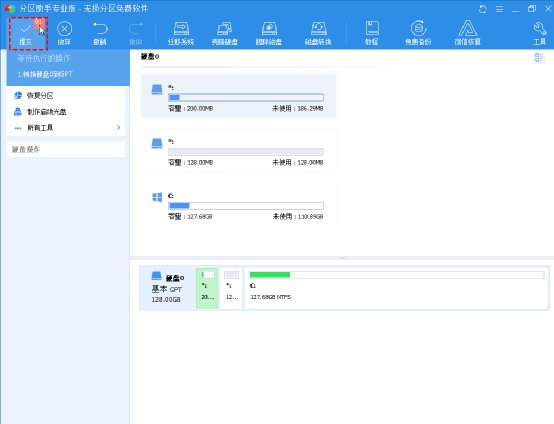
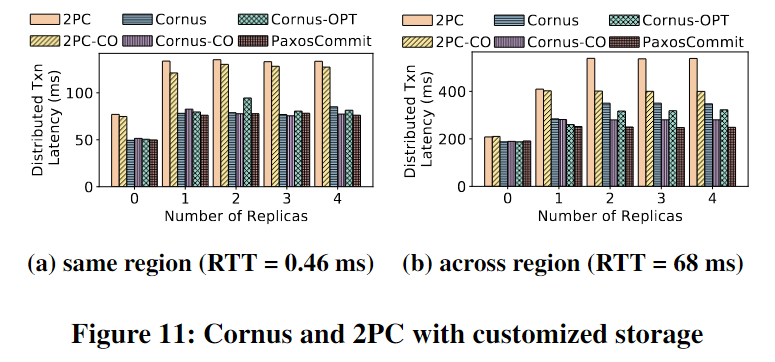
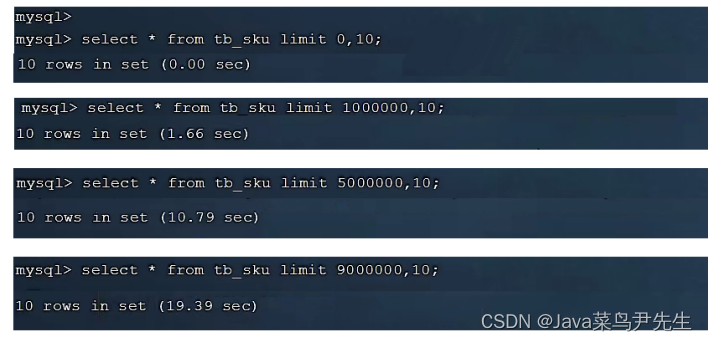
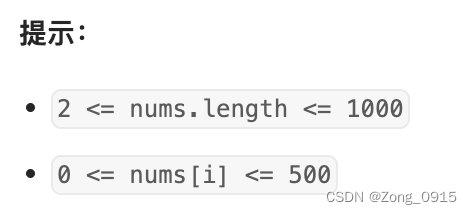
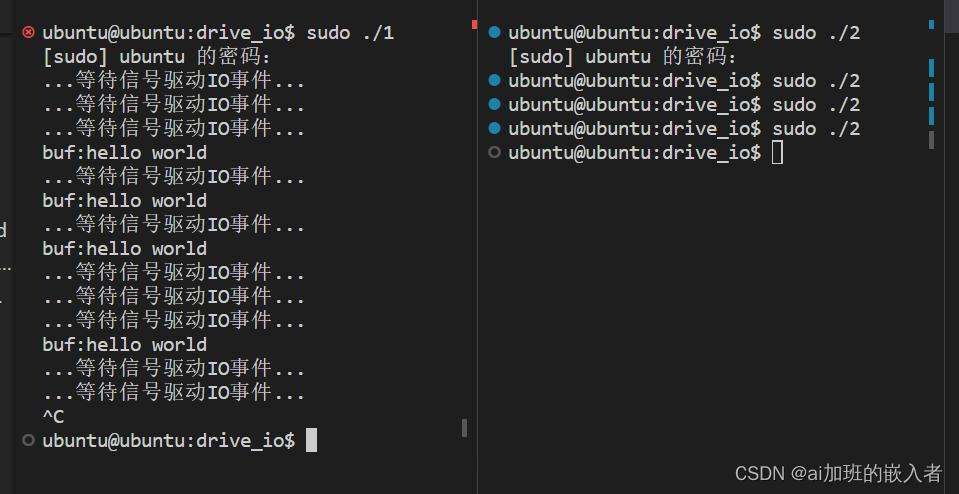
题目:
检测的目标进程:
ydebugg ; “ImmunityDebugger.exe”
_500], rax
Exe ; “ollydbg.exe”
_4F8], rax
hackerE ; “ProcessHacker.exe”
_4F0], rax
Exe ; “tcpview.exe”
_4E8], rax
sExe ; “autoruns.exe”
_4E0], rax
scExe ; “autorunsc.exe”
_4D8], rax
Exe ; “filemon.exe”
_4D0], rax
Exe ; “procmon.exe”
_4C8], rax
xe ; “regmon.exe”
_4C0], rax
Exe ; “procexp.exe”
_4B8], rax
; “idaq.exe”
_4B0], rax
xe ; “idaq64.exe”
_4A8], rax
rkExe ; “Wireshark.exe”
_4A0], rax
Exe ; “dumpcap.exe”
_498], rax
lorerEx ; “HookExplorer.exe”
_490], rax
ecExe ; “ImportREC.exe”
_488], rax
Exe ; “PETools.exe”
_480], rax
xe ; “LordPE.exe”
_478], rax
ectorEx ; “SysInspector.exe”
_470], rax
lyzerEx ; “proc_analyzer.exe”
_468], rax
yzerExe ; “sysAnalyzer.exe”
_460], rax
tExe ; “sniff_hit.exe”
_458], rax
xe ; “windbg.exe”
_450], rax
ontrolE ; “joeboxcontrol.exe”
_448], rax
erverEx ; “joeboxserver.exe”
_440], rax
erverEx ; “joeboxserver.exe”
_438], rax
ehacker ; “ResourceHacker.exe”
_430], rax
xe ; “x32dbg.exe”
_428], rax
xe ; “x64dbg.exe”
_420], rax
Exe ; “Fiddler.exe”
_418], rax
uggerEx ; “httpdebugger.exe”
_410], rax
_3EC], ax
_3CC], 0
检测的目标服务:
mov [rbp+240h+var_23C], 0Dh
lea rax, aVboxwddm ; “VBoxWddm”
mov [rbp+240h+psz2], rax
lea rax, aVboxsf ; “VBoxSF”
mov [rbp+240h+var_208], rax
lea rax, aVboxmouse ; “VBoxMouse”
mov [rbp+240h+var_200], rax
lea rax, aVboxguest ; “VBoxGuest”
