot 1, cpu 1 ipsec sa information:
Number of SAs:4
Src address Dst address SPI VPN Protocol Algorithm
10.1.5.2 1.1.2.1 2179965693 ESP E:AES-256 A:SHA2_256_128
1.1.2.1 10.1.5.2 3813759530 ESP E:AES-256 A:SHA2_256_128
第二种方法,即做vpn又做nat,意思是电脑又和总部vpn通,又能上外网,都在一台防火墙设备上实现。
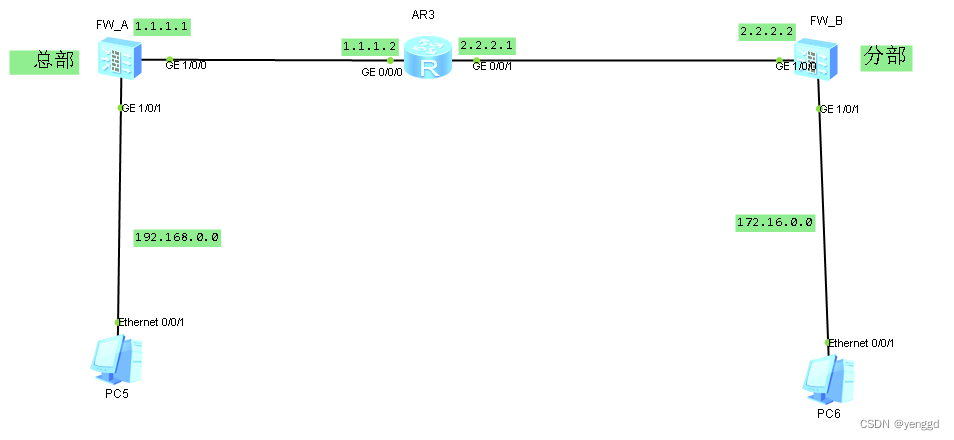
FW_A主要配置:
acl number 3000
rule 5 permit ip source 192.168.0.0 0.0.0.255 destination 172.16.0.0 0.0.0.255
ipsec proposal pro1
transfrom esp
ike proposal 10
ike peer fenbu_1
pre-shared-key admin
ike-proposal 10
nat traversal
ipsec policy-template temp1 1
security acl 3000
ike-peer fenbu_1
proposal pro1
ipsec policy policy1 1 isakmp template temp1
interface GigabitEthernet1/0/0
undo shutdown
ip address 1.1.1.1 255.255.255.0
service-manage ping permit
ipsec policy policy1
interface GigabitEthernet1/0/1
undo shutdown
ip address 192.168.0.1 255.255.255.0
service-manage ping permit
dhcp select interface
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/1
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
ip route-static 0.0.0.0 0.0.0.0 1.1.1.2
FW_B主要配置:
acl number 2000
rule 5 permit source 172.16.0.0 0.0.0.255
acl number 3000
rule 5 permit ip source 172.16.0.0 0.0.0.255 destination 192.168.0.0 0.0.0.255
ipsec proposal pro1
transfrom esp
ike proposal 10
ike peer zongbu
pre-shared-key admin
ike-proposal 10
remote-address 1.1.1.1
nat traversal
ipsec policy policy1 1 isakmp
security acl 3000
ike-peer zongbu
proposal pro1
interface GigabitEthernet1/0/0
undo shutdown
ip address 1.1.1.1 255.255.255.0
service-manage ping permit
ipsec policy policy1
interface GigabitEthernet1/0/1
undo shutdown
ip address 172.16.0.1 255.255.255.0
service-manage ping permit
dhcp select interface
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/1
ip route-static 0.0.0.0 0.0.0.0 2.2.2.1
nat-policy //先匹配vpn的数据,如果是上网的会自动往下走,匹配下面那个策略
rule name policy_vpn
source-address 172.16.0.0 mask 255.255.255.0
destination-address 192.168.0.0 mask 255.255.255.0
action no-nat
rule name policy_internet
source-zone trust
destination-zone untrust
source-address 172.16.0.0 mask 255.255.255.0
action source-nat easy-ip
注意:
如果内部还有对外发部的服务器映射端口,那在nat server映射时命令的尾部一定要加上no-reverse,这样就不产生server-map表,要不然vpn不通。
nat server protocol tcp global 2.2.2.2 80 inside 172.16.0.100 80 no-reverse