mov [rbp+240h+var_1F8], rax
lea rax, aVmci ; “vmci”
mov [rbp+240h+var_1F0], rax
lea rax, aVmhgfs ; “vmhgfs”
mov [rbp+240h+var_1E8], rax
lea rax, aVmmouse ; “vmmouse”
mov [rbp+240h+var_1E0], rax
lea rax, aVmmemctl ; “vmmemctl”
mov [rbp+240h+var_1D8], rax
lea rax, aVmusb ; “vmusb”
mov [rbp+240h+var_1D0], rax
lea rax, aVmusbmouse ; “vmusbmouse”
mov [rbp+240h+var_1C8], rax
lea rax, aVmxSvga ; “vmx_svga”
mov [rbp+240h+var_1C0], rax
lea rax, aVmxnet ; “vmxnet”
mov [rbp+240h+var_1B8], rax
lea rax, aVmx86 ; “vmx86”
mov [rbp+240h+var_1B0], rax
mov r8d, 5 ; dwDesiredAccess
lea rdx, DatabaseName ; “ServicesActive”
xor ecx, ecx ; lpMachineName
call cs:__imp_OpenSCManagerW
1、WINDOWS API
进程遍历
CreateToolhelp32Snapshot
Process32First
Process32Next
EnumProcesses
服务遍历
OpenSCManagerW
EnumServicesStatusExA
EnumServicesStatusExW
进程模块遍历
Module32First
Module32Next
EnumProcessModules
2、脚本
使用WMIC 命令 实现当前系统进程信息遍历
使用WMIC 命令 实现枚举当前系统服务信息遍历
目标:对目标进程和服务进行分类,分类标准自己定,后续讲评。了解API 用法,使用指定API 完成系统进程遍历,并遍历每个进程中的模块信息,并判断当前系统中是否存在目标进程;使用指定API完成系统服务信息遍历,并检测目标服务是否存在;并能正常调试运行;使用WMIC命令 实现系统进程和服务信息的遍历。
查阅的资料

#include <windows.h>
#include <tlhelp32.h>
#include <tchar.h>
// Forward declarations:
BOOL GetProcessList( );
BOOL ListProcessModules( DWORD dwPID );
BOOL ListProcessThreads( DWORD dwOwnerPID );
void printError( const TCHAR* msg );
int main( void )
{
GetProcessList( );
return 0;
}
BOOL GetProcessList( )
{
HANDLE hProcessSnap;
HANDLE hProcess;
PROCESSENTRY32 pe32;
DWORD dwPriorityClass;
// Take a snapshot of all processes in the system.
hProcessSnap = CreateToolhelp32Snapshot( TH32CS_SNAPPROCESS, 0 );
if( hProcessSnap == INVALID_HANDLE_VALUE )
{
printError( TEXT("CreateToolhelp32Snapshot (of processes)") );
return( FALSE );
}
// Set the size of the structure before using it.
pe32.dwSize = sizeof( PROCESSENTRY32 );
// Retrieve information about the first process,
// and exit if unsuccessful
if( !Process32First( hProcessSnap, &pe32 ) )
{
printError( TEXT("Process32First") ); // show cause of failure
CloseHandle( hProcessSnap ); // clean the snapshot object
return( FALSE );
}
// Now walk the snapshot of processes, and
// display information about each process in turn
do
{
_tprintf( TEXT("\n\n=====================================================" ));
_tprintf( TEXT("\nPROCESS NAME: %s"), pe32.szExeFile );
_tprintf( TEXT("\n-------------------------------------------------------" ));
// Retrieve the priority class.
dwPriorityClass = 0;
hProcess = OpenProcess( PROCESS_ALL_ACCESS, FALSE, pe32.th32ProcessID );
if( hProcess == NULL )
printError( TEXT("OpenProcess") );
else
{
dwPriorityClass = GetPriorityClass( hProcess );
if( !dwPriorityClass )
printError( TEXT("GetPriorityClass") );
CloseHandle( hProcess );
}
_tprintf( TEXT("\n Process ID = 0x%08X"), pe32.th32ProcessID );
_tprintf( TEXT("\n Thread count = %d"), pe32.cntThreads );
_tprintf( TEXT("\n Parent process ID = 0x%08X"), pe32.th32ParentProcessID );
_tprintf( TEXT("\n Priority base = %d"), pe32.pcPriClassBase );
if( dwPriorityClass )
_tprintf( TEXT("\n Priority class = %d"), dwPriorityClass );
// List the modules and threads associated with this process
ListProcessModules( pe32.th32ProcessID );
ListProcessThreads( pe32.th32ProcessID );
} while( Process32Next( hProcessSnap, &pe32 ) );
CloseHandle( hProcessSnap );
return( TRUE );
}
BOOL ListProcessModules( DWORD dwPID )
{
HANDLE hModuleSnap = INVALID_HANDLE_VALUE;
MODULEENTRY32 me32;
// Take a snapshot of all modules in the specified process.
hModuleSnap = CreateToolhelp32Snapshot( TH32CS_SNAPMODULE, dwPID );
if( hModuleSnap == INVALID_HANDLE_VALUE )
{
printError( TEXT("CreateToolhelp32Snapshot (of modules)") );
return( FALSE );
}
// Set the size of the structure before using it.
me32.dwSize = sizeof( MODULEENTRY32 );
// Retrieve information about the first module,
// and exit if unsuccessful
if( !Module32First( hModuleSnap, &me32 ) )
{
printError( TEXT("Module32First") ); // show cause of failure
CloseHandle( hModuleSnap ); // clean the snapshot object
return( FALSE );
}
// Now walk the module list of the process,
// and display information about each module
do
{
_tprintf( TEXT("\n\n MODULE NAME: %s"), me32.szModule );
_tprintf( TEXT("\n Executable = %s"), me32.szExePath );
_tprintf( TEXT("\n Process ID = 0x%08X"), me32.th32ProcessID );
_tprintf( TEXT("\n Ref count (g) = 0x%04X"), me32.GlblcntUsage );
_tprintf( TEXT("\n Ref count (p) = 0x%04X"), me32.ProccntUsage );
_tprintf( TEXT("\n Base address = 0x%08X"), (DWORD) me32.modBaseAddr );
_tprintf( TEXT("\n Base size = %d"), me32.modBaseSize );
} while( Module32Next( hModuleSnap, &me32 ) );
CloseHandle( hModuleSnap );
return( TRUE );
}
BOOL ListProcessThreads( DWORD dwOwnerPID )
{
HANDLE hThreadSnap = INVALID_HANDLE_VALUE;
THREADENTRY32 te32;
// Take a snapshot of all running threads
hThreadSnap = CreateToolhelp32Snapshot( TH32CS_SNAPTHREAD, 0 );
if( hThreadSnap == INVALID_HANDLE_VALUE )
return( FALSE );
// Fill in the size of the structure before using it.
te32.dwSize = sizeof(THREADENTRY32);
// Retrieve information about the first thread,
// and exit if unsuccessful
if( !Thread32First( hThreadSnap, &te32 ) )
{
printError( TEXT("Thread32First") ); // show cause of failure
CloseHandle( hThreadSnap ); // clean the snapshot object
return( FALSE );
}
// Now walk the thread list of the system,
// and display information about each thread
// associated with the specified process
do
{
if( te32.th32OwnerProcessID == dwOwnerPID )
{
_tprintf( TEXT("\n\n THREAD ID = 0x%08X"), te32.th32ThreadID );
_tprintf( TEXT("\n Base priority = %d"), te32.tpBasePri );
_tprintf( TEXT("\n Delta priority = %d"), te32.tpDeltaPri );
_tprintf( TEXT("\n"));
}
} while( Thread32Next(hThreadSnap, &te32 ) );
CloseHandle( hThreadSnap );
return( TRUE );
}
void printError( const TCHAR* msg )
{
DWORD eNum;
TCHAR sysMsg[256];
TCHAR* p;
eNum = GetLastError( );
FormatMessage( FORMAT_MESSAGE_FROM_SYSTEM | FORMAT_MESSAGE_IGNORE_INSERTS,
NULL, eNum,
MAKELANGID(LANG_NEUTRAL, SUBLANG_DEFAULT), // Default language
sysMsg, 256, NULL );
// Trim the end of the line and terminate it with a null
p = sysMsg;
while( ( *p > 31 ) || ( *p == 9 ) )
++p;
do { *p-- = 0; } while( ( p >= sysMsg ) &&
( ( *p == '.' ) || ( *p < 33 ) ) );
// Display the message
_tprintf( TEXT("\n WARNING: %s failed with error %d (%s)"), msg, eNum, sysMsg );
}
https://learn.microsoft.com/zh-cn/windows/win32/toolhelp/taking-a-snapshot-and-viewing-processes
#include <windows.h>
#include <stdio.h>
#include <tchar.h>
#include <psapi.h>
// To ensure correct resolution of symbols, add Psapi.lib to TARGETLIBS
// and compile with -DPSAPI_VERSION=1
void PrintProcessNameAndID( DWORD processID )
{
TCHAR szProcessName[MAX_PATH] = TEXT("<unknown>");
// Get a handle to the process.
HANDLE hProcess = OpenProcess( PROCESS_QUERY_INFORMATION |
PROCESS_VM_READ,
FALSE, processID );
// Get the process name.
if (NULL != hProcess )
{
HMODULE hMod;
DWORD cbNeeded;
if ( EnumProcessModules( hProcess, &hMod, sizeof(hMod),
&cbNeeded) )
{
GetModuleBaseName( hProcess, hMod, szProcessName,
sizeof(szProcessName)/sizeof(TCHAR) );
}
}
// Print the process name and identifier.
_tprintf( TEXT("%s (PID: %u)\n"), szProcessName, processID );
// Release the handle to the process.
CloseHandle( hProcess );
}
int main( void )
{
// Get the list of process identifiers.
DWORD aProcesses[1024], cbNeeded, cProcesses;
unsigned int i;
if ( !EnumProcesses( aProcesses, sizeof(aProcesses), &cbNeeded ) )
{
return 1;
}
// Calculate how many process identifiers were returned.
cProcesses = cbNeeded / sizeof(DWORD);
// Print the name and process identifier for each process.
for ( i = 0; i < cProcesses; i++ )
{
if( aProcesses[i] != 0 )
{
PrintProcessNameAndID( aProcesses[i] );
}
}
return 0;
}
https://learn.microsoft.com/zh-cn/windows/win32/psapi/enumerating-all-processes